Information gathering is not an easy task. In many phases, pentester has to go through many tools to gather many information, ethical hacking professors assure. Today we are talking about tool called SHED. Which extract information. This tool can be useful in extracting useful information from the .net program. In many phases of pentesting, if the pentester is having a .net coded software. Pentester can easily open the software using shed. Shed gives an overview of which information is stored and executed. For showing you we have tested this tool on Windows 10.
According the ethical hacking researcher of International Institute of Cyber Security Shed comes handy in initial phase of malware analysis.
- Download tool from github : https://github.com/enkomio/shed/releases/tag/2.0.0
- Unzip the shed tool using any unzip software.
- Then open CMD as administrator. For opening type cmd in start menu and right click on cmd icon then click on run as administrator. Go to location where you have unziped the shed. Type cd C:\Users\Username\Desktop\Shed
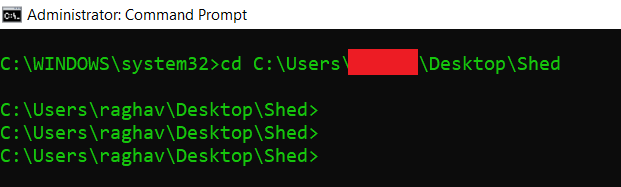
- Type dir
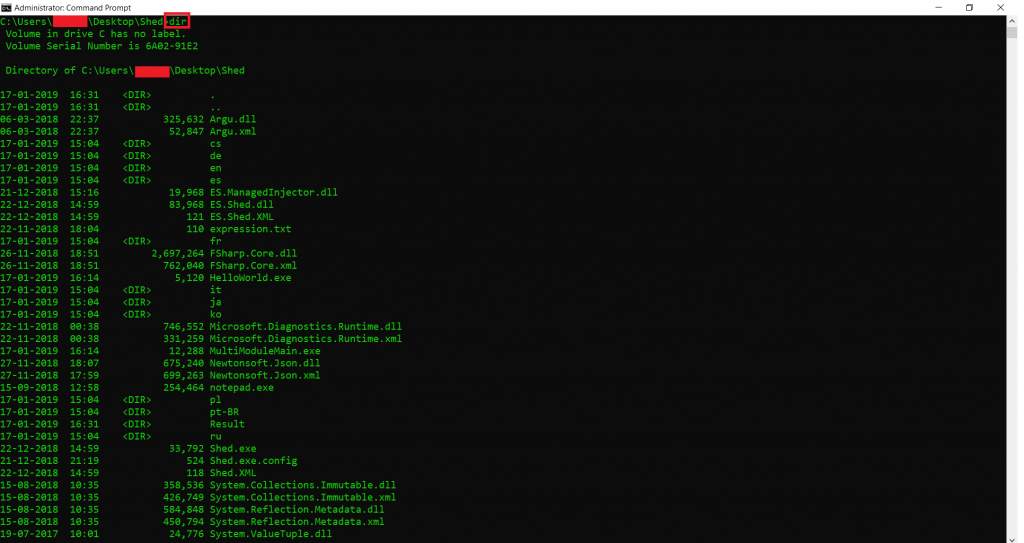
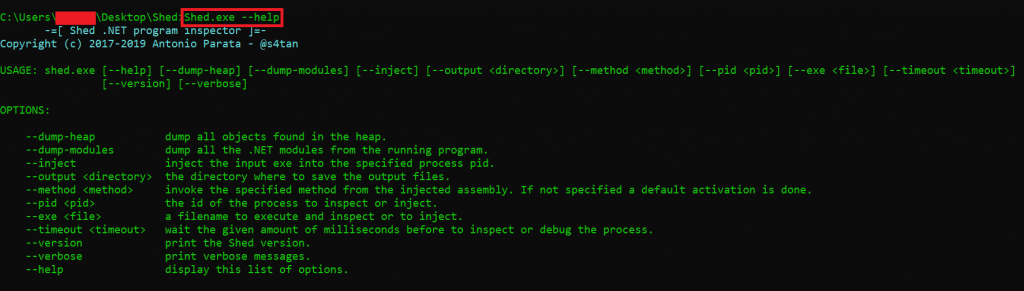
- Type Shed.exe –help
- Then for scanning .net exe files. You can use exe files provided in github : https://github.com/enkomio/shed
- After downloading unzip the file. Open the project in Visual studio. You must configure to open this project. As this project reuqired .net framework 4.7.2.
- If required .net framework is not installed. Then go to : https://dotnet.microsoft.com/download/thank-you/net472
- After downloading and installing .net framework 4.7.2. Open Visual Studio 2015 or any version of visual studio with required framework.
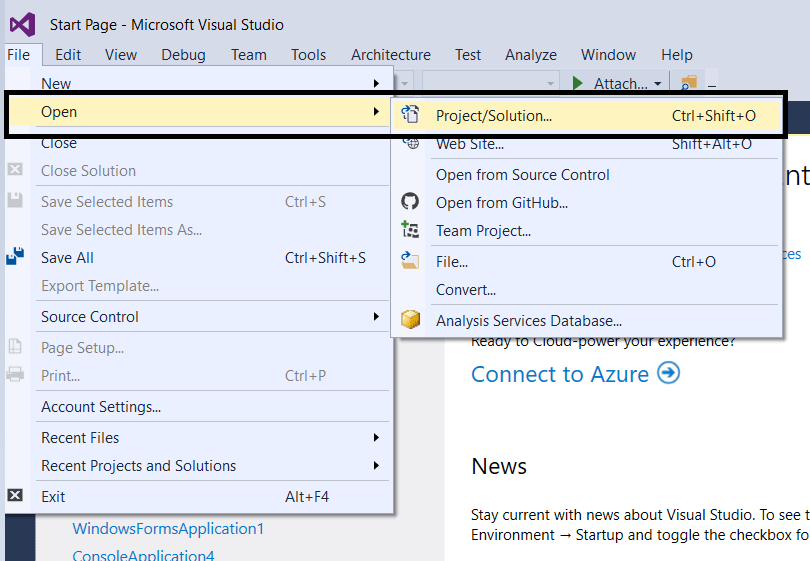
- And open project as shown below.
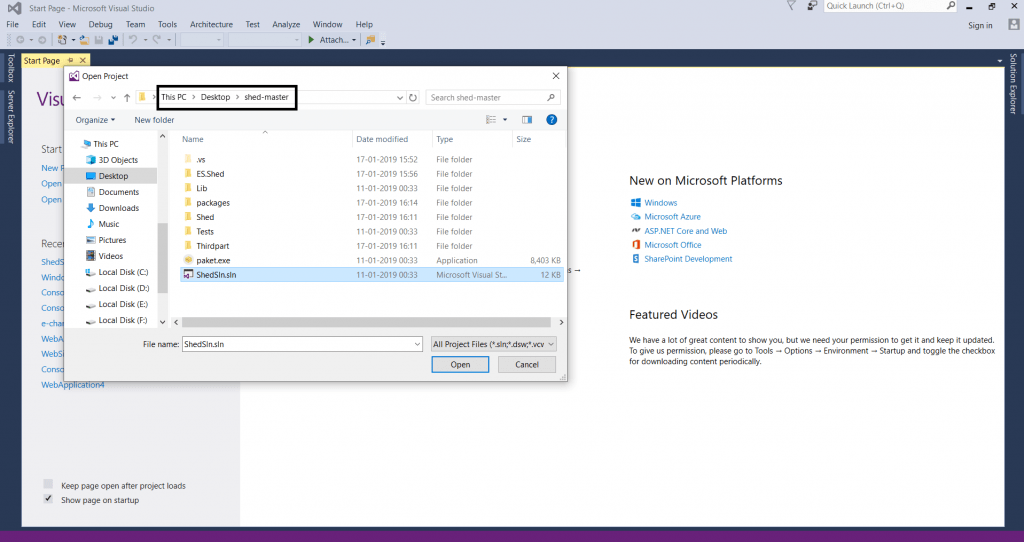
- After opening the program as shown below.
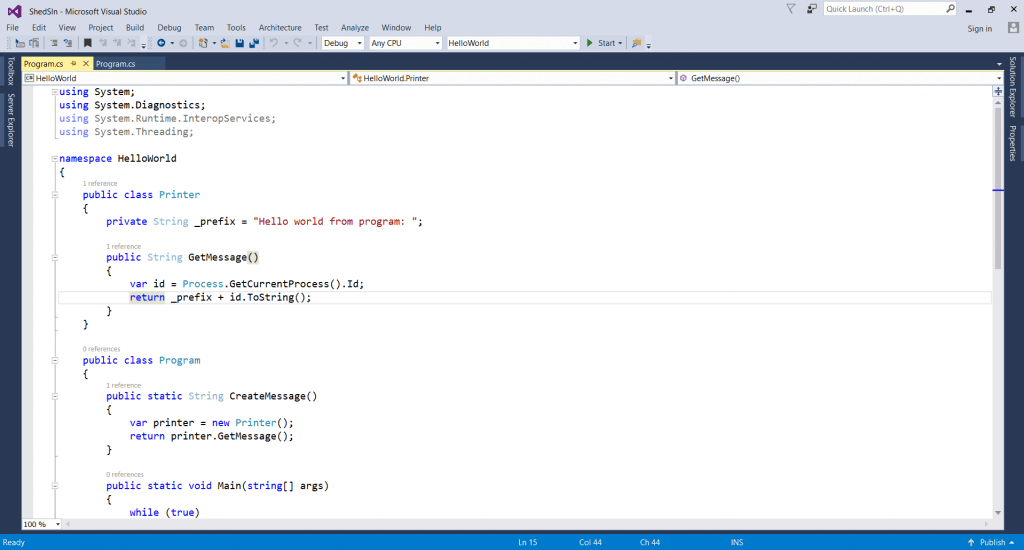
- For checking if the .net framework is installed.
- Choose any program (HelloWorld).
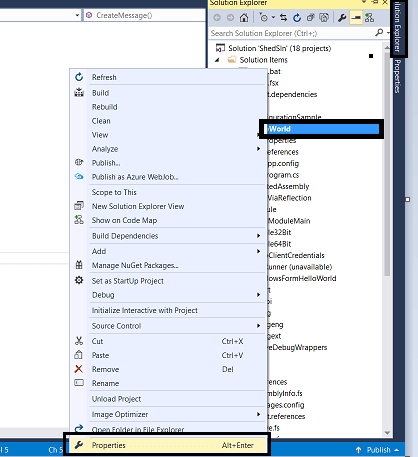
- Right click on program. Go to properties. Check .net framework as shown below.
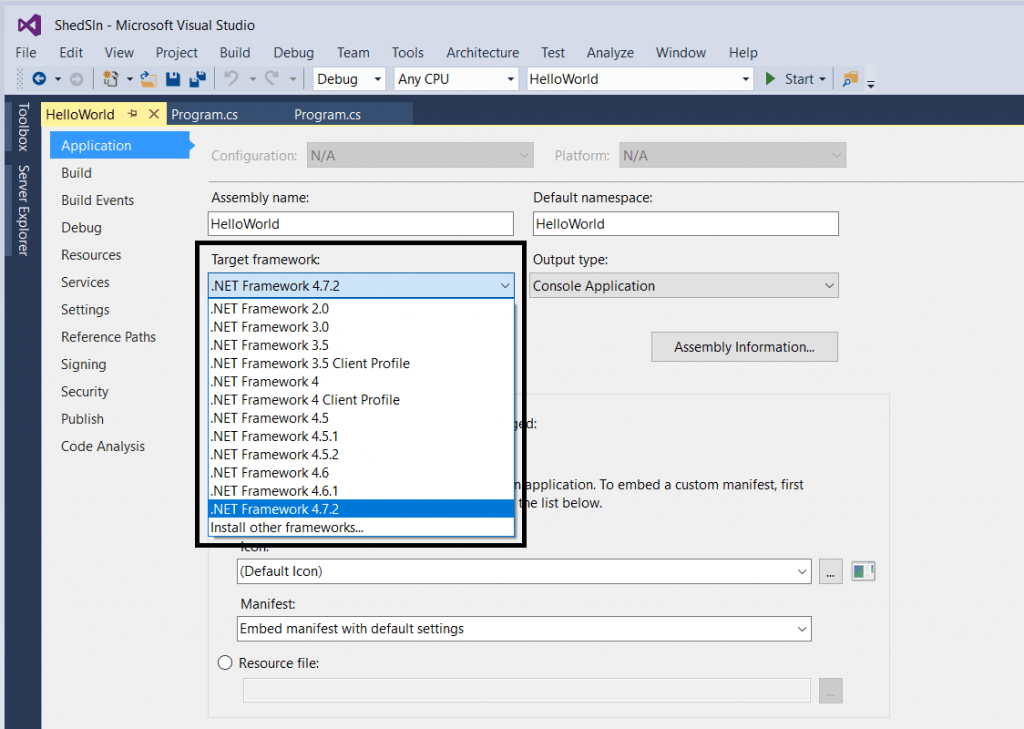
- Then open code and then click on build or press F6. After building an exe will be created.
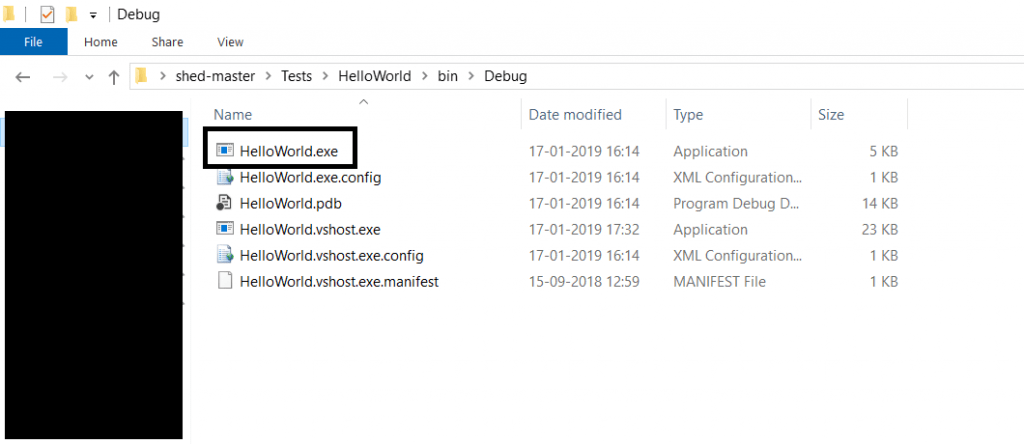
- And now go to debug location in the software. Go to C:\Users\Username\Desktop\shed-master\Tests\HelloWorld\bin\Debug
- Copy the exe to the shed location (C:\Users\Username\Desktop\Shed ) then come back to cmd where shed was opened.
- Go to opened CMD of shed.
- Type Shed.exe –exe HelloWorld.exe
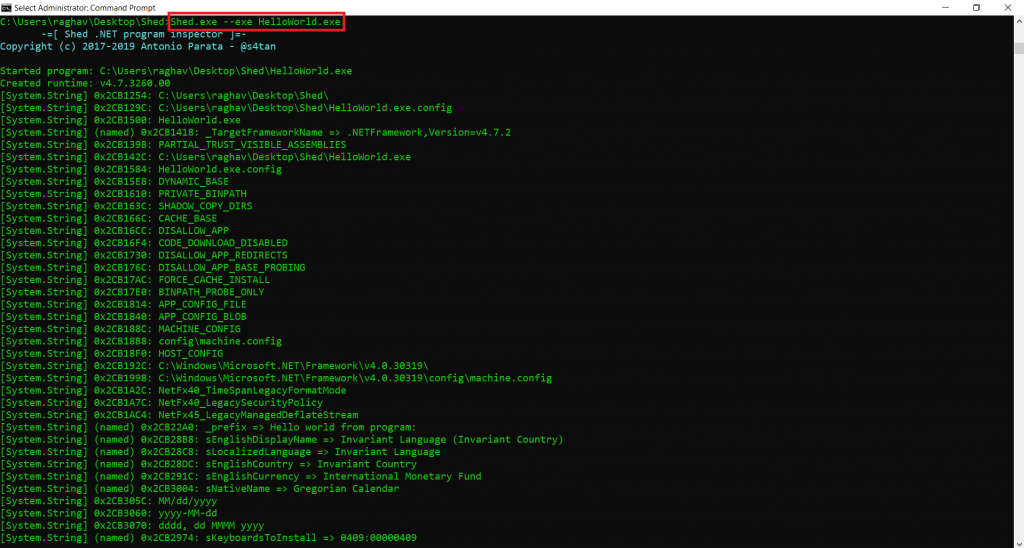
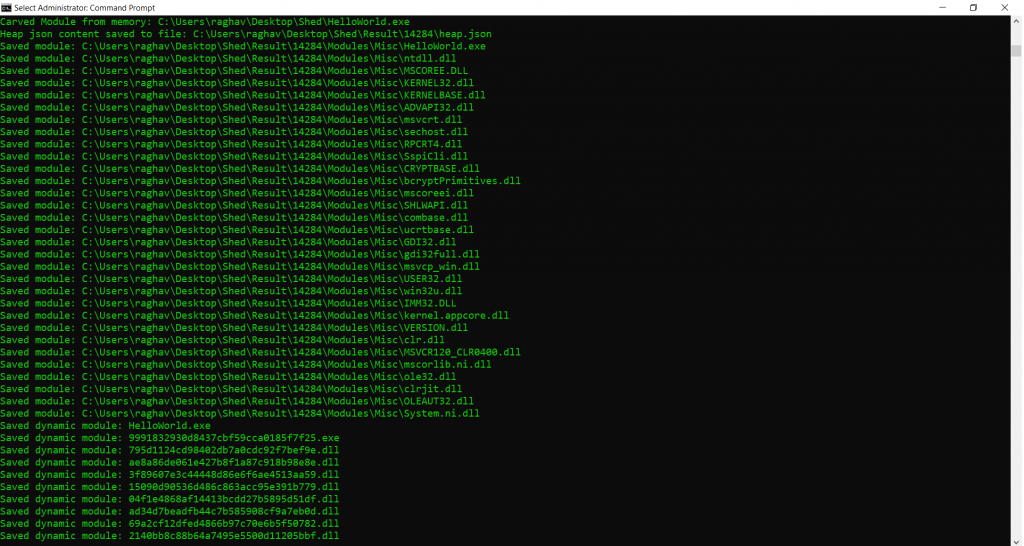
- The above query shows the string values of the .net program. It also shows the DLLs (Dynamic Link Library) and Dynamic modules.
- The above information shows the DLLs of the program. This tool can be used in analyzing any malware code. This tool can be used in other hacking activities.
- Now we will use shed to show on how to inject a DLL in a running process. We will use a .net program given in shed named WindowsFormHelloWorld. Compile this program as we did above and generate WindowsFormHelloworld.exe and copy it to shed directory as we did above.
- Then type WindowsFormHelloworld.exe
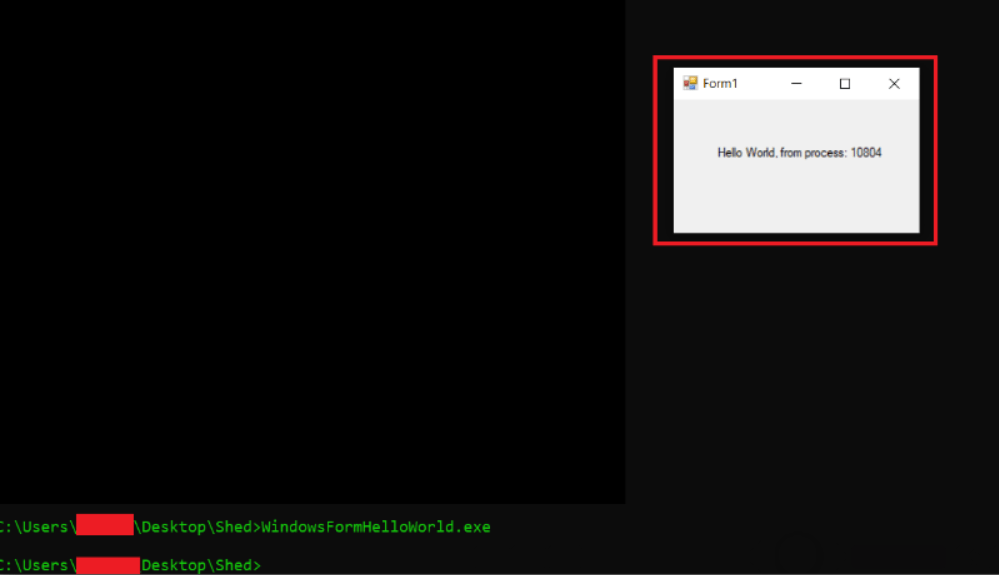
- The above query will start .net program and will show its PID. Now this PID can be used in injecting a dll.
- For injecting dll. you have debug dll presented in sample code. Then copy the InjectAssembly.dll from
C:\Users\Username\Desktop\shed-master\Tests\HelloWorld\bin\Debug to
C:\Users\Username\Desktop\Shed - Type Shed.exe –exe InjectAssembly.dll –inject –pid 10804
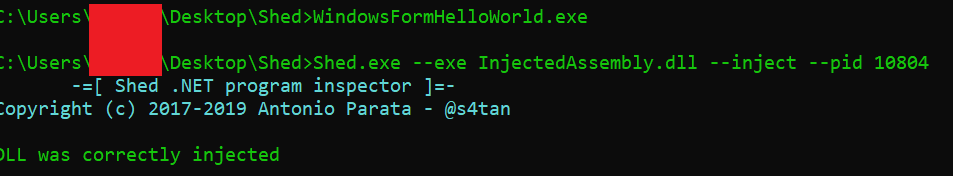
- The above query has injected the dll. Now for opening the result go to : C:\Users\Username\Desktop\Shed\Result\14284
- In results, Open logs where you can see the dll and dynamic dll, string values. As shown above in first query. These information can be used in analyzation of the exe.
- Further it creates .json file. The file shows SystemIO namespaces. References that are used in .net programming. You can separate those namspaces.
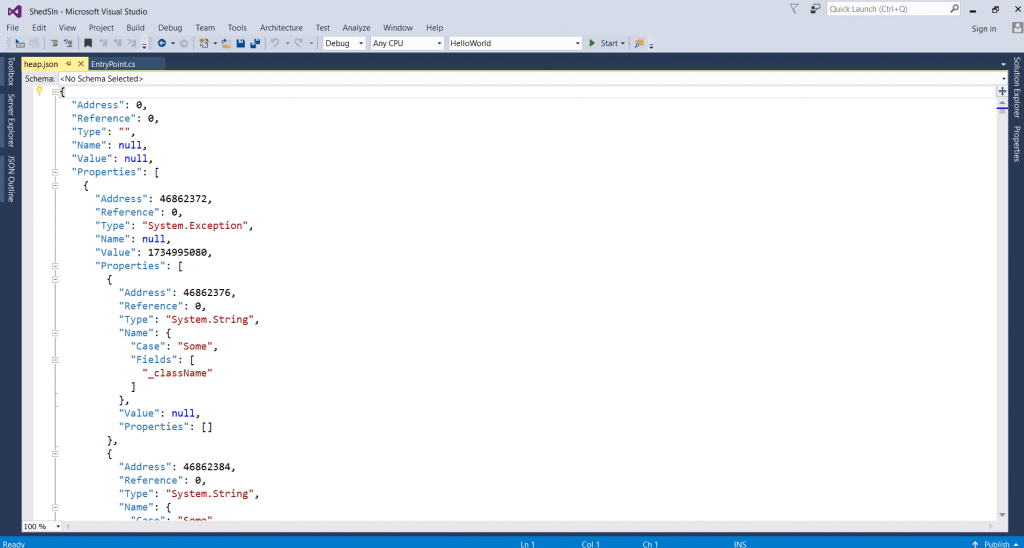
- The above screenshot shows the .net namespaces. These generalize system io namespaces.
- .net malware can delivers adware that can take screenshots of your desktop also. This shed can help you find malware in .net programs.
- This information can be considered in malware analysis or other hacking activities, according to ethical hacking courses.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










