Ethical hacking specialists have detected that a dark web site dedicated to the sale of stolen payment card data has included among its offer a list with at least 1.3 million new credit and debit cards extracted from several India-established banks.
Security firm Group-IB reported the incident for the first time, stating that the list was found on the popular dark web forum Joker’s Stash. According to the experts, the database operators are asking $100 USD for each payment card record, which could grant threat actors profits for up to $130 million USD.
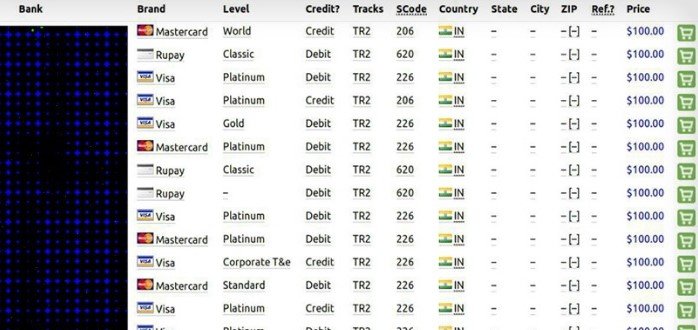
So far, specialists in ethical hacking still do not know the source of the stolen information, although one possible explanation is that hackers may have collected these millions of records at points of sale or ATMs infected with some variant of malware designed for data theft. Unfortunately, the evidence collected indicates that the information is legitimate, so the banking institutions and responsible authorities have already been notified.
After analyzing the list shown at Joker’s Stash dark website, the specialists concluded that almost 99% of the exposed payment cards were issued by banks in India, while the remaining minimum portion appears to be tied to some banks in Colombia. Previous reports from ethical hacking specialists claim that Joker’s Stash is one of the world’s leading illegal sales forums, counting on at least 49 servers and more than 500 domains associated with the operators of the sales forum.
At Joker’s Stash it is not only possible to purchase compromised payment card records, but personal records, social security numbers and even contact information of millions of people, obtained in multiple data breaches are also available.
According to experts from the International Institute of Cyber Security (IICS), this dark web forum uses a blockchain-based domain name (DNS) system, which helps users stay anonymous, so a plugin is required to access a domain name system (DNS) version of the site via the top-level .bazar domain of Emercoin, the DNS used by site operators.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











