A team of researchers has discovered a new way to hide malicious software
The investigators of a cybersecurity firm reported the discovery of a new malware sample capable of retrieving the memes commands published in a Twitter account controlled by a malicious actor. Thanks to this procedure, attackers make it difficult to detect traffic associated with malware, making it detected as legitimate Twitter traffic, as mentioned by information security experts from the International Institute of Cyber Security.
The idea of exploiting legitimate web services to control malware is not something new; in past opportunities some hackers have controlled malicious code through platforms like Gmail, Dropbox, PasteBin, and even Twitter.
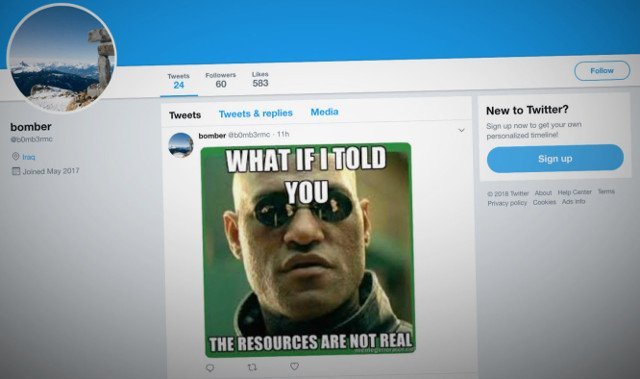
However, this time is a little different. The malware discovered by cybersecurity experts uses steganography (a technique to hide content within a digital graphic image in a way that is invisible to an observer) to hide the commands embedded in an image (in this case a meme) posted on Twitter.
“This trojan identified as TROJAN.MSIL.BERBOMTHUM.AA shows interesting behavior because malware commands are received via legitimate Twitter traffic and uses a harmless-looking meme and cannot be deleted unless the account where it was published is removed from the platform”, mentions the report of cybersecurity specialists.
The Twitter communication team reported that it closed the malicious account last December 13th.
The attackers hid the command /print within the memes, which allowed them to take screenshots of the compromised machine, in addition to sending them to a command and control server, whose address was obtained through a URL encoded in PasteBin.
In addition, BERBOMTHUM malware reviews the Twitter account used by attackers and downloads and analyzes meme files and extracts the command that they include. The Twitter account used by attackers was created in 2017 and contained only two memes, which were published in October 25 and 26. These images were used to send the /print command to the BERBOMTHUM malware.
The commands used by the attackers and their tasks are:
· /print – Performs screen captures
· /processos – Retrieves the list of running processes
· /clip – Captures the contents of the Clipboard
· /username – Retrieves user name from infected machines
· /docs – Retrieves file names from a predefined route
According to experts on cybersecurity, this malicious software is at an early stage of development, so more similar incidents are not discarded in the future.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











