Among the wide variety of Internet of Things (IOT) devices currently available, smart doorbells and security cameras are among the most widely used solutions in modern homes. Due to their extensive use, a flaw in these systems could expose some risks to thousands of households, so it is necessary to use all possible security measures, data protection specialists recommend.
Ring is one of the most popular companies in this market and, although in the past multiple security flaws have been reported in their systems, many of these are avoidable with a little attention from the owners of the device, because just take a few minutes implement multi-factor authentication to prevent multiple security risks. Here’s how to enable this security measure on your Ring device.
This is a highly reliable and easy-to-enable security measure.
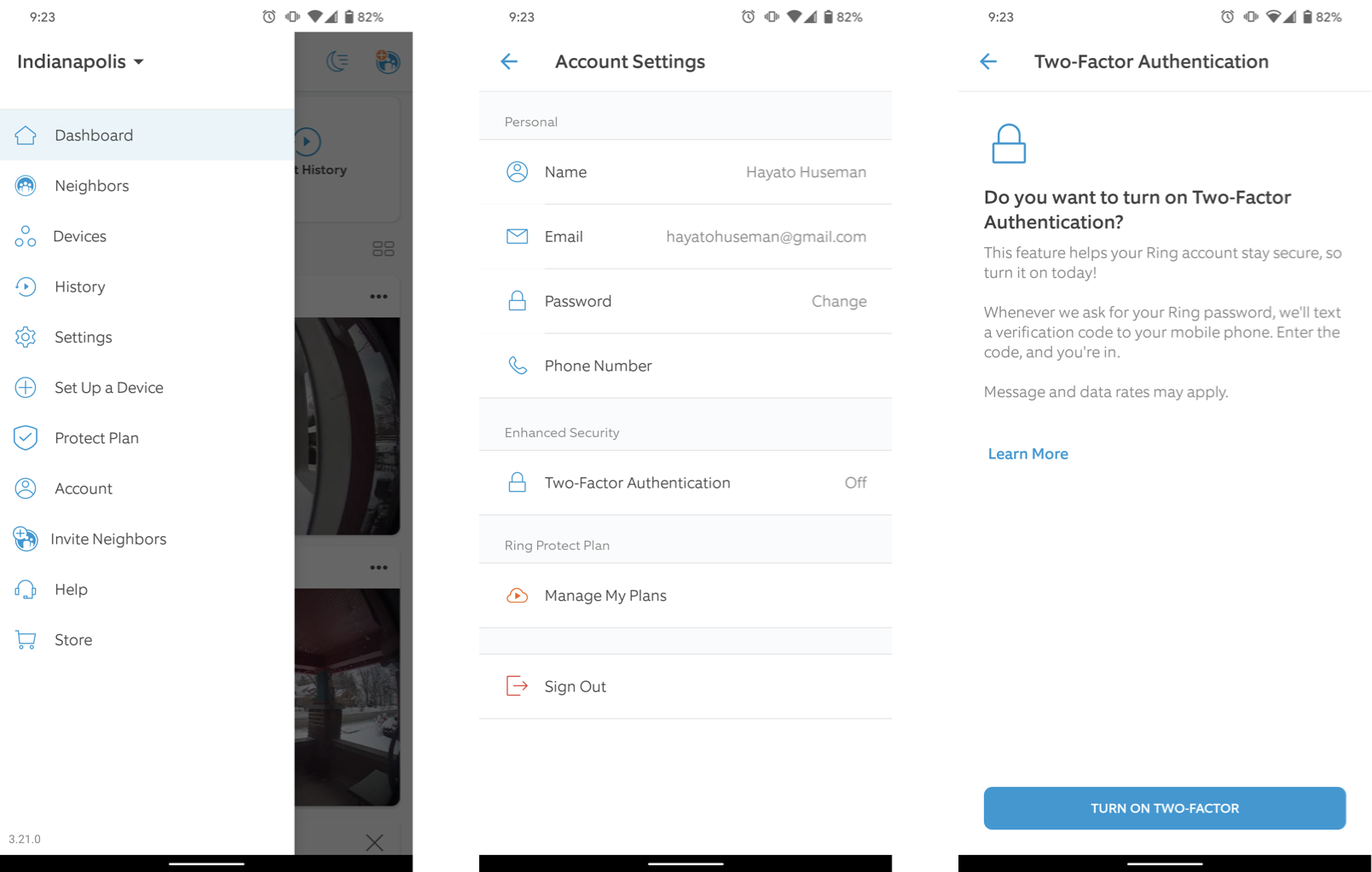
To start enabling from the Ring mobile app:
- Swipe left to access the side panel, and then select the Account option
- Under Enhanced Security, select Two-Factor Authentication
- When prompted to confirm on the next page, select Turn on Two-Factor

- Enter your password
- Enter your phone number for the system to send you a verification code
- Enter the verification code on the next page
Two-factor authentication is now enabled. From now on, you will receive a verification code via SMS each time you try to log in to your Ring account.
It is also possible to enable two-factor authentication for Ring users from the company’s official website. This could be a more convenient method for the user, as a phone number is not required to enable it every time you log in, data protection specialists mention.
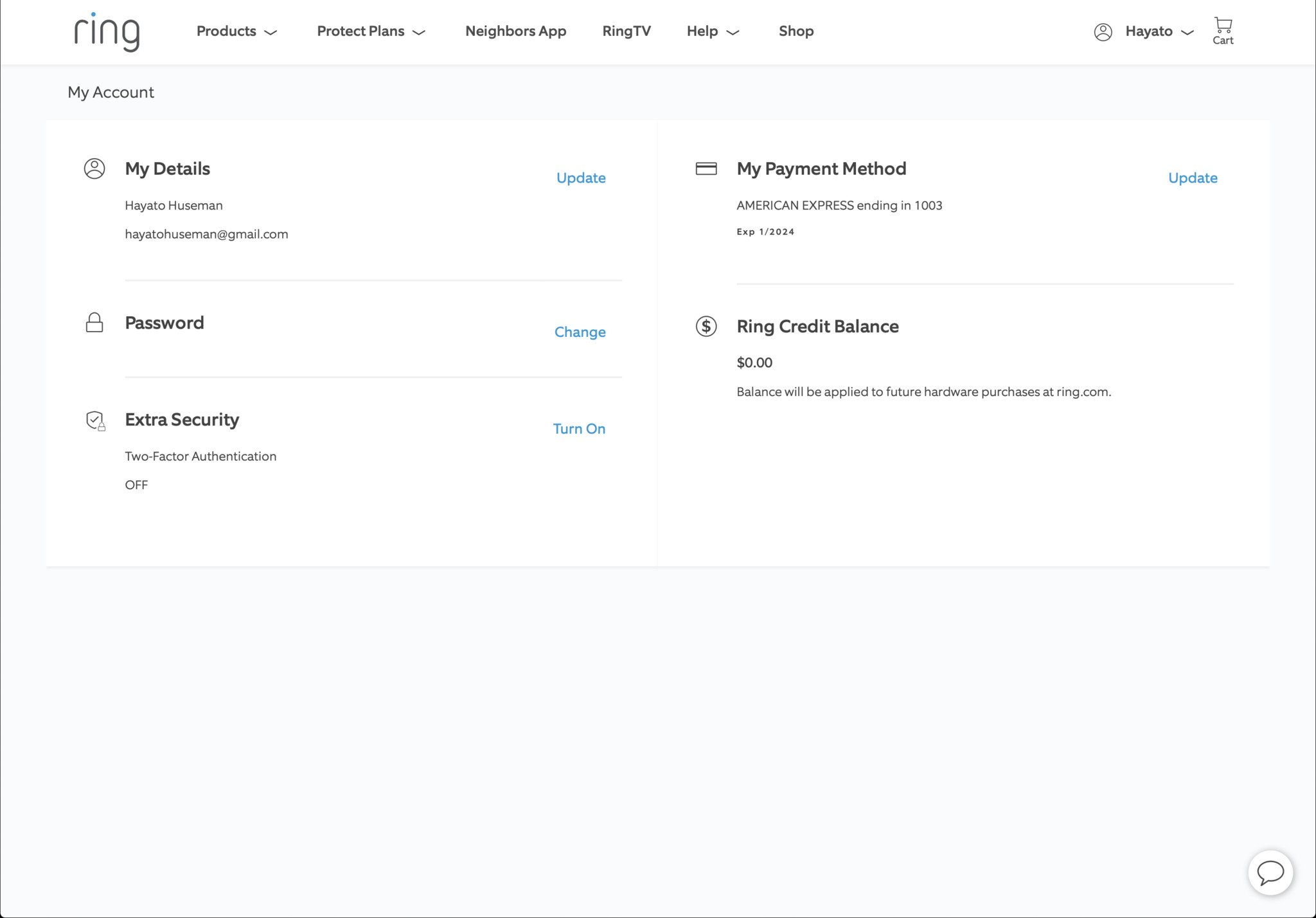
- To get started, log in to Ring, hover over your name, and click the Account option from the drop-down menu
- Under Additional Security, click Activate, then click Two-Factor Authentication
- Click Activate two factors on the confirmation screen
- Enter your password
- Enter your phone number to receive a verification code
- Enter the verification code on the next page
According to data protection specialists at the International Institute of Cyber Security (IICS), a hacker who wanted to compromise a Ring user account with two-factor authentication enabled would have to get the user’s login credentials, in addition to intercepting the SMS containing the key to confirm the legitimate login. While this is not impossible, this additional layer of security certainly increases the complexity of an attack, strengthening the weak default configurations of systems like Ring.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











