Devices that use the Android operating system are often targeted by multiple cyberattacks attempts. This time, experts in ethical hacking from Trend Micro reported the discovery of three malicious apps available on Google Play used to compromise devices and steal sensitive information by exploiting a critical vulnerability.
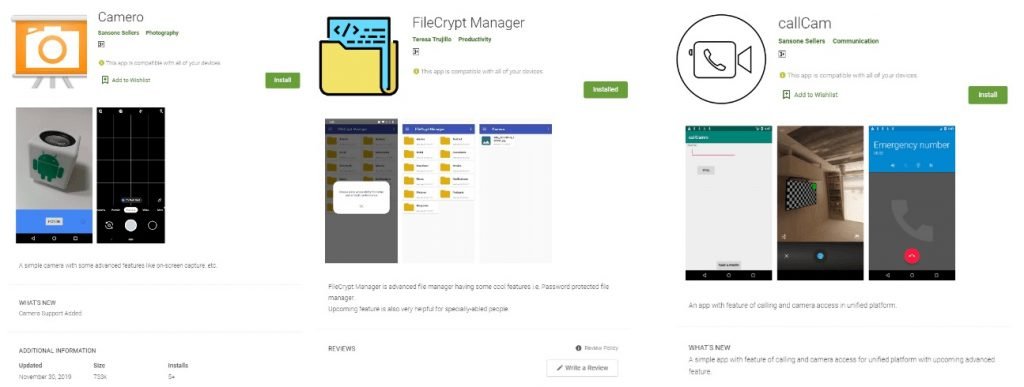
The three malicious applications are Camero, FileCryptManager and CallCam. According to the report, the malicious code hidden in these applications is used to exploit a dangerous use-after-free vulnerability tracked as CVE-2019-2215.
SOURCE: Trend Micro
This is the first attack detected in the wild exploiting the CVE-2019-2215 vulnerability, claimed the experts in ethical hacking. In case of being exploited, this security flaw allows hackers to download files on the target device without the need of victims’ interaction.
Apparently these apps are linked to the hacking group known as SideWinder APT, active for at least eight years. The main feature of these hackers is their special focus on Windows devices operating in military installations in the US and many other parts of the world.
Malicious apps were disguised as camera and file administrators; while Camero and FileCryptManager act as droppers of the malicious payload, CallCam contains the final payload to steal the victims’ information.
In turn, the final attack is divided into two distinct stages:
- Stage 1: Download the DEX file from the attacker’s C&C server
- Stage 2: The downloaded DEX file downloads an APK that will be installed after exploiting your device or using accessibility
Trend Micro’s ethical hacking experts’ report mentions that this whole process is done without victims being able to notice malicious activity, plus their interaction is not required: “Hackers evade detection using various methods of obfuscation, data encryption, and use of dynamic code,” they add. Before delivering the final payload, droppers attempt to root the phone or, failing that, get Accessibility Permission on the attacked device.
When the final payload starts on the infected device, it hides its icon and starts collecting information in the background, encrypting the stolen data and sending it to the attacker’s C&C server. According to the International Institute of Cyber Security (IICS), these attacks usually collect data such as location, battery status, apps installed on the device, user account data, WiFi usage, among other details.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










