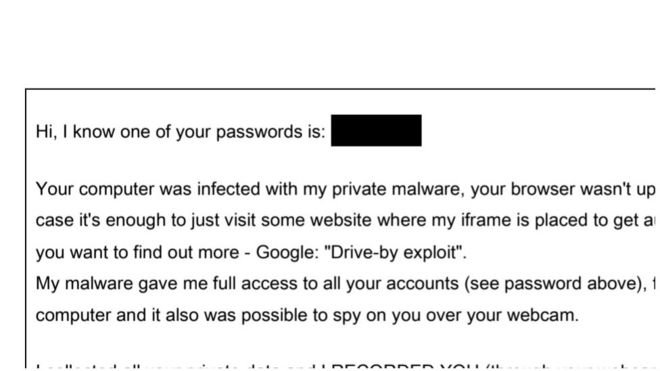
During 2019 hundreds of thousands of users worldwide were victims of an email scam in which those responsible claimed to have hacked people’s devices to record videos of victims visiting pornographic or similar content sites. In exchange for not disclosing the alleged embarrassing video, the hackers demanded a ransom that had to be paid in Bitcoin, as reported various information security firms that tracked this fraudulent campaign.
In this message, hackers threaten victims to disclose these videos or photos unless they make an $800 USD payment in Bitcoin (the amount could vary depending on the region). The message included some details about the victim, such as usernames and passwords for some online platforms, probably collected from data breaches on other sites.
Recently, French authorities unveiled the arrest of two individuals related to this campaign. One of the defendants is a 21-year-old Frenchman who was interviewed in 2017 by the specialist platform KerbsOnSecurity, when he admitted he was the creator of a dangerous malware variant. The report does not specify the names of the accused, although one of them is identified under the pseudonym Antoine I.”
After months of investigation, Antoine I. was handed over to the French authorities, the hacker was subsequently charged by the French government for various crimes, including organized association to commit extortion, fraudulent use of computer systems, money laundering, among others.
According to information published by French newspaper Le Parisien, the defendant admitted having designed the “sextortion” scheme, which he launched since 2018 and reached its peak activity during the summer of 2019. In complicity with the second individual arrested, Antoine I. would have deployed dangerous malware to infect more than 2,000 computer equipment, integrating a botnet to send hundreds of thousands of fraudulent emails.
As mentioned above, Antoine I. was interviewed a couple of years ago by the specialized information security platform KerbsOnSecurity. In that interview, the hacker was awarded the creation of Nuclear Bot, a dangerous Trojan used to steal credentials to access online banking platforms from victims: “I think the creation of this malware was a big mistake; many people will reuse it to steal money,” he said in the interview, for which he used his so-called real name, Augustin Inzirillo.
Despite his statements lamenting the creation of Nuclear Bot (also known as NukeBot), the hacker did not hesitate to take advantage of this malware to deploy the massive sextortion campaign with which he and his accomplice dishonestly earned at least €1M.
However, the hacker was unable to cover his trail properly, as while using the Twitter account @tinygang1 (now suspended) he revealed that he had used a variant of NukeBot to attack online banking users in Poland, France, among other countries. An information security researcher notified the French authorities of the activity of this Twitter account, in addition to searching for information on his own.
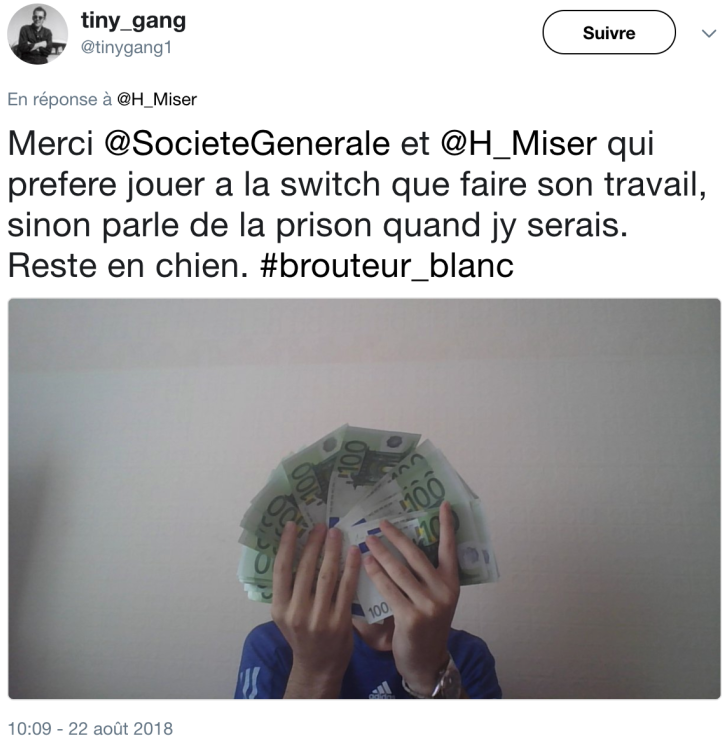
“The hacker modified the NukeBot source code repeatedly to create its own version of the malware, known as Tinynuke. Comparing it to the original code, leaked on GitHub, it was notorious that Tinynuke is a version with features far more advanced than the original NukeBot, especially video recording,” the researcher said in a report.
In addition, the researcher claims that the Twitter account operators @tinygang1 attacked various targets in France with modified versions of TinyNuke at least four times; stolen funds would have been washed in complicity with a mule network in the UK and other locations. Based on these indicators, information security firms and independent researchers agree that it is highly likely that campaign operators are responsible for creating the original code.
Multiple rumors about the author of this malware circulate in the cybersecurity and cybercrime community, most point to a serious ego problem: “He likes others to talk about it, although he is often very angry when these comments are in a mocking tone. It has even physically threatened other hackers and researchers,” the expert says.
The investigator’s report is consistent with the note published by Le Parisien, which states that Antoine I. threatened to death an anonymous information security investigator, identified as Marc: “If I don’t stop messing with me, I’ll put a bullet in your head,” the hacker threatened him.
Moreover, the International Institute of Cyber Security (IICS) mentions that this sextortion campaign was operated from Ukraine and other locations, mainly in Eastern Europe. For reasons that are not yet clear, the hacker returned to France to surrender to the authorities, his sentence will be revealed shortly.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











