Many times when running a scan of any URL to find its vulnerabilities. Pentesters or security researchers tries to find admin page. Landing on any admin page of any website is a critical vulnerability for any website. Because attackers could run session hijacking attacks or use brute force methods to steal login credentials of admin page. Many times developers forget to patch admin panel. According to ethical hacking researcher international institute of cyber security recently there has been many vulnerabilities came up which redirects end users to admin panels. We will show a method to find admin page of any website.
- For testing we will use Kali Linux 2018.4 amd64. Open terminal type git clone https://github.com/mIcHyAmRaNe/okadminfinder3.git
- Type cd okadminfinder3/
- Run ls
- Then type chmod u+x requirements.txt
- Type ls -ltr
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/mIcHyAmRaNe/okadminfinder3.git Cloning into 'okadminfinder3'… remote: Enumerating objects: 264, done. remote: Total 264 (delta 0), reused 0 (delta 0), pack-reused 264 Receiving objects: 100% (264/264), 231.98 KiB | 293.00 KiB/s, done. Resolving deltas: 100% (139/139), done. root@kali:/home/iicybersecurity/Downloads# cd okadminfinder3/ root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ls Classes LICENSE LinkFile okadminfinder.py README.md requirements.txt root@kali:/home/iicybersecurity/Downloads/okadminfinder3# chmod u+x requirements.txt root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ls -ltr total 48 -rwxr--r-- 1 root root 77 Jan 2 01:54 requirements.txt -rw-r--r-- 1 root root 3598 Jan 2 01:54 README.md -rwxr-xr-x 1 root root 18022 Jan 2 01:54 okadminfinder.py drwxr-xr-x 2 root root 4096 Jan 2 01:54 LinkFile -rw-r--r-- 1 root root 11347 Jan 2 01:54 LICENSE drwxr-xr-x 3 root root 4096 Jan 2 01:54 Classes
- Type pip3 install -r requirements.txt
root@kali:/home/iicybersecurity/Downloads/okadminfinder3# pip3 install -r requirements.txt
Collecting colorama==0.4.1 (from -r requirements.txt (line 1))
Downloading https://files.pythonhosted.org/packages/4f/a6/728666f39bfff1719fc94c481890b2106837da9318031f71a8424b662e12/colorama-0.4.1-py2.py3-none-any.whl
Collecting requests==2.21.0 (from -r requirements.txt (line 2))
Cache entry deserialization failed, entry ignored
Downloading https://files.pythonhosted.org/packages/7d/e3/20f3d364d6c8e5d2353c72a67778eb189176f08e873c9900e10c0287b84b/requests-2.21.0-py2.py3-none-any.whl (57kB)
100% |████████████████████████████████| 61kB 81kB/s
Requirement already satisfied: PySocks==1.6.8 in /usr/lib/python3/dist-packages (from -r requirements.txt (line 3)) (1.6.8)
Requirement already satisfied: argparse==1.4.0 in /usr/local/lib/python3.7/dist-packages (from -r requirements.txt (line 4)) (1.4.0)
Requirement already satisfied: tqdm==4.31.1 in /usr/local/lib/python3.7/dist-packages (from -r requirements.txt (line 5)) (4.31.1)
Requirement already satisfied: idna<2.9,>=2.5 in /usr/lib/python3/dist-packages (from requests==2.21.0->-r requirements.txt (line 2)) (2.6)
Requirement already satisfied: certifi>=2017.4.17 in /usr/lib/python3/dist-packages (from requests==2.21.0->-r requirements.txt (line 2)) (2018.8.24)
Requirement already satisfied: chardet<3.1.0,>=3.0.2 in /usr/lib/python3/dist-packages (from requests==2.21.0->-r requirements.txt (line 2)) (3.0.4)
Requirement already satisfied: urllib3<1.25,>=1.21.1 in /usr/lib/python3/dist-packages (from requests==2.21.0->-r requirements.txt (line 2)) (1.22)
Installing collected packages: colorama, requests
Found existing installation: colorama 0.3.9
Uninstalling colorama-0.3.9:
Successfully uninstalled colorama-0.3.9
Found existing installation: requests 2.22.0
Uninstalling requests-2.22.0:
Successfully uninstalled requests-2.22.0
Successfully installed colorama-0.4.1 requests-2.21.0
- Type ./okadminfinder.py –help
root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ./okadminfinder.py --help
____ __ __ __ _ _______ __
/ __ \/ //_/___ _____/ /___ ___ (_)___ / ____(_)___ ____/ /__ _____
/ / / / ,< / __ `/ __ / __ `__ \/ / __ \/ /_ / / __ \/ __ / _ \/ ___/
/ /_/ / /| / /_/ / /_/ / / / / / / / / / / __/ / / / / / /_/ / __/ /
\____/_/ |_\__,_/\__,_/_/ /_/ /_/_/_/ /_/_/ /_/_/ /_/\__,_/\___/_/
version 2.5.3 created by O.Koleda & rewrited by mIcHy AmRaNeusage: okadminfinder.py [-h] [-u URL] [-t] [-p PROXY] [-rp] [-r] [-v] [-U] [-i] optional arguments: -h, --help show this help message and exit -u URL, --url URL Target URL (e.g. 'www.example.com' or 'example.com') -t, --tor Use Tor anonymity network -p PROXY, --proxy PROXY Use an HTTP proxy (e.g '127.0.0.1:8080') -rp, --random-proxy Use randomly selected proxy server -r, --random-agent Use randomly selected User-Agent -v, --verbose Display more informations -U, --update Update OKadminFinder -i, --interactive Interactive interface[other arguments not required]
- Type ./okadminfinder.py -u testphp.vulnweb.com
- Testphp.vulnweb.com is common testing website. Used for running various scans.
- You can also use proxies or TOR service for hiding your identity.
- Type ./okadminfinder.py -u testphp.vulnweb.com OR type ./okadminfinder.py -r -u testphp.vulnweb.com
- -r is used for random user agent.
- -u is used for target URL. Target URL is testphp.vulnweb.com
root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ./okadminfinder.py -u testphp.vulnweb.com
____ __ __ __ _ _______ __
/ __ \/ //_/___ _____/ /___ ___ (_)___ / ____(_)___ ____/ /__ _____
/ / / / ,< / __ `/ __ / __ `__ \/ / __ \/ /_ / / __ \/ __ / _ \/ ___/
/ /_/ / /| / /_/ / /_/ / / / / / / / / / / __/ / / / / / /_/ / __/ /
\____/_/ |_\__,_/\__,_/_/ /_/ /_/_/_/ /_/_/ /_/_/ /_/\__,_/\___/_/
version 2.5.3 created by O.Koleda & rewrited by mIcHy AmRaNeSite testphp.vulnweb.com is stable
Processing …: 0%| |0/574
[✔] http://testphp.vulnweb.com/admin/ Admin page found!
Processing …: 1%|▉ |7/574
[✔] http://testphp.vulnweb.com/login.php Admin page found!
- Above shows the admin page of testphp.vulnweb.com
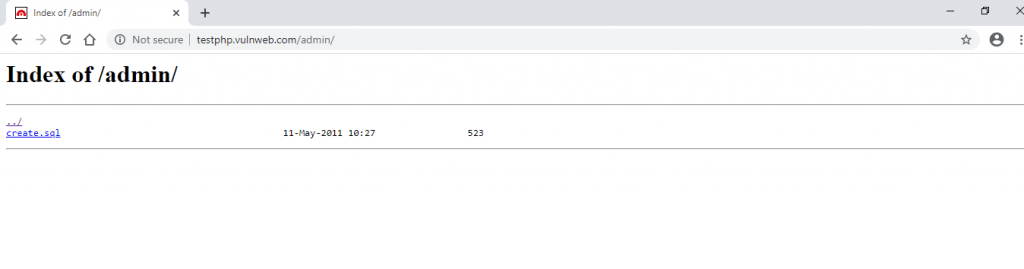
- Above you can refer admin page of the website.
- Let’s try on another sites.
- Type ./okadminfinder.py -u www.arifhabib.com.pk
- -u is used for target URL. Target URL – www.arifhabib.com.pk
root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ./okadminfinder.py -u www.arifhabib.com.pk
____ __ __ __ _ _______ __
/ __ \/ //_/___ _____/ /___ ___ (_)___ / ____(_)___ ____/ /__ _____
/ / / / ,< / __ `/ __ / __ `__ \/ / __ \/ /_ / / __ \/ __ / _ \/ ___/
/ /_/ / /| / /_/ / /_/ / / / / / / / / / / __/ / / / / / /_/ / __/ /
\____/_/ |_\__,_/\__,_/_/ /_/ /_/_/_/ /_/_/ /_/_/ /_/\__,_/\___/_/
version 2.5.3 created by O.Koleda & rewrited by mIcHy AmRaNeSite www.arifhabib.com.pk is stable
Processing …: 2%|█▋ |13/574
[✔] http://www.arifhabib.com.pk/cpanel/ Admin page found!
Processing …: 32%|███████████████████████▎ |186/574
[✔] http://www.arifhabib.com.pk/controlpanel/ Admin page found!
Processing …: 100%|████████████████████████████████████████████████████████████████████████|574/574
Completed
2 Admin pages found
574 total pages scanned
[/] Scanning over; Press Enter to Exit
- Opening the webpage in web browser.
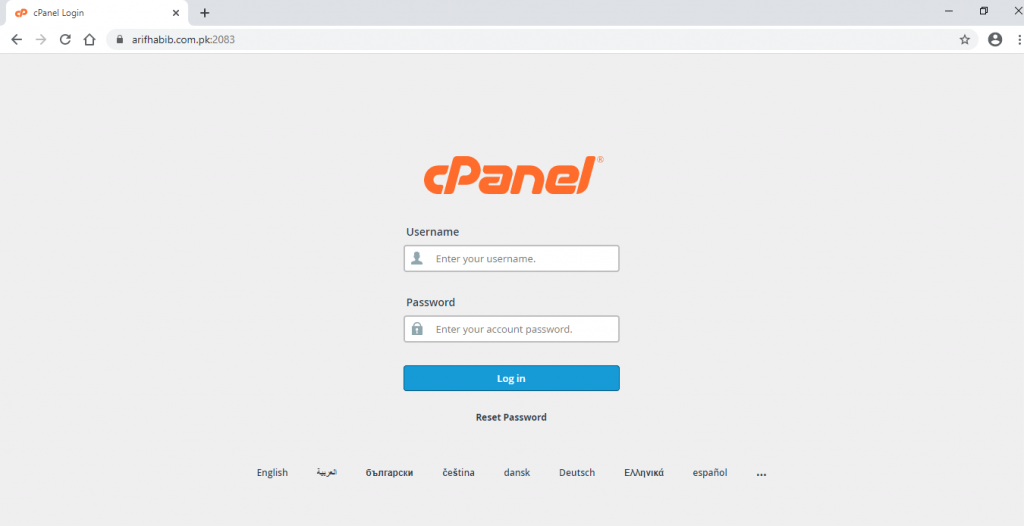
- Knowing admin page of any website puts an potential risk to website owner.
- Now we try with TOR anonymity.
- Type ./okadminfinder.py –tor -u exide.com.pk/
- –tor – It will used TOR service for finding target website admin page.
- For starting type sudo service tor start
- For checking TOR service running status. Type ps -ef | grep tor
- -u is used for target URL. Target URL – exide.com.pk/
root@kali:/home/iicybersecurity/Downloads/okadminfinder3# ./okadminfinder.py --tor -u exide.com.pk/
____ __ __ __ _ _______ __
/ __ \/ //_/___ _____/ /___ ___ (_)___ / ____(_)___ ____/ /__ _____
/ / / / ,< / __ `/ __ / __ `__ \/ / __ \/ /_ / / __ \/ __ / _ \/ ___/
/ /_/ / /| / /_/ / /_/ / / / / / / / / / / __/ / / / / / /_/ / __/ /
\____/_/ |_\__,_/\__,_/_/ /_/ /_/_/_/ /_/_/ /_/_/ /_/\__,_/\___/_/
version 2.5.3 created by O.Koleda & rewrited by mIcHy AmRaNeSite exide.com.pk/ is stable
Processing …: 0%| |0/574
[✔] http://exide.com.pk//admin/ Admin page found!
Processing …: 2%|█▋ |13/574
[✔] http://exide.com.pk//cpanel/ Admin page found!
Processing …: 3%|█▉ |15/574
[✔] http://exide.com.pk//dashboard Admin page found!
Processing …: 3%|██▎ |18/574
[✔] http://exide.com.pk//wp-login.php/ Admin page found!
Processing …: 5%|███▎ |26/574
[✔] http://exide.com.pk//wp-admin/ Admin page found!
Processing …: 8%|██████ |48/574
[✔] http://exide.com.pk//admin/index.php Admin page found!
- Opening the exide admin page.
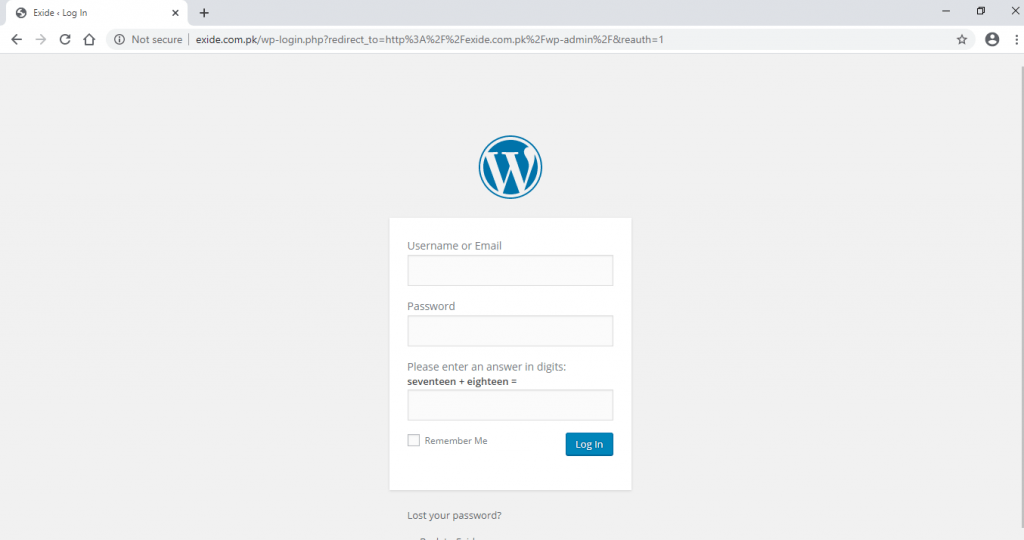
- Above shows the admin page using TOR proxies. It might take time while using TOR. But it will find the available admin page.
Check youtube link to see the practical of okadminfinder3
- Okadminfinder3 will use pre-build common list of admin logins, which are commonly found on any website admin panel. Below you can checkout listed keywords.
- You will find the file with name of adminpanellinks.txt
- Type cat adminpanellinks.txt
root@kali:/home/iicybersecurity/Downloads/okadminfinder3/LinkFile# cat adminpanellinks.txt %s/admin/ %s/admin.asp/ %s/admin/admin.asp/ %s/admin.aspx/ %s/admin/admin.aspx/ %s/admin.php/ %s/administrator/ %s/login.php %s/admin.php %s/user/ %s/usuarios/ %s/usuario/ %s/Admin/ %s/cpanel/ %s/phpmyadmin/ %s/dashboard %s/cms/ %s/users/ %s/wp-login.php/ %s/admin/login %s/auth/login/ %s/moderator/ %s/webadmin/ %s/webmaster/ %s/adminarea/ %s/bb-admin/ %s/wp-admin/ %s/wp-login/ %s/wp-admin.php %s/userlogin/ %s/logins/ %s/login.html %s/adminLogin/ %s/admin_area/ %s/panel-administracion/ %s/instadmin/ %s/memberadmin/ %s/administratorlogin/ %s/panel/ %s/forum/admin %s/adm/ %s/cp/ %s/vue-element-admin %s/admin/cp.php %s/cp.php %s/admincontrol/ %s/admincp/ %s/admin/account.php %s/admin/index.php %s/admin/login.php %s/admin/admin.php %s/admin_area/admin.php %s/admin_area/login.php %s/siteadmin/login.php %s/siteadmin/index.php %s/siteadmin/login.html %s/admin/account.html %s/admin/index.html %s/admin/login.html

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










