
The popular Google Translate service is used as a tool to deploy cyberattacks
Network security and ethical hacking specialists from the International Institute of Cyber Security reported the emergence of a phishing campaign in which attackers use the Google Translate service to extract Google and Facebook access credentials from their victims.
The cybersecurity specialist known as Larry Cashdollar discovered that a hacker, or group of hackers, is conducting a new phishing attack that takes advantage of Google Transalate. This malicious campaign targets Facebook and Google accounts and, according to the expert, is much harder to detect when using the mobile version of a browser.
Attackers send phishing emails to potential victims, presenting them as “security alerts” generated by Google to report access to user accounts from an unknown Windows device; after posing the scenario to the victims the email shows a button with the phrase ‘Consulting activity’.
When this button is clicked, the victim is redirected to a Google Translate session that opens the phishing page, shown as a Google login page.
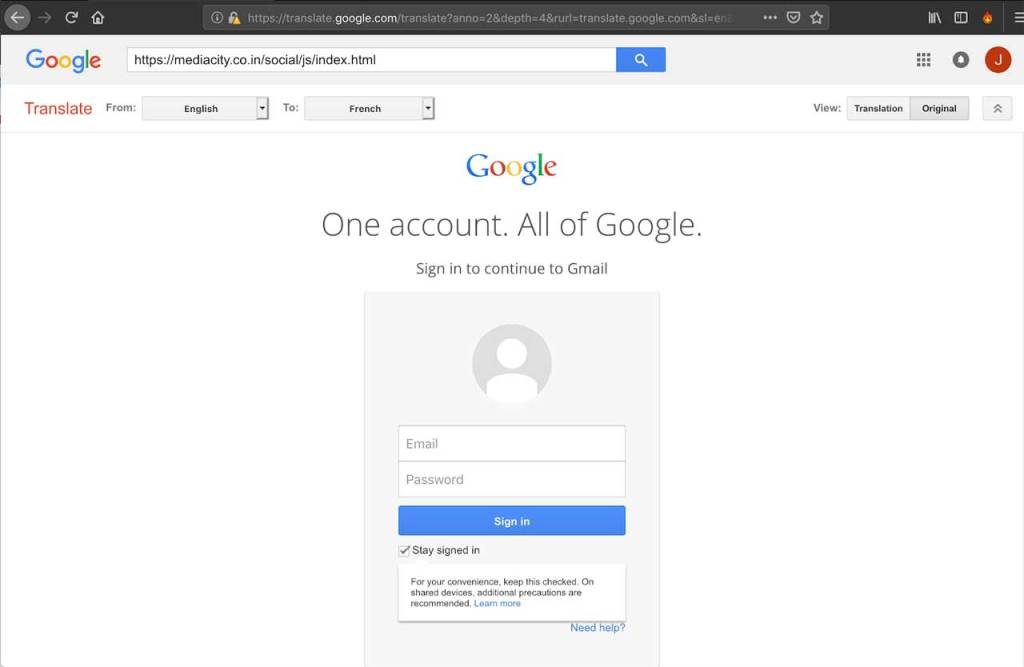
The network security expert stressed that users of the desktop version of the browser could detect this attack at first glance, as the translator’s bar is visible on the home screen. However, this is very difficult to detect in mobile browsers.
“The use of Google Translate has a variety of purposes, but the main one is that the URL contains a legitimate Google domain,” mentions the network security specialist. “Although this tactic might be successful in some cases, especially on mobile devices, it is virtually impossible for a desktop user not to see the Translator’s toolbar on the home page,” added Larry Cashdollar.
In successful cases, once the victim enters their Google credentials on the phishing page, they will be sent to the attacker by email, thanks to a malicious script. If the attacker receives the user’s Google accesses, they will perform a second attack trying to get the Facebook access credentials.
The expert mentions that the design of the phishing page for Facebook is very poor and is not properly optimized for mobile devices, so it was very easy to detect the attempted fraud. “Some attackers pay more attention to details than others; in this case, the scam was easily detected when checking the page; Still, this does not mean that phishing is not a risk faced by every day individuals and organizations of all kinds”, concluded Cashdollar.
Experts recommend paying attention to details before getting carried away by messages like this. Reviewing the sender, the URL and the structure of the messages received are simple but helpful measures to mitigate this kind of risk.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











