SHODAN:- Shodan is a scanner which finds devices connected over the internet. Shodan can finds devices like traffic lights, security cameras, home heating devices and baby monitors, ethical hacking consultants assure. This web scanner can also finds the SCADA system like -gas stations, nuclear power plants. Shodan tells the physical location of connected devices over the internet.
Ethical hacking researcher says that shodan can creates violation on users privacy because it ping almost on any device connected over the internet without taking users permission.
For using shodan go to: https://www.shodan.io/
- For creating an account go to https://account.shodan.io/register
- Shodan search engine can also be used without signing up. Signing up is not compulsory.
- Enter the necessary details- your username,password and email for signing up in shodan.
- After creating an account sign in with your credentials.
- After singing in, shodan will open. Now you can explore shodan.
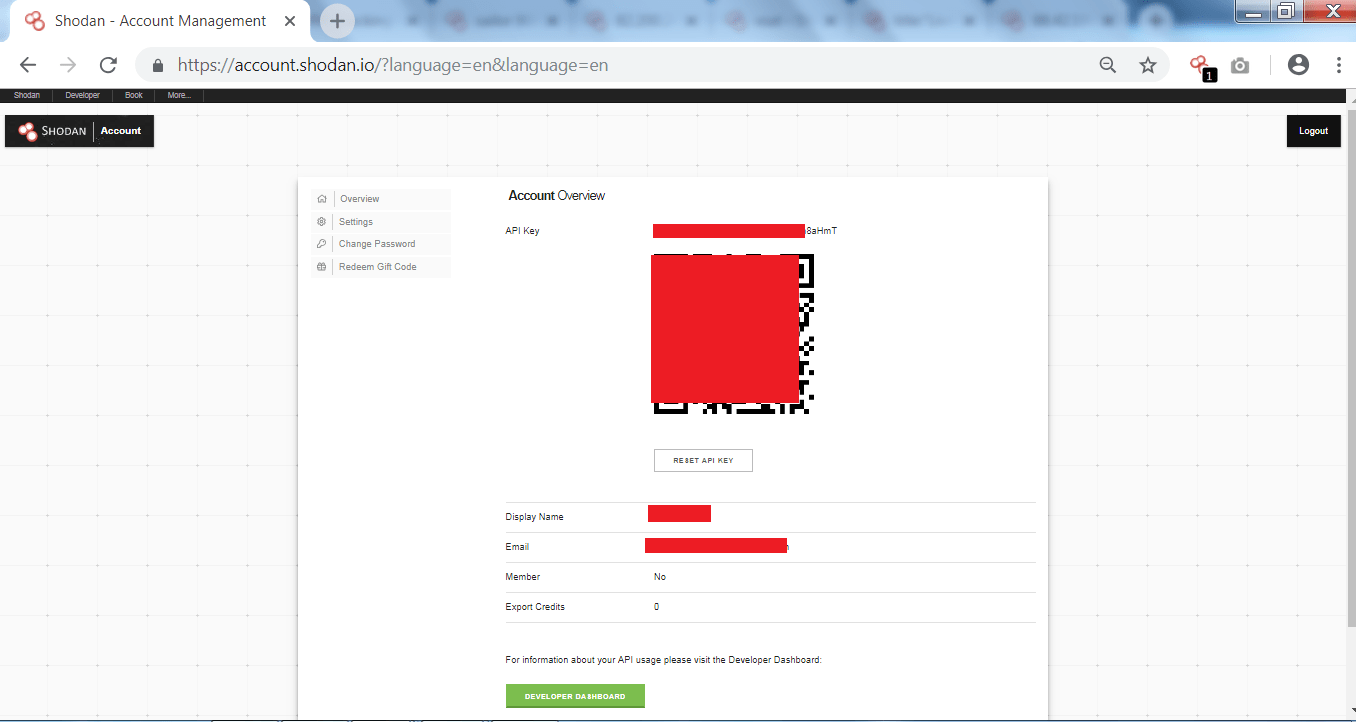
- After creating your account in shodan. Sign in to your account and shodan will show your account api key. For security reasons the key has been hided (ZoxxxxxxPFmYHJvSWhKixxxxxxxxxxHmT).
- You can also use the API key in recon-ng for reconnaissance.
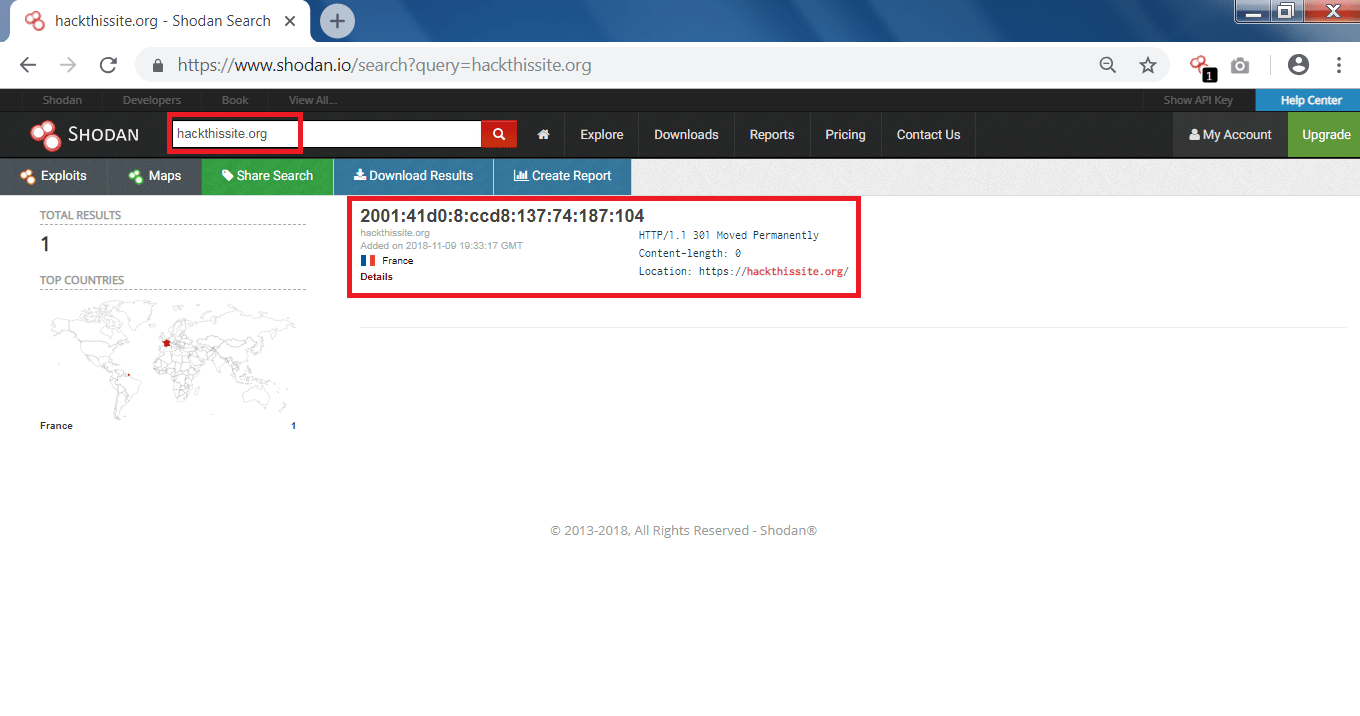
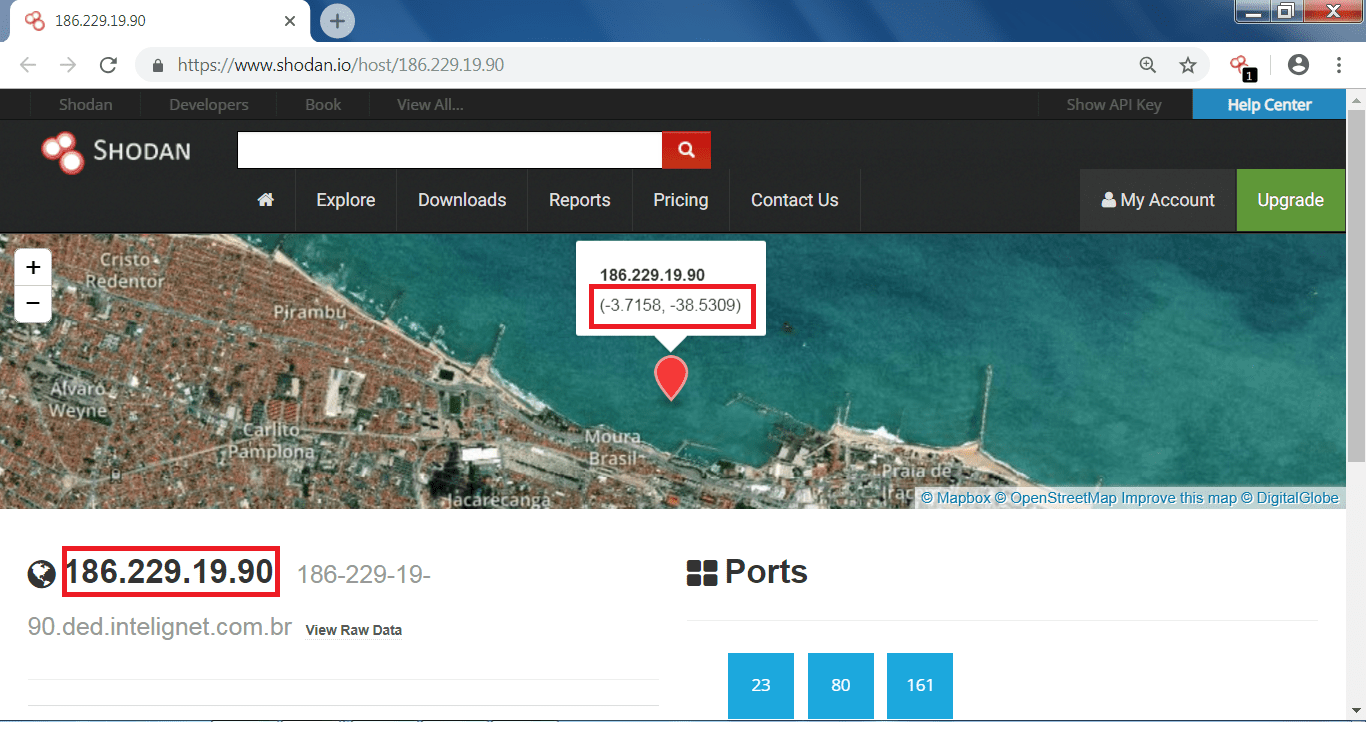
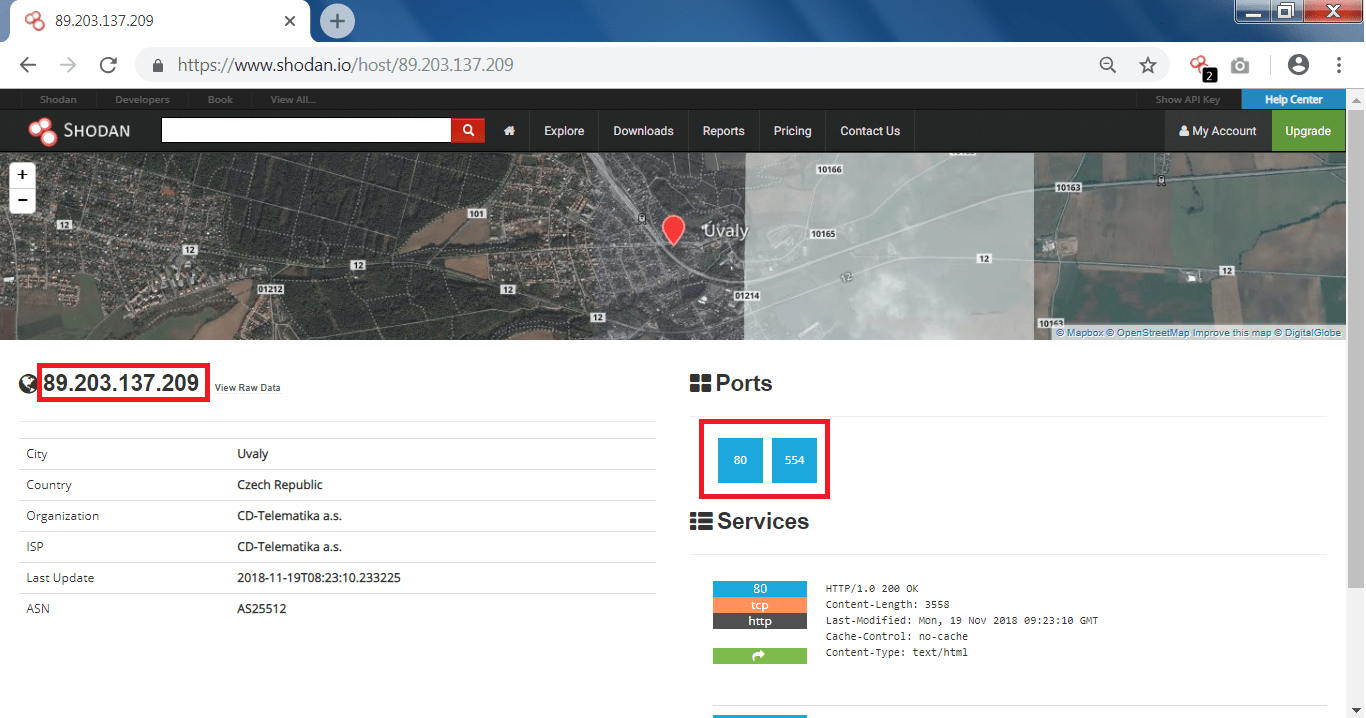
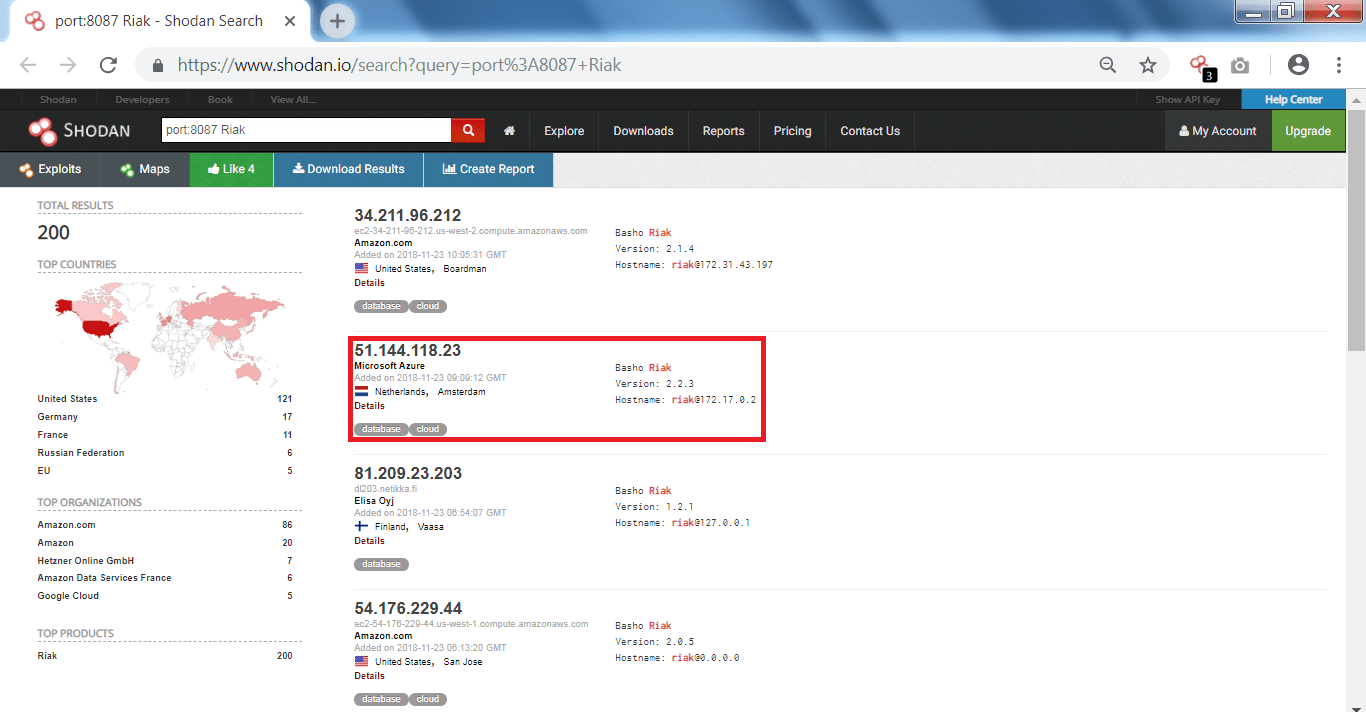
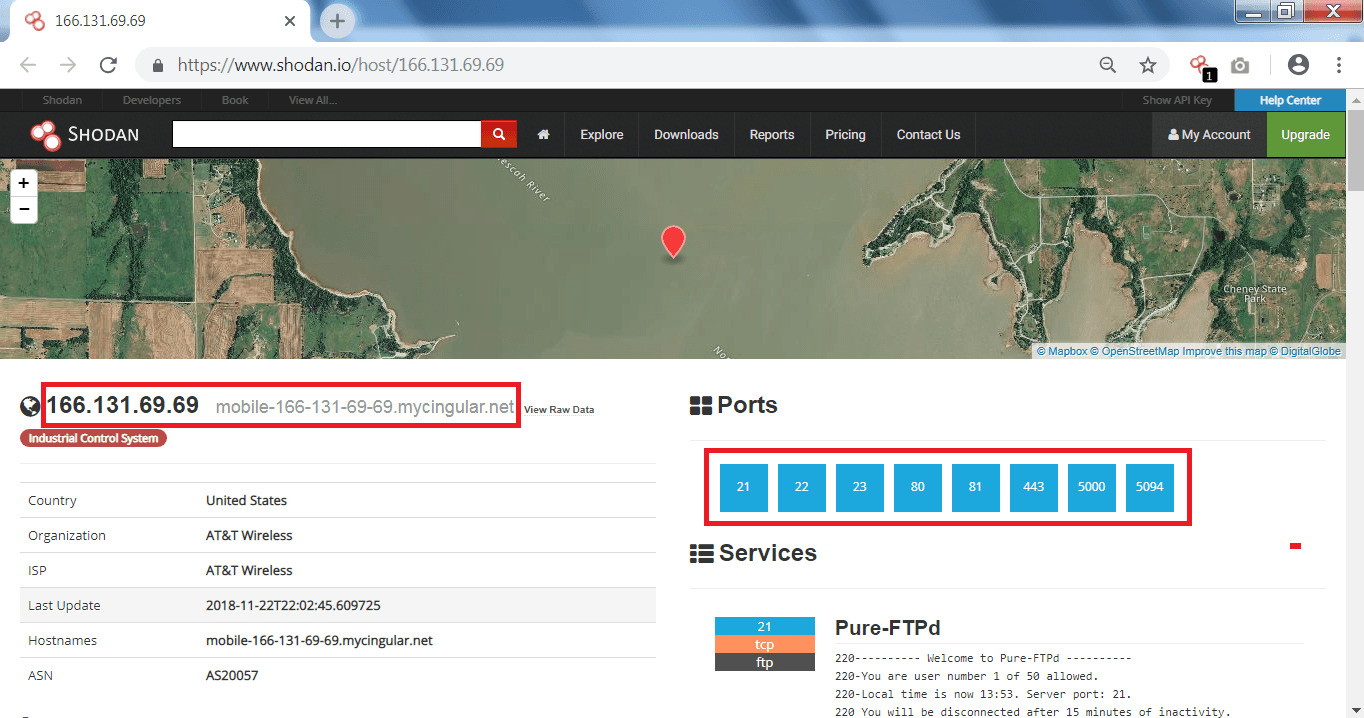
- You can also search any website/IP address simply enter the your target name and as you see below it will show the details of the target, mention ethical hacking investigators.
Fun with SHODAN:-
- The below site in the screen shot is most popular for testing your hacking skills.(hackthissite.org)
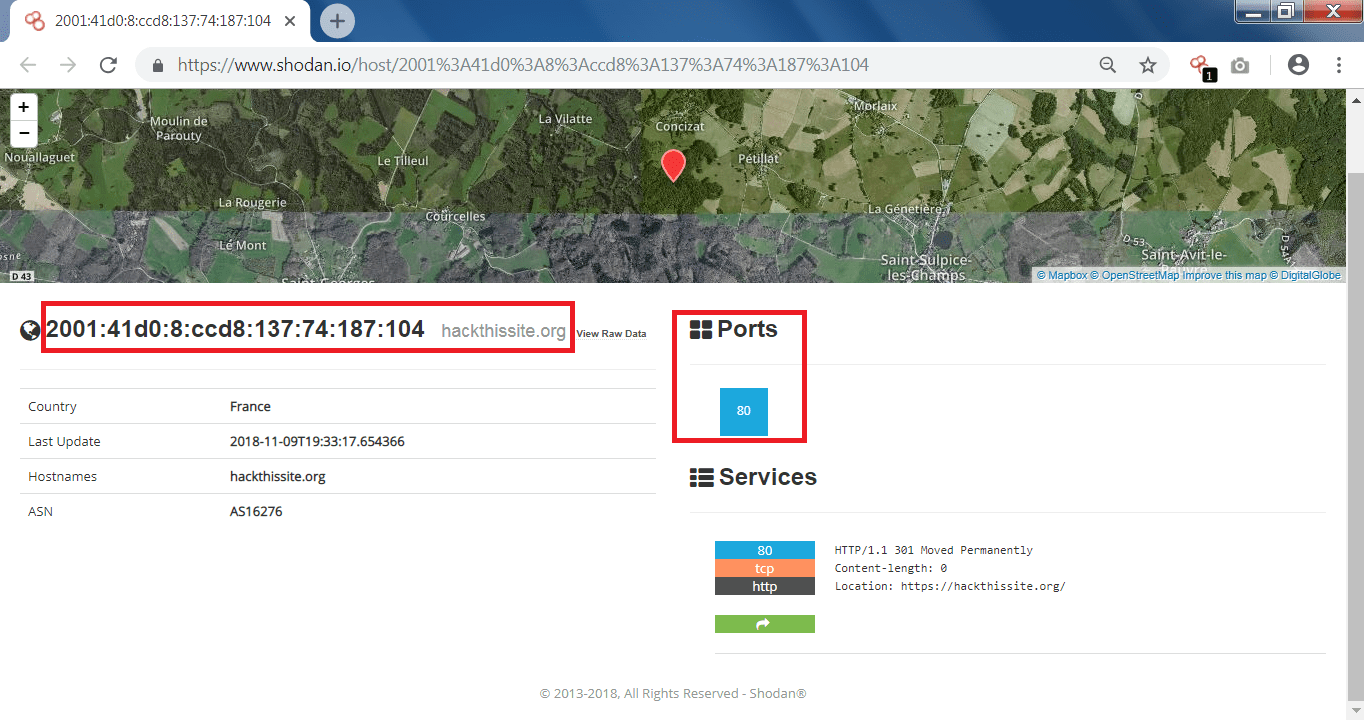
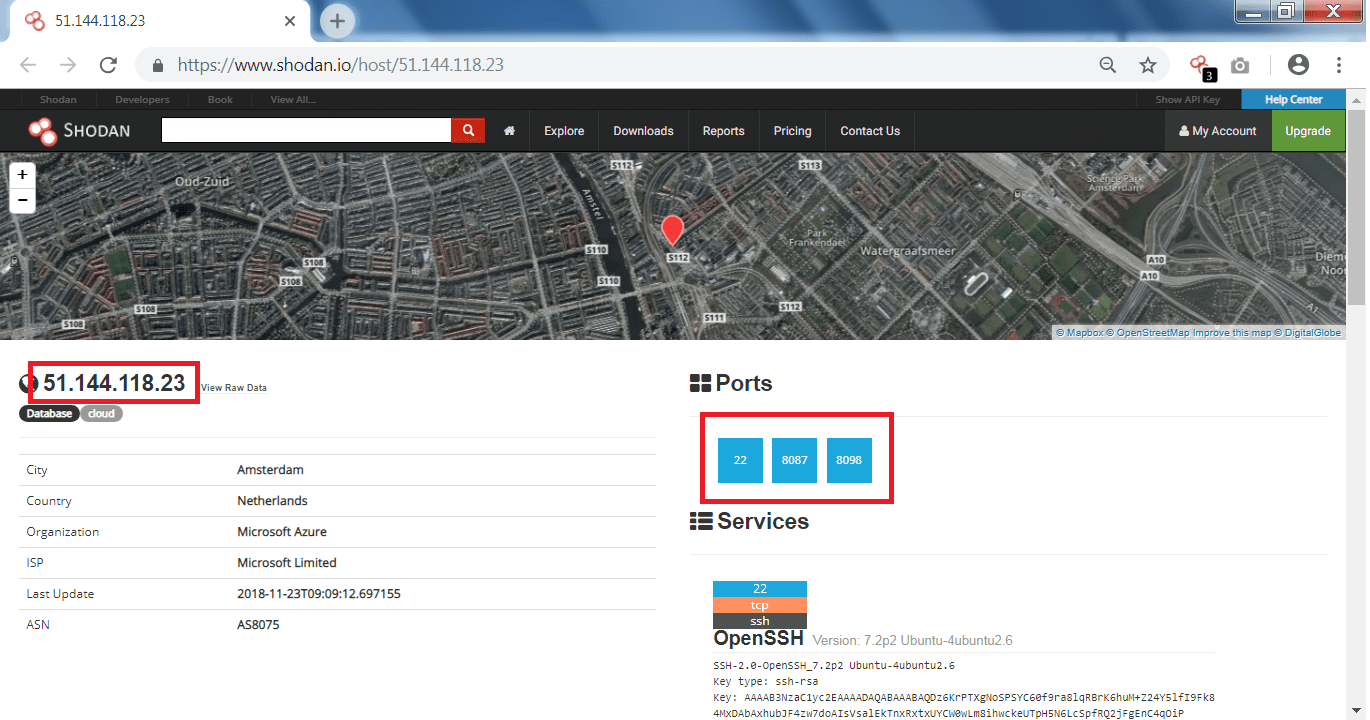
- After typing the target website, open ports and the IP address has found which can be used in footprinting and reconnaissance.
SHODAN FEATURES:-
Shodan offers many great features to search. Normal user can easily explore shodan. Most of the pentesters use shodan for finding vulnerabilities, according to ethical hacking courses.
There are many keywords to search in shodan and here are some of the keywords which have been used to show you how shodan works:-
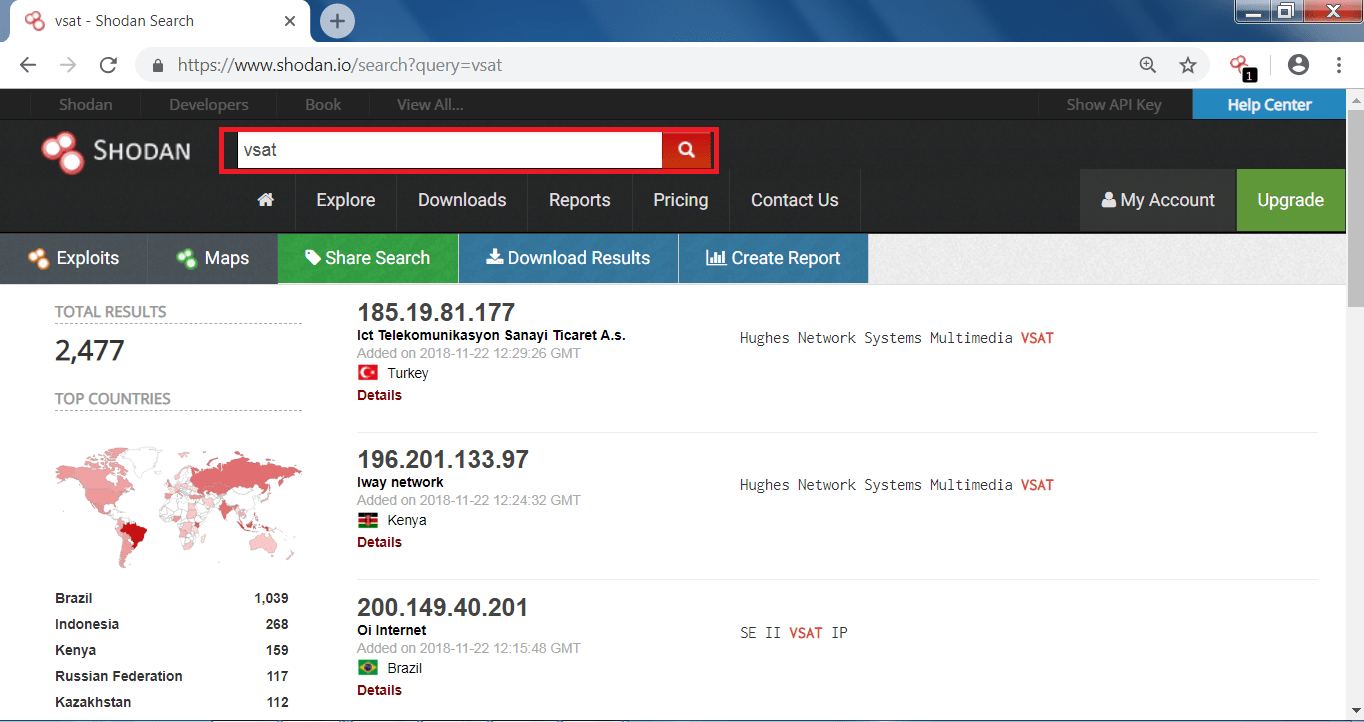
- VSAT – Mainly works in boats/ship tracker to detect boats/ship location.
- Cameras – Shows the open IP’s of the web-cameras which are used in surveillance.
- Exploring the other like – databases, video game servers, Industrial Control System.
- Databases – show the databases with lack of security.
- Video Game Servers – shows the running open servers of the games.
- ICS (Industrial Control System) – shows the open ICS systems which are vulnerable.
SEARCHING BOATS/SHIPS ON SHODAN:-
Boats/ships uses VSAT (Very-Small-Aperture Terminal) which uses satellite communication to communicate with the outer world. VSAT uses IPv4 for the communication. As shodan ping all the IP addresses over the internet, so in this pinging process shodan also list’s the IP’s associated with VSAT communication on the boat. Now in the below screens you will see how a normal internet user can search the boats in the sea.
===================SNIP=================
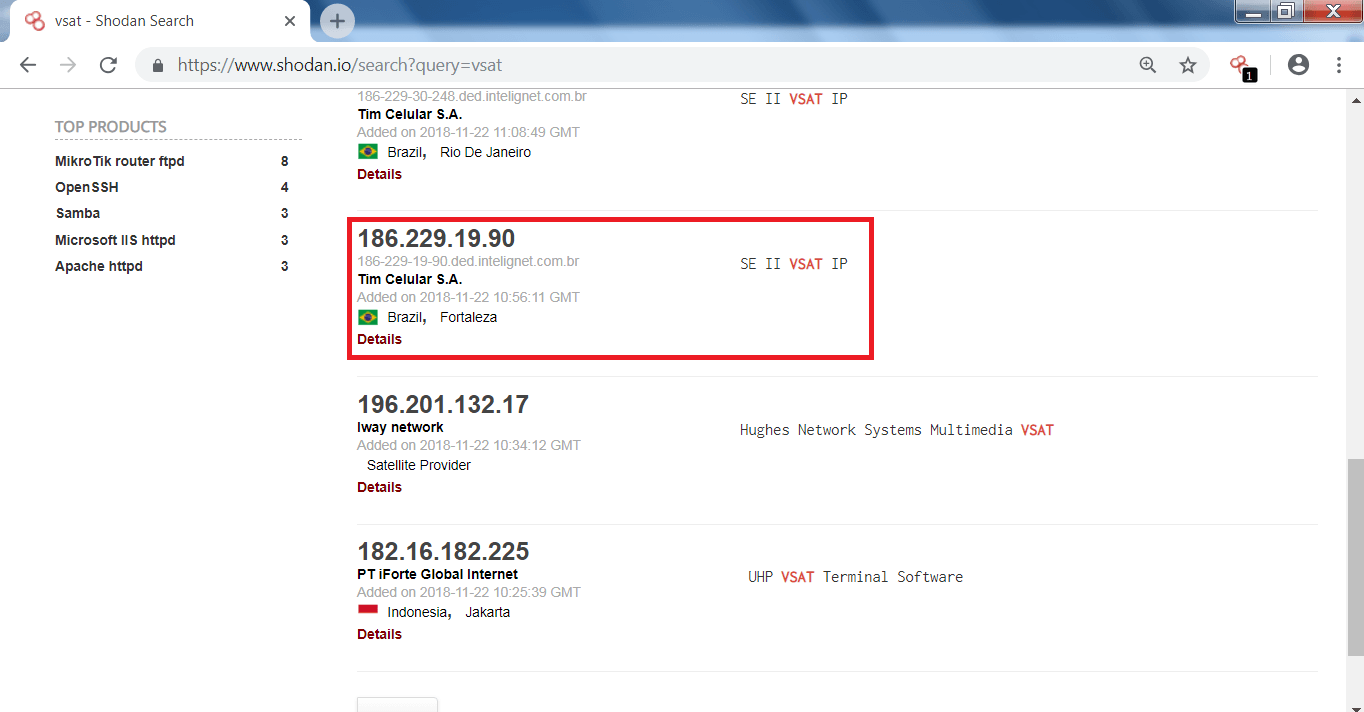
- if you type VSAT in the search engine of shodan you will find there are many unprotected IP’s of the ship.
- You can see in the above screen shots, open ports and IP address of the ship which can be used in other hacking activities.
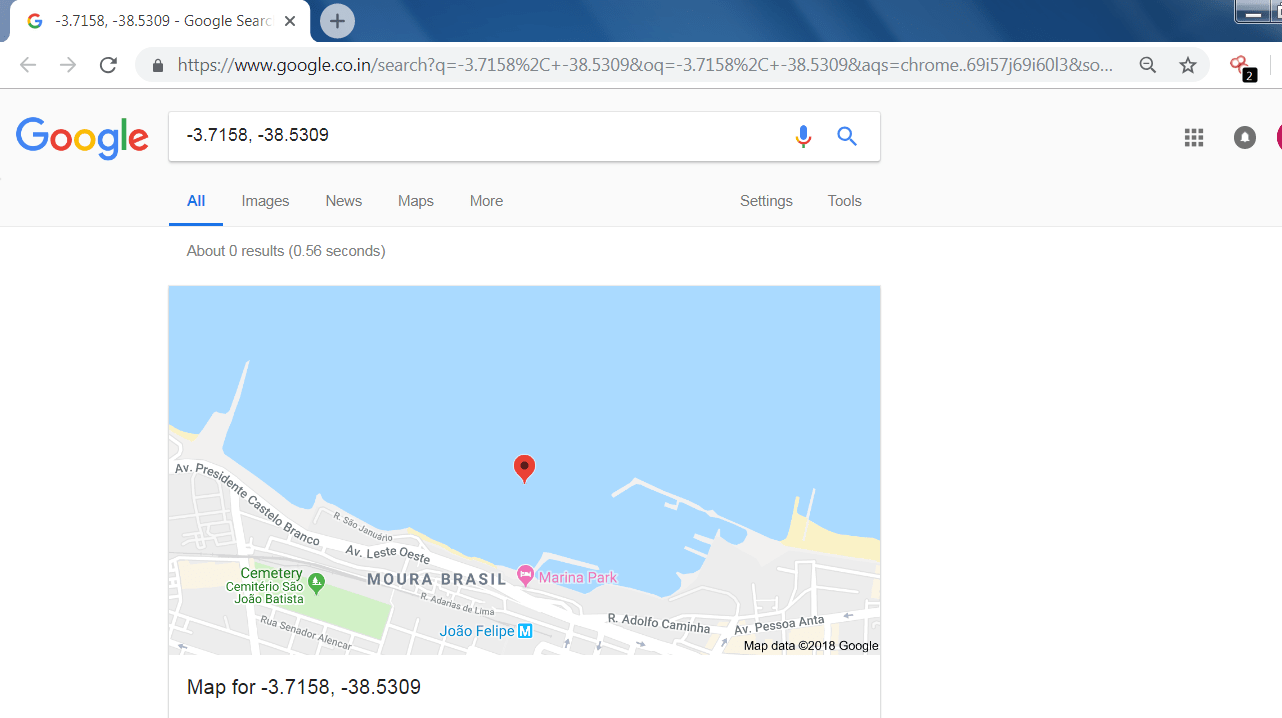
- You can also check the location of the ship by typing the longitude and latitude of the ship in the google search engine.
SEARCHING LIVE CAMS:-
You can search the live cameras with open ports.For searching the live webcams. go to shodan search engine and type webcams.
For example :-
- For searching webcams, you can type webcams or the query of the webcam which mostly URL path used by IP camera
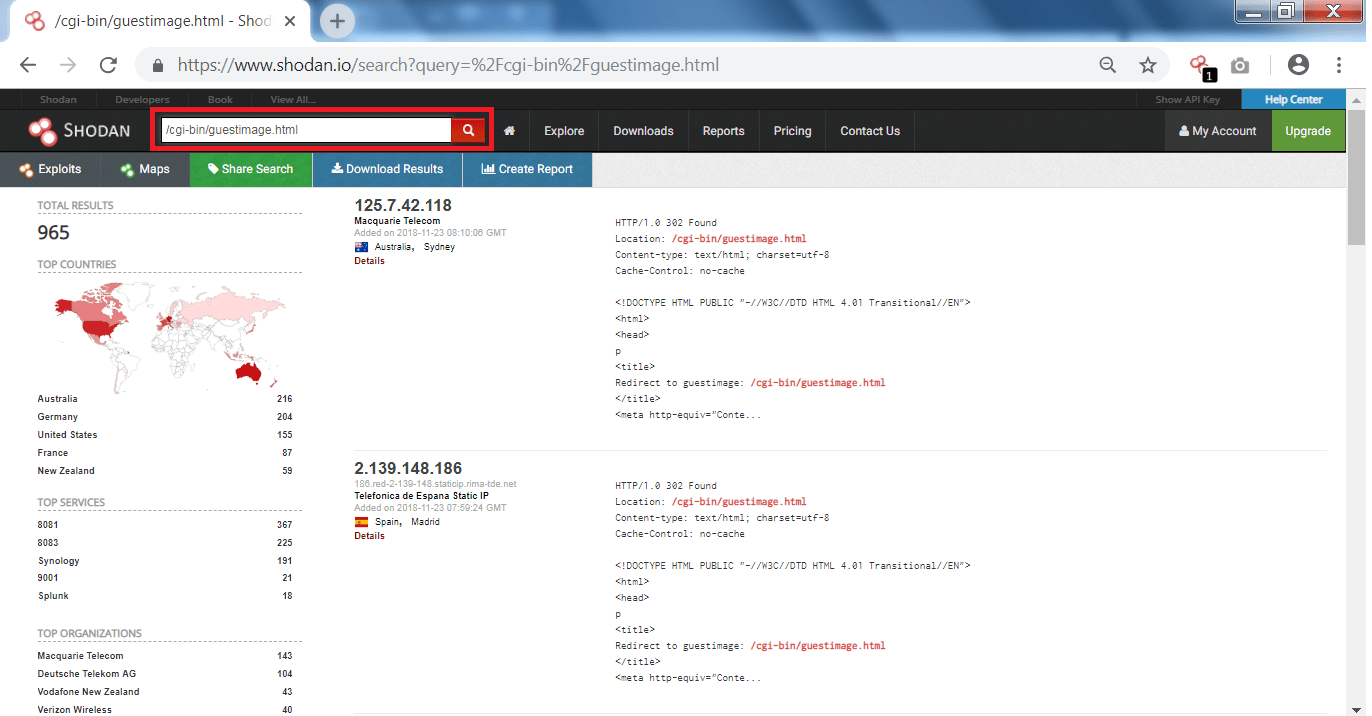
- So we will search /cgi-bin/guestimage.html
- The above URL path is normally used by Mobotix company which makes IP surveillance camera.
===================SNIP================
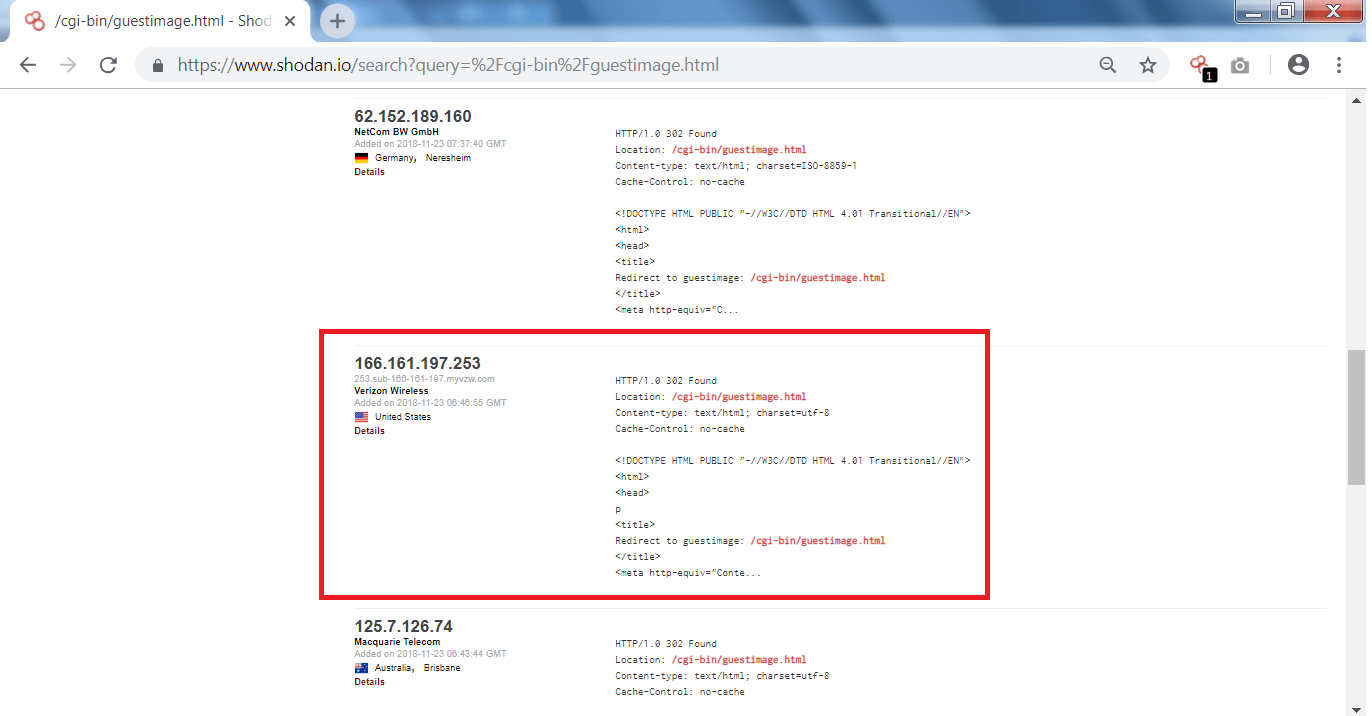
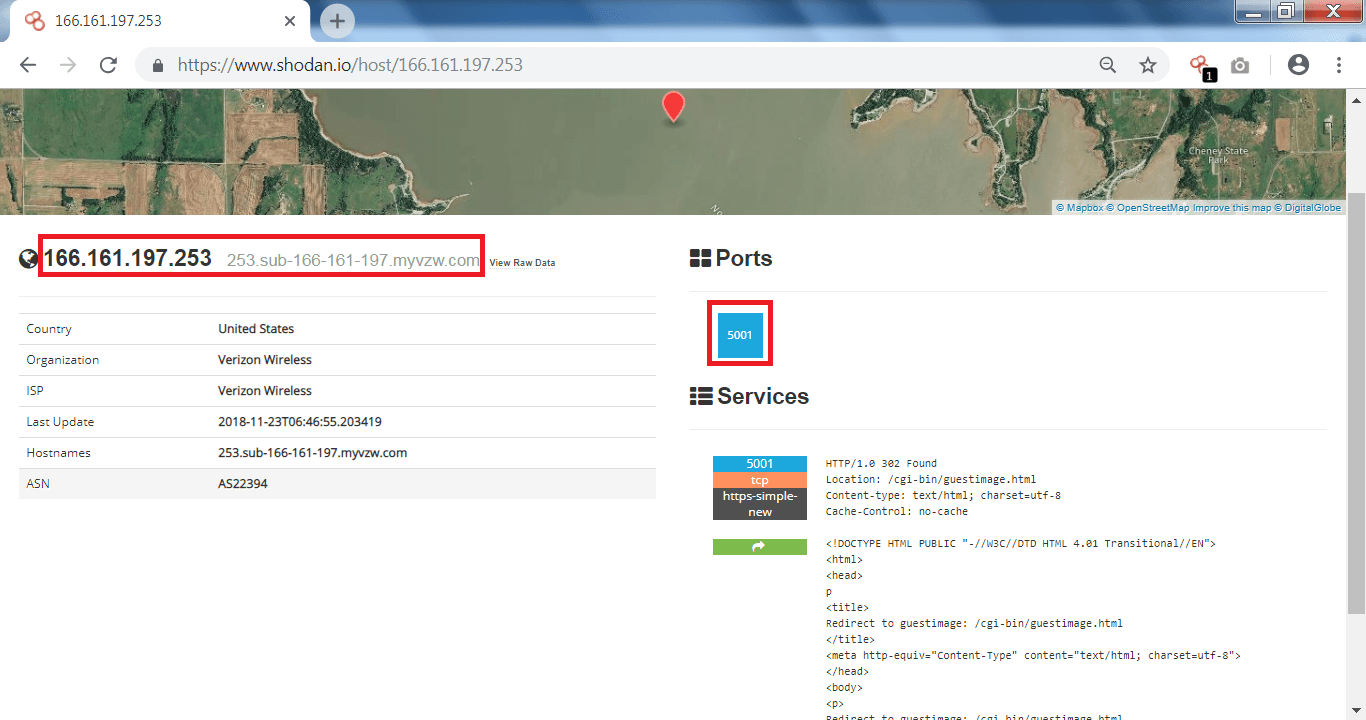
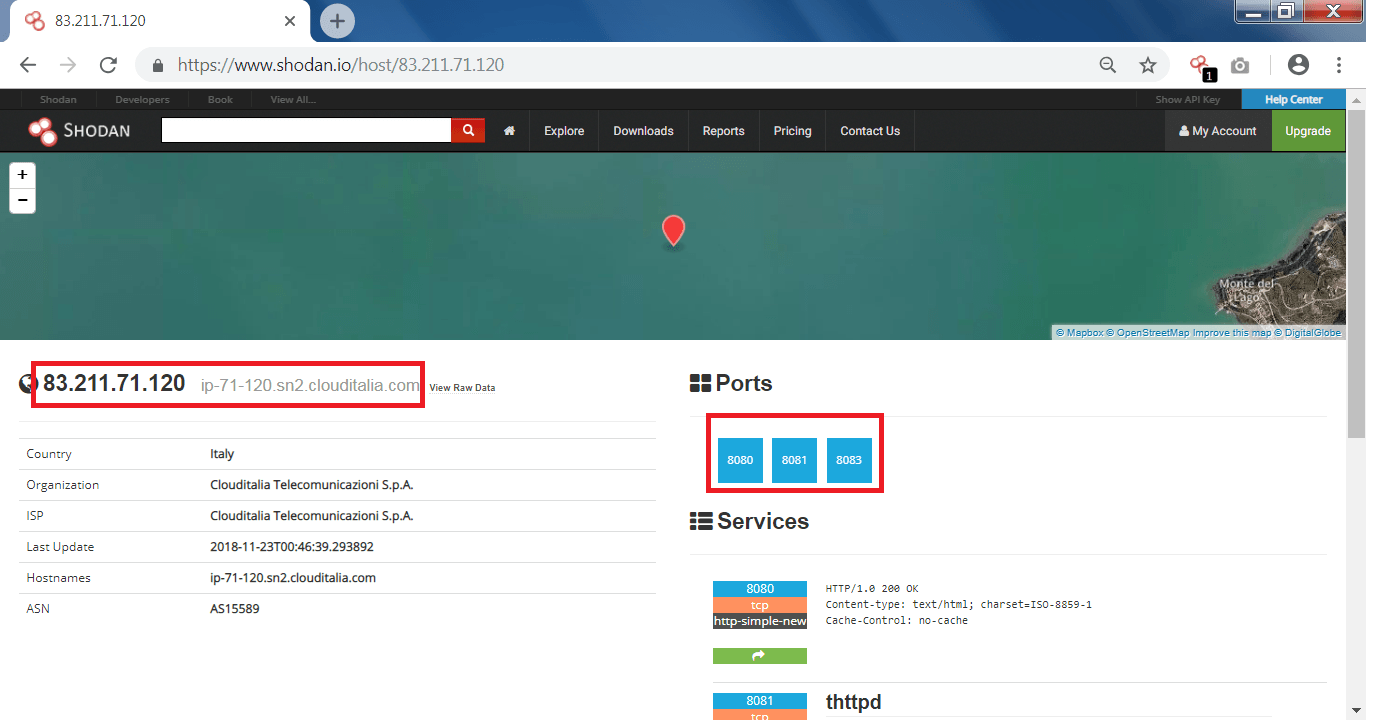
- After searching through the query, there is an IP – 166.161.197.253 which we will examine further.
- After clicking on the IP, You can see open port and the IP address of the myvzw.com from the organisation verizon wireless.
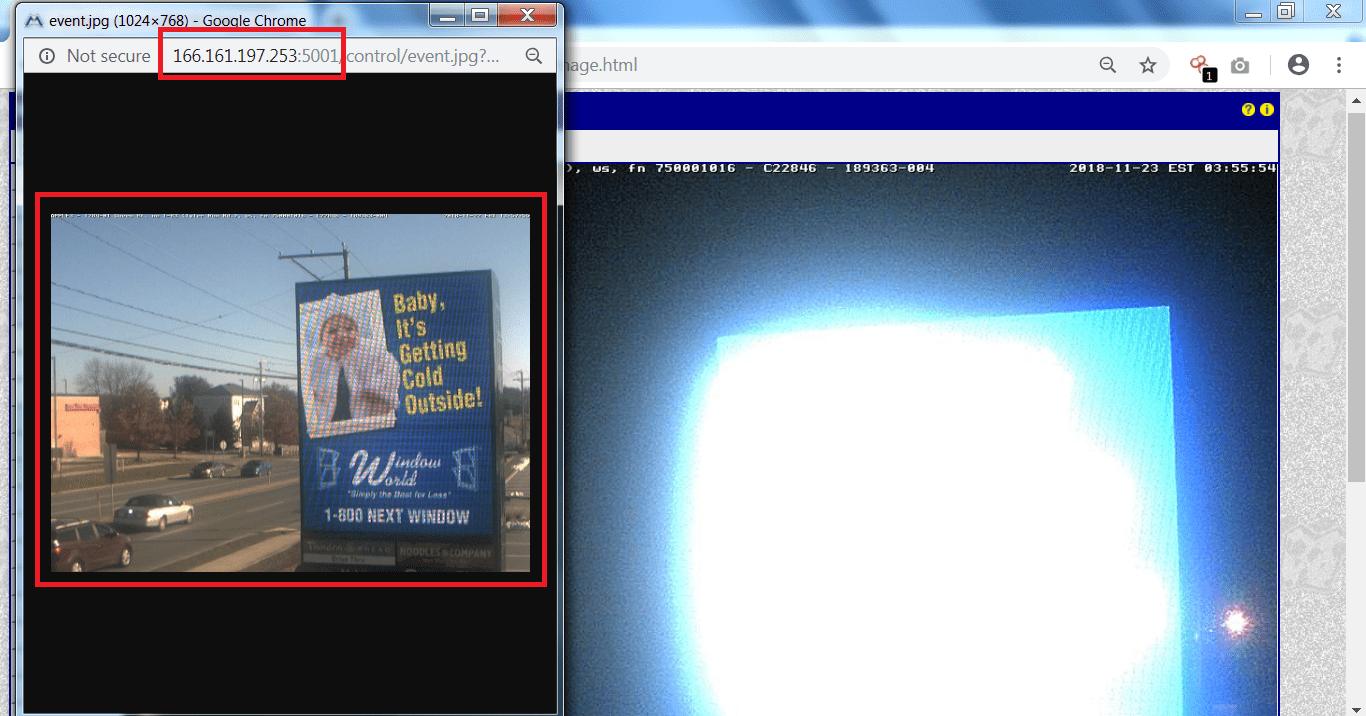
- Now to open IP address type the above IP address with the port into your browser 166.161.197.253:5001 as shown below.
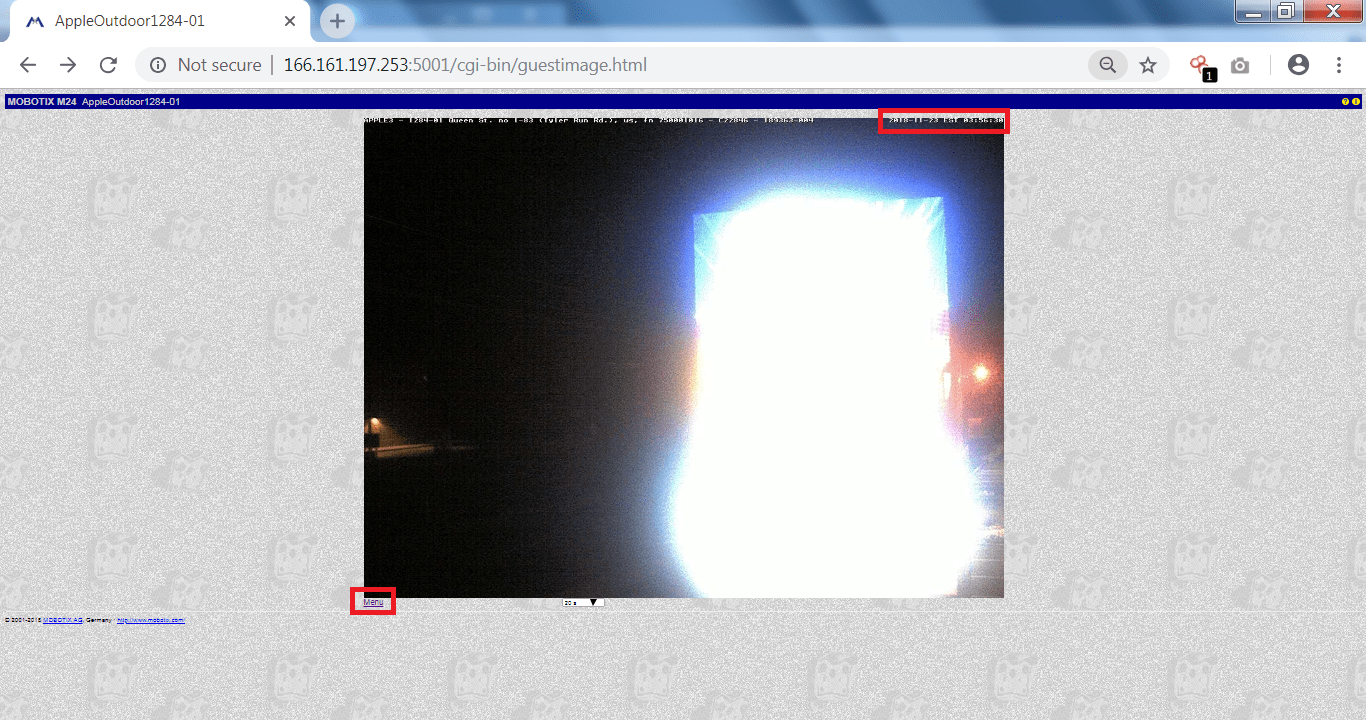
- As you can see the targeted IP camera is working but it is night over there. Now we will try to find some previous recording to check if the camera is working.
- Click on the menu market red in the above screen shot.
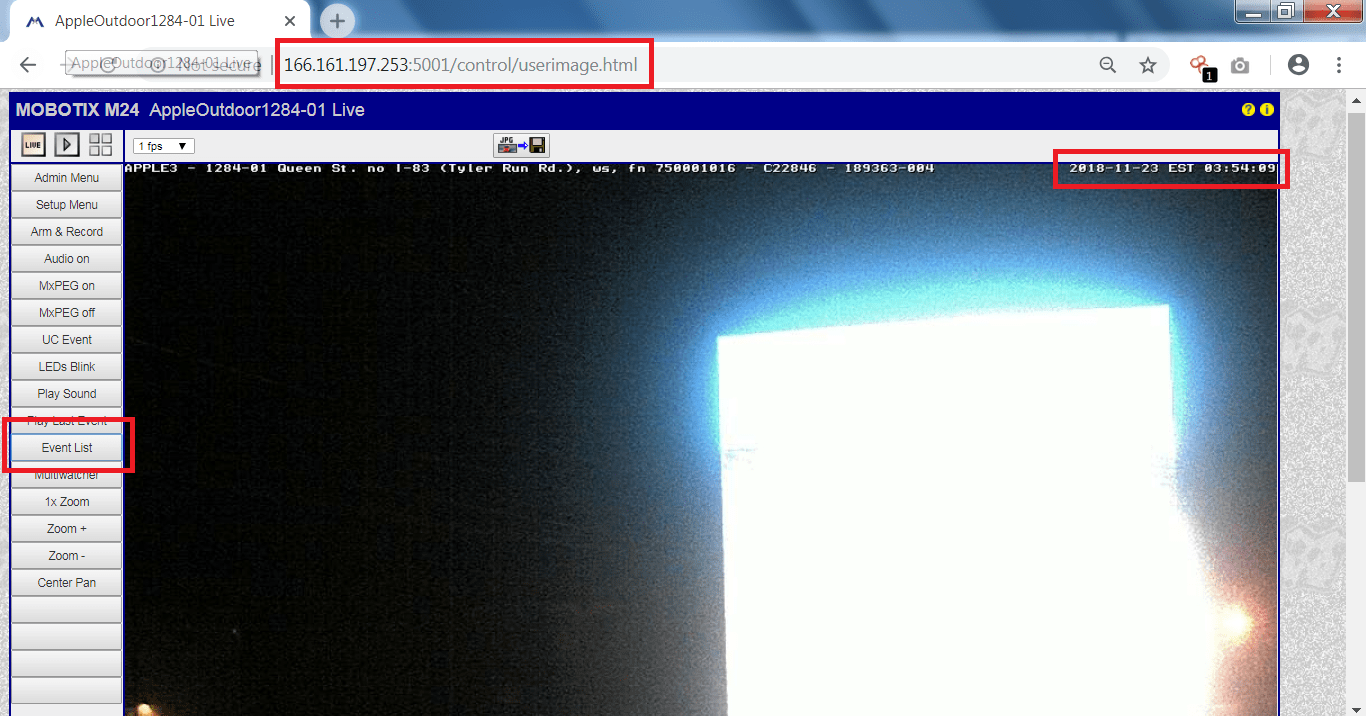
- Go to the event list.
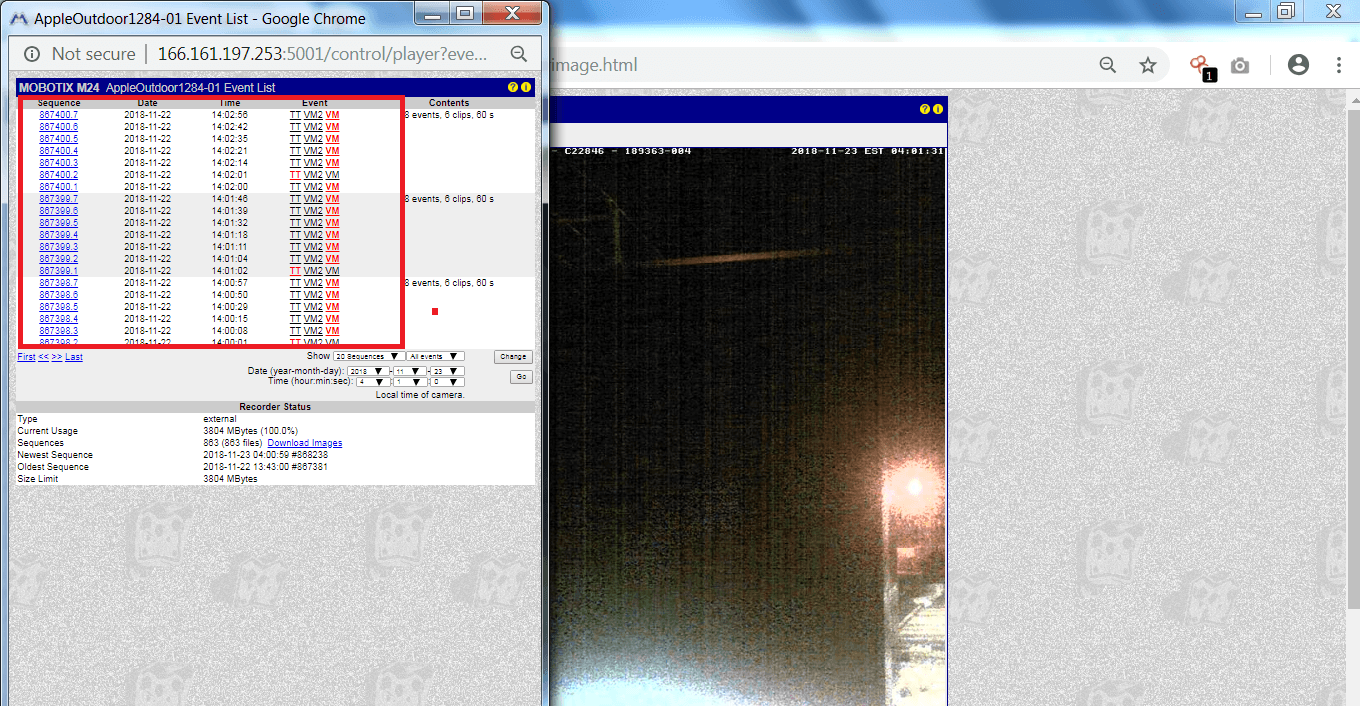
- As there are many previous records.One of the record we will show you the day mode.
- One of the previous record as you can see that this surveillance camera is open to exploit.
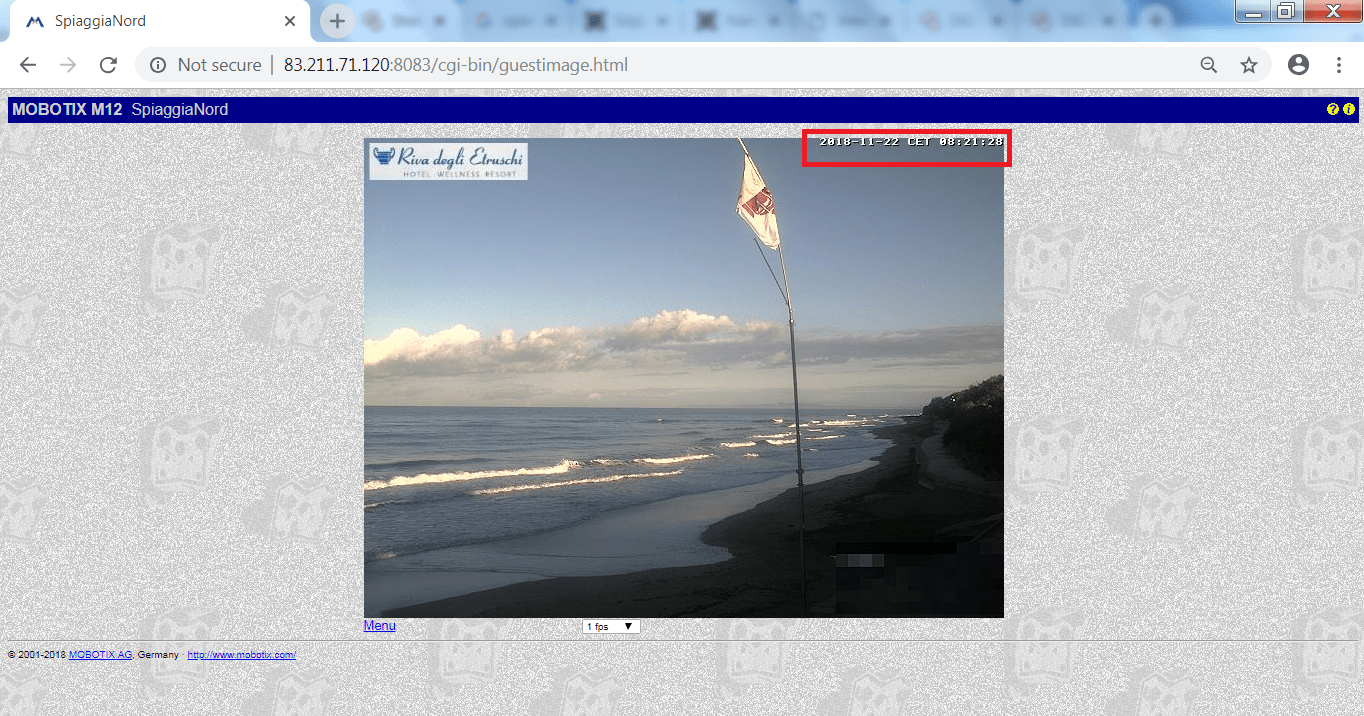
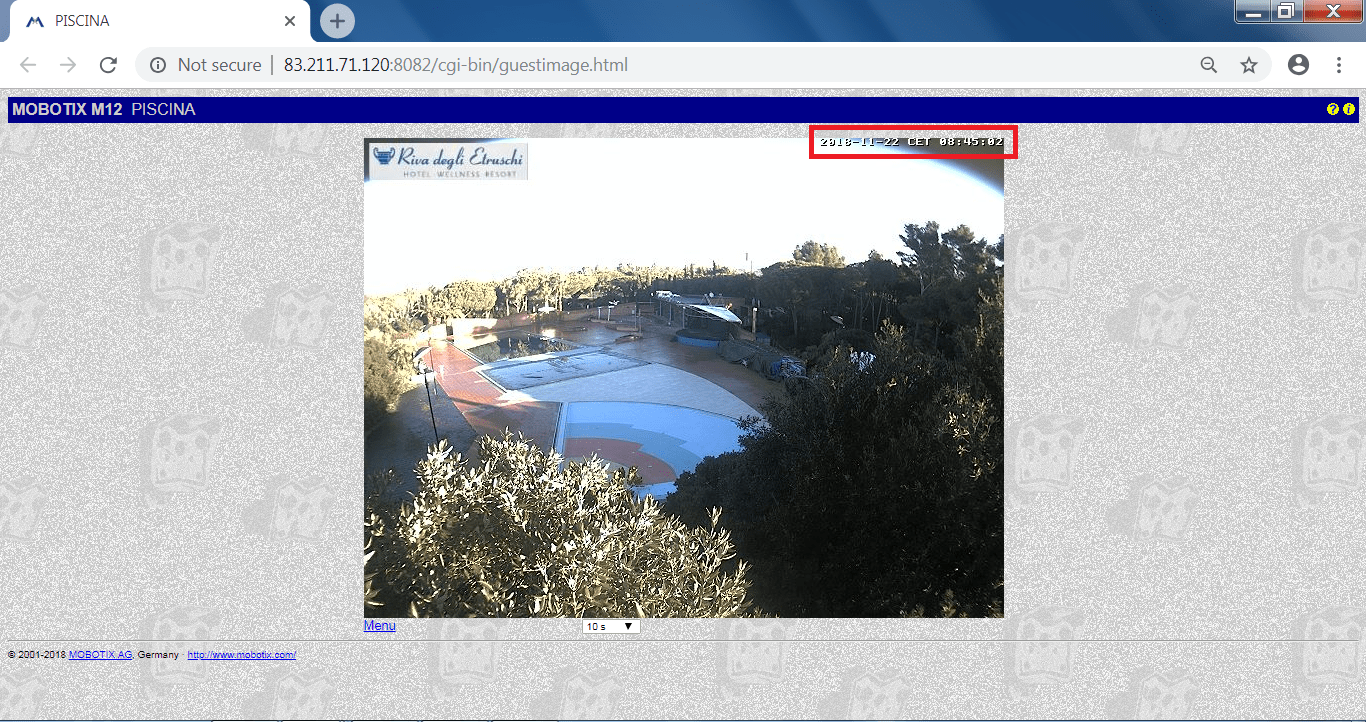
Another surveillance camera which is found in the list.
- When we open the IP address with the listed ports we found that:-
- Beach surveillance camera.
- Above screen shots, are from the Hotel wellness resort (riva degli etruschi).
Another example:-
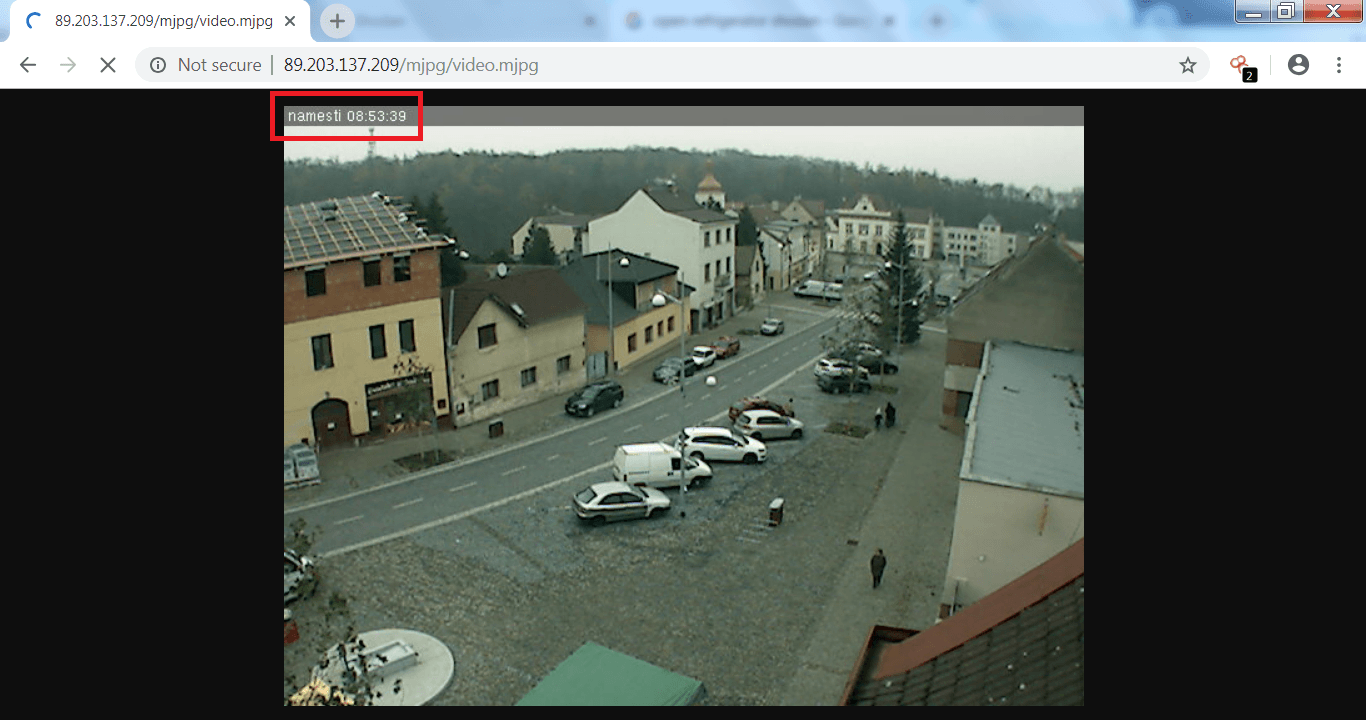
- Opening the IP address 89.203.117.200 shows live surveillance.
- Above screen shot is from Czec Rpublic. A local street location from live cam.
OTHER FEATURES IN SHODAN:-
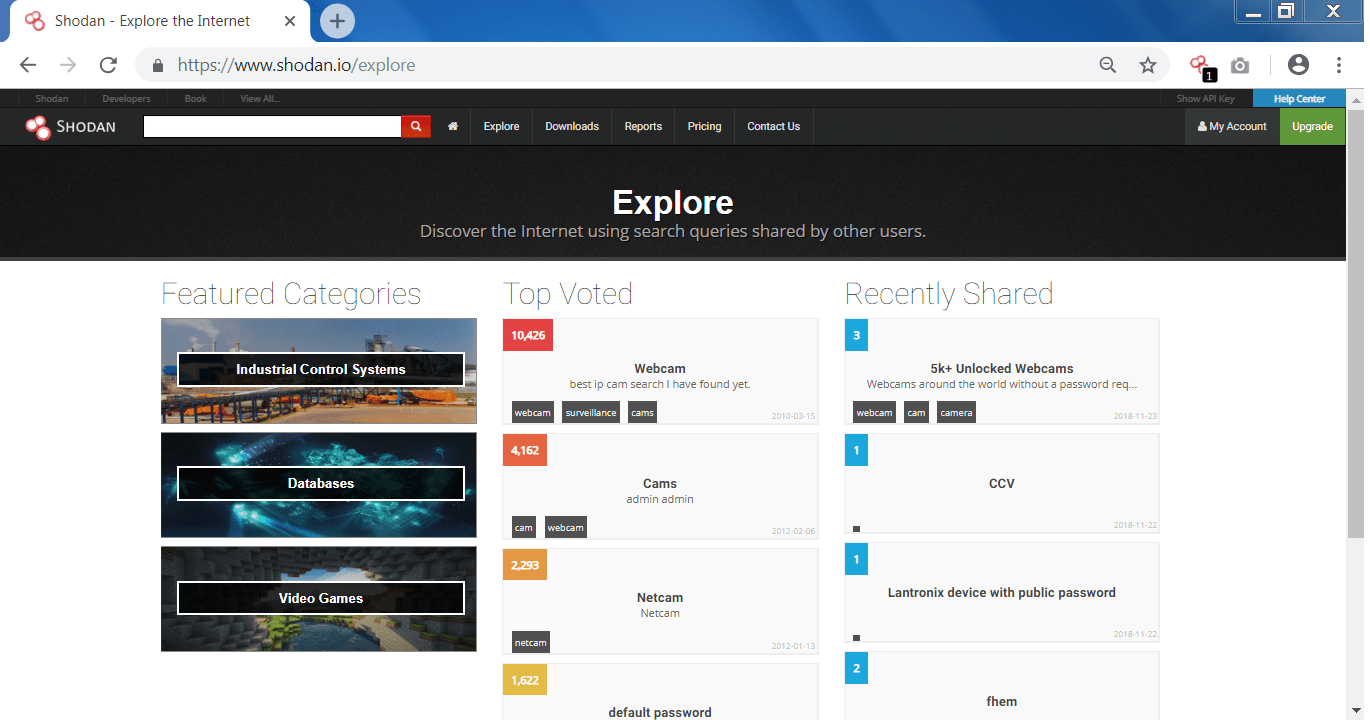
Shodan gives many options to explore.
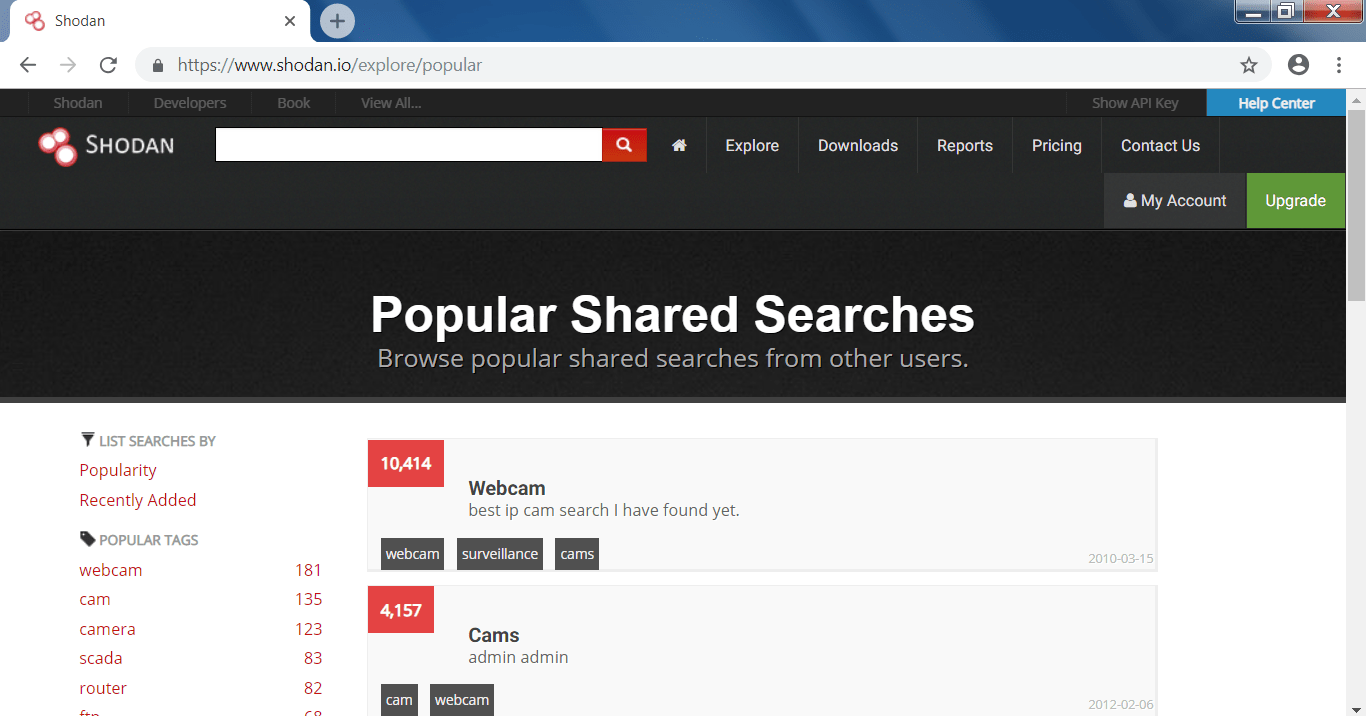
- By clicking on the explore, you can find the most popular searches which has been done in shodan by other users. And shows the most common and recent searches.
- These common searches can be used easily used to exploit them as they have lack of security.
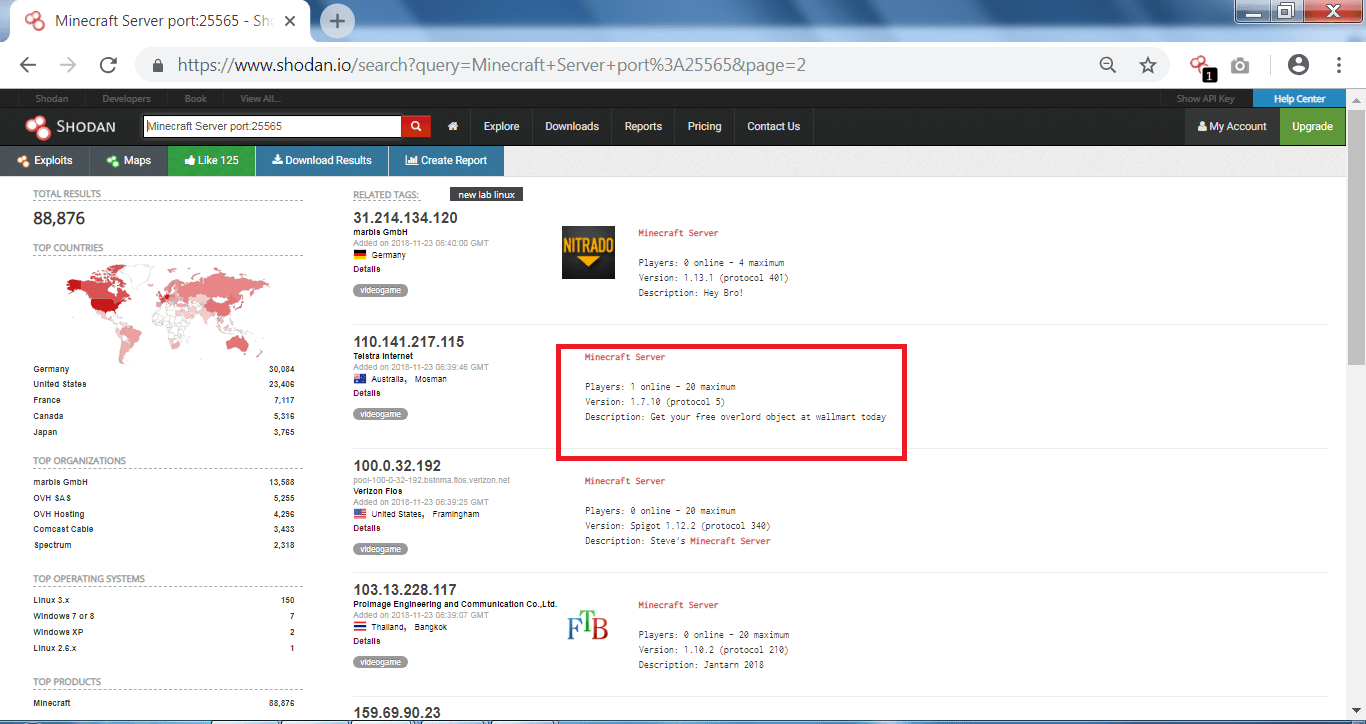
SEARCHING VIDEO GAMES:-
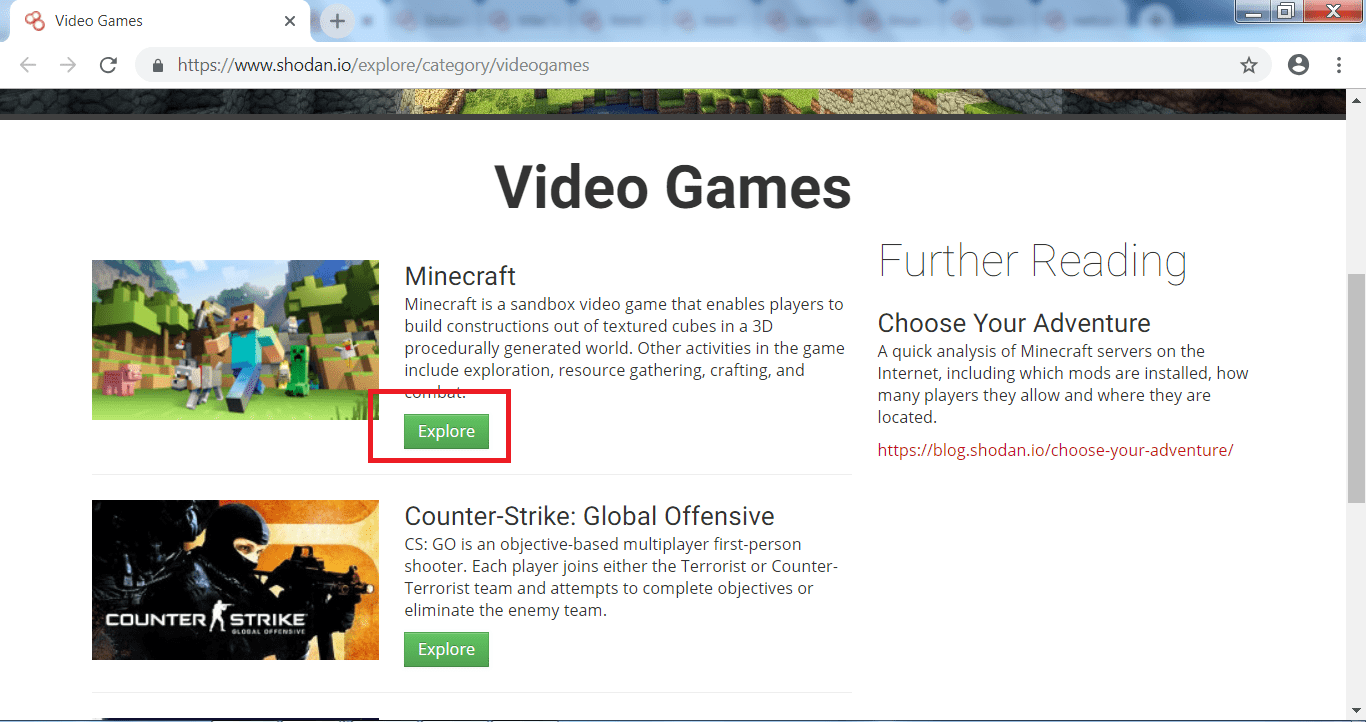
- You can open listed game servers to check IP addresses.
- Here we have chosen the target.
==================SNIP====================
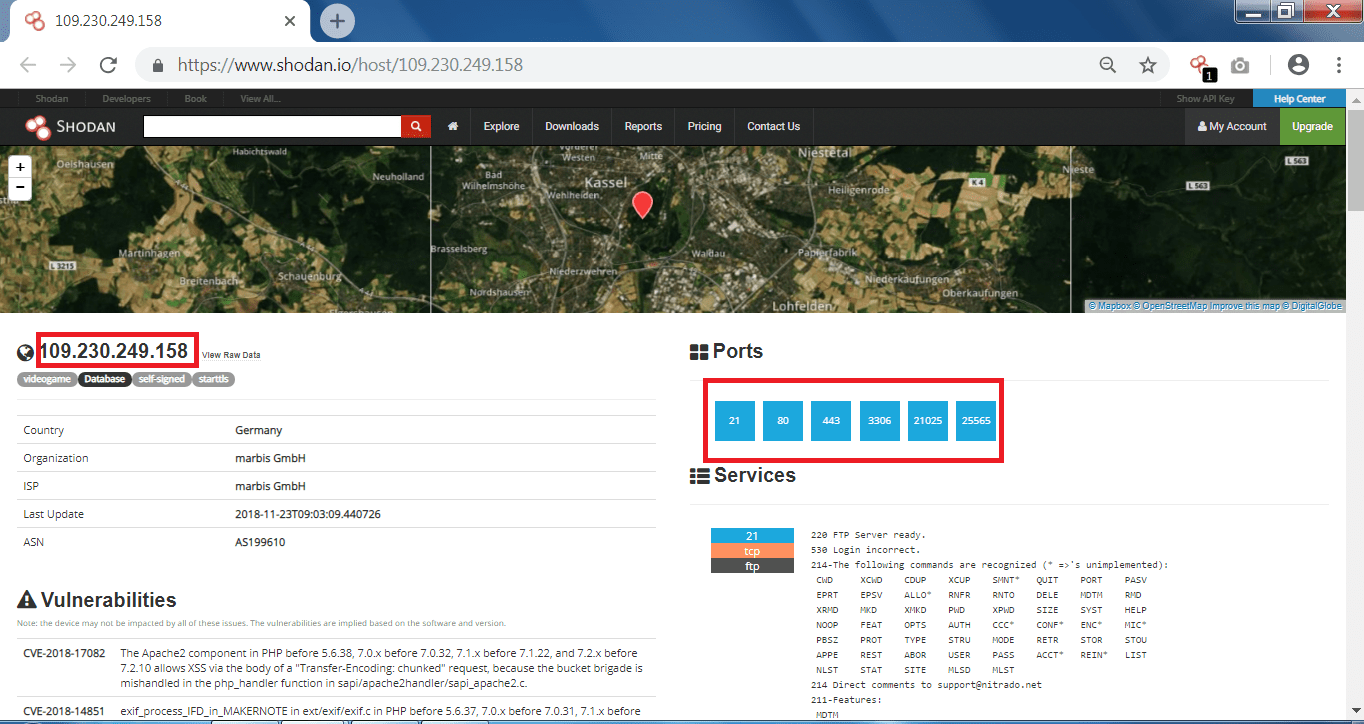
- Minecraft server can be used in port scanning and in other hacking activities.
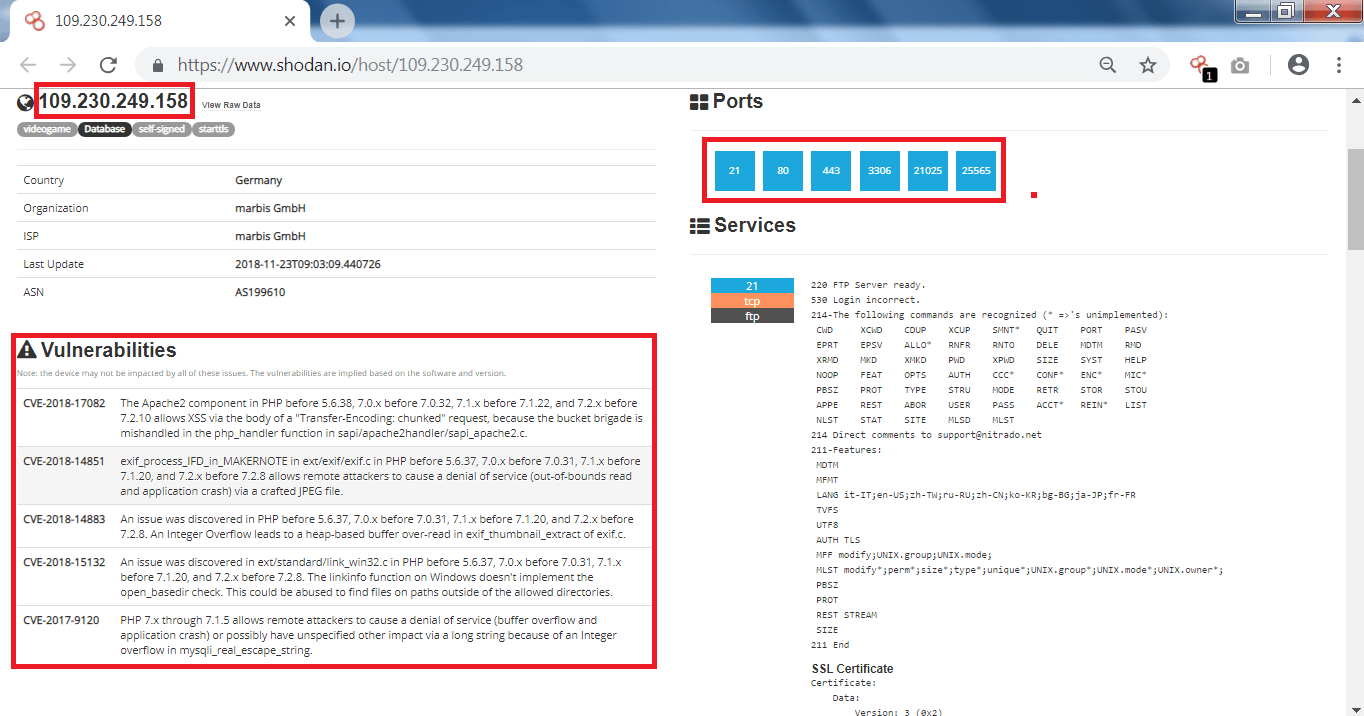
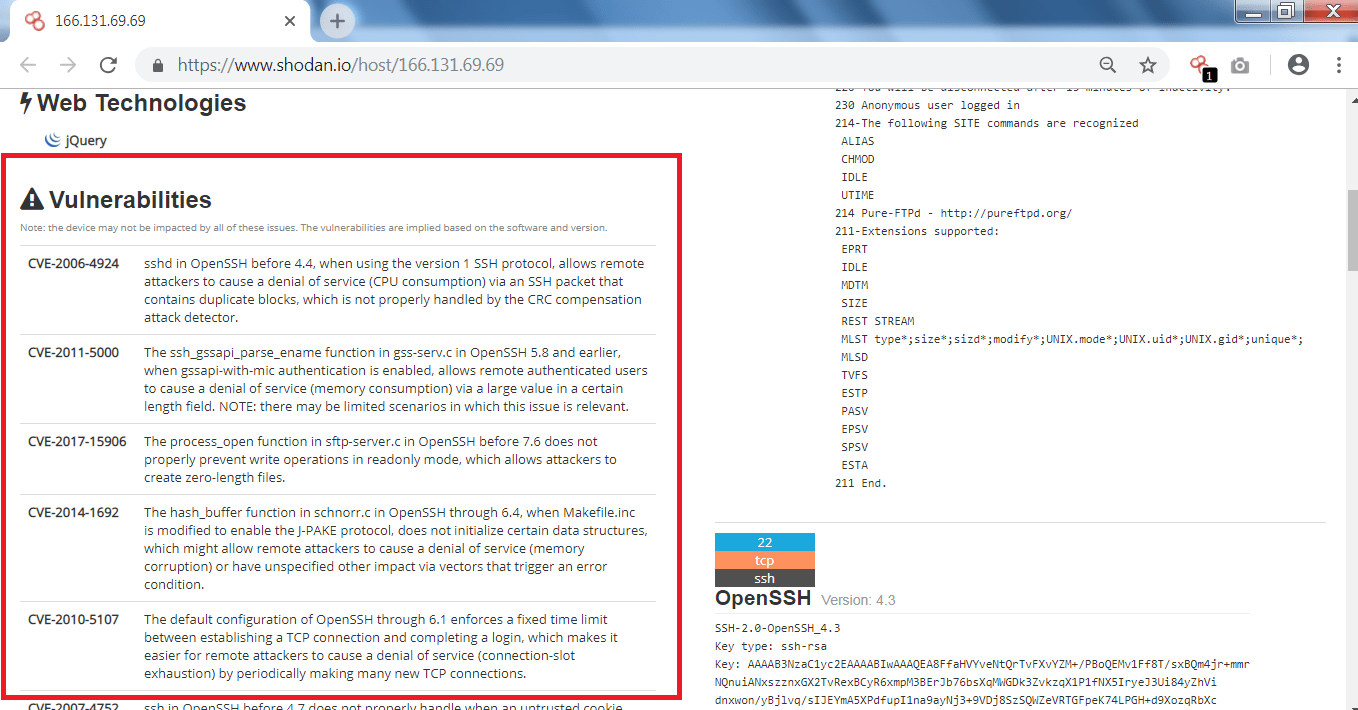
- The above listed vulnerabilities can be used can be used by remote attackers to cause denial-of-service attack. And the vulnerability could allow to get into the directories, as per ethical hacking specialists.
SEARCHING DATABASES:-
- Choose the database.
- Selecting the target.
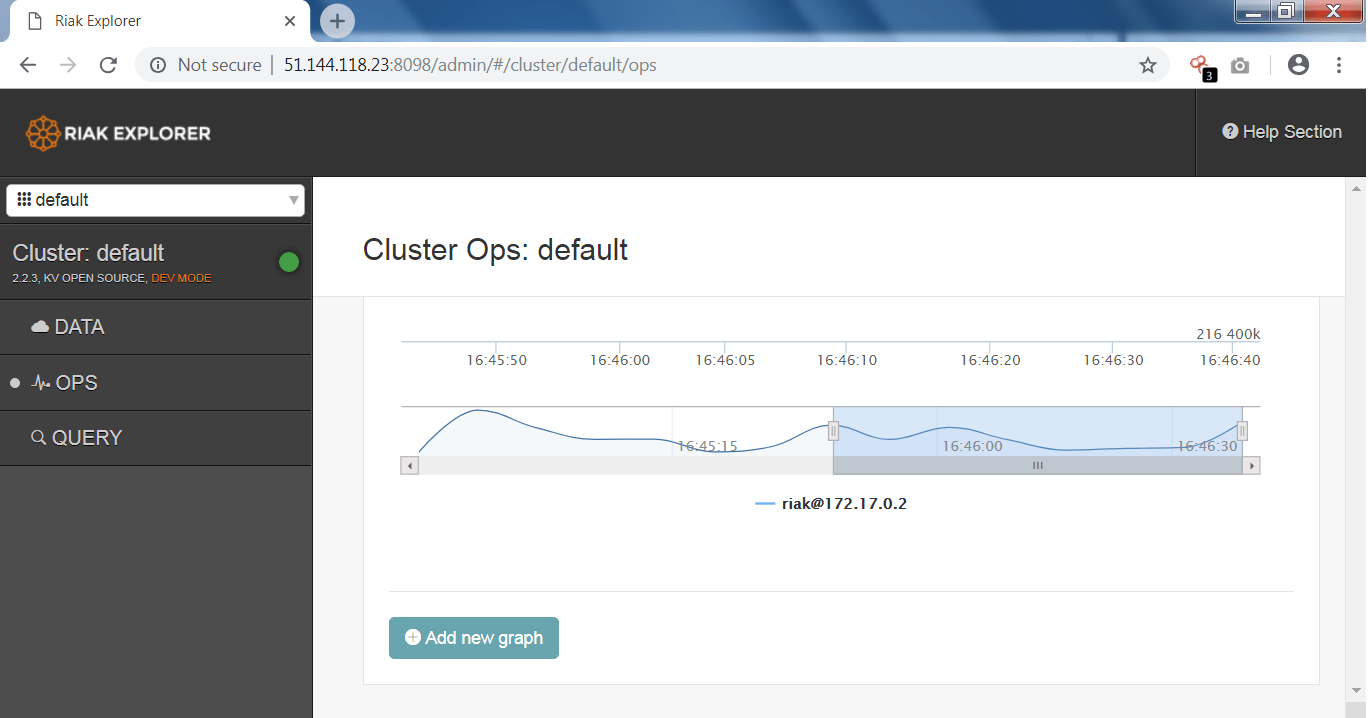
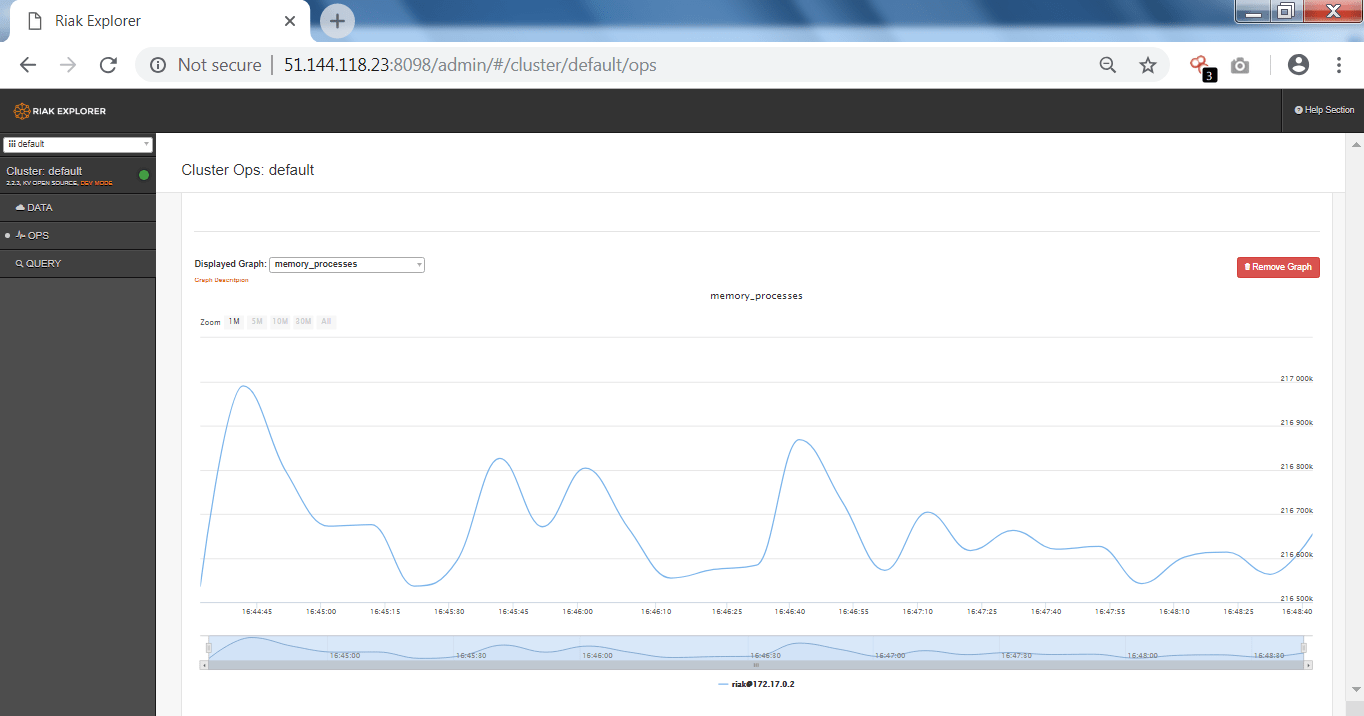
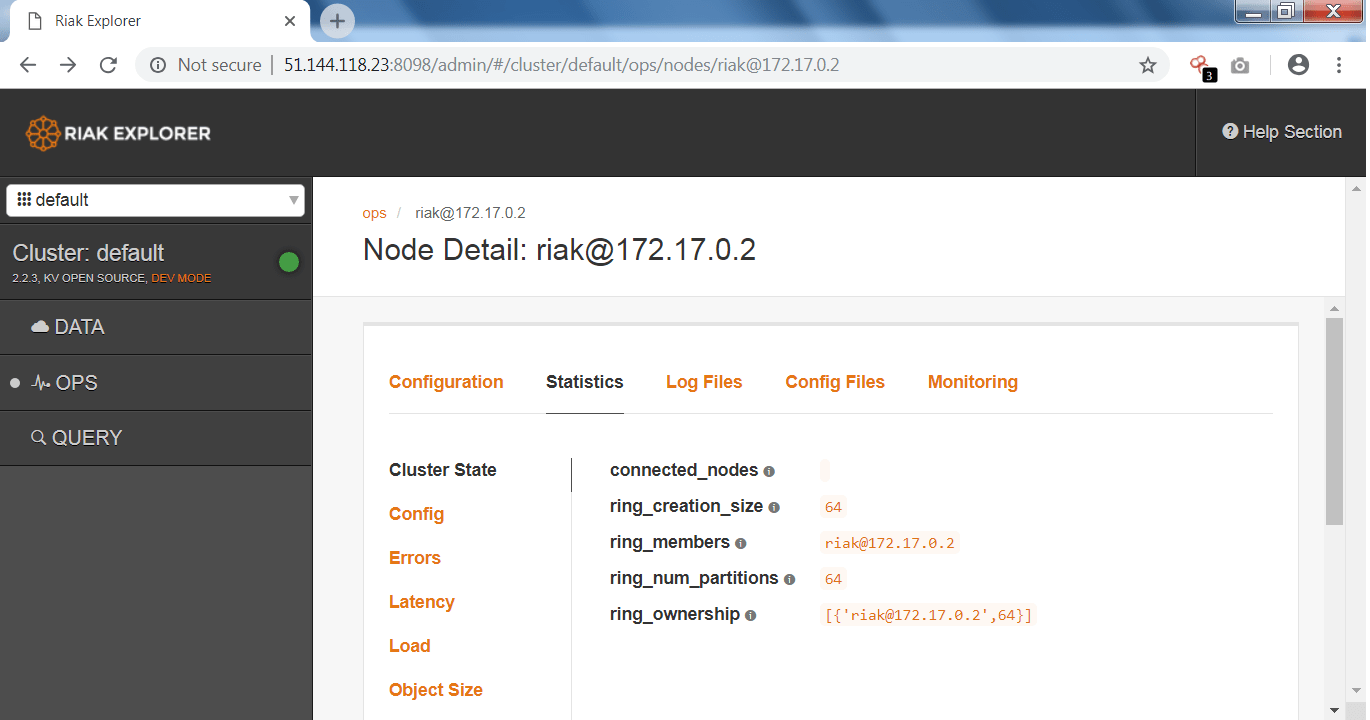
- In the above screen shot, you can use the IP address with listed ports to open the db page.
- It shows the graph of the memory process which can be used in initial phase of penetration testing.
- As you can see the above screen shots, the above admin details can be used in other hacking activities.
SEARCHING ICS (INDUSTRIAL CONTROL SYSTEM):-
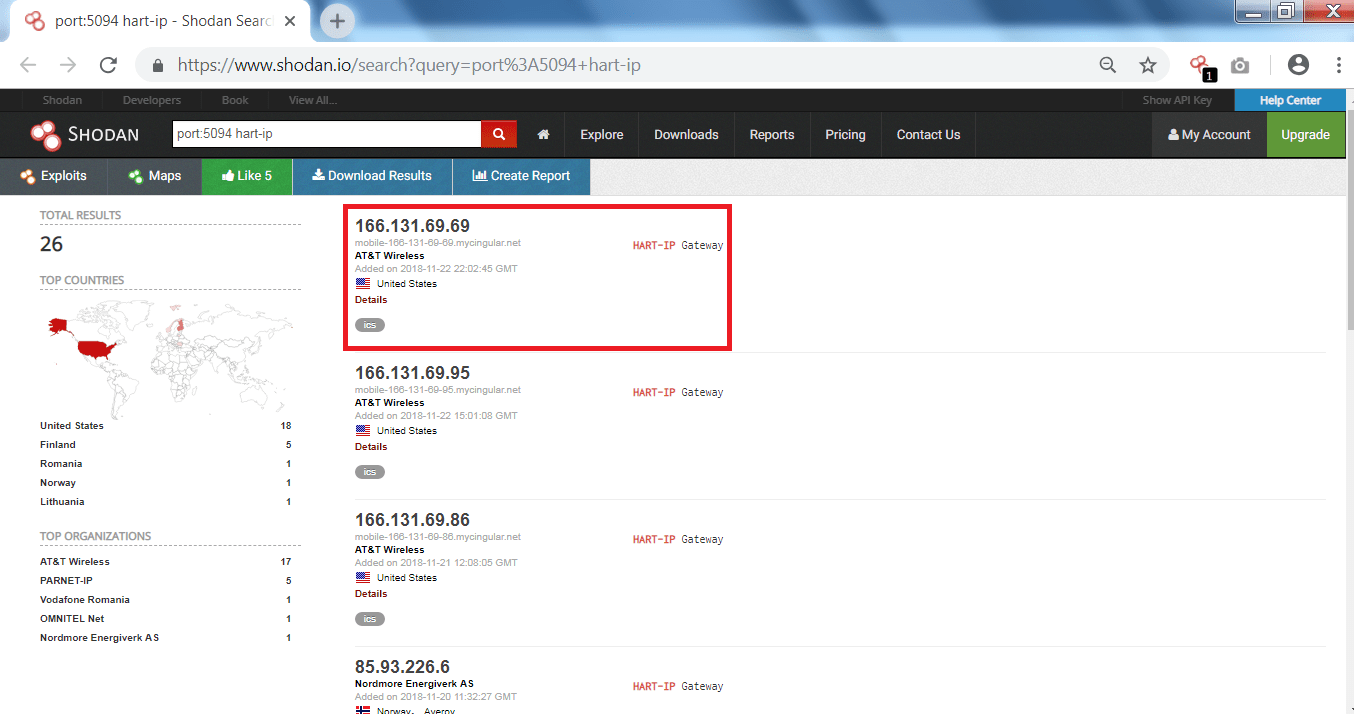
- Select the target.
===================SNIP==================
- The above IP address and open ports can be used in port scanning.
- In the above screen shots, the listed vulnerabilities can cause a massive attacks to the target. Denial-of-service attack can be used by attackers. Remote execution can also be done on this vulnerable website.
USING THE GOOGLE CHROME EXTENSION:-
-
- For quick and fast information, you can also use the google chrome addon which is available in the google chrome appstore. For installing shodan addon in google chrome go to: https://chrome.google.com/webstore/detail/shodan/jjalcfnidlmpjhdfepjhjbhnhkbgleap?utm_source=chrome-ntp-icon
- After installing the addon, whenever you open the target site. Shodan addon will start its query and will show the target website open ports/IP address.
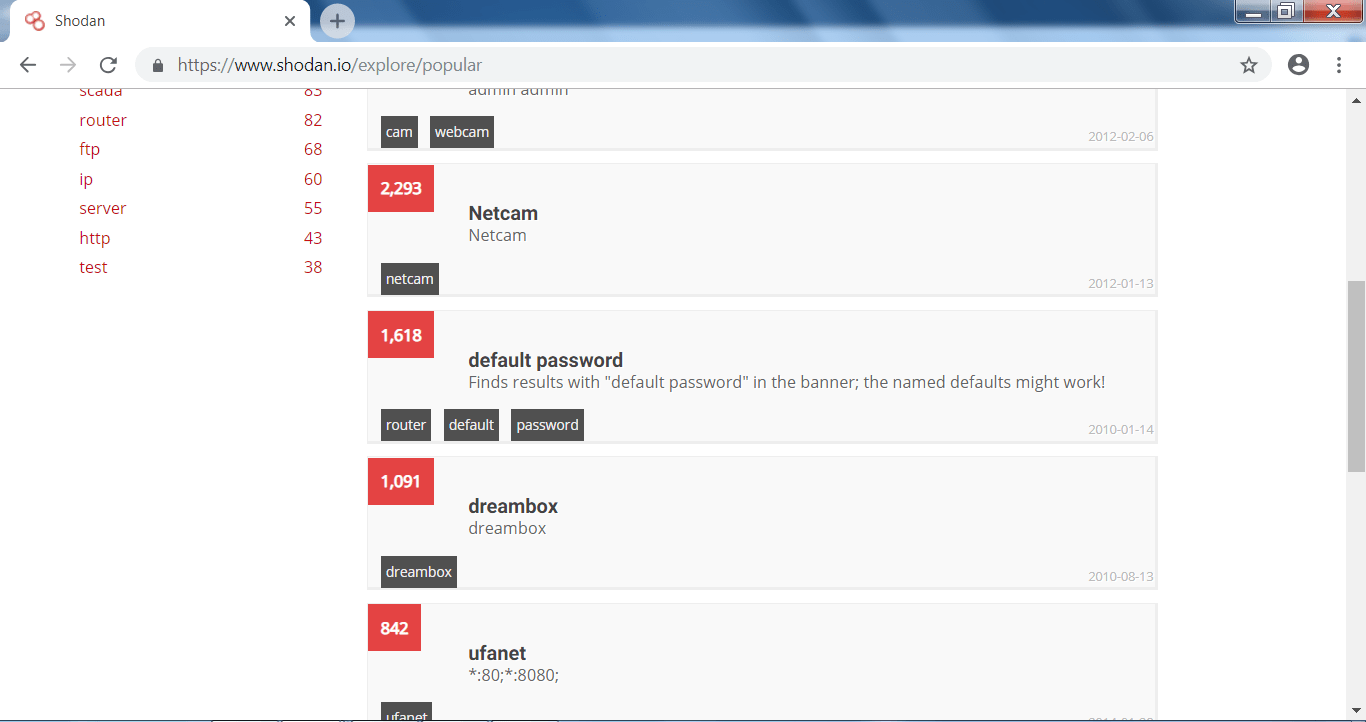
MOST POPULAR SEARCHES:-
Shodan offers many features like searching any open cams, searching for routers with default security methods.
============SNIP============
- In the above screen shot, here are some of the listed open devices which can be used in hacking activities. The most popular searches are easy to find and can be exploited by script kiddie also.
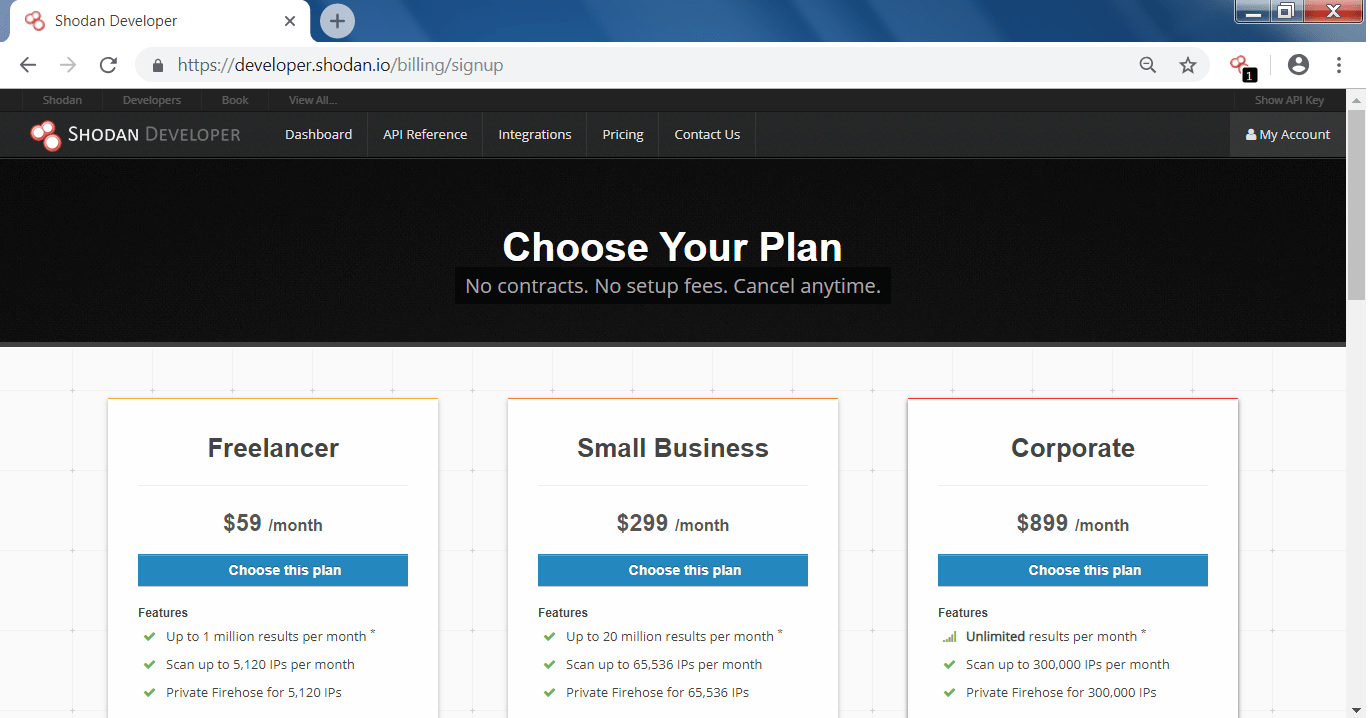
PAID PLANS:-
- You can also use the paid plans if you working as professional pentester because shodan provides detailed information for the target.
OTHER RESOURCES:-
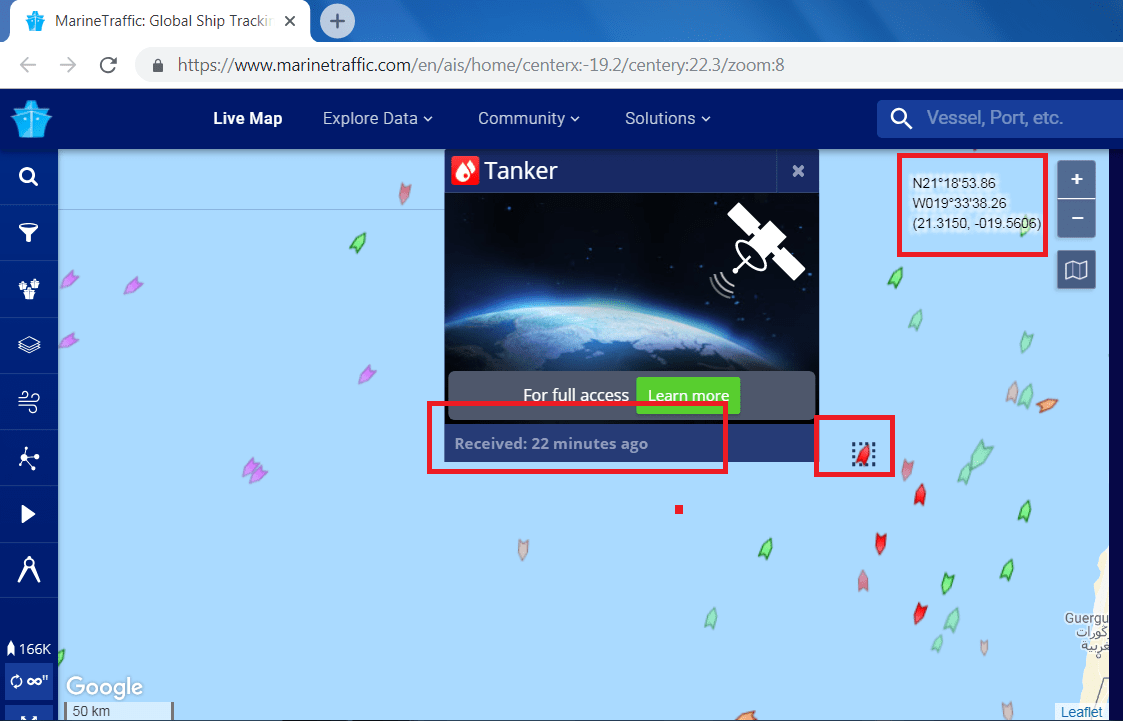
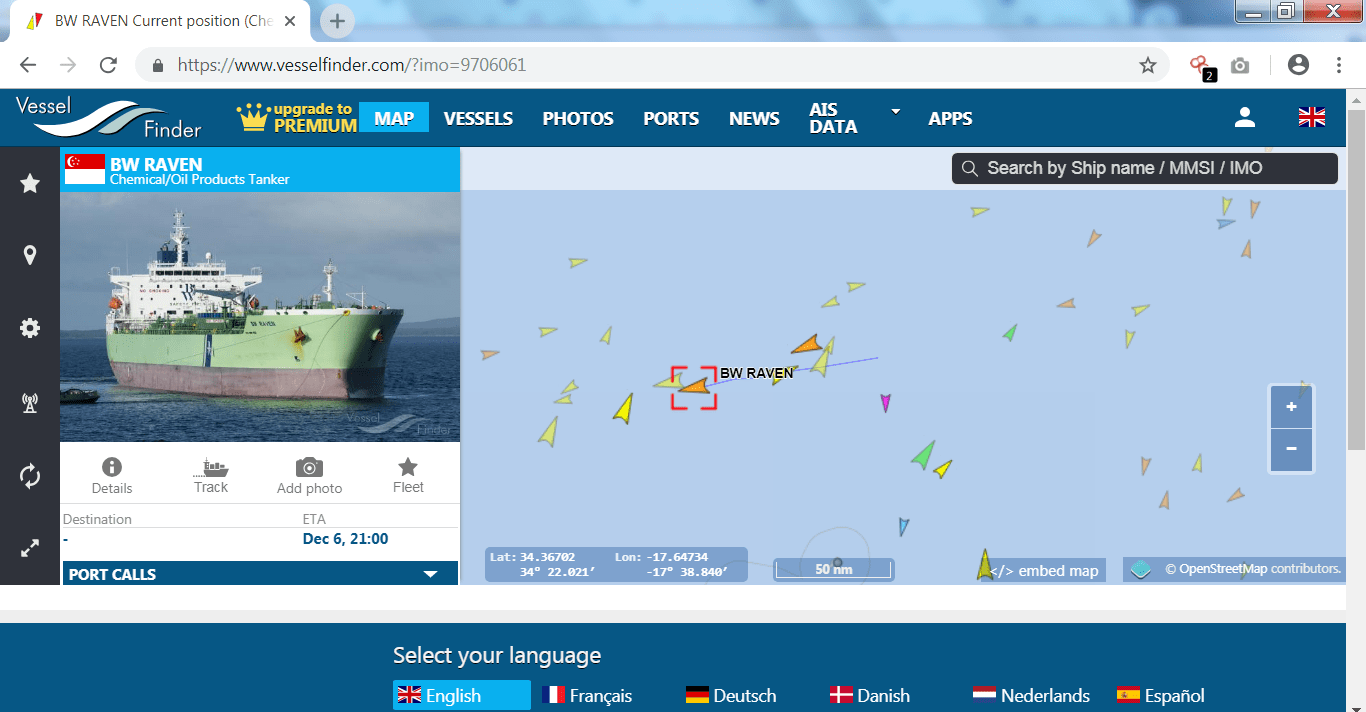
You can also use the some other resources to check ship latitude and longitude.
- https://shiptracker.shodan.io
- https://www.vesselfinder.com
- https://www.marinetraffic.com
These websites provide AIS (Automatic Identification System) that uses transponder device to receive the signal to satellite and then transmit those signals to receiver to tell their location, but shodan ship tracker is more than that.
- As you can see in the above screen shots, there are two websites who shows the ship location by using AIS system. Normal user can check to know the location of the website. These two websites shows the longitude and latitude of the ship.

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.