Despite the security controls set on the platform, malware can sometimes be spotted into apps available on Google Play Store. Specialists in digital forensics of security firm TrendMicro have detected an adware, identified as “AndroidOS_Hidenad.HRXH”, present in 85 popular apps available on this platform. According to reports, the malware has been downloaded more than 8 million times.
Obviously the presence of this malware, designed to show ads to the user in an intrusive way, violates the current advertising rules for the applications available in the Play Store, because it acts even with the standby screen.
The ads displayed by this malware even prevent those affected from using their smartphones properly, blocking the screens until the ads end, which can take up to five minutes. According to digital forensics experts, in this way adware operators can generate advertising revenue in very short periods of time, which makes this method of attack relatively profitable; similar tactics have been detected before.
Popular apps that feature millions of active users, such as Super Selfie Camera, Cos Camera, Pop Camera and One Stroke Line Puzzle are among those affected by the AndroidOS_Hidenad.HRXH adware. The full list of affected applications, provided by TendMicro, is available here.
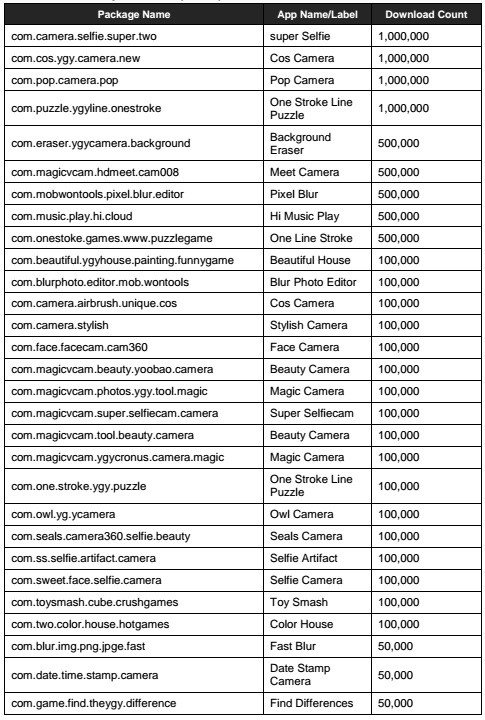
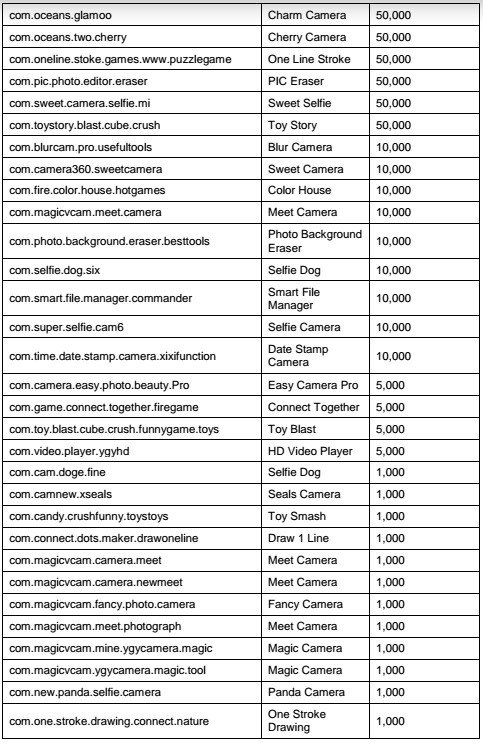
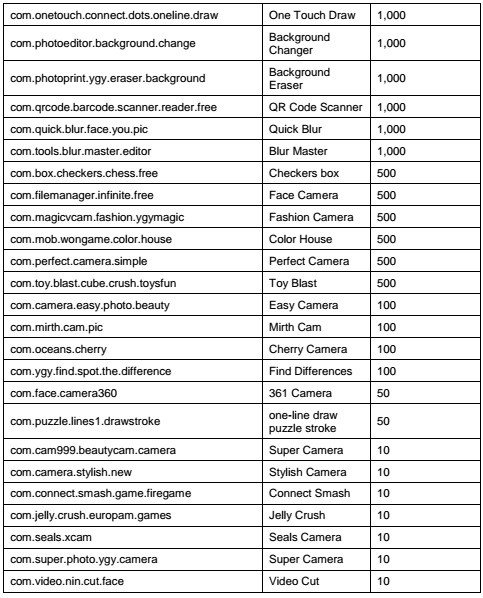
A prominent feature of this malware is its ability to hide from Google security teams, application developers and antivirus tools. In addition, after its installation, the malware waits about 30 minutes to clear its icon and replace it with a shortcut, which also complicates its uninstall process, so the user has to go straight to the settings menu of their smartphones, digital forensics specialists mention.
After receiving the report, Google proceeded to remove from the Play Store the 85 apps infected with this adware. However, the company, in addition to application developers, recommends that users take some additional security measures to prevent such incidents from happening again.
First of all, users are advised to upgrade their Android operating system to Android 9 Pie or Android 8 Oreo version if possible, as this adware only works on devices with versions earlier than Oreo. In addition, Android 8.0 and later versions by default ask users for permission to create shortcuts to apps; installing an antimalware tool on your smartphone is also a highly recommended measure.
Unfortunately this is not the first time this kind of malware is found in apps hosted on the Google Play Store. A few months ago, a digital forensics investigation by the International Institute of Cyber Security (IICS) revealed the presence of an adware in more than 50 Android apps; the malware, known as “TsSdk”, would have been downloaded about 30 million times before being removed from the platform by Google. Detected in two different variants, TsSdk developers focused especially on infecting video and photo edition apps, music players and some little complex games.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











