When a database is left exposed on the Internet, two things can happen: the companies that control them detect the flaws and secure them, or instead, hackers could find them first, exposing millions of data. When the second case is presented, data protection experts mention that it is common for the exposed information to end up in some dark web forum, as is the last reported case, involving more than 21 million accounts belonging to the Fortune 500 list companies.
To be accurate, these exposed databases contain a total of 21, 040, 296 accounts (including usernames and passwords). Over 90% of these passwords have already been cracked by hackers, so they are available in plain text.
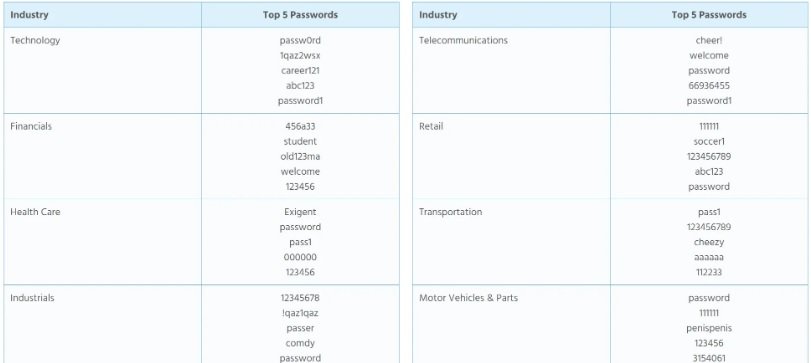
Most of the hacked accounts belong to companies in technology and financial sectors, and it has been found that a significant portion of the databases is updated, as the older accounts would have been created less than twelve months ago, data protection experts report.
Using machine learning tools, researchers were able to eliminate fake leaks, duplicate registrations, and default passwords, discovering a total of 4.9 million authentic accounts. The rest of the leaked records are fake, outdated, or belong to previous data breach incidents.
A worrying finding is that regardless of the type of company or the range of employees, the passwords used are extremely weak. “More than 40% of the compromised accounts used the company name (with minimal variations) as a password,” the experts mention.
Out of the samples collected by experts, it is possible to conclude that retailers are much more prone to the use of weak passwords than other sectors; however, security in other sectors is not much better, as almost half of the passwords exposed could have been cracked in less than a minute.
Data protection experts from the International Institute of Cyber Security (IICS) mention that data from this massive leak will soon be available for consultation on the specialized platform Have I Been Pwned, where concerned users they will be able to check the status of their business email accounts.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











