Information gathering is a crucial part before exploiting any website. There are many tools that are available online which helps in gathering information. But these tools somehow fails to found what pentester/ security researcher wants, according to ethical hacking . Today we will show you information gathering tool called Badmod.
According to ethical hacking researcher of international institute of cyber security says that Badmod can be useful while checking any vulnerabilities of the website.
Badmod is a small tool written in php used in information gathering. The tool can gather lot of information which can be used in other phases of pentesting. For showing you we have tested this tool on Kali Linux 2018.4
- For installing type git clone https://github.com/MrSqar-Ye/BadMod.git
- Before proceeding further. Make sure you have installed php in Kali Linux.
- If not installed type sudo apt-get update
- Then type sudo apt-get install php
- Type sudo apt-get install php-curl
- After installing php. You have to change permission of the INSTALL file.
- For that type chmod u+x INSTALL
- After changing permission type ls -ltr to check if permission has changed.
- Then type cd /bin/badmod
- Type chmod u+x BadMod.php for changing the permission of this file. As this file is used while executing the tool.
- Then type sudo badmod to start the tool.
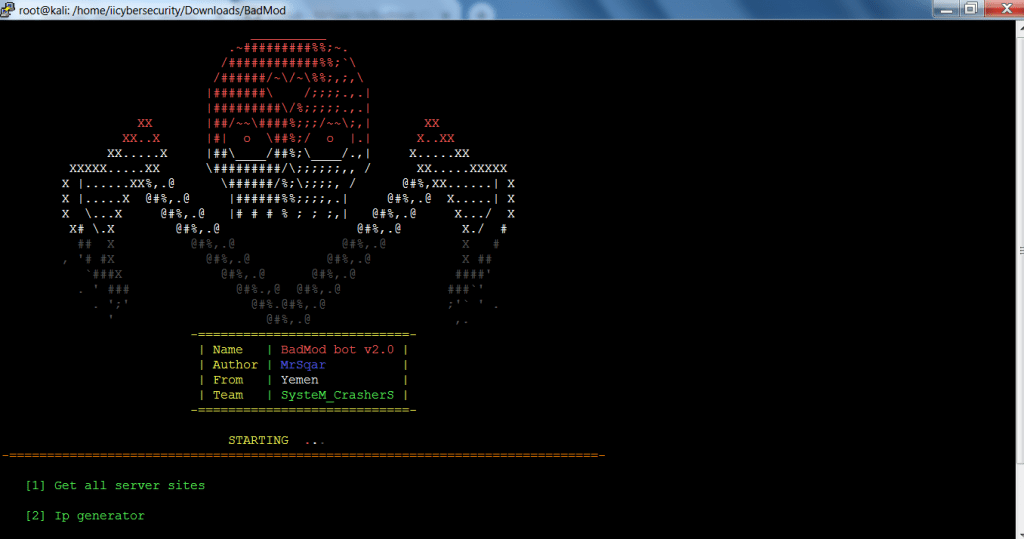
- The above is the tool used in information gathering.
- Type 2 for IP generator.
- Then type 20 for generating IP addresses as shown below.
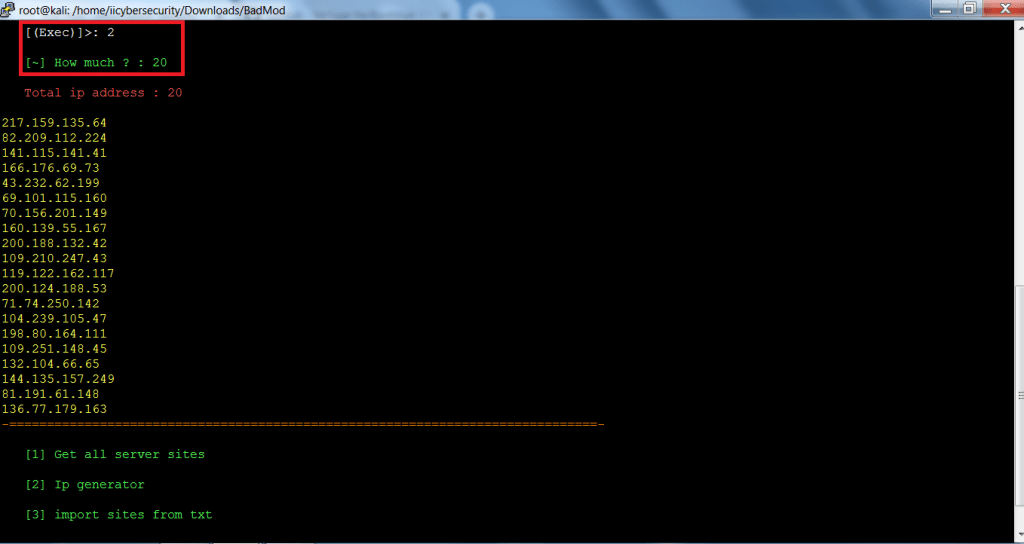
- After executing above queries, Badmod has generated 20 IP addresses. These IP addresses can be used in spreading the viruses on the local network.
- If target is in the attacker’s network, attacker can force target to visit those IP addresses by assigning them on default gateway.
- The above IP addresses can further used in other hacking activities.
- Type 3 to import sites from a list.
- This query check whether site is vulnerable or not.
- Type siteslist.txt as your list name.
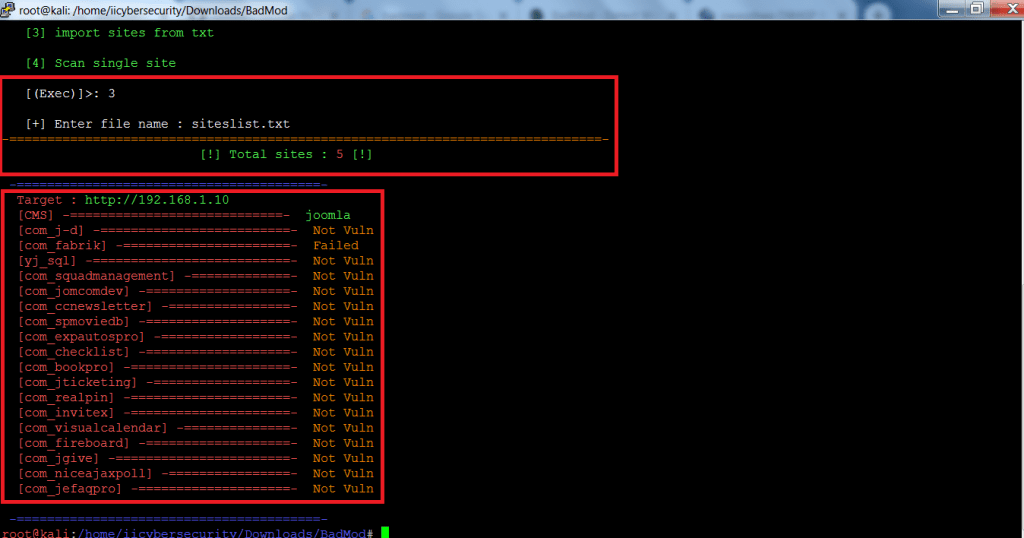
- The above query shows the links if the links are vulnerable or not. As shown in above screenshot that links are not vulnerable to exploit.
- The above query can be used in other hacking activities.
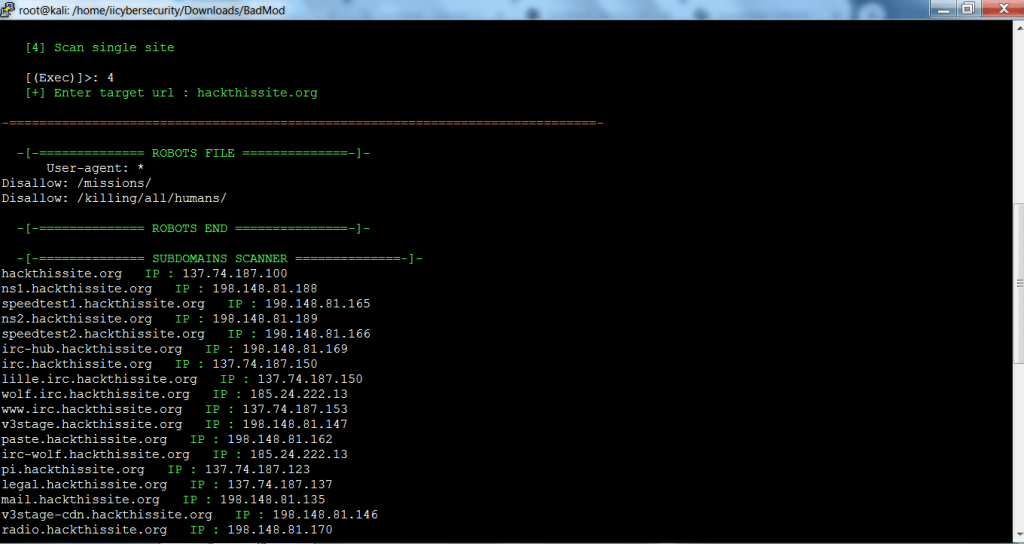
- Type 04 for information gathering.
- Type hackthissite.org URL you want to scan.
==================================SNIP================================
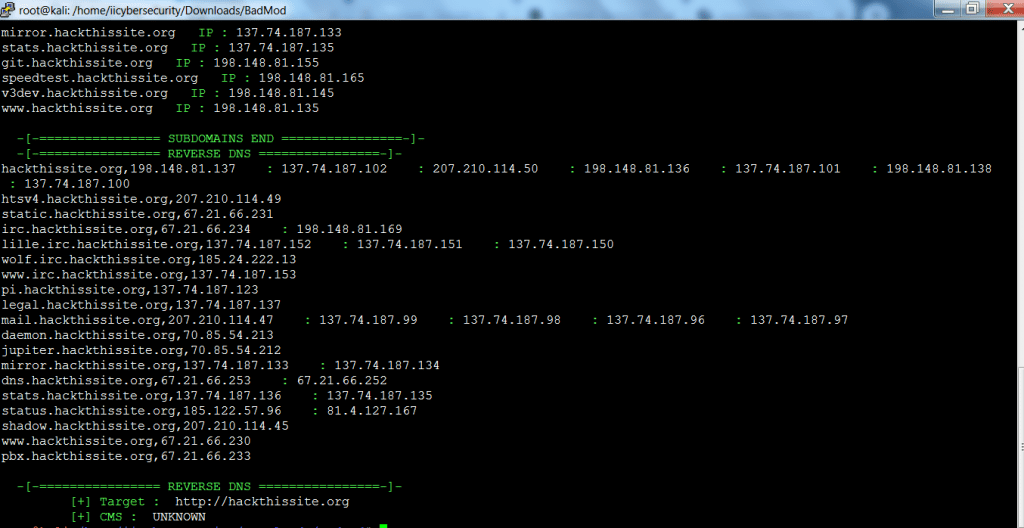
- The above query shows the reverse DNS and sub domain DNS. The above list of DNS in initial phase of information gathering.
- The above information can be used in other hacking activities.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











