A group of information security specialists from the security firm WizCase (complete report here) has reported the finding of multiple data leaks from medical websites and software solutions around the world. The compromised information includes prescriptions, diagnoses, Social Security numbers and, in many cases, full names and addresses.
All databases were found unsecured, as experts not even needed a password to access the information, leaving millions of patients and medical staff members exposed.
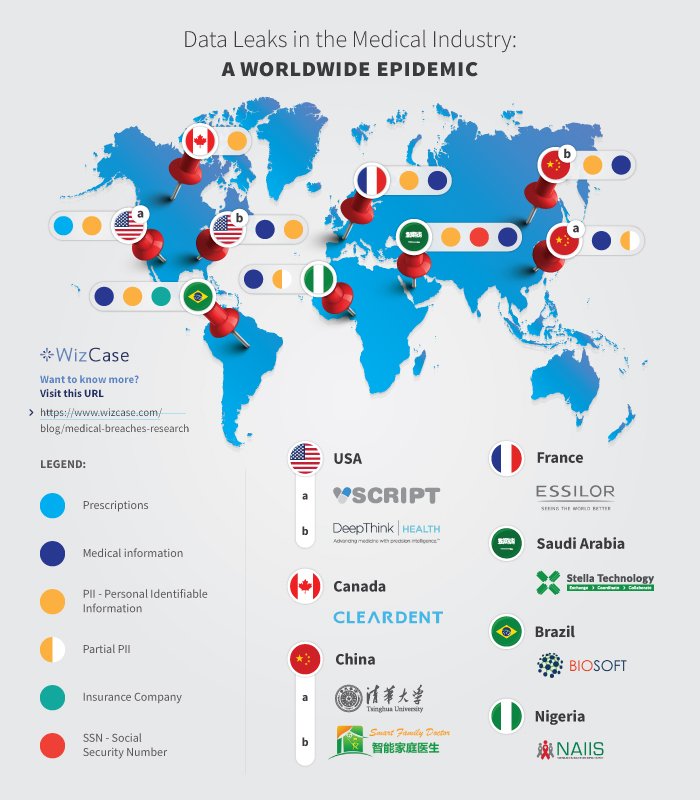
The research leader Avishai Efrat discovered nine unsecured medical databases in countries such as Saudi Arabia, Brazil, Canada, China, the United States, France and Nigeria. Although they vary in each particular case, in general the details presented include:
- Full names
- Phone numbers
- Home address
- Email address
- Workplace
- Social security numbers
- Diagnostics
- Medical prescriptions
- Clinical test results
With regard to the companies operating these databases, the information security experts were also able to establish a detailed profile, described briefly in the following paragraphs.
- Saudi Arabia: Health-applying software company Stella Technology exposed more than 4 GB of information belonging to nearly 300k patients, including multiple personal details, on an Elasticsearch server
- Brazil: The database exposed in Brazilian territory, operated by the company Biosoft Medical Software, has 3 GB of information, equivalent to almost 1.2 million records belonging to patients throughout the country
- Canada: In the case of Canada, the company involved is Dental Software, with its ClearDent solution. In this case, an 8 MB database, equivalent to nearly 60k exposed patients, was discovered on an Elasticsearch server
- China: Tsinghua University Faculty of Medicine exhibited a database of 650 MB, equivalent to 60k patient records from Tsinghua University Hospital and other medical centers in various Chinese cities
- United States: Deep Think Health, a company that provides a machine learning platform for the medical industry, exposed a 2.8 GB database, representing more than 700k records of patients and medical staff on an Elasticsearch server. The most sensitive cases involve the exposure of diagnoses and treatment of cancer patients
- France: The involved company in French territory is Essilor, dedicated to the design and manufacture of ophthalmological devices. The compromised database consists of 5.7 GB, including details of thousands of patients, optometrists and employees from various areas of the company
- Nigeria: All results of the 2018 HIV/AIDS Indicators and Impact Survey were exposed in the African country. In total, the database consists of 1 GB, equivalent to more than 88 thousand records.

According to information security experts, because most are services provided by third parties, it is likely that the people affected do not even know that their data is in the hands of these companies. Whether we are aware or not, the security risks are real; these risks include widely known practices such as phishing, extortion email campaigns, phone and email fraud, and identity theft.

The intervention of external companies hinders the process of containment of such incidents; however, information security experts from the International Institute of Cyber Security (IICS) advised any user potentially affected to follow some simple advice. It is necessary to ignore any suspicious or linking emails to external sites, as massive phishing campaigns are already being deployed using the exposed data. Also, remember that personal information should never be disclosed via email, as no legitimate company requests personal data by this means. Continuous monitoring of your online accounts and bank statements is also a good alternative.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










