The flaw was found while experts analyzed the user-side security of dating apps
A team of forensic experts set out to conduct research on user-side security in dating applications, and one of the main objectives was Tinder’s mobile application.
After performing the initial recognition steps, a Tinder domain with multiple user-side security issues was found, meaning that hackers could access profiles and detailed user information. The dating service operators were contacted immediately after the investigators found the vulnerabilities.
According to specialists in digital forensics, the vulnerable endpoint is not property of Tinder, but of Branch.io, a platform of attribution used by many large corporations around the world. Once Tinder contacted Branch.io an update patch was implemented to resolve the vulnerability.
Delving into the topic, it was discovered that many websites shared the vulnerable endpoint in their code and domains, including sites such as Shopify, Yelp, Western Union, and Imgur. This means that up to 685 million users might be compromised.
While the vulnerability has already been resolved, Tinder users or any of the affected sites are encouraged to verify that their account has not been compromised, searching for unusual activity logs or changing their passwords.
According to the experts in digital forensics, the XSS vulnerability based on the Document Object Model (DOM), also known as “XSS type 0” is a cross-site scripting flaw that appears inside the DOM.
It is a type of attack in which malicious payload is executed as a result of modifying the DOM environment in the victim’s browser, even more so in a dynamic environment. In XSS based on DOM, the HTML source code and the attack response will be exactly the same. This means that the malicious payload cannot be found in the response, which greatly hinders the performance of the XSS mitigation functions built into the browser, such as the Chrome Auditor XSS.
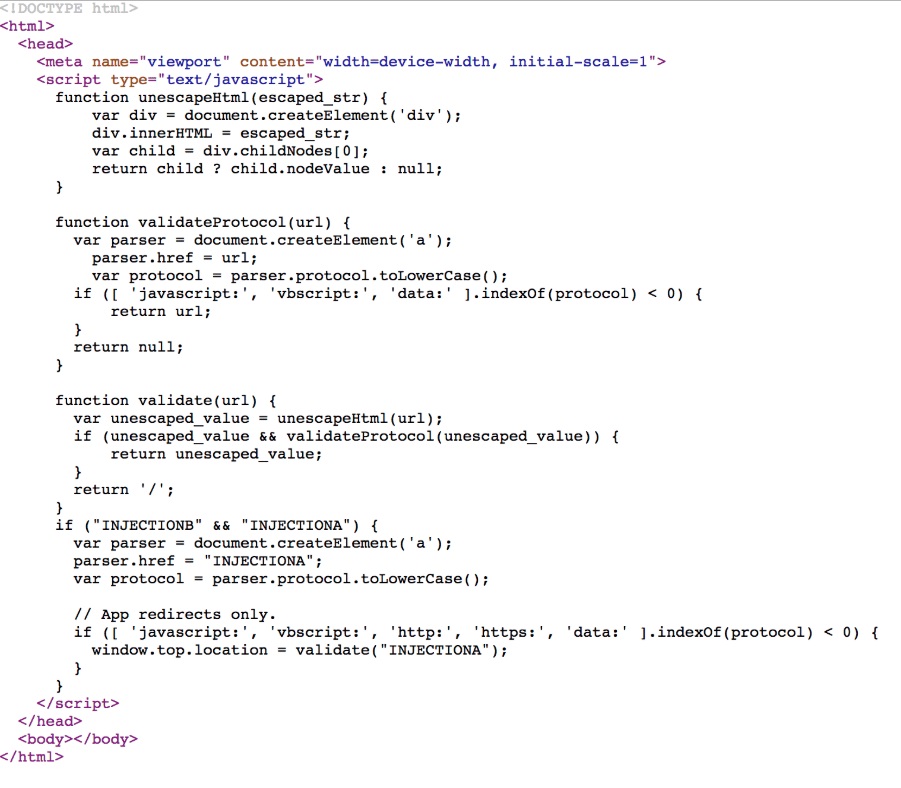
The initial finding was that the endpoint Https://go.tinder.com/amp-iframe-redirect was prone to multiple vulnerabilities (the scheme_redirect and redirect_strategy GET parameters control the content.
redirect_strategy is “InjectionA” and scheme_redirect is “INJECTIONB” in the displayed code.
This meant that by modifying redirect_strategy to a DOM-XSS payload, it was possible to run client-side code in the context of a Tinder domain in any browser.
According to specialists in digital forensics from the International Institute of Cyber Security, the vulnerability also affected sites such as RobinHood, Canva, Letgo, and more.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.












