Using a smart combination of different tools, Kamerka can take an address, a cue point or coordinates and show exposed cameras connected to the Internet on a map
Security cameras are a very common thing for the people living in the big cities. As reported by specialists in digital forensics and cybersecurity from the International Institute of Cyber Security, many of these cameras are connected to the Internet, and can be accessed either intentionally or inadvertently, so that other users access their transmissions. You can find a vulnerable device anywhere, from business, to schools and homes. A new tool allows you to locate the exposed security cameras on a map.
While some researchers would normally have to track open device lists with tools like Shodan, Kamerka allows users to enter an address to find the cameras nearby on a map.
The tool highlights in a tangible way the prevalence of unsafe cameras that surround us and that anyone can use and utilize potentially for surveillance or espionage.
“You can search all over the world if there is a camera exposed in a sensitive place”, mentions the expert in digital forensics who developed the tool, identified with the alias ‘Woj-Ciech’, in a publication on his blog.
As ‘Woj-Ciech’ explains, Kamerka joins several different pieces of Python code. The tool uses Shodan to find the cameras exposed in the first place (those who run the tool must have a Shodan account with a key API). It then uses Geopy, a Python module that facilitates geolocation of addresses, landmarks, and cities. The final ingredient is Folium, a Python library that handles the creation of the map.
After a user enters the desired location, the script returns a list of found devices and creates the HTML-based map. By opening this in a browser, users can scroll and zoom in the inspected area by clicking on the markers to reveal the IP address of the cameras discovered, report experts in digital forensics.
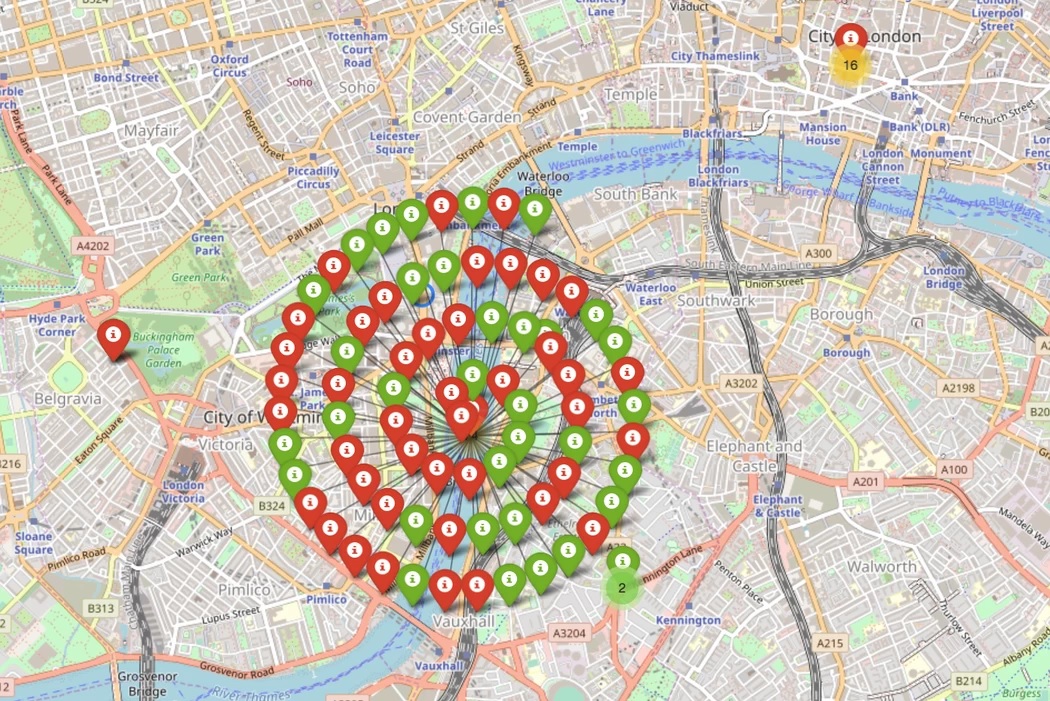
“Any user with sufficient knowledge can use Kamerka to search for cameras in Washington DC, or perhaps in their own neighborhood”, continues ‘Woj-Ciech’. The expert claims he has even found cameras near one of Amazon’s “secret” stores recently documented by WikiLeaks.
Cybersecurity and digital forensics specialists were able to verify that the tool works after testing it in different locations such as London, New York and Paris. Not all the results threw completely exposed security cameras; some required other authentication steps, or were login administrator panels instead of a security camera transmission. No live streaming was found during the tests, but camera control panels with known and predictable default passwords were found, as well as other open control panels but these were not performing live streaming at that time.
Needless to say that using this tool in other devices is not recommended.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.












