Fake text or fake SMS or fake message are the biggest threat industry is facing. All applications require an account to keep your settings, app usage. While registering through applications, they generally require mobile number for registering & returns with OTP (One Time Password). You might encounter many times you receive unnecessary OTPs from different recipients. Many times attacks/ spammers uses SMS bombing techniques to irritate or disturb their targets.
SMS bombing is a technique of sending fake messages on any mobile number. SMS bombing uses an script containing SMS Gateway APIs. It uses SMS APIs of different SMS gateways. According to ethical hacking researcher of international institute of cyber security SMS bombers utilizes different gateways. SMS gateway providers gives services of forwarding, routing & storing incoming messages. For sending messages using SMS gateway connect with SMSC centers.
Some popular SMS Gateways are :-
- You can also check free APIs & you can use in creating sms bomber scripts. Go to : https://rapidapi.com/
- Nexmo SMS Messaging
- Twillo SMS
- TeleSign
- D7SMS
- Telnyx
- MessageBird
- Click Send (IntelTech)
SMS Bomber Application :-
- There are different tools which are used in SMS bombing. BombitUP is an application used in SMS bombing.
- Download application : https://www.bombitup.net/
- Download & install BOMBitUP_v4.03.1.apk
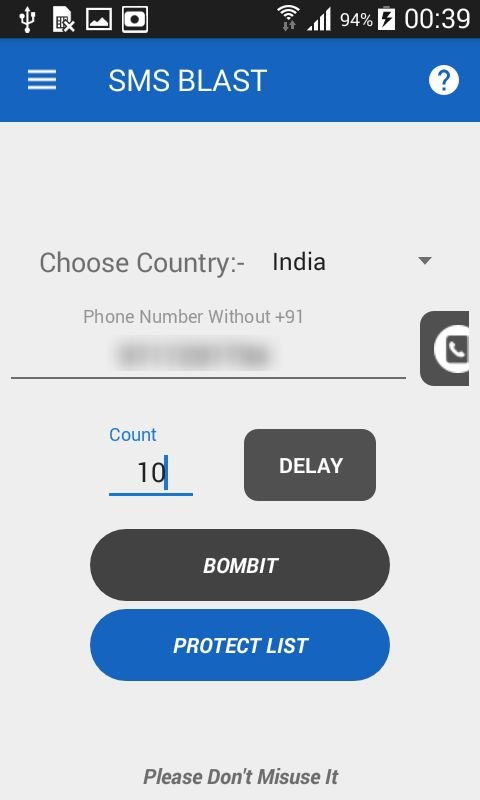
- Enter target mobile number & then enter no. of count messages you want to send.
- Click on BOMBIT
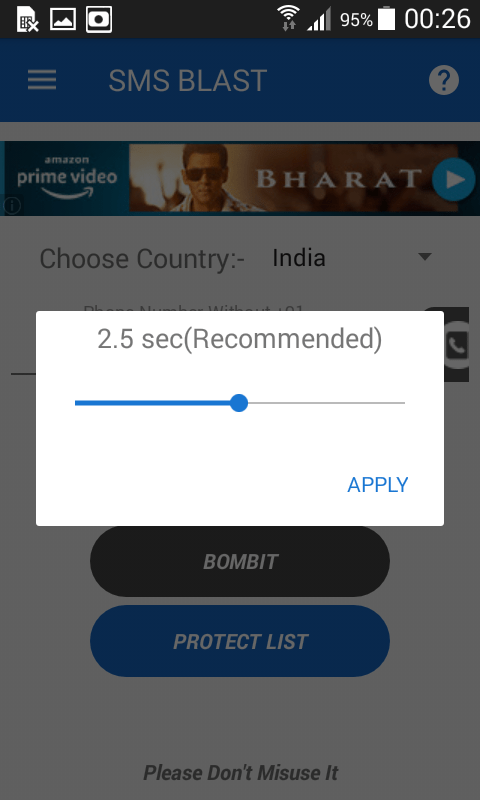
- You can also setup delays in no. of seconds. By default is 2.5 second.
- It depends on the bombit server. But most of times messages are sent on time.
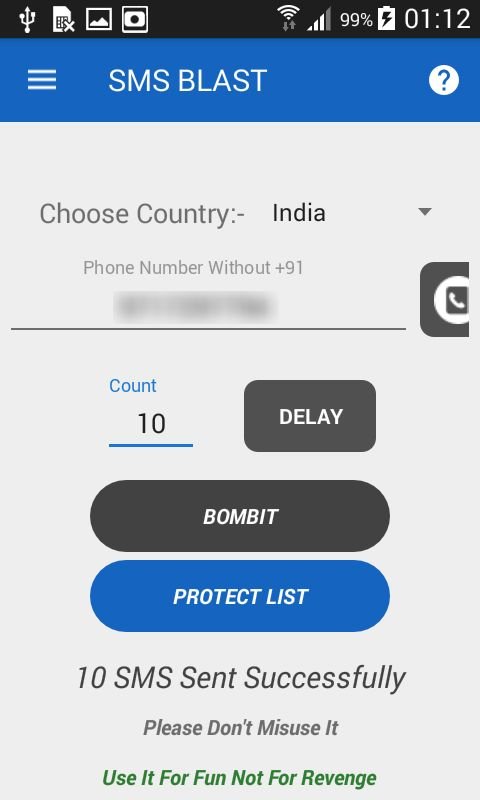
- Click on Bombit
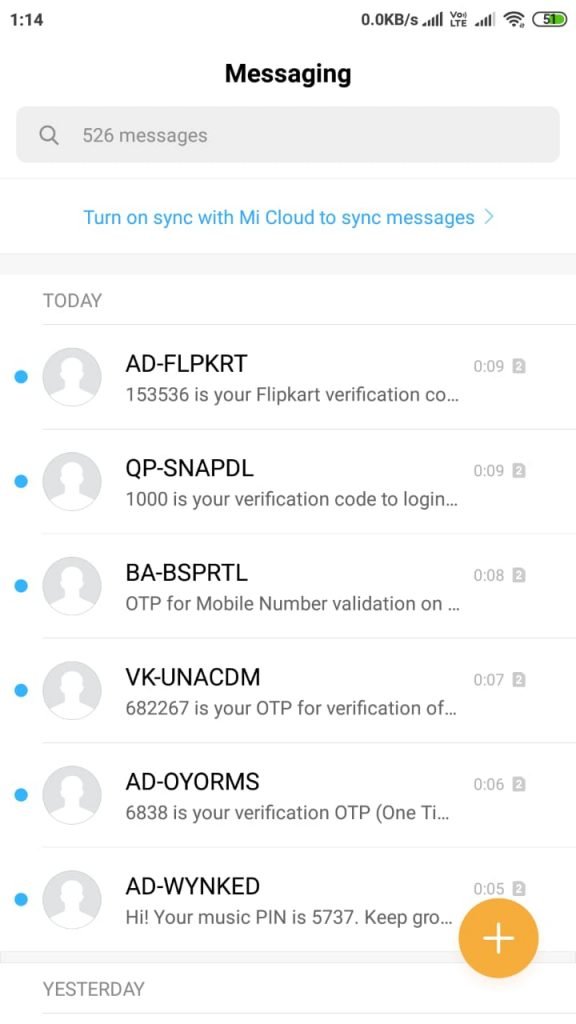
- Above screenshot shows that 10 messages has been sent. Below shows received messages.
- Above you can see received messages on the target number.
You can checkout the SMS Bomber practical :-
As per the ethical hacking researcher of International Institute of Cyber Security there are many more ways to send fake SMS or fake messages to do social engineering attacks

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.