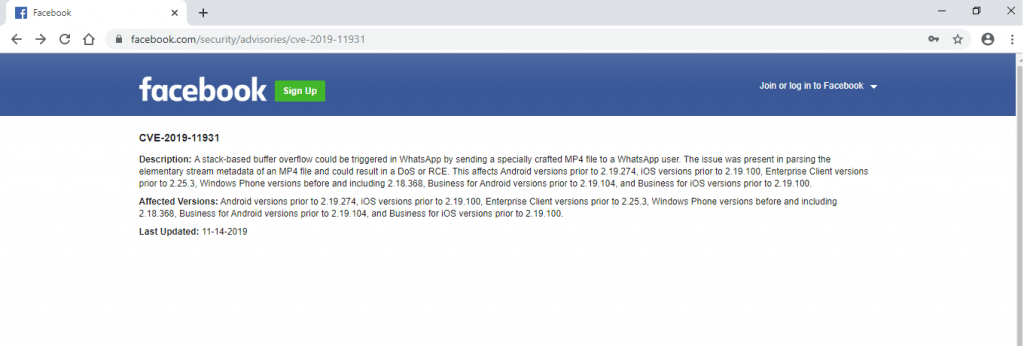
Again, WhatsApp has become the target of malicious hacker attacks. According to web application security specialists, a critical vulnerability has been revealed in the instant messaging service that, if exploited, would allow a threat actor to hack a smartphone using only a malicious mp4 file to generate denial of service conditions (DoS) or even remote code execution (RCE).
The vulnerability, tracked as CVE-201911931, is present in the video encoder output, which is converted to video file metadata; it is mentioned that the flaw exists due to incorrect analysis of elementary metadata from mp4 files, which allowing to triggering the error.
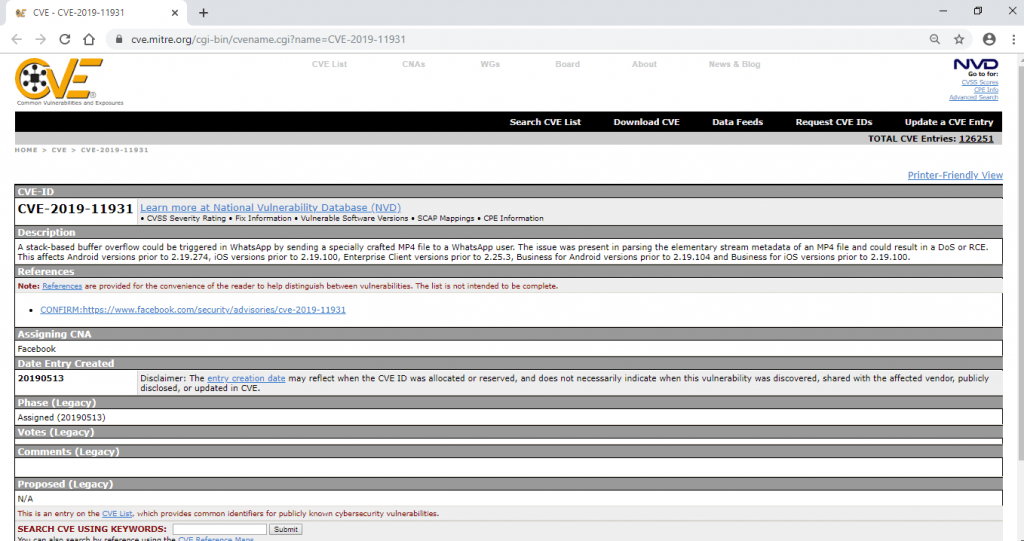
It is not yet clear whether the targeted user should download and play the video or if the vulnerability is exploited just by receiving the file, although it is a fact that the flaw affects the versions of WhatsApp and WhatsApp for Business for iOS, Android and even for Windows Phone.
The bug report, presented by Facebook, mentions that: “It is possible to trigger a stack-based buffer overflow by sending a specially crafted mp4 file to an application user”. Web application security specialists mention that the latest versions of WhatsApp already include the fix of this flaw, plus they remind users that the vulnerability was rated as critical, so it is necessary that they update their app to the latest version available.
Does this flaw really affect WhatsApp users?
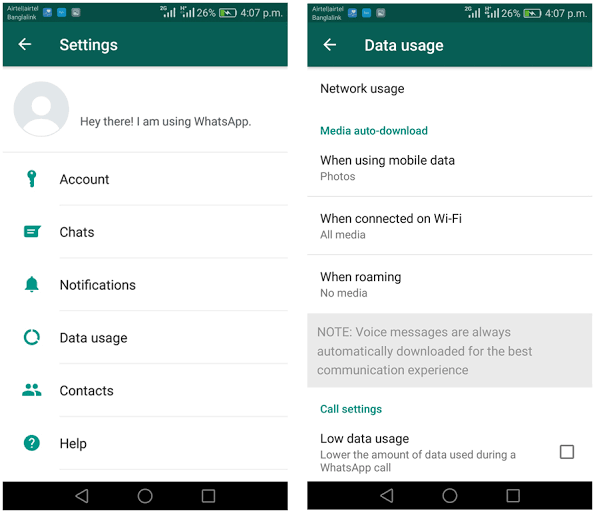
There are multiple reasons why this vulnerability could be exploited in the wild. The main reason is that many users rely to the automatic download of the multimedia content received through the app. According to web application security specialists, the main recommendation to avoid the exploitation of this flaw is to disable automatic download of photos and videos in the account settings.
Although there are no known cases of exploitation, Facebook decided to release the report so that WhatsApp users were aware of its existence and updated as soon as possible. Users are invited to enter their corresponding app store and install the latest version of the app.
In case your app is already updated but you want to run some tests, web application security specialists from the International Institute of Cyber Security (IICS) recommend downloading an older version from external app stores or third-party websites; in this case, make sure these platforms are secure.
Privacy scandals have been a constant on WhatsApp over the past year. A few weeks ago, it was revealed that the advanced spyware known as Pegasus had been used to violate the privacy of thousands of journalists and activists around the world, with WhatsApp being the main path of infection of this malware, allegedly developed by the Israeli security firm NSO Group.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











