An unusual incident has brought a serious headache to the British authorities. According to web applications security specialists, about a week ago, an unidentified hacker or hacker group compromised the Twitter account of the London Metropolitan Police, better known as Scotland Yard. Hackers posted some tweets with messages against policemen.
Most of the tweets posted by hackers refer to the British rapper Digga D, whose real name is Rhys Herbert. The rapper was imprisoned a year ago along with four gang members because they planned to attack another gang armed with baseball bats and machetes. Herbert was only 17 at the time. “Release Digga D,” one of the messages mentions.
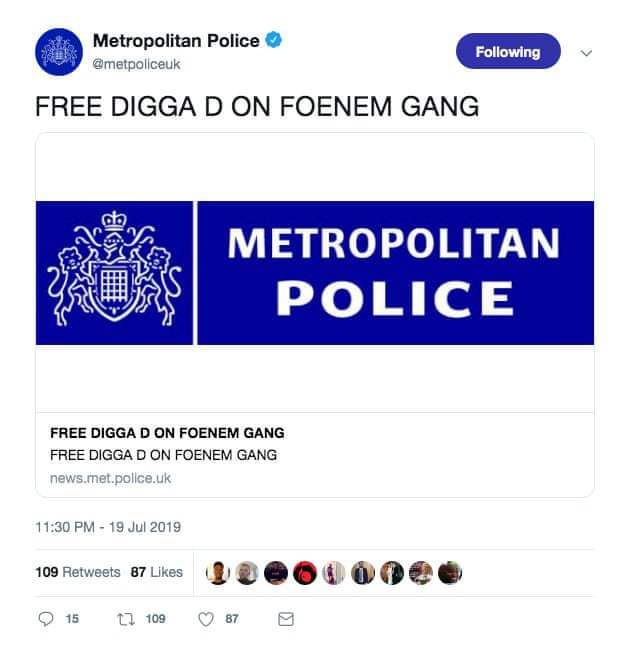
Roy Smith, Chief of Police in London, said: “We are aware that our Twitter account has been compromised; our web application security experts are working after hours to eliminate messages posted by the attack operators and ensure that this does not happen again. Please ignore any postings from this account until further notice.”
As he’s used to, U.S. President Donald Trump took this incident as an opportunity to criticize the work of the authorities in London, specifically attacking Mayor Sadiq Khan; “The streets of London will never be secure with that incompetent mayor,” Trump posted on his Twitter account.
Web application security experts reported that some hours later the London Police website had also been hacked, altering the content of the news feed and the institution’s email. Scotland Yard says this is not an attack on its IT infrastructure, as only the police online press office was affected. This service is provided to the London Police by MyNewsDesk, which automatically distributes the content generated by Scotland Yard to its website and Twitter account.
According to the specialists from the International Institute of Cyber Security (IICS), the authorities regained access and control of the compromised services last Saturday night.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











