According to digital forensics specialists at security firm Applied Risk there are more than 100 vulnerabilities in multiple building management systems (BMS) of various manufacturers. If exploited, these flaws would allow threat actors to deploy denial of service (DoS) and remote code execution (RCE) attacks, and even collect critical information about the operation of these systems.
The vulnerabilities were discovered in the BMS of companies such as BACnet, Bosch, Nortek, Siemens, Schneider, Omron, among others. By performing a series of scans on Shodan, experts found about 19,000 vulnerable deployments connected to the public Internet, including 7,620 exposed BACnet systems and 3,230 Bosch systems, which are the most exposed signatures during this analysis.
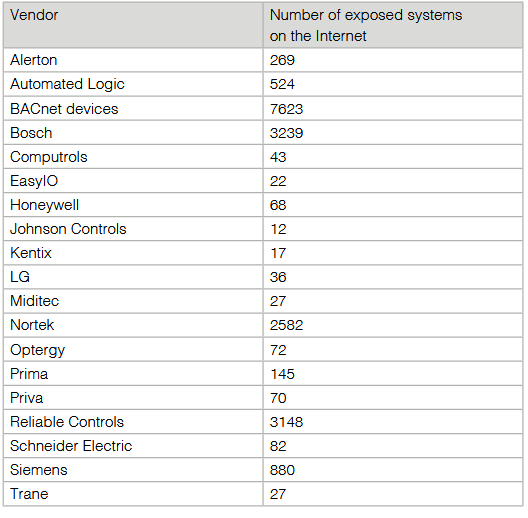
SOURCE: Applied Risk
Activities that hackers could do when exploiting these flaws include:
- Remote locking and unlocking of doors and entrances
- Control of physical access to restricted areas
- Denial of service
- Handling alarms and surveillance systems
- Temperature control, boilers, air conditioning, blinds, gas readings, etc.
All these systems are exposed on the Internet, so anyone who knows where to look will surely be able to find them. As digital forensics specialists mention, these systems are commonly implemented in multiple structures, including government buildings, hospitals, banks or private companies. In case of exploitation, hackers could take full control of one of these facilities for malicious purposes.
In their report, the experts say that all the systems analyzed contain the same vulnerabilities and security errors, an indicator that, in addition to the presence of security flaws, the administrators of these systems make the same errors, which further exposes these systems.
In addition to revealing vulnerabilities and management errors that affect the integrity of these systems, Applied Risk digital forensics specialists issued a number of recommendations for end users, vendors, and administrators of systems can identify these security risks and mitigate the possible exploitation of these failures. According to the experts of the International Institute of Cyber Security (IICS), the full report includes a proof-of-concept for a remote code execution attack on the affected products, which proves that the risk is real across multiple facilities around the world.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











