Joomscan is a web vulnerability scanner used to detect command execution, sql injection and other web application attacks. As name suggest, joomscan scans websites created using joomla. Joomscan locate the browsable folders, locate each file to identify the version of a component installed, explain ethical hacking teachers.
- For running the joomscan type joomscan in linux terminal.
- In the above screenshot it shows the joomscan features which are used in finding the vulnerabilities. For further options type joomscan –help
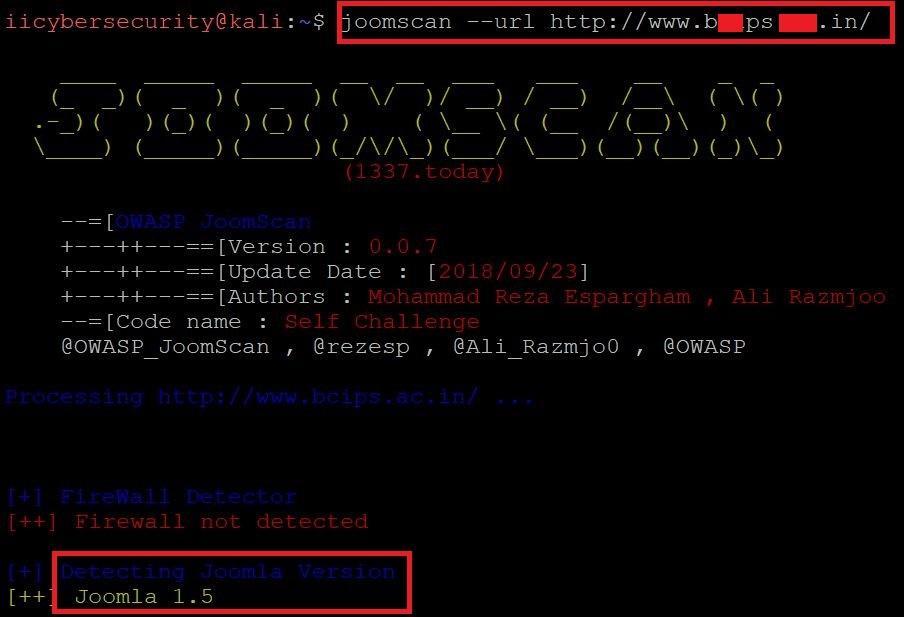
- For scanning target URL type joomscan -url https://<target-website>/
- After scan has started joomscan will try to find the vulnerabilities for the target URL. As marked Joomscan has detected Joomla Version 1.5 running on target website.
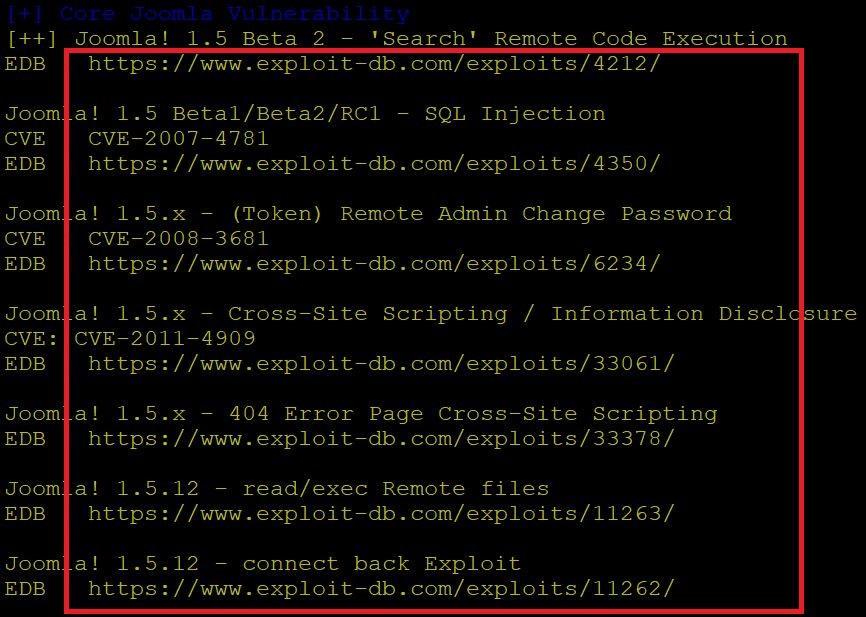
- In the above screen shot it shows joomla component, sql injection vulnerability that can be used in sql injection attacks. The site also has vulnerability of cross-site scripting which can disclose the information about the target. The main vulnerability is Remote Admin Change Password in which attacker can get access of the admin by getting the access token of the admin page.
As per past researches done in by ethical hacking researcher of international institute of cyber security joomscan has been used in reverse engineering attacks, which allows the hacker to create accounts in the websites even if the registration is disabled in joomla sites. This vulnerability has been patched in the latest version of joomla CMS (Content Management System).

Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator. He is a cyber-security researcher with over 25 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked with Google and Citrix in development of cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.