
A Reddit user found a way to bypass advertising on the platform with a tool available on the latest MacBook Pro
A user of the Reddit platform called “u/BiggerBadgers” discovered how to skip YouTube ads on an Apple’s MacBook Pro. According to network security and ethical hacking specialists from the International Institute of Cyber Security, this is possible thanks to the touch bar featured in these devices.
Network security experts are still unclear if this has to be called “vulnerability”; although some have mentioned that this is really the only utility function they have found in the Apple touch bar.
The Reddit user added that it was possible to skip an ad designed to be viewed completely, as YouTube does not include the option to skip it after a few seconds. Regardless of the type of ad the user wants to skip, the process is the same: it must be played towards the end of the line that marks the duration of the ad in the touch bar to skip it.
This trick is only functional in the Safari browser, in the ‘Application controls’ configuration of the touch bar. The touch bar setting must be maintained as the default.
For ads that can be skipped after a few seconds, you can see how long you have to wait to skip it, and a timeline of the video should appear on the touch bar.
With your finger, tap and drag the timeline indicator to the right, but don’t drag it to the end. Then release your finger and click the “Skip” button. It is important that you stop dragging the flag before you get to the end of the ad timeline, the network security experts mention.
Then simply click on “Skip”.
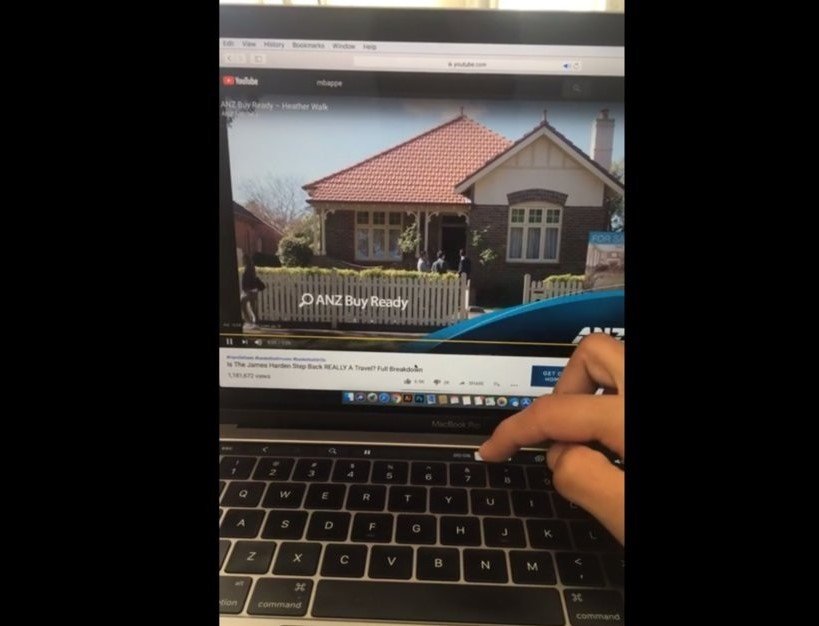
The Reddit user claims he was able to skip one of the ads that YouTube shows his users forcibly and cannot be skipped.
This is what experts commonly call a workaround, so YouTube or Apple could correct this feature at any time.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











