There are numerous way in which web applications can be infected and everyday backdoor news can be seen in headlines. Shell backdoor is another form malware script which are used to create a backdoor on web servers. In the form of backdoor, remote access is granted to access web server files. Now days developers should take care while creating an upload functionality in web application. According to ethical hacking researcher of International Institute of Cyber Security a small vulnerability in web application code can help hacker inject backdoor in web application. After injecting backdoor on server with malicious scripts, attackers tries to execute different commands and can do other malicious activities on web server.
We will show you various backdoors which are used for infecting any website. This will help system administrator’s to scan web servers for such backdoor files. Following process demonstrates process followed by hackers to upload backdoor on web servers with upload vulnerability.
- For testing with backdoor, we will use DVWA (Dam Vulnerability Web Application).
- Download the DVWA ISO for testing backdoor from http://www.dvwa.co.uk/DVWA-1.0.7.iso.
- For running DVWA ISO, you can use Oracle Virtualbox. Download virtualbox & install the executable.
- After installation of virtualbox. Import the DVWA ISO. Start the ISO.
- A terminal will open, type ifconfig. In our case IP Address of DVWA machine on which web server is running is 192.168.1.105.
- On hacker machine, open browser and type http://192.168.1.105.
- You will get DVWA login page.
- Default credentials for login
- Username: admin
- Password: password
- Now on hacker machine download backdoor’s for testing.
- Download from: https://github.com/backdoorhub/shell-backdoor-list
- If you are using Google Chrome, it might show warning or block backdoor before download of backdoor.
- For that we are using Mozilla Firefox.
- Mozilla firefox gives the an option to download the files. After downloading the zip file, Unzip the shell backdoors.
- Then go back to DVWA login. Enter the
- Username: admin
- Password: password

- So for testing on DVWA we are lower the security, as shown below. For that go DVWA security.
- Click on low & then click on Submit.
- All the shell backdoor will be uploaded from File Upload Vulnerability. Click on choose backdoor file & then click on upload. We will show how it work in below steps.
- Uploading backdoor, we downloaded earlier.
- Starting with first backdoor, 0byt3m1n1_Backdoor.
- Go to : http://192.168.1.105/vulnerabilities/upload
0byt3m1n1_Backdoor
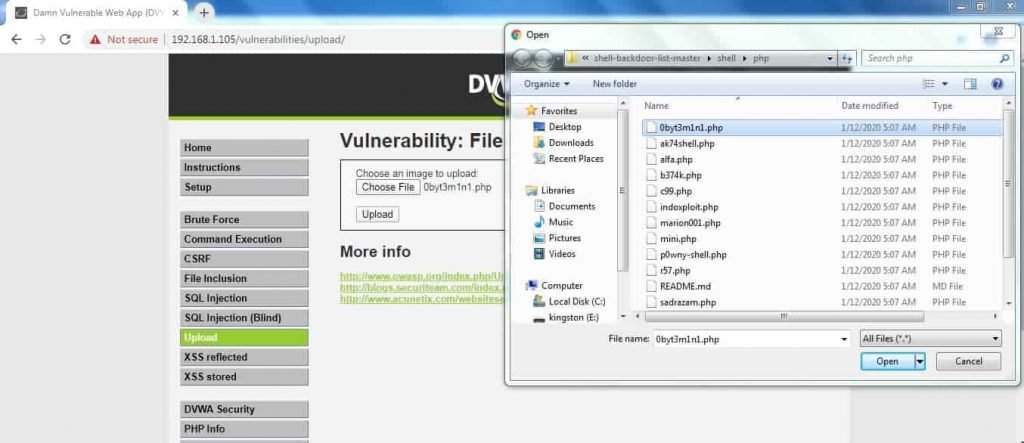
- Select 0byt3m1n1_Backdoor.
- Click on upload & you will see “successfully uploaded“.
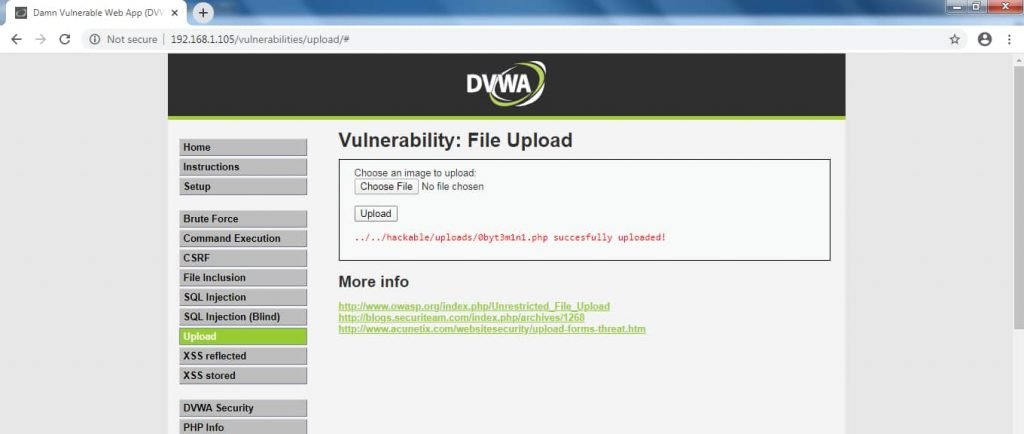
- After uploading the backdoor, attacker can access the web server files. Depending on the backdoor functionality attacker can even make changes or copy the file to another location.
- For accessing backdoor, open browser type http://192.168.1.105/hackable/uploads/0byt3m1n1.php
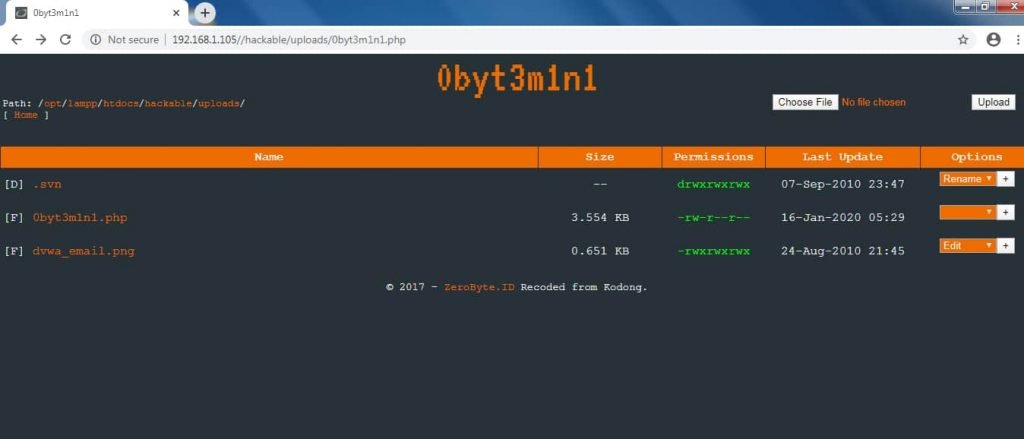
- Above shows that 0byt3m1n1 backdoor shows all the files on web server.
- 0byt3m1n1 gives basic functionality to edit, rename or delete the files.
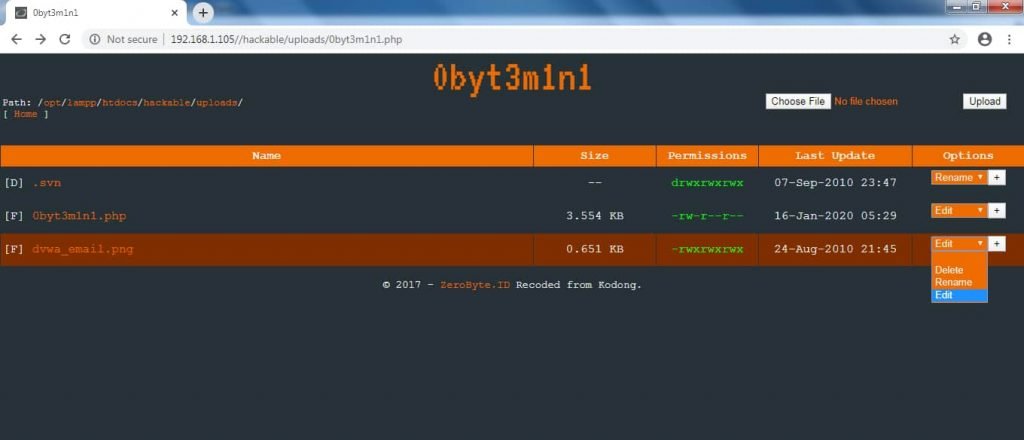
- Attacker can edit the files which are found on the server.
- As per ethical hacking researcher of International Institute of Cyber Security, if the security configured on server is high, attacker can use advance methods to upload the backdoor, which involves embedding backdoor in image file.
ak74shell Backdoor
- Testing another shell backdoors. Go to http://192.168.1.105/vulnerabilities/upload for uploading the shell backdoors.
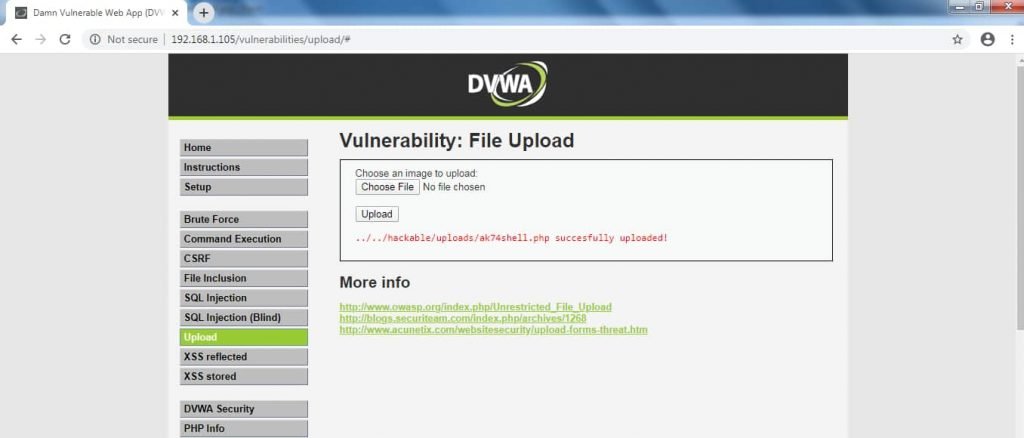
- After uploading the backdoor, go to browser type http://192.168.1.105/hackable/uploads/ak74shell.php
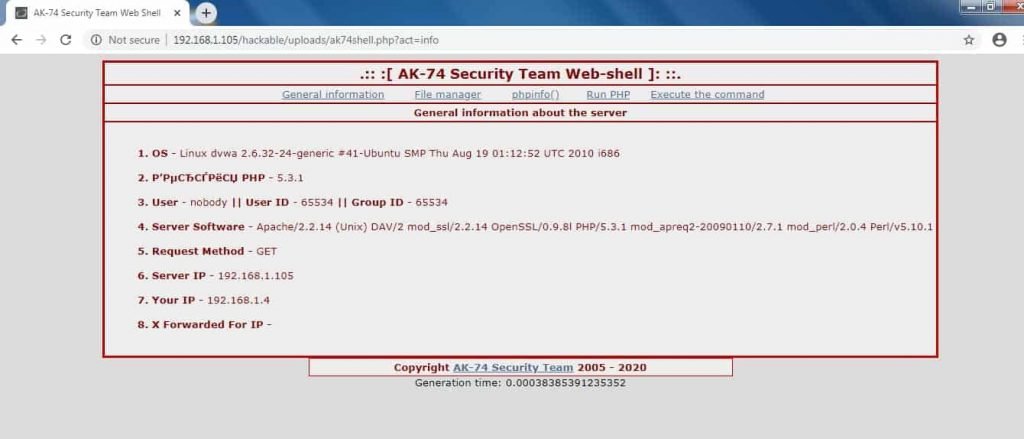
- ak74shell backdoor has many options to explore the web sever.
- Starting with General information. This clearly shows the operating system on which website is running and other details like Server software, source IP address & the attacker Ip address.
- Moving to another options – File manager. File manager shows all files which are available on the web server.
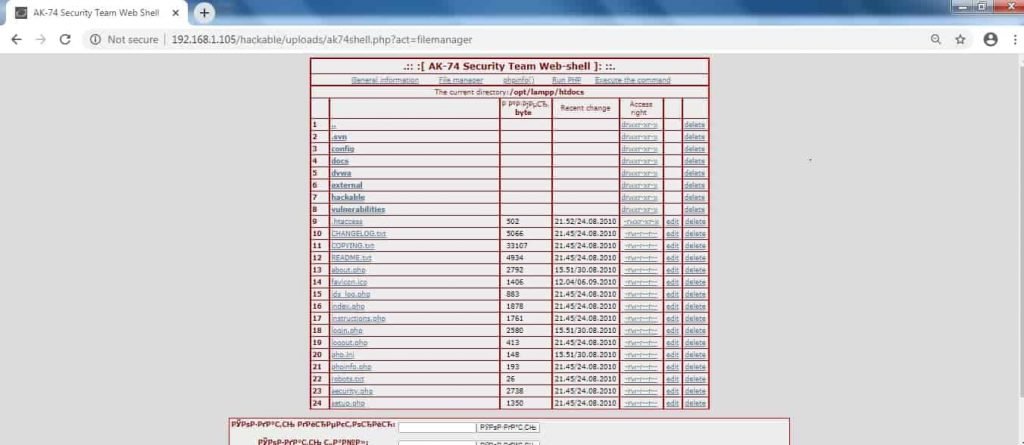
- Above shows the directories, files with recent change dates, access permission and gives the option for edit, delete.
- ak74shell changes file parameters to run desired code.
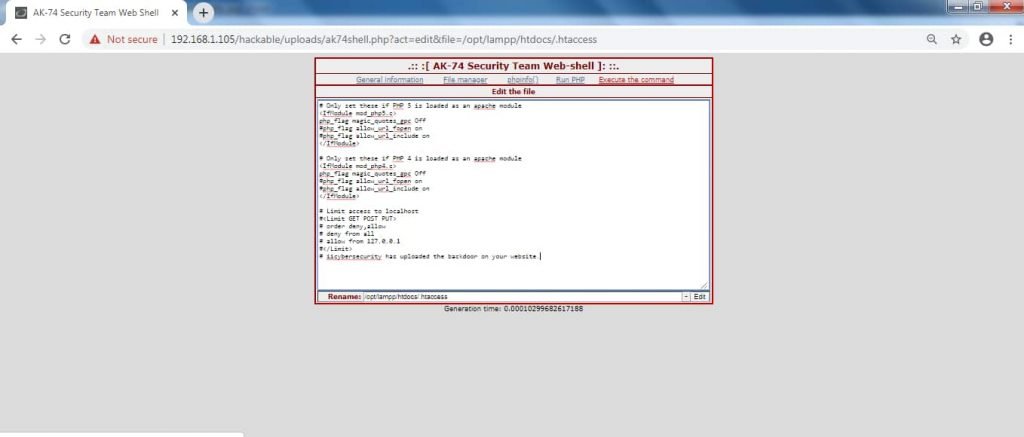
- This php backdoor also gives an option to execute command of Linux shell.
- Click on “Execute The Command” type any linux command. ls will show the files in current directory.
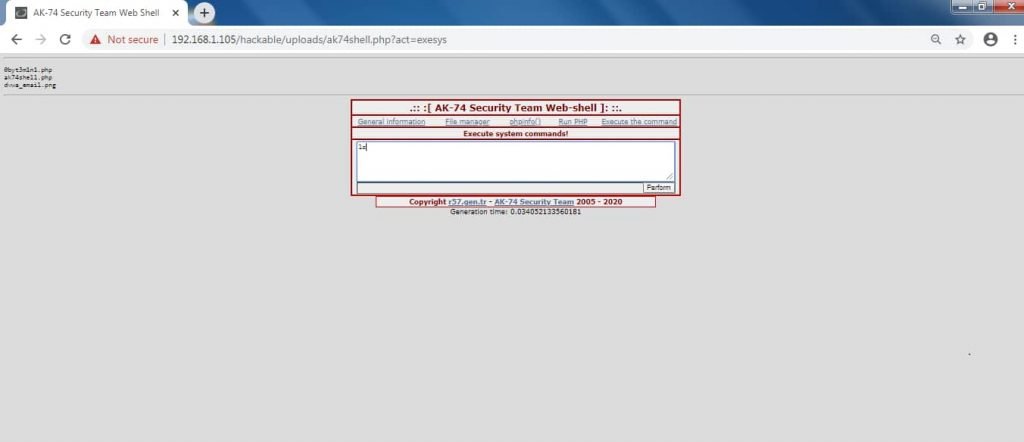
- Above the shows the ak74shell Command Shell which can be used to change or remove any important file from the server.
p0wny Backdoor
- Testing other php backdoor. Open browser type http://192.168.1.105/vulerabilites/upload
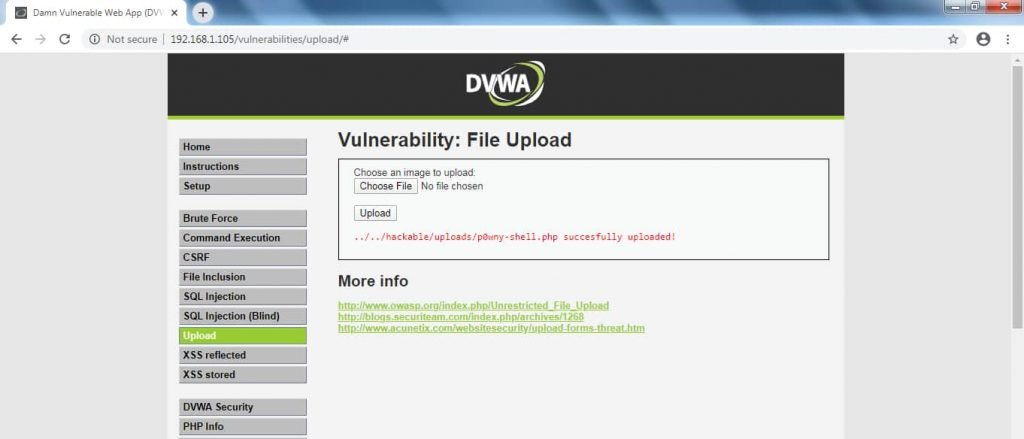
- After uploading the backdoor. Open browser type http://192.168.1.105/hackable/uploads/p0wny.php
- This backdoor gives direct access to web server files.
- p0wny will open Linux command shell.
- Attacker can run different Linux command in order to access directories and files.
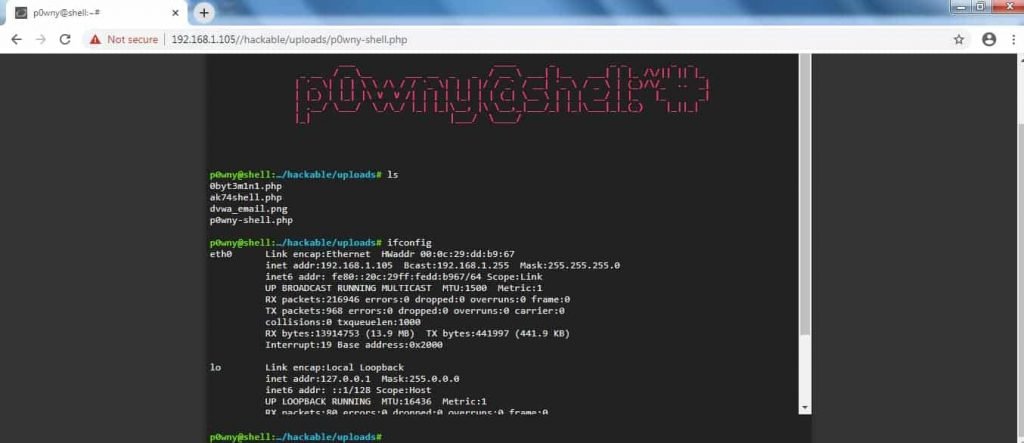
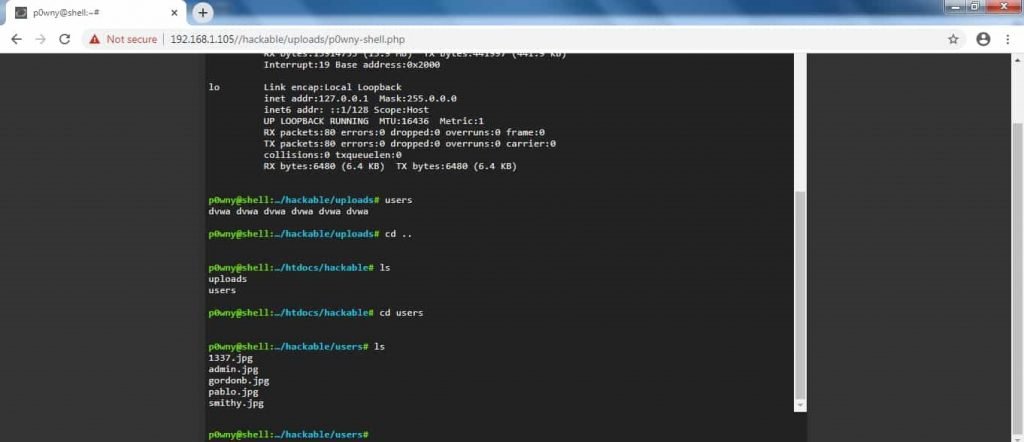
- Above shows the p0wny php backdoor Linux shell which is most dangerous vulnerability for any web server.
- You can similarly test another backdoors which are available on github. This can help to test web application upload vulnerability.
PHP Shell :
B374K Shell
C99 Shell
R57 Shell
Wso Shell
0byt3m1n1 Shell
Alfa Shell
AK-47 Shell
Indoxploit Shell
Marion001 Shell
Mini Shell
p0wny-shell
Sadrazam Shell
Webadmin Shell
WordPress Shell
ASP Shell :
Pouya Shell
Kacak Asp Shell
Asp Cmd (Old ISS)
Asp Cmd (New ISS)

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











