Facial recognition is becoming a common use tool, assure experts in ethical hacking. From its simplest applications (as an authentication method, e.g.), to the most complex (airport security), the growth in the use of this technology has exceeded any expectation.
While it offers some advantages, this technology also has a negative side, closely related to people’s privacy. As the use of facial recognition progresses, private companies, government agencies, and even malicious actors have greater capabilities to track people regardless of their intentions, so their application is truly privacy invasive.
Ethical hacking specialists believe that, due to this remarkable growth, it is vital for technology users to have at least basic notions about the operation, usage and applications of facial recognition technology. Having this information will give us new perspectives on the advancement of this technology, its capacity for inference in our daily lives and the measures that can be implemented to control it.
What is facial recognition?
To begin with, it’s worth remembering that facial recognition is one of several methods of “biometric identification“, which is basically a combination of hardware and software with the ability to examine a person’s physical characteristics to distinguish them from any other individual. Other forms of biometric identification include fingerprint or retina scanning and even voice recognition.

Biometric identification systems take an image to contrast it with images stored in a database and look for matches to determine the identity of the individual. According to ethical hacking experts, in the case of facial recognition, the process can be divided into three parts: detection, faceprint creation and identity verification.
After the image is captured, the recognition software scans it and then searches for matches in a real environment, a crowd or a mall, for example. In these cases, surveillance cameras will feed to facial recognition software, which will begin identifying each face.
Once the system has identified all possible faces in a security cam feed, it will perform a thorough analysis of each one with image reorientation and resizing techniques. In case the software manages to fully capture a face, a record of it will be created, sometimes called a ‘faceprint’. This record works in the same way as fingerprint identification, as facial features all put together compose a unique face.
Among the elements that the system analyzes highlight features such as eye shape, eyebrows, nose shape, scars, among others, although experts in ethical hacking say that a fundamental element is eye analysis. Some accessories, especially sunglasses, can make it difficult to be detected by one of these systems, functioning as anti-facial recognition tools.
Facial recognition tools
As we have already mentioned, the most important application of these systems is surveillance; private companies know this and have focused on developing increasingly sophisticated recognition tools. An example is the Japanese company Fujifilm, which seeks to break into this market considerably with the launch of the SX800 surveillance system.

This is one of the most advanced long-range surveillance cameras; featuring a 40x optical zoom, the SX800 has been designed for security activities at border points and large commercial facilities. According to the company, this camera has a lens with an equivalent focal length up to 1000 millimeters; in simpler words, it is possible to focus the plate license of a car located over 1 kilometer (0.6 miles) away using the SX800.
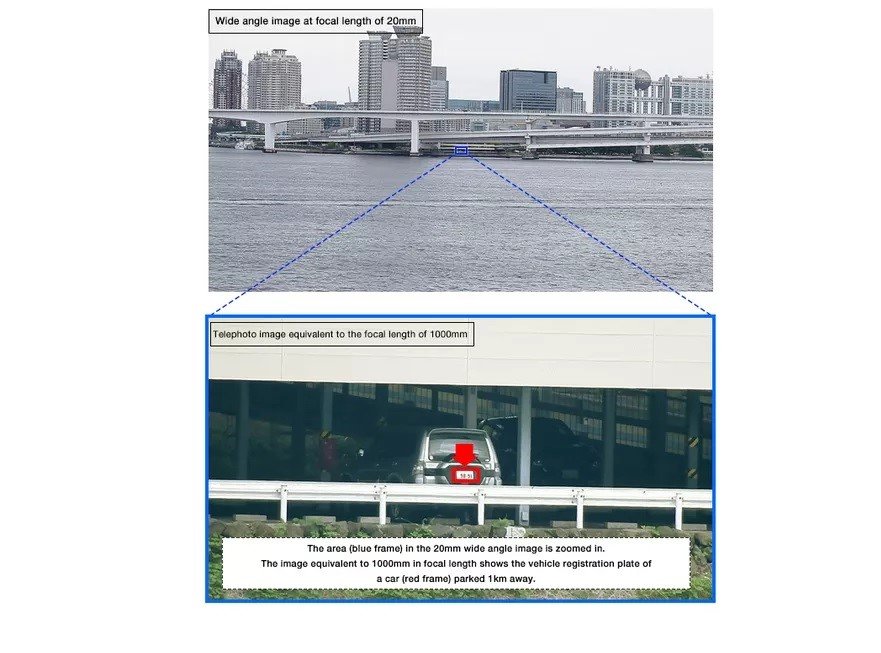
Although there are cameras with a much more powerful zoom on the market, ethical hacking specialists claim that this tool remains one of the best options by including some additional features for security and surveillance implementations. For example, the SX800 features an autofocus function of up to 0.3 seconds and an image processing engine to eliminate the effect produced by rain, mist or other factors; in addition, the image processing engine allows you to record a fully viewable video using the maximum zoom, even at night.
According to specialists from the International Institute of Cyber Security (IICS), advanced tools such as this facilitate surveillance activities at critical security points, such as airports and other points of entry to certain territories; this technology can help consolidate some of the most ambitious security and surveillance plans for governments like the United States, where President Donald Trump has expressed his intention to store a record of every person who enters or leaves American territory.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











