Distributed denial of service attack is a popular attack used to target any website to make them down. DDOS is an malicious attempt in which target server is flooded with the internet traffic. DDOS normally sends the large no. of request to the target website to slow down, explain ethical hacking experts.
There have been many DDOS tools that are used in attacking the targeted websites. But there have been lot of online services which are hired in making DDOS attacks. These services are easily available over the internet. A quick google search can be used to hire these DDOS services.
According the ethical hacking researcher of International Institute of Cyber Security, 0x-booter is most common and updated way to attack on any website because they offer some affordable price for DDOS attack.
0x-booter is the new popular DDOS service which is to hired for DDOS attacks. 0x-booter has gained 500gbps of power to defame any website. They have 20 k bots to their services which they used while attacking.
NOW ON HOW TO HIRE A HACKET FOR DDOS ATTACK
- For accessing the website go to : https://0x-booter.pw/
- For using the features and services of the website. You have to register in their website. They have some strict rules for using their product. Don’t use any spam while signing process.
- For signing in go to : https://0x-booter.pw/panel/register.php
- After sign in process log in using you credentials as shown below.
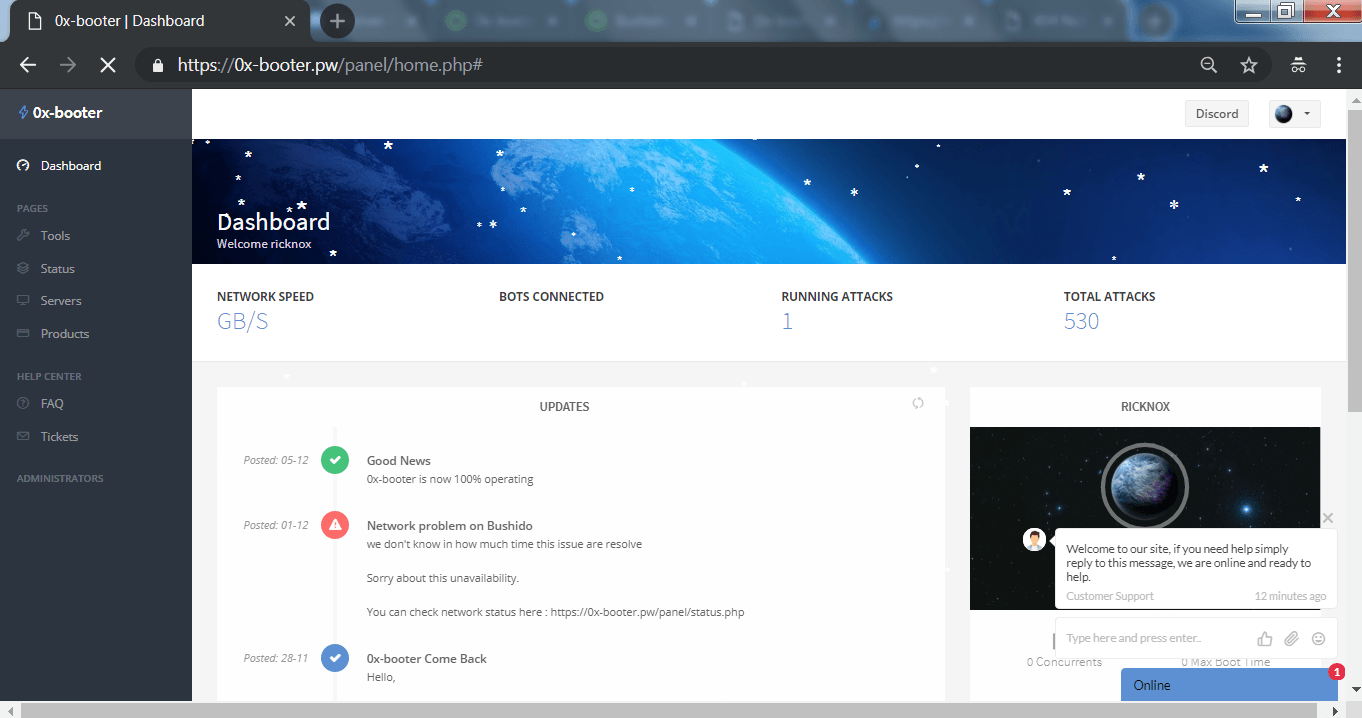
- Once you logged a dashboard opens which shows the basic information about running attacks and total attacks. You can also view the tickets and graph which shows ongoing attacks stats on the main panel.
- After clicking on products page(on the left panel), you can choose their no. of attacks which you want use as their service.
- They offer multiple prices for DDOS attacks starting from $20 to $200
- They also shows the time they will take to make the DDOS attack on the target as shown below.

- You can also use different tools which are available in 0-x booter.
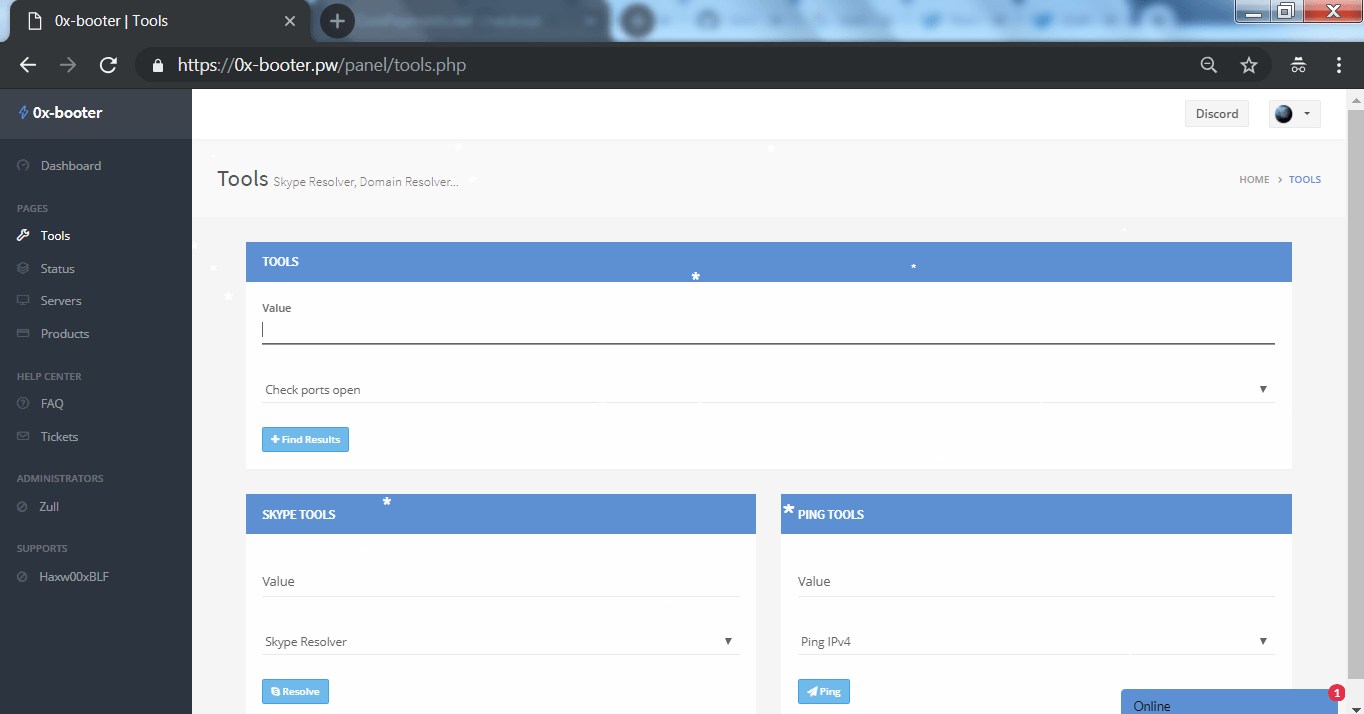
- 0-x booter monitors website using uptimerobot to check the status of the DDOS attacks and scanning the targets.
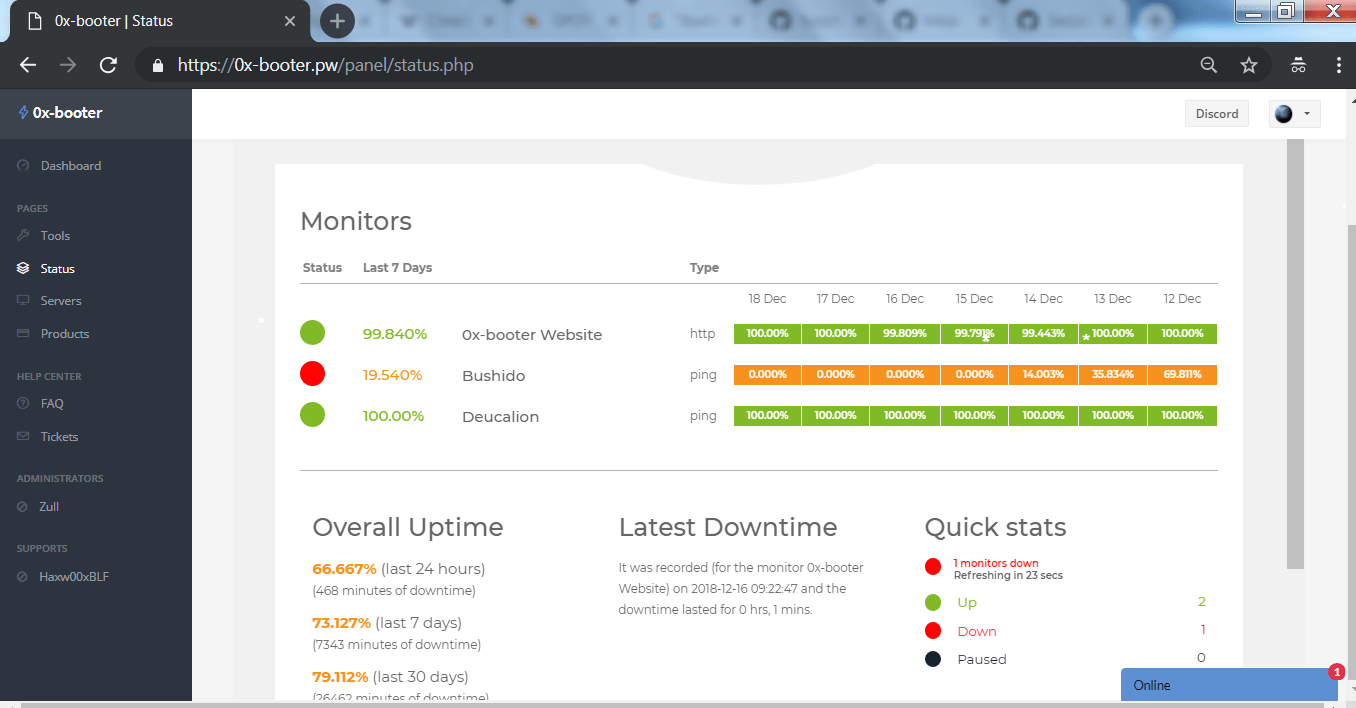
- The above screenshot shows the uptime of the 0-x booter, bushido botnet and deucalion botnet which states that site and the deculion botnet has been active from 12th December continuously but bushido botnet seems down in earlier days but now it has been up.
- The above listed botnets are common botnets which 0-x booter uses in their attacks. For seeing in detailed analysis. You can open any botnet. Botnet will open in another website named as uptimerobot.com
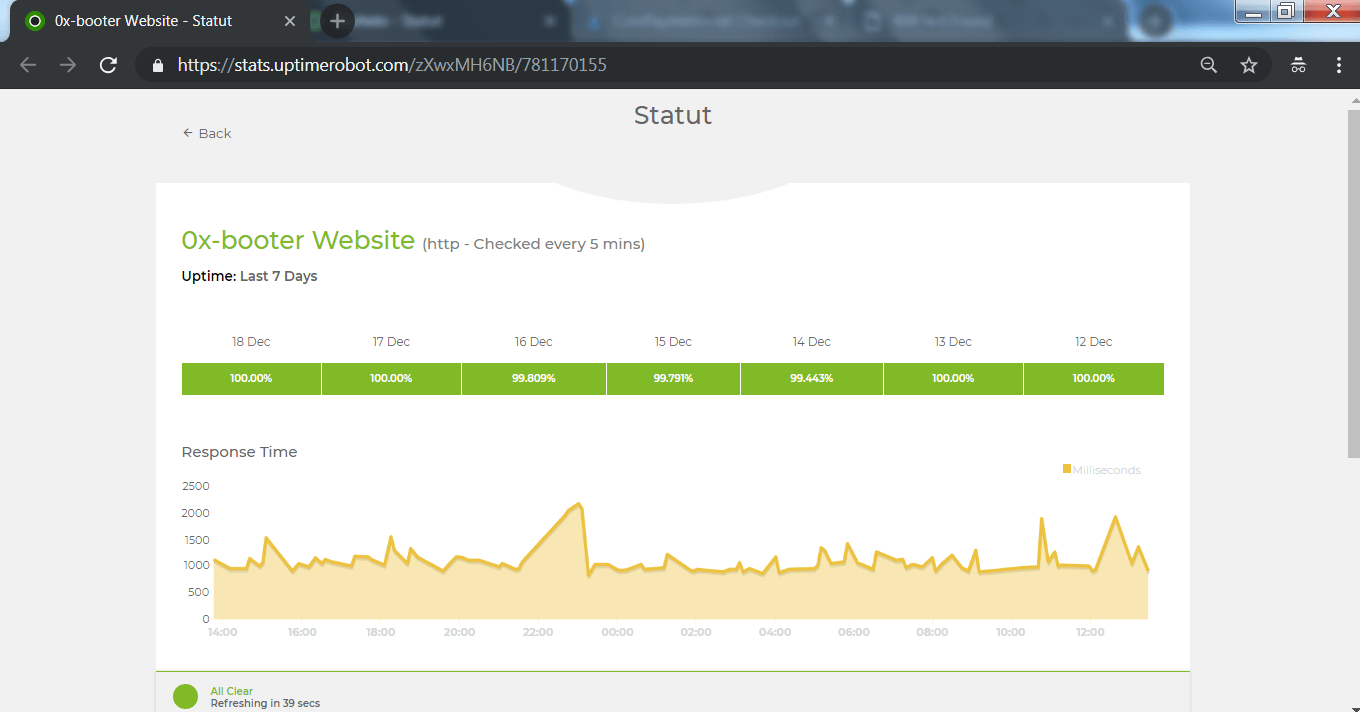
- The above listed shows the 0-x booter website uptime which is check in every 5 minutes.
- Before using any of the services of the 0-x booter as shown below, you have to use pay them in cryptocurrency. These services often require some of the validations while paying them.
MIRAI BOTNET CODED WITH PASSWORD LIST :-
- There are two most common botnets which is used by 0-x booter that are :-
- Bushido Botnet
- Mirai Botnet
- You can easily found the source code of mirai on github link :
https://github.com/jgamblin/Mirai-Source-Code/tree/6a5941be681b839eeff8ece1de8b245bcd5ffb02/mirai/bot
- The above listed are used in creating of the botnets. Most of the mirai botnet code has also used for creating the bushido botnet.
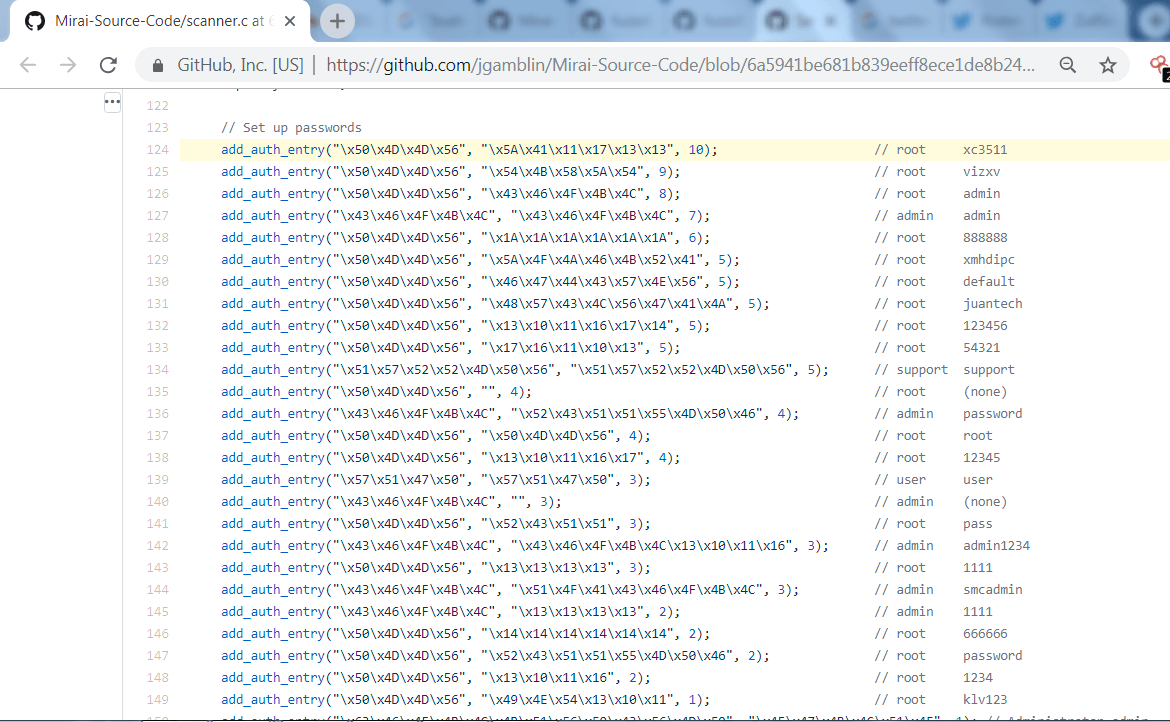
- Mirai source code different set of passwords and usernames just like dictionary attack as shown below. This list is available on the mirai source code list.
- You can checkout any code and these codes can be used in making your own botnets. These information can be used in other hacking activities.
- Here is the glimpse one of the code which you can use in making any of the botnet. These botnet codes can be used in other hacking activities.
- Here is the list of most common devices which are used by mirai to target the devices. Bushido also uses the same way to target website. These exploits used in the process are listed in the exploit database also.
Vulnerable Devices List :-
-
- Dasan GPON router https://www.exploit-db.com/exploits/44576
- D1000 Wireless Router https://www.exploit-db.com/exploits/40740
- Huawei HG532 https://www.exploit-db.com/exploits/43414
Ethical hacking researcher also states about the botnet are used for spam campaign other than DDOS, by referring to the recent news on botnet infects over 400k routers which are used for spam campaign.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.











