Pentesters/ security researchers uses many devices for testing their hacking skills or finding new bugs in any web application. Mostly users uses Linux different flavors for testing purposes. But mostly Kali Linux is the most popular OS which is used by pentesters and it is also the part of ethical hacking & mobile hacking courses offered by International Institute of Cyber Security. We will show you a method to create any android device into pentesting or hacking device.
Before rooting any device we need to understand boot process of android :-
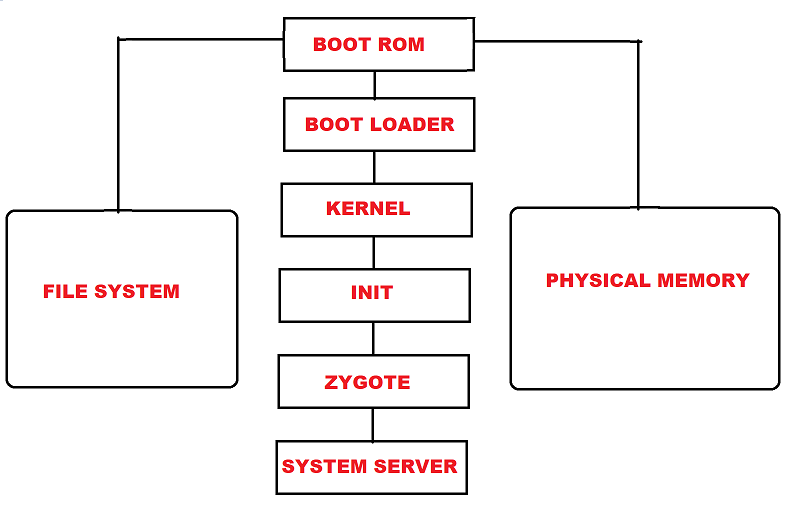
- Boot ROM – This is the initial phase of booting process which runs on startup. Boot ROM start its process from defined location. Then boot ROM executes boot loader.
- Boot Loader – Bootloader contains information to find system kernel. Boot Loader executes before android OS. Boot Loader detects RAM & loads program to run kernel.
- Kernel – Once Kernel boots, Kernel executes in memory to load drivers & initializes the process table. After finishing system setup by kernel.
- Init – Init is the first process which runs script /init.rc. This script is responsible for the initial set up of system. Init setups all services related to linux system boot.
- Zygote – Zygote boots with system. When Zygote launches app_process it creates Dalvik VM & calls Zygote main() method. It triggers a fork & creates a clone to itself. It creates an exact clean Dalvik VM with preloaded classes & resources. Zygote enables it code sharing accross Dalvik VM to consume the startup time.
- System Server – As Zygote loads all the required Java classes. System server loads native library known as android_servers. Android server provides interfaces to all functionalities. After setting native services, android server will create an thread which will start remaining services in system. Each service will run an separate Dalvik thread in system server. Once system services are running. Android will complete its boot process.
- Activity Manager – In the last activity manager will launch home screen with apps & icons.
Install Kali Linux on Rooted Android mobile.
Requirements:-
- Computer running Windows 7/10
- Tools – Odin for flashing ROMs
- Mobile – Samsung Galaxy Grand Neo Plus I9060
- Rooting – Kingoroot PC Version
Rooting Samsung Grand Neo Plus :-
- For testing we will use Samsung Grand Neo Plus I9060. Before installing we will root the device.
- There are various methods of rooting android devices. Mostly users use automation ways to root android mobiles or tablets which are taught in mobile hacking courses offered by iiCyberSecurity.
- We have tried popular applications like Kingoroot. But the app was fail to root the device. So we tried using Kingoroot PC version. Download Kingoroot from : https://www.kingoapp.com/
- Connect your mobile with USB cable. Kingoroot will automatically detect your mobile. As you have installed samsung drivers. Kingoroot will automatically detect your phone & ask you for rooting your device.
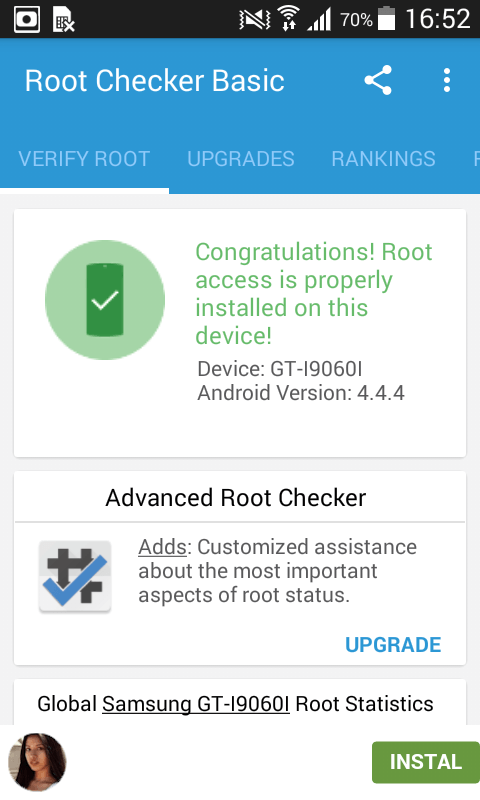
- Click on root and kingoroot will root the device.
- After rooting install root checker app & you can see that device has been rooted.
- After rooting, for installing Kali Linux. Download three applications :
- Complete Linux Installer – https://play.google.com/store/apps/details?id=com.zpwebsites.linuxonandroid&hl=en_IN
- Terminal Emulator – https://play.google.com/store/apps/details?id=jackpal.androidterm&hl=en_IN
- After installing all applications. Download Kali Linux images from : https://sourceforge.mirrorservice.org/l/li/linuxonandroid/Kali%20Linux/
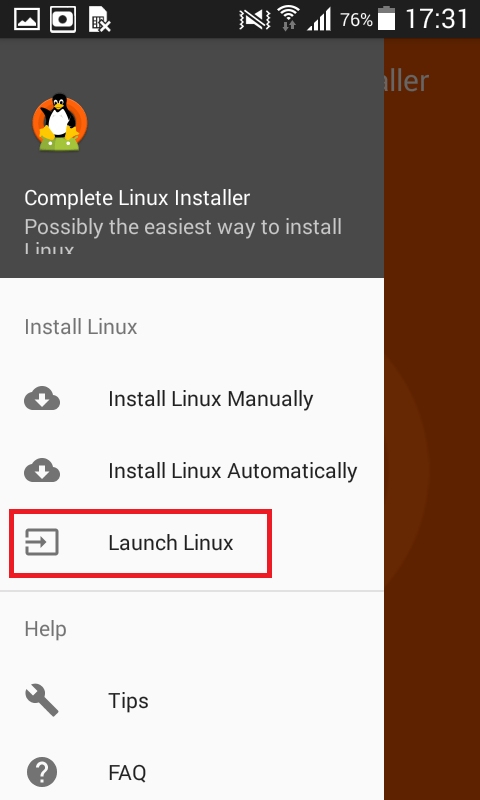
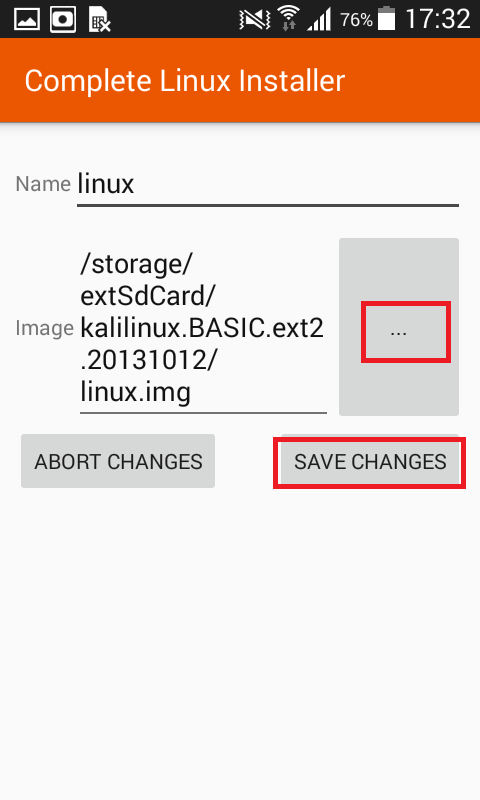
- Extract the image, copy the image to external memory card. Now open Complete Linux Installer application. Go to : Launch Linux
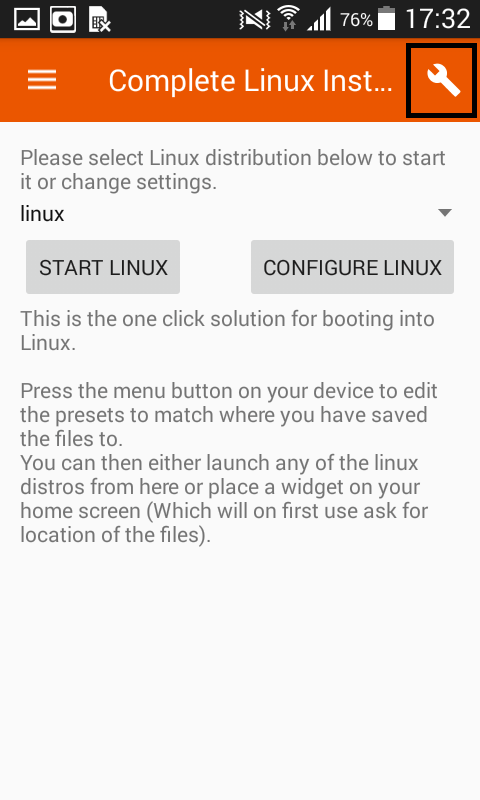
- Click on settings icon.
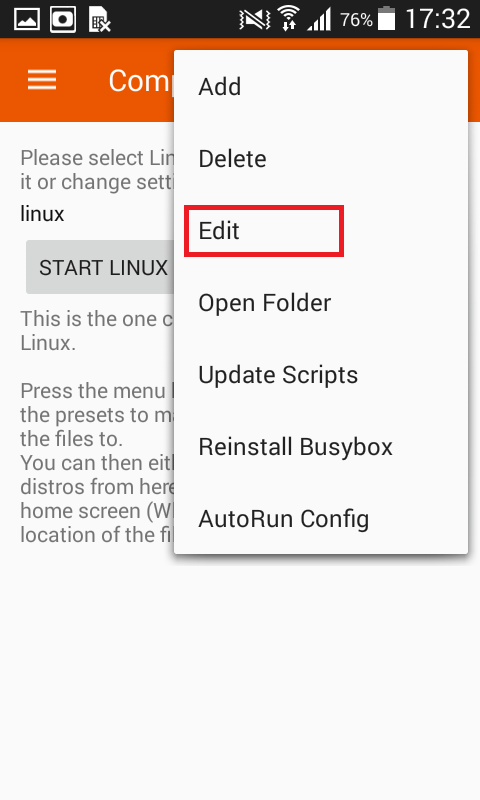
- Go to edit.
- Select Kali Linux image.
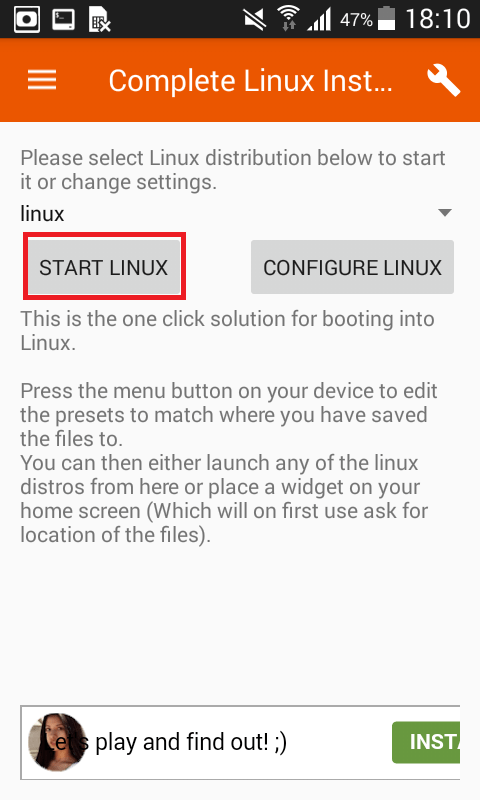
- Then click on Launch Linux.
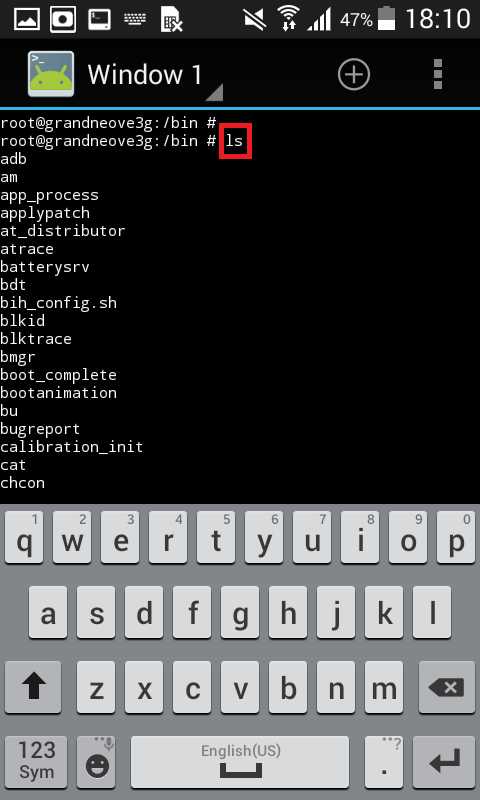
- As you click on launch linux. Terminal Emulator will open for running Kali Linux.
- Above you can see that linux has started.
- This same process is the part of the ethical hacking course offered by International Institute of Cyber Security
Install Kali Linux on NON ROOTED Android Device :-
Kali Linux Installation –
- For testing we have used Xiaomi Redmi Note 4.
- For installing Kali Linux without rooting your device. You need to download three android applications.
- CommandBot ; https://play.google.com/store/apps/details?id=org.connectbot&hl=en_IN
- VNC Viewer : https://play.google.com/store/apps/details?id=com.realvnc.viewer.android&hl=en_IN
- UserI_And : https://play.google.com/store/apps/details?id=tech.ula&hl=en_IN
- After downloading all required applications. Open UserI_And.apk Here you need to configure UserI_And for using Kali Linux.
- UserIAnd provides various Linux distributions for installing. So we will continue with Kali Linux.
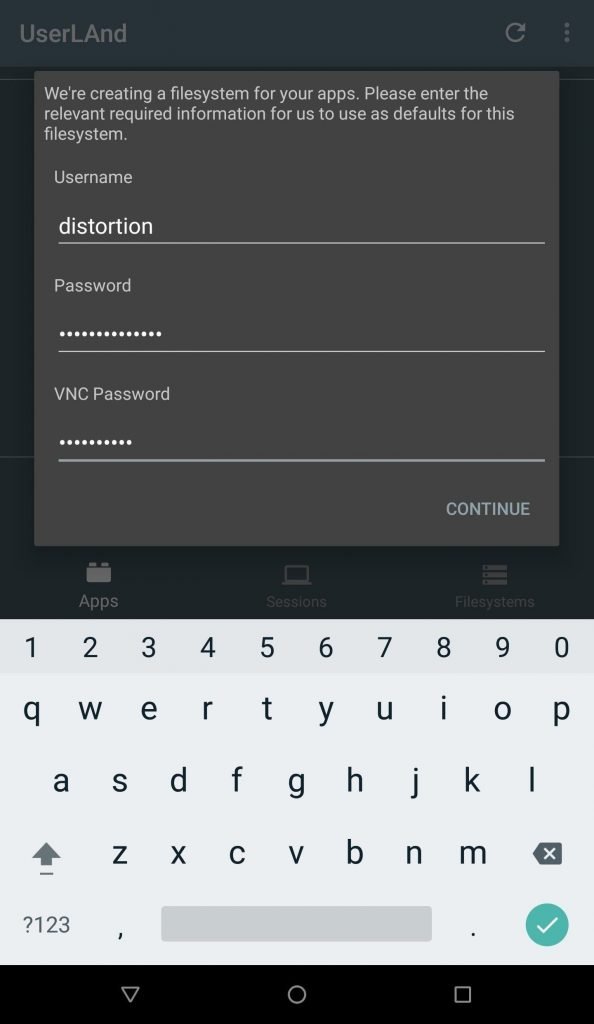
- Click on Kali Linux,
- Enter any username & password of Kali Linux & VNC password of your choice, we have used distortion username. Make sure enter password between 6 to 8 characters for VNC viewer.
- After then Commonbot will start. And here you have to enter Kali Linux login password.
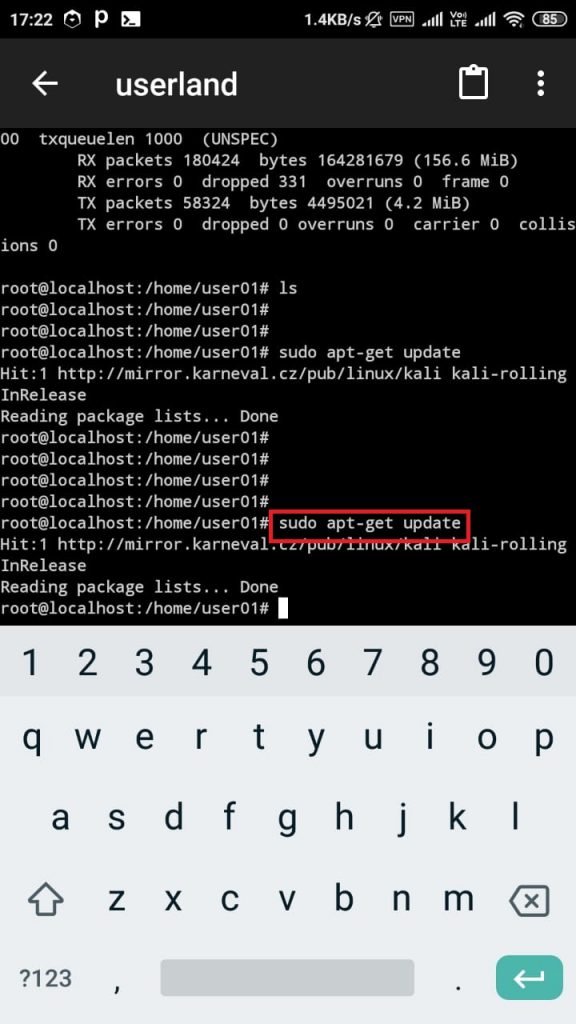
- Then type su
- Type sudo apt-get update. So from here only basic features will accessible in Kali Linux. For accessing all the features of Kali Linux. You have to install all the required tools.
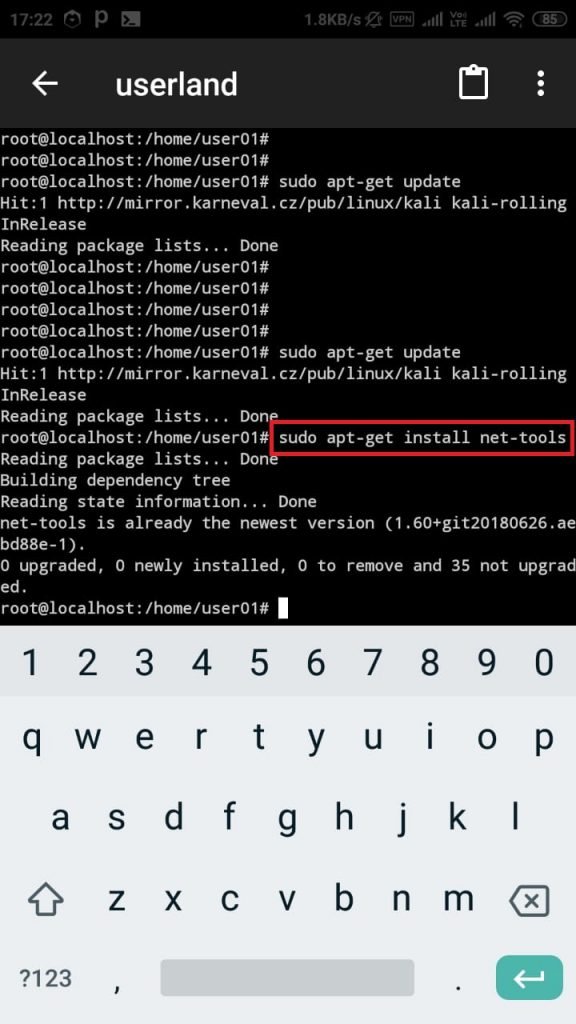
- For checking ip. You need to install net-tools. For that type sudo apt-get install net-tools
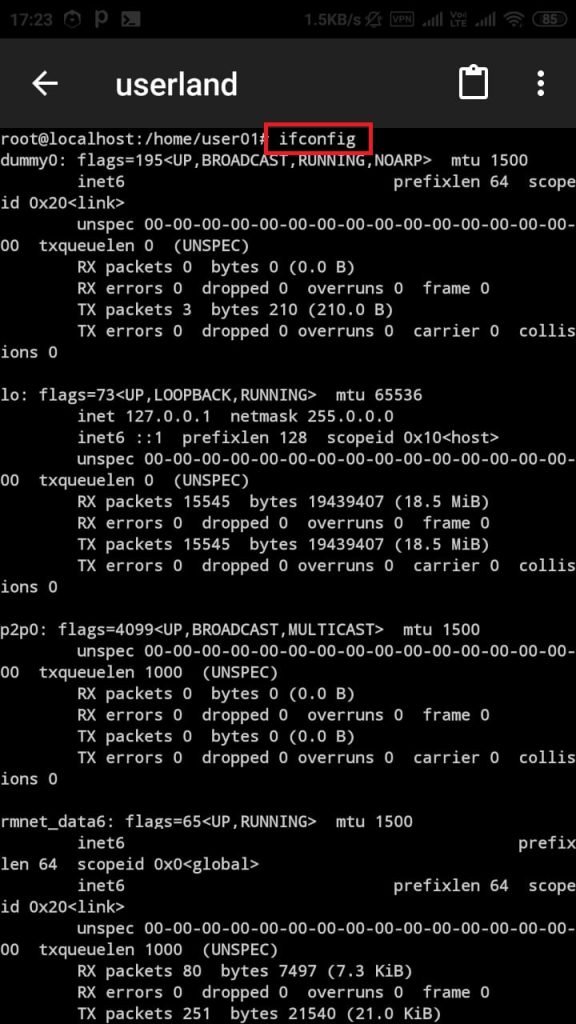
- You can see that net-tools has installed. Type ifconfig.
- Above screenshot, shows ip address of local device. This shows that Kali Linux has been installed.
- Researcher of International Institute of cyber Security (iiCyberSecurity, IICS) are trained to keep things on the go, like linux on mobile.
Install stock ROM recovery if the rooting of the device failed.
Requirements:-
- Computer running Windows 7/10
- Tools – Odin for flashing ROMs
- Mobile – Samsung Galaxy Grand Neo Plus I9060
- Rooting – Kingoroot PC Version
Stock ROM Recovery :-
- For changing stock ROM. Downloaded ROM for Samsung Galaxy Grand Neo Plus I9060 mobile from: https://drive.google.com/file/d/0B5h2nhCP9mgaemRYLUdhNXN6XzA/view
- And flash ROM using Odin tool. Download Odin from : https://odindownload.com/
- First install samsung USB drivers. Download driver from : https://www.samsungusbdrivers.net/2017/02/samsung-galaxy-grand-neo-2014-usb.html
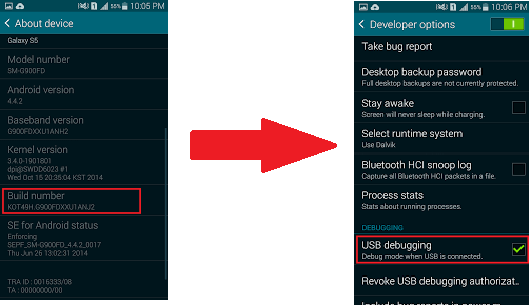
- Turn on debugging options. For that enable Developer options. To enable developer options. Go to < Settings < About Phone. Simultaneously click on Build Number. This will enable developer options.
- Then go to back settings. And head to Developer options. Open developer options & enable USB debugging.
- After then go to download mode by following below screenshot.
- It will open download mode of the mobile.
- Then install drivers. After installing drivers make sure that your computer is detecting your mobile automatically or else install below.
- https://www.samsungusbdrivers.net/2017/02/samsung-galaxy-grand-neo-2014-usb.html
- Open Odin as administrator.
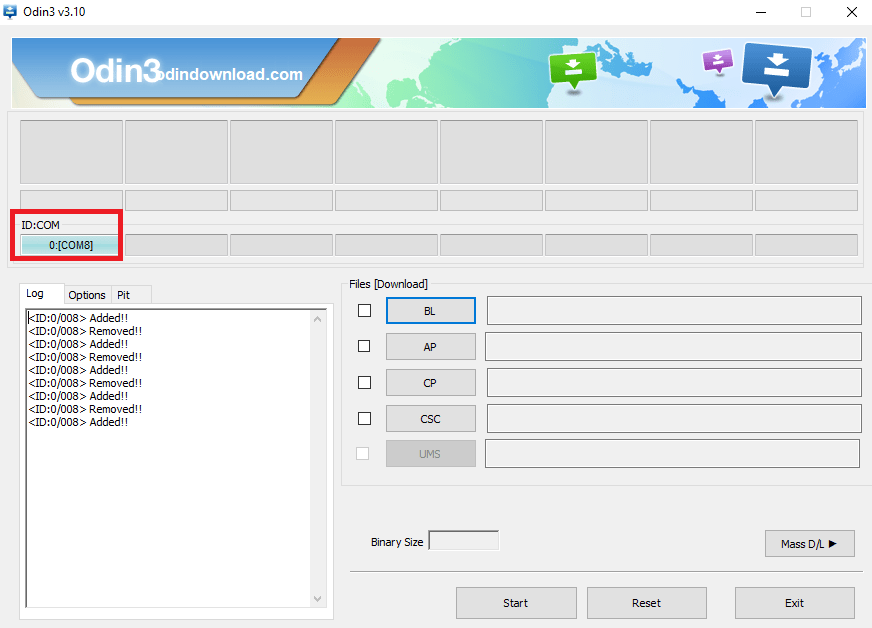
- Connect Your mobile. As you connect your mobile. It will display under ID:COM
- Below you can 0:[COM8] means that mobile has connected. It refers the mobile ID.
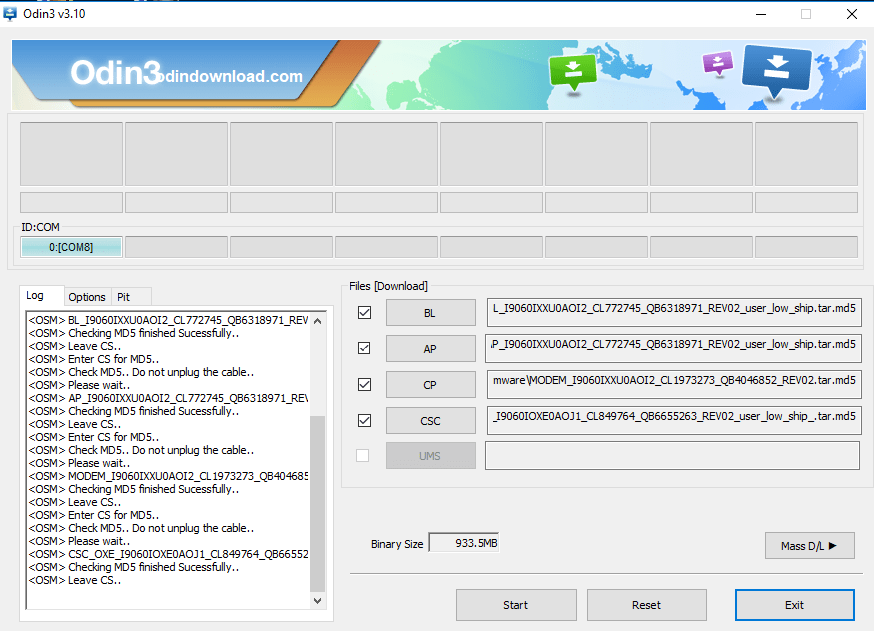
- After connecting mobile. Open BL, AP, CP, CSC files in odin.
- BL – Bootloader is used to flash into mobile. As it hold information about system kernel & has to execute before android OS.
- AP – Application Processor – This area contains ROM which flashes into the device.
- CP – Core Processor – Here it act like a modem for mobile. CP install required files for the device.
- CSC – Consumer Software Customization – CSC contains geographical region details, carrier branding.
- browse and select all the above file as shown below:
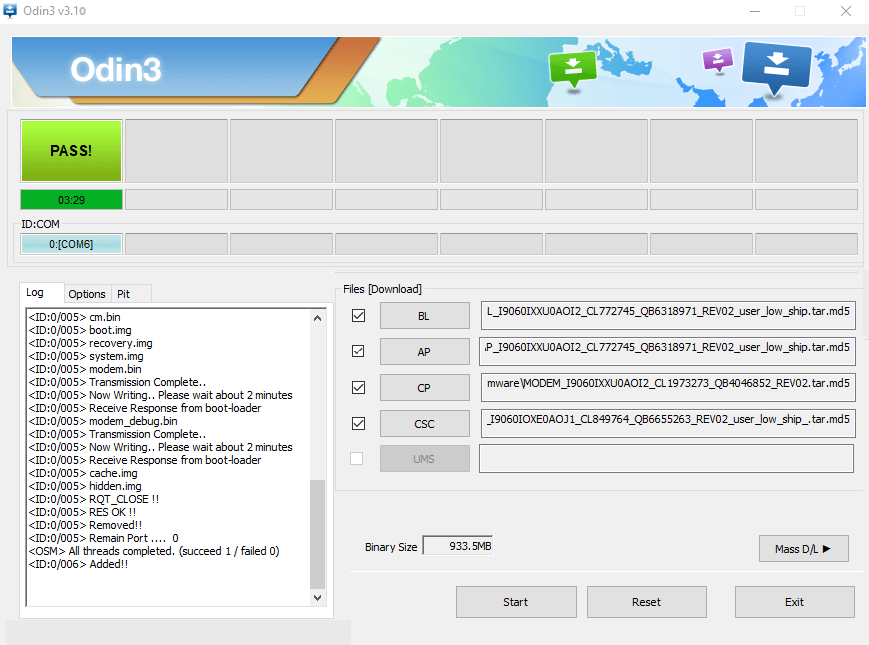
- Click on start. And Odin will flash the files into your mobile.
- Above screenshot shows that ROM has flashed into mobile device. Now unplug your device & start by pressing lock button.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.