INFOGA INTRO:- Infoga is the tool design for gathering the email information of the company/target. This tool is written in python. Infoga gather information from different search engines like Google, Yahoo, Baidu etc. Infoga looks simple but very effective, say ethical hacking professionals. This tool is considered in early stages of pentesting or just to know visibility of company/target on the internet.
According to ethical hacking researcher from International Institute of Cyber Security infoga is used in information gathering and using that information in other hacking activities.
- This tool does not come pre installed in kali linux. So for installing infoga go to
github link:- https://github.com/m4ll0k/Infoga.git
- Open terminal in linux and type: git clone https://github.com/m4ll0k/Infoga.git
- Now go to infoga location or where you have installed the infoga.
- Type cd Infoga
- Then type ls (list the cloned directory contents)
- If the infoga does not start and shows the error of python/pip3 or requests not installed simply type sudo apt-get update to update the python libraries.
- Then type
sudo apt-get install python3-dev/ sudo apt-get install python3-pip (in most cases it require python3 to install).
- After installing the above required libraries for infoga type python3 infoga.py
________________________________________ Infoga - Email Information Gathering Momo Outaadi (m4ll0k) https://github.com/m4ll0k ________________________________________ Usage: infoga.py [OPTIONS] -d --domain Target URL/Name -s --source Source data, default "all": all Use all search engine google Use google search engine bing Use bing search engine yahoo Use yahoo search engine ask Use ask search engine baidu Use baidu search engine dogpile Use dogpile search engine exalead Use exalead search engine pgp Use pgp search engine -b --breach Check if email breached -i --info Get email informations -v --verbose Verbosity level (1,2 or 3) -H --help Show this help and exit
- -d domain – enter the target URL/Name which you want to scan.
- -s source – enter the source from where you want to gather the email information.
- -all will use all the search engines provided by the infoga. For gathering information from any particular search engine use search engines like google, yahoo, bing, ask, baidu, dogpile, exalead,pgp.
- -b breach – enter the target email to check if the email is breached.
- -i info – enter the target email to check the information about the email.
- -v verbose – enter the verbose level 1,2,3 that how deep information of the target you want.
USING ALL THE SEARCH ENGINES :-
- Type python3 infoga.py –domain cia.gov –source all -v 3
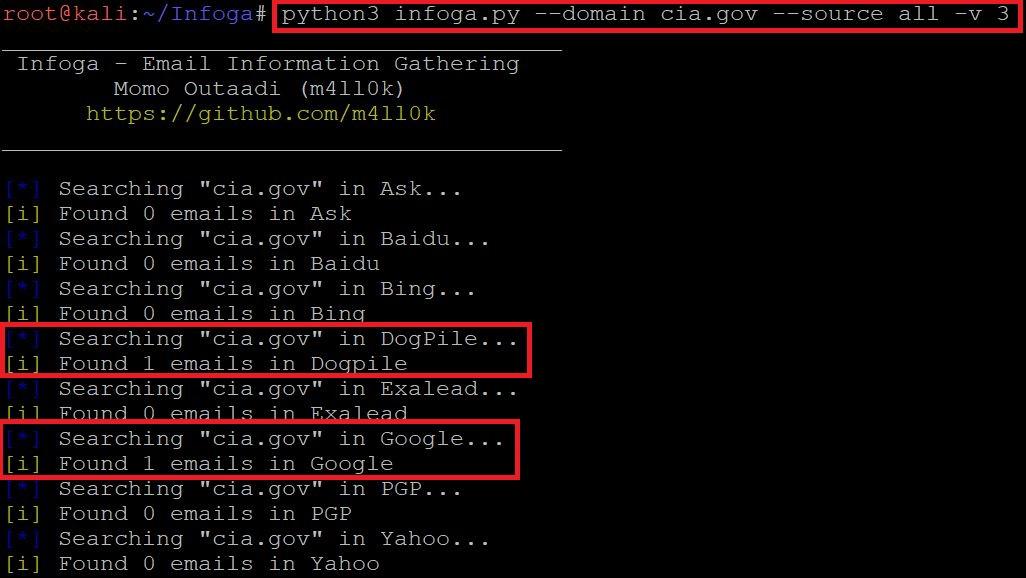
============================OUTPUT SNIP========================
- Type python3 infoga.py -d cia.gov -s all -v 3
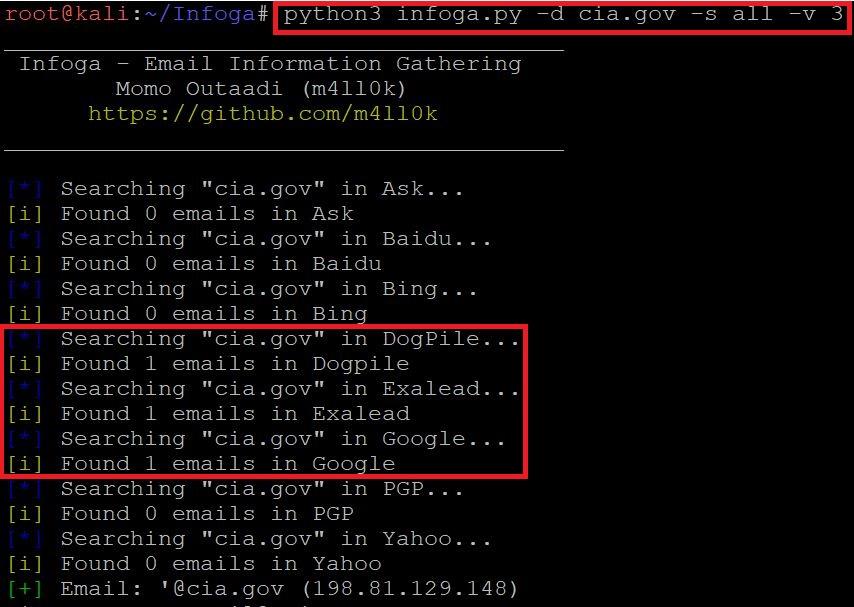
=======================OUTPUT SNIP============================
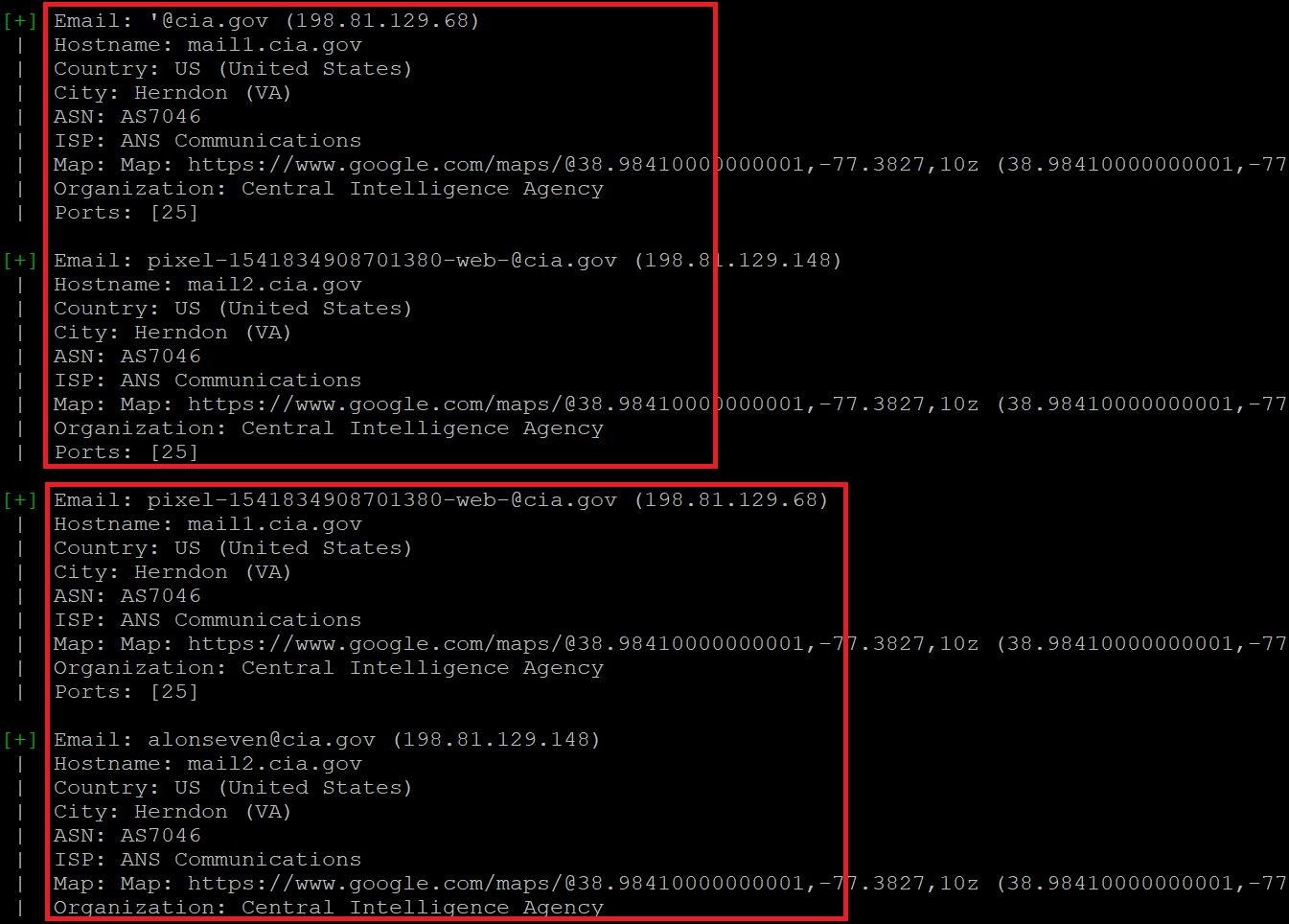
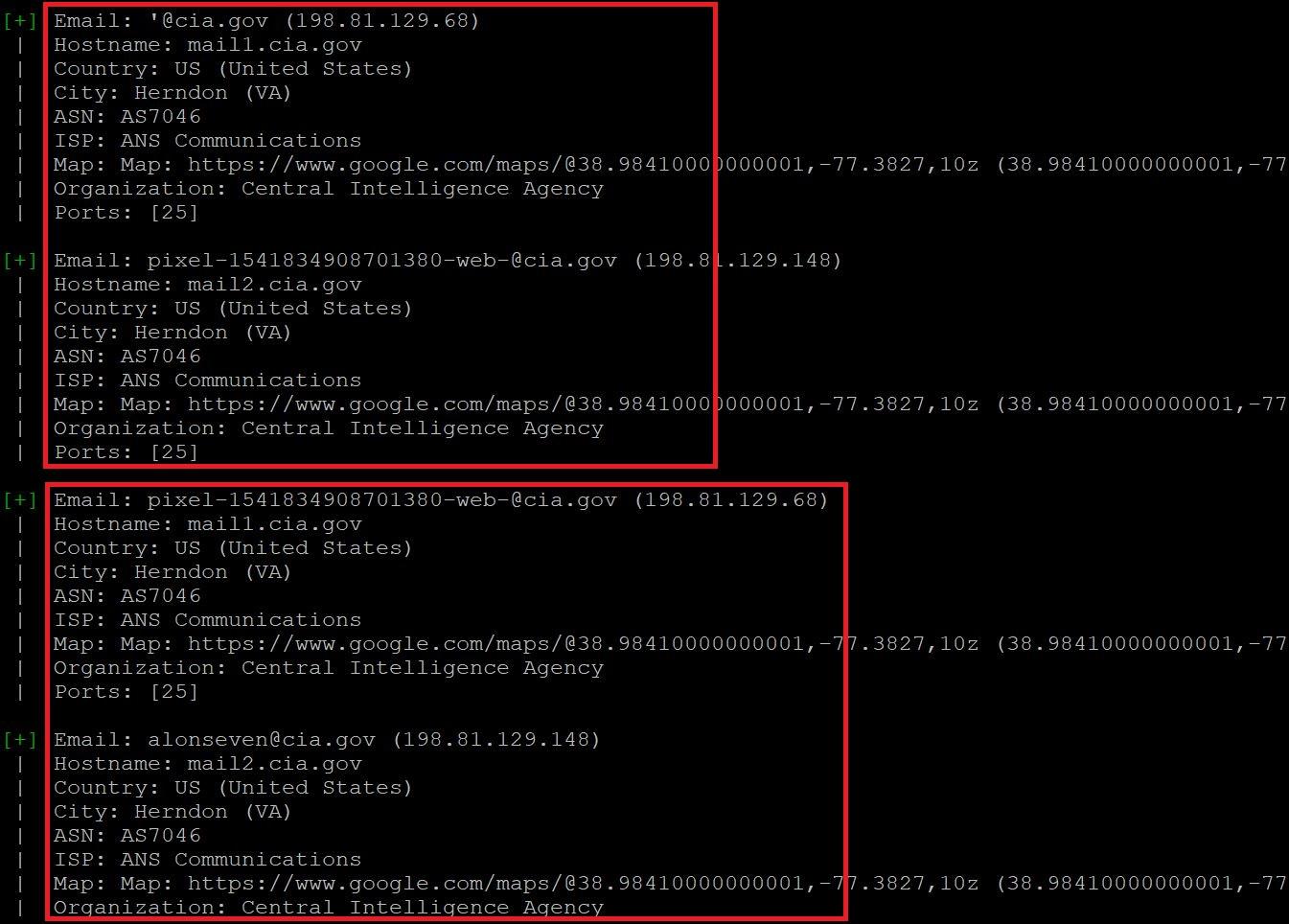
- In the above screen shot, after executing the query for gathering the email information. Infoga has found 2 mails in listed search engines. This information also shows the open ports of the target. It also shows the country,city,hostname,ISP(Internet Service Provider) and shows the map location.
- Open ports vulnerability can be used in sql injection attacks. Email can also be used in email bombing (overflowing the target mail by sending huge volumes of mail). ASN (Autonomous System Number) can used in attacking on regional internet registry which can results into control of the registration account.
SCANNING THE TARGET WEBSITE USING GOOGLE :-
- Type python3 infoga.py –domain cia.gov –source google –verbose 3 as shown below:-
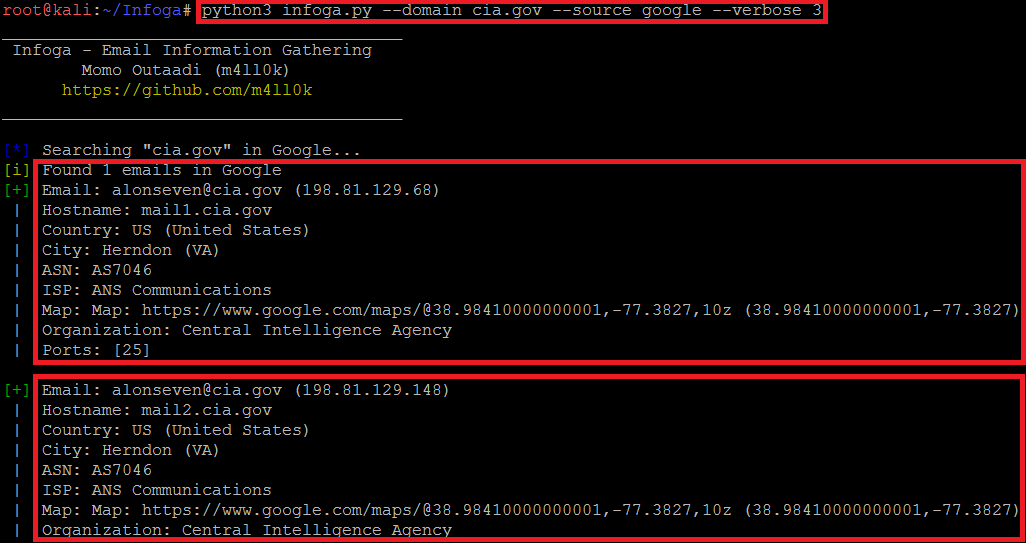
- Type python3 infoga.py -d cia.gov -s google -v 3
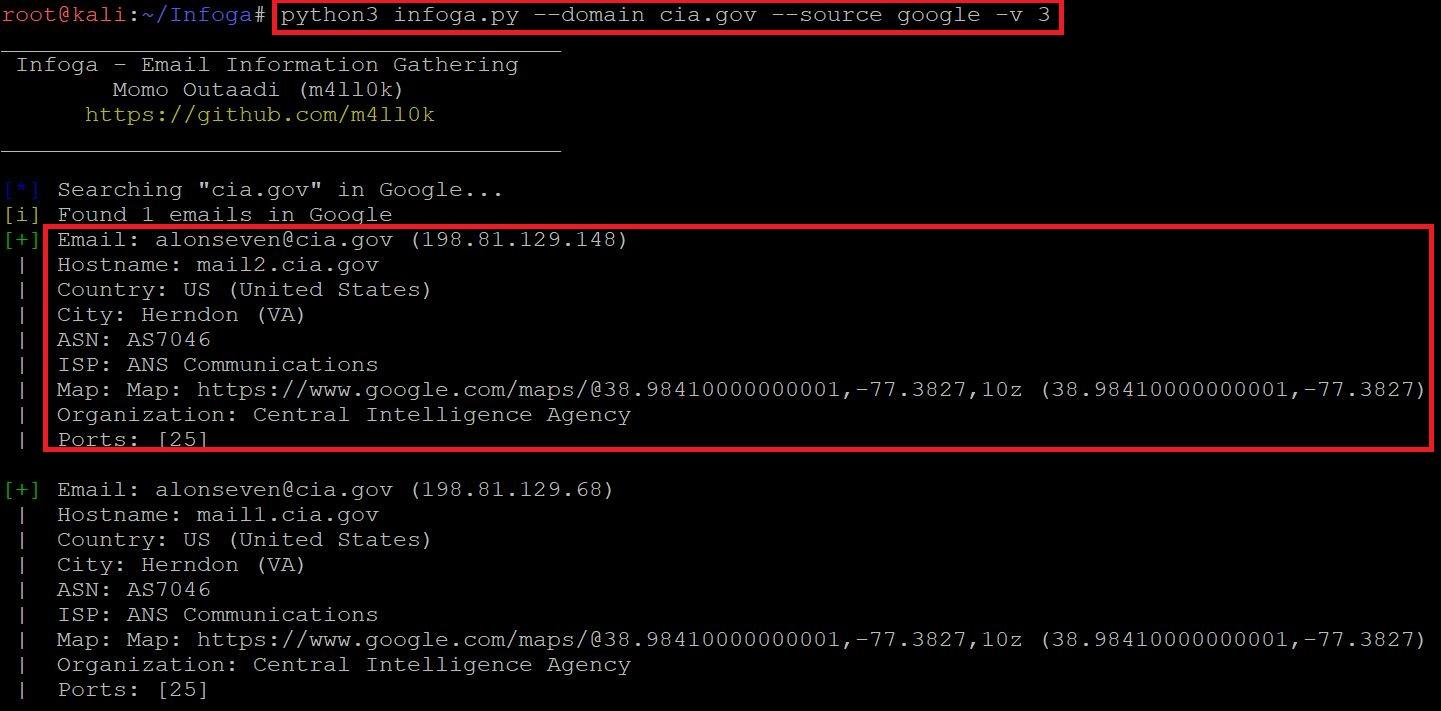
- In the above screen shot, after executing the query for gathering the email information. Infoga has found 2 mails in google. This information also shows the open ports of the target. It also shows the country,city,hostname,ISP(Internet Service Provider) and shows the map location.
- Open ports vulnerability can be used in sql injection attacks. Email can also be used in email bombing (overflowing the target mail by sending huge volumes of mail). ASN (Autonomous System Number) can used in attacking on regional internet registry which can results into control of the registration account.
GETTING THE INFORMATION OF THE EMAIL USING GOOGLE :-
- Type python3 infoga.py –info alonseven@cia.gov –source google -v 3
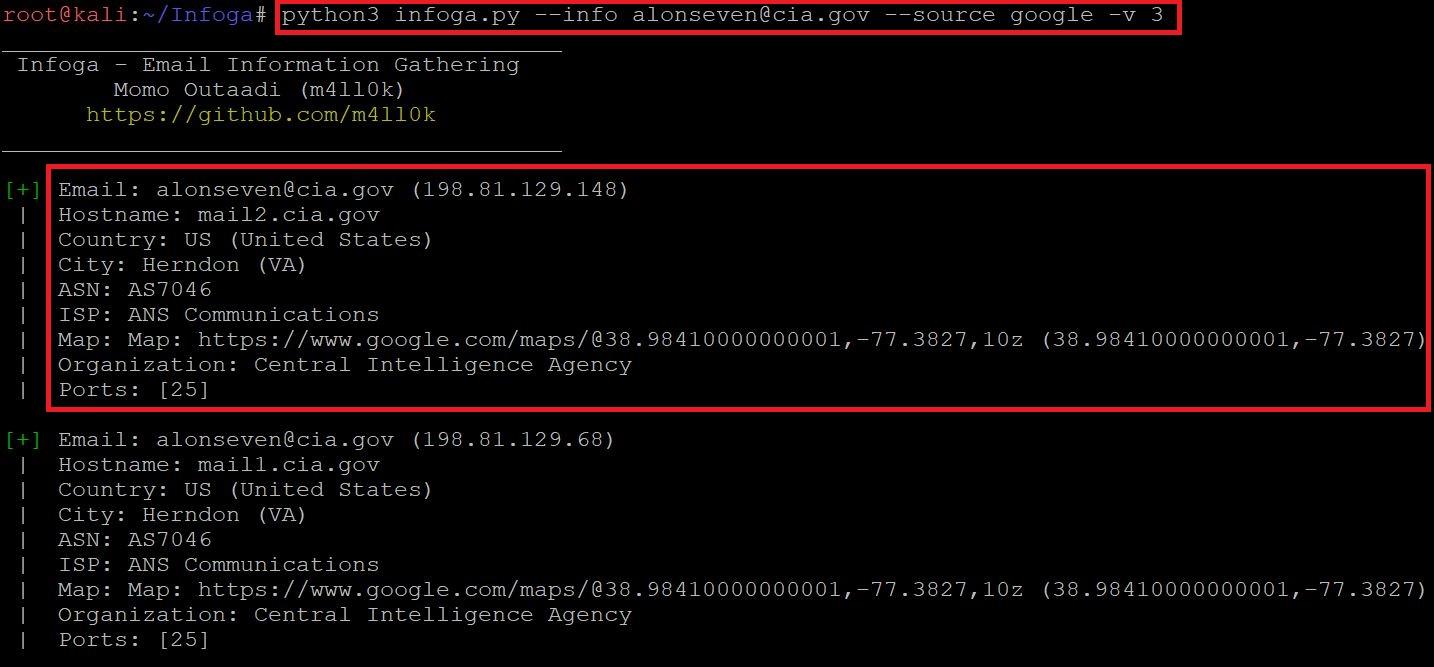
- Type python3 infoga.py -i alonseven@cia.gov -s google -v 3
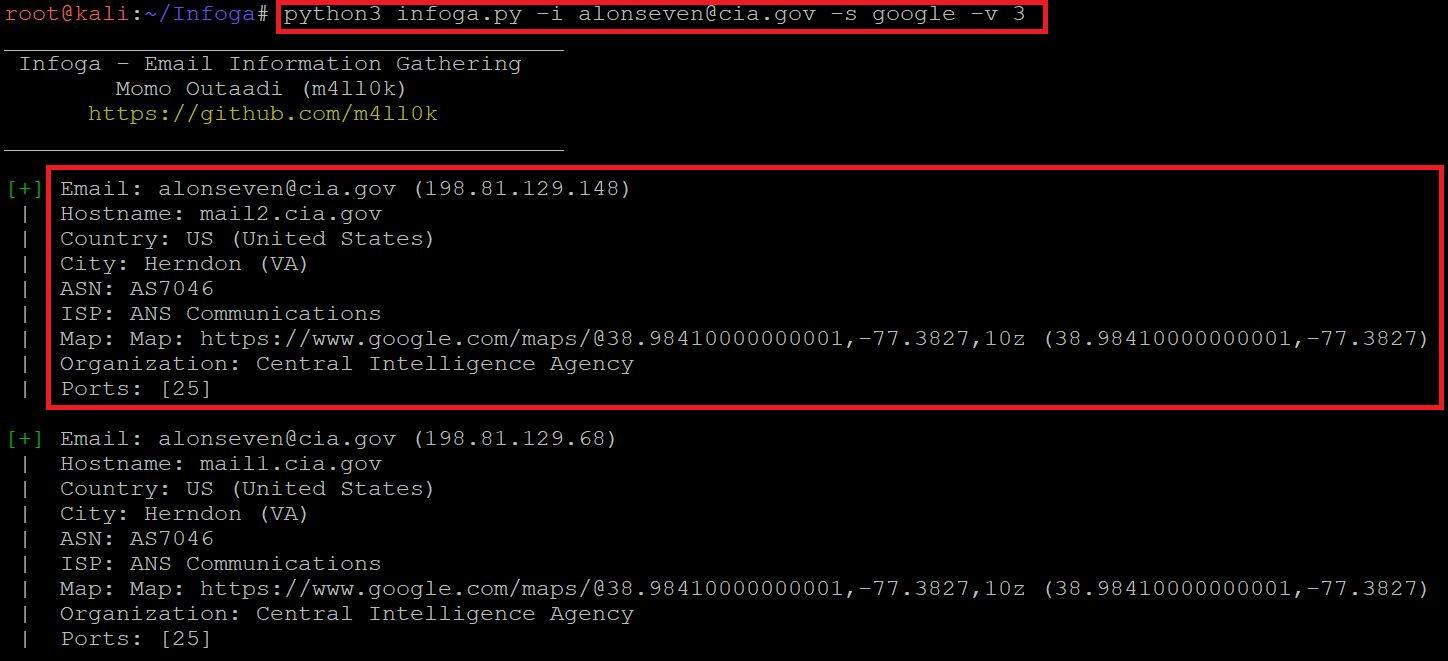
- In the above screen shot after executing the above query infoga scans the email and shows mail ip address, hostname, country-US, city-Herndon, ISP(Internet Service Provider) and open port information.
- The above information could be used in information gathering part. The above information can also be used in bruteforce attack.
USING ALL THE SEARCH ENGINES :-
- Type python3 infoga.py –info alonseven@cia.gov –source all -v 3
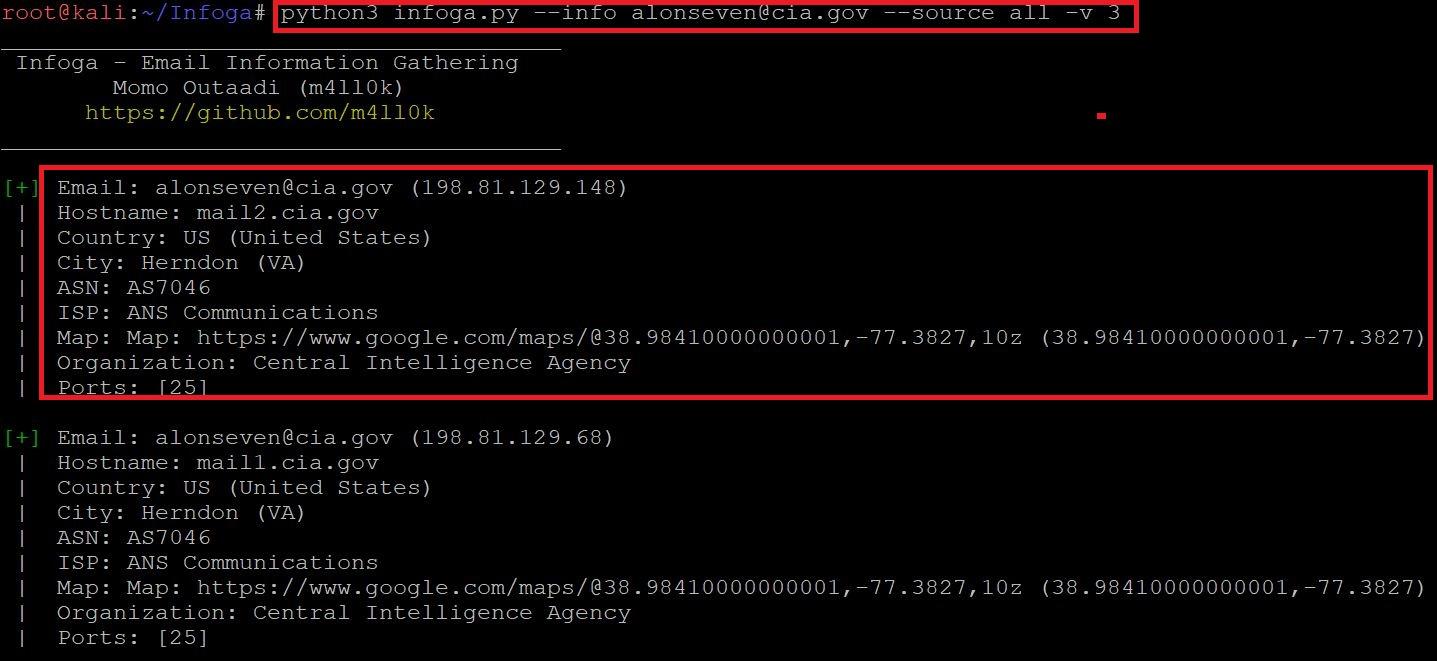
- Type python3 infoga.py -i alonseven@cia.gov -s all -v 3

- In the above screen shot after executing the above query infoga scans the email and shows mail ip address, hostname, country-US, city-Herndon, ISP(Internet Service Provider) and open port information.
- The above information could be used in information gathering part. The above information can also be used in bruteforce attack, according to ethical hacking courses.
CHANGING THE VERBOSE LEVEL :-
- Type python3 infoga.py -d cia.gov -s google -v 3
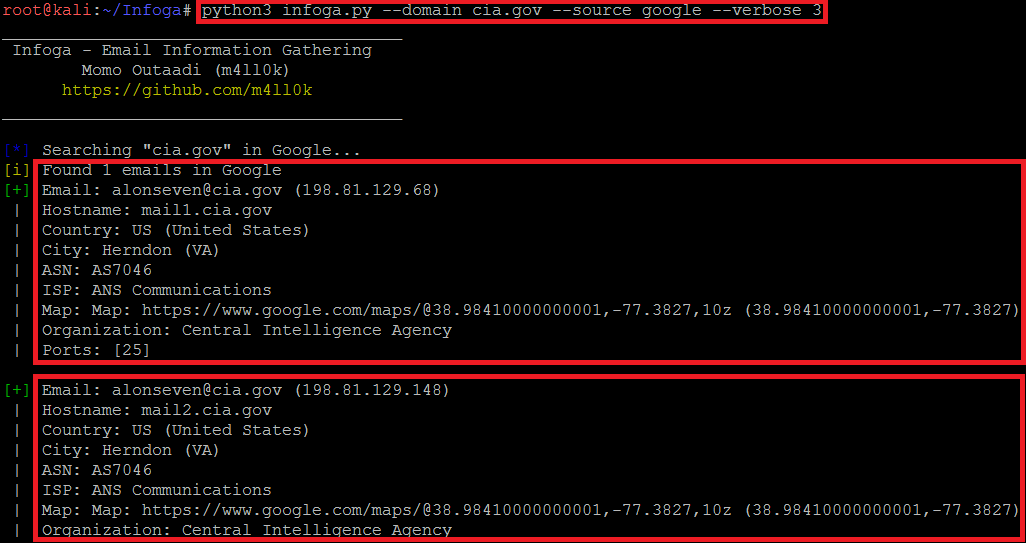
- In the above screen shot after executing with high verbose level it will scan the target website more deeper and will show more information like ISP(Internet Service Provider) Map location.
- Type python3 infoga.py -d cia.gov -s google -v 2
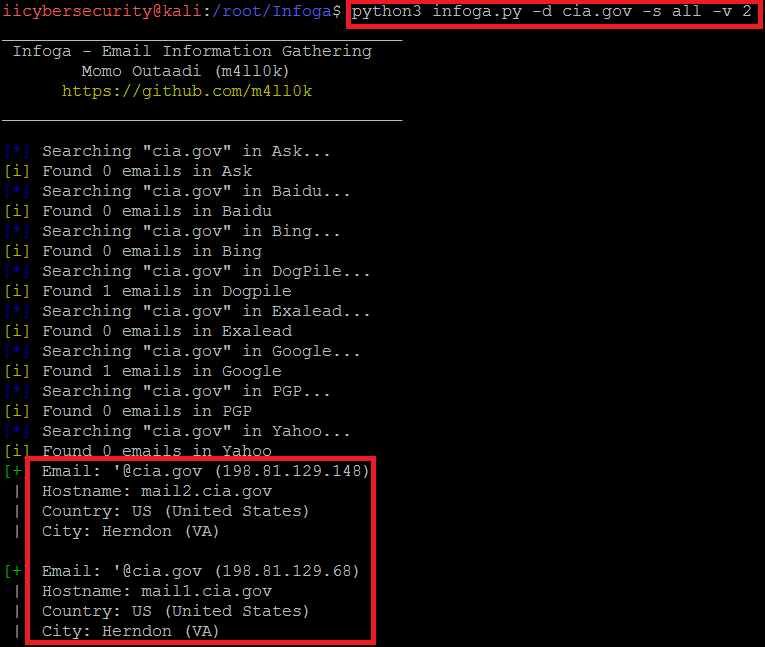
- In the above screen shot after executing with verbose level 2 it will scan the target website and will show only the basic information like mail, hostname, country and the city.
- Type python3 infoga.py -d cia.gov -s google -v 1
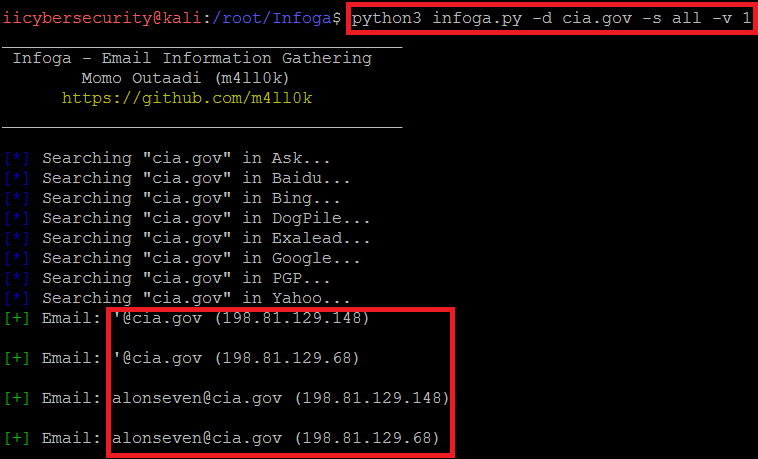
- In the above screen shot after executing the query with verbose level 1. Infoga will show only the target ip address.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.










