CRUNCH INTRO:- While cracking the password, attacker always needs an wordlist. Normally, wordlist use thousand of words per second to crack the password. If attacker gathers some information about the victim like – birthday dates, children names, pets name, girlfriend name etc. Attacker can use information in creating of the custom wordlist, say ethical hacking investigators.
While attacking on any organisation we might need an custom wordlist, to generate the wordlist for attacking. Thats why crunch is used. Crunch is an inbuilt tool from Kali Linux. Crunch helps in creating an custom wordlist. And that wordlist can be used in John The Ripper, Cain And Abel, Aircrack-ng and many more password cracking tools.
Ethical hacking researcher of iicybersecurity says that crunch is mostly used in mass level of attacking on login webpages of popular social media platforms as well as on big tech companies.
Basic Command of Crunch:-
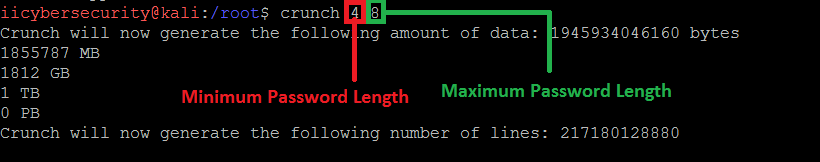
crunch <mini. password length> <max. password length>
- You can also specifiy the numbers or the characters in wordlist. If you specify the character the wordlist will generate in characters and if you specify the numbers the wordlist will generate in numbers as shown below.
- Here wordlist will be generated in characters.
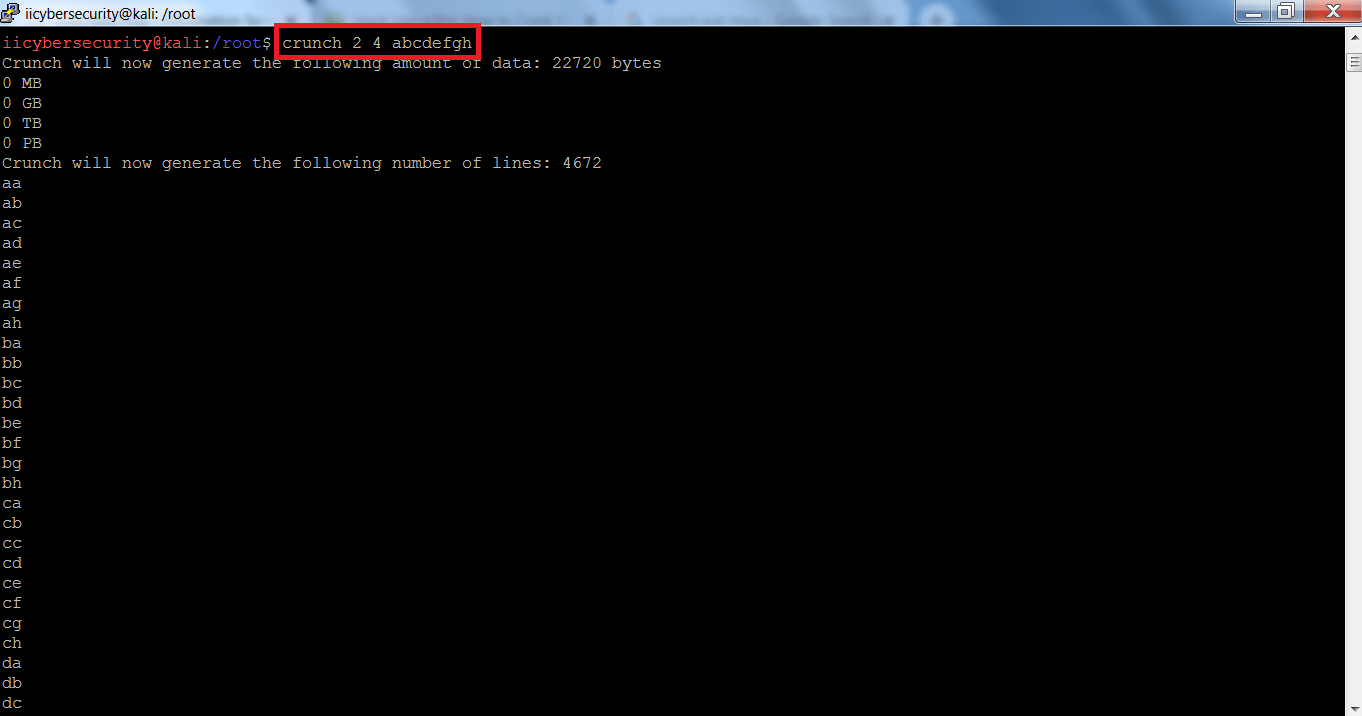
- Type crunch 2 4 abcdefgh
- 2 is the minimum password length and 4 is the maximum password length.
- abcdefgh characters are used to generate the list.
- You can also use the numbers to generate the wordlist.
- Here wordlist will be generated in numbers.
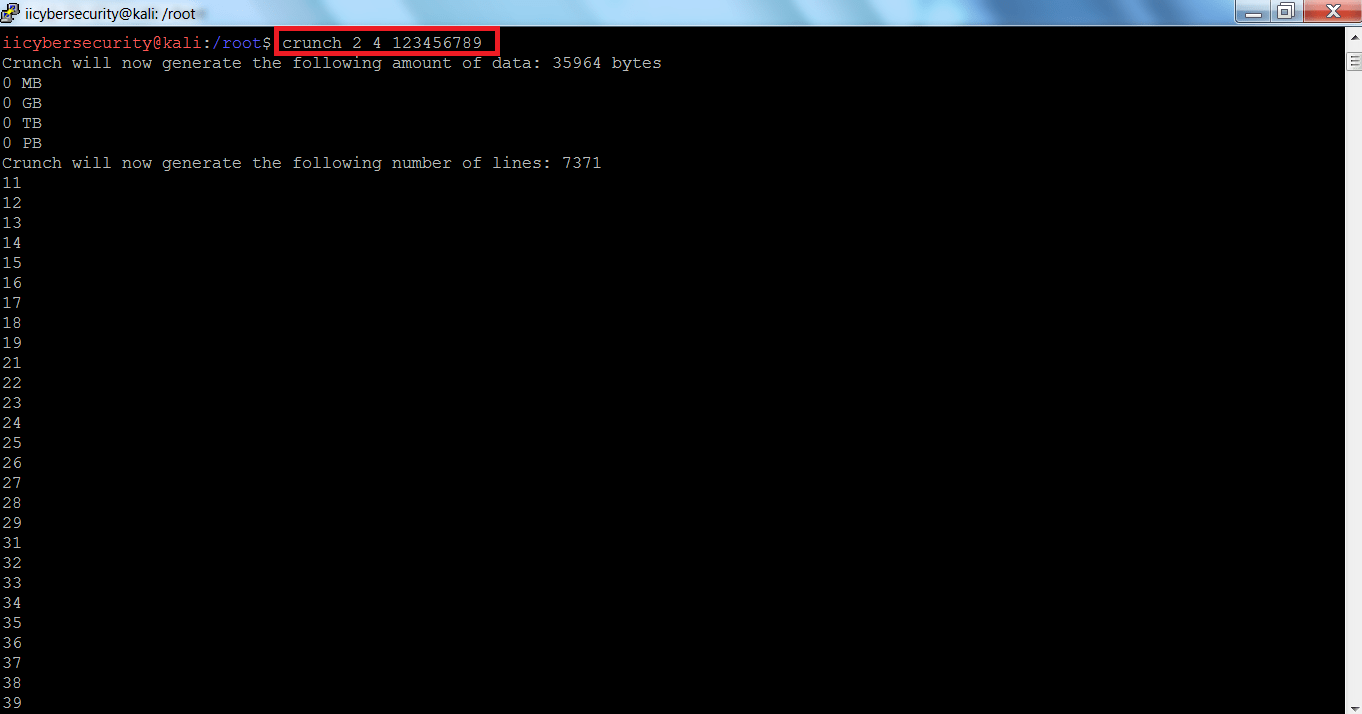
- Type crunch 2 4 123456789
- 2 is the minimum password length and 4 is the maximum password length.
- 123456789 numbers are used to generate the list.
START WITH CRUNCH TO SEE MORE OPTIONS:-
- Type crunch
- Type man crunch
====================SNIP===================
==================SNIP=================
- The above screen shots are the manual pages of the crunch. These manual pages can be used in knowing the options of crunch command.
CREATING AN SIMPLE WORDLIST:-
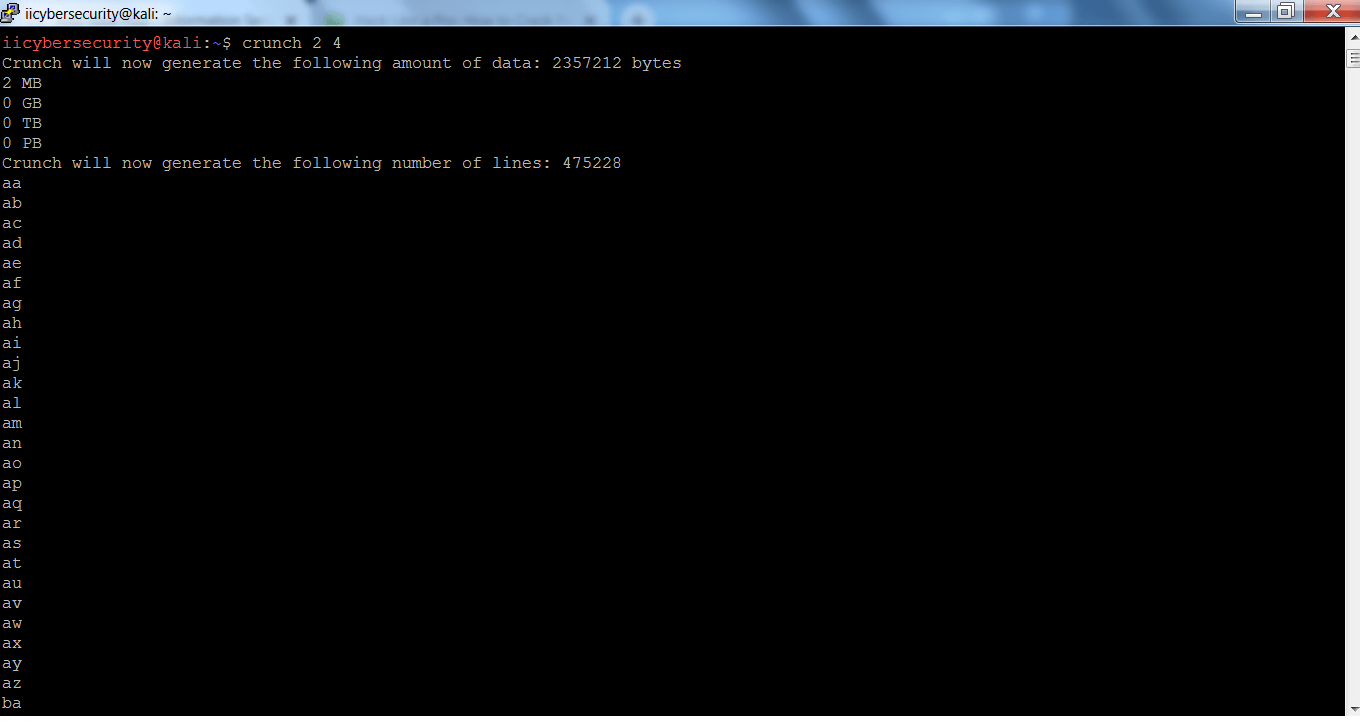
We are assuming that the target having password between 2 and the 4 characters. So the crunch will make wordlist between 2 to 4 character.
- Type crunch 2 4 in linux terminal.
- 2 is the minimum password length and 4 is the maximum password length.
- As you can see that the crunch has started to make the wordlist. Notice one thing that wordlist has been created between 2 to 4 characters.
- You can use the above wordlist for cracking the password.
CREATING THE WORDLIST WITH NUMBERS:-
- Type crunch 10 10 9875347821 -o /root/numericlist.txt
- 9875347821 are the numbers used to generate the list.
- 10 is the minimum password length and next 10 is the maximum password length in the above command.
- -o /path/to/save/list is used to specify the location to save the wordlist.
root@kali:~# crunch 10 10 9875347821 -o /root/numericlist.txt Crunch will now generate the following amount of data: 11811160064 bytes 11264 MB 11 GB 0 TB 0 PB Crunch will now generate the following number of lines: 1073741824 crunch: 1% completed generating output crunch: 2% completed generating output crunch: 3% completed generating output crunch: 4% completed generating output crunch: 5% completed generating output crunch: 6% completed generating output crunch: 7% completed generating output crunch: 7% completed generating output crunch: 8% completed generating output crunch: 9% completed generating output crunch: 9% completed generating output crunch: 10% completed generating output crunch: 11% completed generating output crunch: 11% completed generating output crunch: 12% completed generating output crunch: 13% completed generating output crunch: 14% completed generating output crunch: 15% completed generating output crunch: 16% completed generating output crunch: 17% completed generating output crunch: 18% completed generating output crunch: 19% completed generating output crunch: 20% completed generating output crunch: 22% completed generating output crunch: 23% completed generating output crunch: 24% completed generating output crunch: 25% completed generating output crunch: 26% completed generating output crunch: 27% completed generating output crunch: 28% completed generating output crunch: 29% completed generating output crunch: 30% completed generating output crunch: 31% completed generating output crunch: 33% completed generating output crunch: 34% completed generating output crunch: 35% completed generating output crunch: 36% completed generating output crunch: 38% completed generating output crunch: 39% completed generating output crunch: 40% completed generating output crunch: 41% completed generating output crunch: 43% completed generating output crunch: 44% completed generating output crunch: 45% completed generating output crunch: 46% completed generating output crunch: 47% completed generating output crunch: 48% completed generating output crunch: 49% completed generating output crunch: 51% completed generating output crunch: 52% completed generating output crunch: 53% completed generating output crunch: 54% completed generating output crunch: 55% completed generating output crunch: 56% completed generating output crunch: 57% completed generating output crunch: 59% completed generating output crunch: 60% completed generating output crunch: 61% completed generating output crunch: 62% completed generating output crunch: 64% completed generating output crunch: 65% completed generating output crunch: 66% completed generating output crunch: 67% completed generating output crunch: 68% completed generating output crunch: 70% completed generating output crunch: 71% completed generating output crunch: 72% completed generating output crunch: 73% completed generating output crunch: 74% completed generating output crunch: 76% completed generating output crunch: 77% completed generating output crunch: 78% completed generating output crunch: 79% completed generating output crunch: 80% completed generating output crunch: 82% completed generating output crunch: 83% completed generating output crunch: 84% completed generating output crunch: 85% completed generating output crunch: 86% completed generating output crunch: 88% completed generating output crunch: 89% completed generating output crunch: 90% completed generating output crunch: 91% completed generating output crunch: 92% completed generating output crunch: 93% completed generating output crunch: 94% completed generating output crunch: 95% completed generating output crunch: 97% completed generating output crunch: 98% completed generating output crunch: 99% completed generating output crunch: 100% completed generating output
- After executing the above command crunch will generate the password list using the numbers <9875347821>.
root@kali:~# ls root@kali:~# head numericlist.txt 9999999999 9999999998 9999999997 9999999995 9999999993 9999999994 9999999992 9999999991 9999999989 9999999988
- The above numeric list could be used if the attacker knows the mobile number of the target. It could be an possibility that password must be an mobile number.
CREATING THE WORDLIST WITH OTHER OPTIONS
USING -i OPTION:-
-i is used to inverts the output. This options inverts the output generated without -i option. If we don’t use -i, crunch will generate list in aa, ab, ac, ad, ae but if you use -i, crunch will generate list in aa, ba, ca, da, ea as shown below.
- Type crunch 1 2 abcdefgh -i -o /root/wordlist2/txt
- abcdefgh are the characters used in generating list.
- 1 is the minimum password length and 2 is the maximum password length in the above command.
- -o /path/to/save/list is used to specify the location to save the wordlist.
root@kali:~# crunch 1 2 abcdefgh -i -o /root/wordlist2.txt Crunch will now generate the following amount of data: 208 bytes 0 MB 0 GB 0 TB 0 PB Crunch will now generate the following number of lines: 72 a b c d e f g h aa ba ca da ea fa ga ha ab bb cb db eb fb gb hb ac bc cc dc ec fc gc hc ad bd cd
- The above output is inverting the output generated without -i option.
iicybersecurity@kali:/root$ crunch 2 4 Crunch will now generate the following amount of data: 2357212 bytes 2 MB 0 GB 0 TB 0 PB Crunch will now generate the following number of lines: 475228 aa ab ac ad ae af ag ah ai aj ak al am an ao ap aq ar as
For Lower Case Characters:-
USING -t OPTION:-
- -t allows you to specify a pattern
- @ will insert lower case characters
- , will insert upper case characters
- % will insert numbers
- ^ will insert symbols
Now we will take -t commands one by one:
- <@> insert lower case characters.
- Type crunch 10 10 -t @@@@@@0316 -o /root/birth_datlist.txt
- 10 is the minimum and next 10 is the maximum password length in the above command.
- -o /path/to/save/list is used to save the list.
- Here 0316 is the birth date used for generating the list.
root@kali:~# crunch 10 10 -t @@@@@@0316 -o /root/birth_datlist.txt Crunch will now generate the following amount of data: 3398073536 bytes 3240 MB 3 GB 0 TB 0 PB Crunch will now generate the following number of lines: 308915776 crunch: 2% completed generating output crunch: 5% completed generating output crunch: 8% completed generating output crunch: 10% completed generating output crunch: 13% completed generating output crunch: 16% completed generating output crunch: 18% completed generating output crunch: 21% completed generating output crunch: 24% completed generating output crunch: 27% completed generating output crunch: 29% completed generating output crunch: 32% completed generating output crunch: 35% completed generating output crunch: 37% completed generating output crunch: 40% completed generating output crunch: 43% completed generating output crunch: 45% completed generating output crunch: 48% completed generating output crunch: 51% completed generating output crunch: 54% completed generating output crunch: 56% completed generating output crunch: 59% completed generating output crunch: 62% completed generating output crunch: 64% completed generating output crunch: 67% completed generating output crunch: 70% completed generating output crunch: 72% completed generating output crunch: 75% completed generating output crunch: 78% completed generating output crunch: 81% completed generating output crunch: 83% completed generating output crunch: 87% completed generating output crunch: 90% completed generating output crunch: 92% completed generating output crunch: 95% completed generating output crunch: 99% completed generating output crunch: 100% completed generating output
- As on assumption we can take that target can have password on the birthday dates. So we can generate the wordlist on the birth dates.
root@kali:~# ls root@kali:~# head birth_datlist.txt aaaaaa0316 aaaaab0316 aaaaac0316 aaaaad0316 aaaaae0316 aaaaaf0316 aaaaag0316 aaaaah0316 aaaaai0316 aaaaaj0316
- As you can see the above list has been generated using the particular birthday date. The above information can be used in password cracking.
For Upper Characters:-
- <,> insert uppercase character.
- Type crunch 10 10 -t ,,,,,,0316 -o /root/birth_dat2list.txt
- 0316 use as birthday dates to generate list.
- 10 is the minimum password length and next 10 is the maximum password length in the above command.
root@kali:~# crunch 10 10 -t ,,,,,,0316 -o /root/birth_dat2list.txt Crunch will now generate the following amount of data: 3398073536 bytes 3240 MB 3 GB 0 TB 0 PB Crunch will now generate the following number of lines: 308915776 crunch: 2% completed generating output crunch: 5% completed generating output crunch: 8% completed generating output crunch: 11% completed generating output crunch: 13% completed generating output crunch: 16% completed generating output crunch: 18% completed generating output crunch: 21% completed generating output crunch: 24% completed generating output crunch: 27% completed generating output crunch: 29% completed generating output crunch: 32% completed generating output crunch: 34% completed generating output crunch: 36% completed generating output crunch: 39% completed generating output crunch: 42% completed generating output crunch: 44% completed generating output crunch: 47% completed generating output crunch: 50% completed generating output crunch: 52% completed generating output crunch: 55% completed generating output crunch: 58% completed generating output crunch: 60% completed generating output crunch: 63% completed generating output crunch: 66% completed generating output crunch: 69% completed generating output crunch: 71% completed generating output crunch: 74% completed generating output crunch: 77% completed generating output crunch: 80% completed generating output crunch: 83% completed generating output crunch: 86% completed generating output crunch: 89% completed generating output crunch: 92% completed generating output crunch: 94% completed generating output crunch: 97% completed generating output crunch: 100% completed generating output root@kali:~# ls root@kali:~# head birth_dat2list.txt AAAAAA0316 AAAAAB0316 AAAAAC0316 AAAAAD0316 AAAAAE0316 AAAAAF0316 AAAAAG0316 AAAAAH0316 AAAAAI0316 AAAAAJ0316
- After the executing the above command, query will generate the wordlist in uppercase letter.
FOR NUMBERS:-
- <%> is used to generate numbers.
- Type crunch 10 10 -t %%%%%%0618 -o /root/petnameslist.txt
- 0618 use as birthday dates to generate list.
- -o is used to save the path of the list.
root@kali:~# crunch 10 10 -t %%%%%%0618 -o /root/petnameslist.txt Crunch will now generate the following amount of data: 11000000 bytes 10 MB 0 GB 0 TB 0 PB Crunch will now generate the following number of lines: 1000000 crunch: 100% completed generating output root@kali:~# ls root@kali:~# head petnameslist.txt 0000000618 0000010618 0000020618 0000030618 0000040618 0000050618 0000060618 0000070618 0000080618 0000090618
- The above output can be used in password cracking.
USING THE CHARSET:-
Crunch provides a feature where you can generate a list using a specific character set. If you know that your target is using the password of 7 alphanumeric characters. You can generate a list of the possibilities in crunch, explain ethical hacking consultants.
For using the charset first select the charset.
- Type cd /usr/share/crunch
- Then type ls
- Type cat charset.lst
root@kali:/usr/share/crunch# ls
charset.lst
root@kali:/usr/share/crunch# cat charset.lst
# charset configuration file for winrtgen v1.2 by Massimiliano Montoro (mao@oxid.it)
# compatible with rainbowcrack 1.1 and later by Zhu Shuanglei <shuanglei@hotmail.com>
hex-lower = [0123456789abcdef]
hex-upper = [0123456789ABCDEF]
numeric = [0123456789]
numeric-space = [0123456789 ]
symbols14 = [!@#$%^&*()-_+=]
symbols14-space = [!@#$%^&*()-_+= ]
symbols-all = [!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
symbols-all-space = [!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
ualpha = [ABCDEFGHIJKLMNOPQRSTUVWXYZ]
ualpha-space = [ABCDEFGHIJKLMNOPQRSTUVWXYZ ]
ualpha-numeric = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789]
ualpha-numeric-space = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 ]
ualpha-numeric-symbol14 = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=]
ualpha-numeric-symbol14-space = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+= ]
ualpha-numeric-all = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
ualpha-numeric-all-space = [ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
lalpha = [abcdefghijklmnopqrstuvwxyz]
lalpha-space = [abcdefghijklmnopqrstuvwxyz ]
lalpha-numeric = [abcdefghijklmnopqrstuvwxyz0123456789]
lalpha-numeric-space = [abcdefghijklmnopqrstuvwxyz0123456789 ]
lalpha-numeric-symbol14 = [abcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()-_+=]
lalpha-numeric-symbol14-space = [abcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()-_+= ]
lalpha-numeric-all = [abcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
lalpha-numeric-all-space = [abcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
mixalpha = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ]
mixalpha-space = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ ]
mixalpha-numeric = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789]
mixalpha-numeric-space = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 ]
mixalpha-numeric-symbol14 = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=]
mixalpha-numeric-symbol14-space = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+= ]
mixalpha-numeric-all = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
mixalpha-numeric-all-space = [abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
#########################################################################################
# SWEDISH CHAR-SUPPORT # #########################################################################################
#########################
# Uppercase #
#########################
ualpha-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ]
ualpha-space-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ ]
ualpha-numeric-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789]
ualpha-numeric-space-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789 ]
ualpha-numeric-symbol14-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=]
ualpha-numeric-symbol14-space-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+= ]
ualpha-numeric-all-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
ualpha-numeric-all-space-sv = [ABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
#########################
# Lowercase #
#########################
lalpha-sv = [abcdefghijklmnopqrstuvwxyzåäö]
lalpha-space-sv = [abcdefghijklmnopqrstuvwxyzåäö ]
lalpha-numeric-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789]
lalpha-numeric-space-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789 ]
lalpha-numeric-symbol14-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789!@#$%^&*()-_+=]
lalpha-numeric-symbol14-space-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789!@#$%^&*()-_+= ]
lalpha-numeric-all-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
lalpha-numeric-all-space-sv = [abcdefghijklmnopqrstuvwxyzåäö0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/ ]
###################
# Mixcase #
#########################
mixalpha-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ]
mixalpha-space-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ ]
mixalpha-numeric-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789]
mixalpha-numeric-space-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789 ]
mixalpha-numeric-symbol14-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=]
mixalpha-numeric-symbol14-space-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+= ]
mixalpha-numeric-all-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/]
mixalpha-numeric-all-space-sv = [abcdefghijklmnopqrstuvwxyzåäöABCDEFGHIJKLMNOPQRSTUVWXYZÅÄÖ0123456789!@#$%^&*()-_+=~`[]{}|\:;"'<>,.?/
- You can use any of the char set value to generate the list.
- For showing you we have select ualpha to generate the list.
- For using any char set type:
crunch 8 8 -f /usr/share/crunch/charset.lst ualpha -o root/newwordlist.txt
- 8 is the minimum number of password length and next 8 is the maximum number of password length.
- /usr/share/crunch/charset.lst ualpha will be used particular charset to generate the list.
- -f to use the charset.lst in order create crunch.
root@kali:/usr/share/crunch# crunch 8 8 -f /usr/share/crunch/charset.lst ualpha -o root/iicybersecurity/newlist.txt Crunch will now generate the following amount of data: 1879443581184 bytes 1792377 MB 1750 GB 1 TB 0 PB Crunch will now generate the following number of lines: 208827064576
- After executing the above command, crunch has generated the list which can be used in mass level of attacks.
As per ethical hacking researcher of International Institute of Cyber security wordlist should be handy while doing penetration testing and there are other method to create wordlist using twofi
Now time to generate your own wordlist and try cracking password using john the ripper

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.