The company has launched a new bounty program for ethical hacking specialists
Program Description
Information security of our days depends on the collaborative communication of identity and identity data within and through the web domains. Often, a client’s digital identity is the key to accessing services and interacting over the Internet. According to ethical hacking experts from the International Institute of Cyber Security, companies like Microsoft have invested a lot of resources in the privacy and security of their identity solutions for both consumers and companies.
Microsoft is committed with the creation, implementation, and improvement of customer identity-related specifications to strengthen authentication, login security, API security, and other critical tasks, as part of a community of standards compliance experts, such as those established by the OpenID Foundation. In recognition of that commitment to customer security, Microsoft launches its Identity Bounty Program.
If you are an ethical hacking and security researcher and you have discovered a vulnerability in any of the Microsoft identity services, the company would appreciate that the flaw could be privately communicated to them, in order to give them the opportunity to solve it before publishing the technical details report. Beyond its commitment to the identity standards industry, the company has extended its rewards program to meet the highest standards of security identity.
Program Scope
- windows.net
- microsoftonline.com
- live.com
- windowsazure.com
- activedirectory.windowsazure.com
- activedirectory.windowsazure.com
- office.com
- microsoftonline.com
- Microsoft Authenticator (iOS & Android apps)
Out of Scope
- Reports of automatic tools or scans
- Issues without a clear impact on identity security (such as clickjacking on a static web site), lack of security headers, or message error
- Password, email and account policies such as mail identity verification, expired links, or password complexity
- Configuration errors committed for the user, such as enabling HTTP access on account storage to allow a Man-in-the-Middle attack
- Vulnerabilities in specifications not explicitly mentioned
- Vulnerabilities in non-certified Microsoft product or service implementations
- Lack of security headers or cookie security flags
- Server-side information disclosure, such as IP addresses, server names, and stack traces
- Denial-of-service issues
- Vulnerabilities that require user’s improbable actions to be exploited
- Publicly known vulnerabilities by Microsoft and the computer security community in general
- Vulnerabilities in web applications that only affect unsupported browsers and plugins
- Applications requiring data manipulation, network access or physical attack against Microsoft offices or data centers and/or social engineering against the company, employees or contractors will not be accepted
- Two-factor authentication bypass requiring physical access to a logged in device
- Local access to user data when operating a rooted mobile device
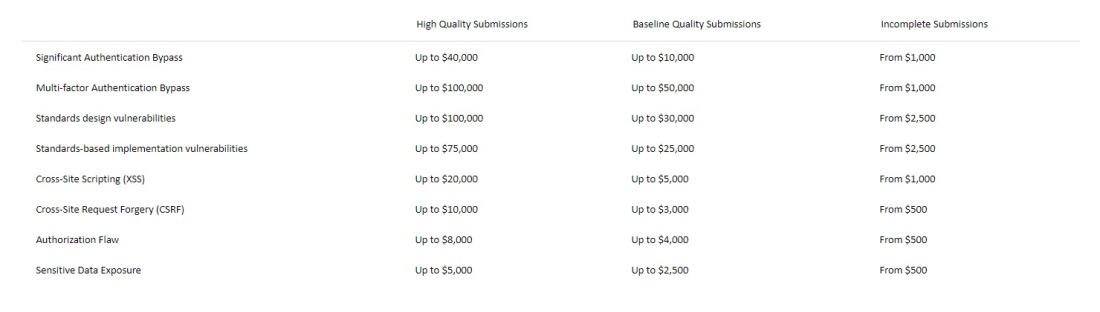
How is the bounty amount set?
The rewards for reports that meet the requirements of this program range from $500 to $100k USD. Higher payments will be delivered based on the quality of the report and the vulnerability’s security impact. Ethical hacking specialists participating in the program are encouraged to include as many data as possible in their reports for a correct pricing calculation. Regularly, a lesser reward is delivered if the vulnerability requires a lot of interaction whit the user to be exploited.
- If the company receives multiple reports from different sources for the same problem, the reward will be given to the first report received
- The first external report received on an internally known problem will receive up to 10% of the maximum reward amount
- If a duplicate report provides Microsoft with previously unknown information for the company, a differential sum will be paid to the duplicate report
- If a report is potentially eligible for multiple rewards programs, the researcher will receive only one payment, out of the largest reward possible
- Microsoft reserves the right to reject any report that, to the company’s consideration, does not meet all the requirements previously stipulated
A high quality report provides necessary information for ethical hacking experts at the time of reproducing, understanding, and fixing problems as soon as possible. This regularly includes backup information, vulnerability description, and a proof of concept. Microsoft recognizes that some problems are extremely difficult to reproduce and understand, so this will be considered at the time of qualifying all the received reports.
Many Microsoft sites share a common platform. For this reason, a vulnerability reported in a domain might exist in other domains that share the same platform. For example, a problem reported in account.microsoft.com could be present exactly the same way in account.microsoft.com.uk, so the vulnerability would be corrected in the same way in both cases.
Microsoft asks ethical hacking experts participating in the program to take the time necessary to confirm this, so as to include in the report other possible locations of the same error instead of sending multiple flaws. In such cases, the first report received will be considered as a single vulnerability report, while the remainder will be considered as duplicates.
Prohibited Safety Research Methods
The following methods of investigation shall be deemed prohibited within this program:
- Phishing attempts or any other form of social engineering against Microsoft employees. The scope of this program is limited to the report of technical vulnerabilities in the specified Microsoft online services
- Any type of denial-of-service test
- Perform automated analysis of services that generate significant amounts of traffic
- Gain access to any information that does not belong to you completely
Even with these restrictions, Microsoft reserves the right to respond to any action on its networks that seems malicious.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











