Enterprise network security experts explain that spoofing occurs when someone makes a call and deliberately modifies the information shown to the person who receives the call, thus hiding his/her identity. The person interested in hiding his/her information may choose a phone number and it will be shown to the call receiver.
By surfing the Internet anyone can find several call ID spoofing services and some others are also available for mobile devices operating with iOS and Android, they all offer additional services to the call spoofing.
Specialists in enterprise network security from the International Institute of Cyber Security mention that the practice of spoofing has different reasons considered legitimate to be performed; this activity is considered within the limits of law when the person who performs it does not intend to harm the people he/she calls.
Pranksters, doctors who want to protect their privacy and that of their patients, private and government detectives, sales professionals, or call companies for quality control purposes, often search spoofing ID services to maintain a high level of privacy and anonymity to achieve their goals in an efficient way.
However, some features of these services make them attractive to different malicious actors who will try to take advantage of the spoofing in the worst possible way.
A spoofed call could be considered illegal when the person who performs it does so with the intention of causing damage in some way to the call receiver. Enterprise network security experts commented that it is illegal to perform spoofed calls aiming to cause harm, committing fraud, or obtaining something of value by questionable means.
A frequent method of spoofing considered illegitimate is known as the neighbor spoofing, in which spoofing calls are disguised with phone numbers similar to that of the victim, so that the victim is more likely to answer the call and fall into deception. These campaigns are performed for different purposes, all of them malicious.
Below is a list of spoofing services gathered by enterprise network security experts, which provide different services according to the needs of users, from just the spoofed call, to more complex features, such as call recordings, statistics and ambient sound.
SpoofCard
This service includes features such as call recording, direct to voicemail calls, voice disguise, and SMS messaging. It is also available for iOS and Android powered mobile devices.
SpoofTel
SpoofTel also has additional services to spoofing, such as ambient sound, recording, and voice disguise. With rates from .10 cents per minute of call, and .50 cents per text message, SpoofTel operates on desktops and mobile devices with iOS.

Covert Calling
Covert calling also includes features such as call recording, ambient sound and voice disguise, as well as offering a temporary demo of the online tool.

https://www.covertcalling.com/
Spoof My Phone
Available for Android and iOS, Spoof My Phone offers, in addition to standard spoofing ID services, the group call option, allowing more than one person to participate in the call, useful for enterprise network security specialists who work with small groups of people.

Itellas Communications
This is a spoofing service focused on bussines customers and enterprise network security experts; it offers different plans including features such as mobile and desktop use, voice notes, and service usage statistics.

Bluff My Call
Bluff My Call offers basic spoofing features, such as caller ID and text messaging, as well as more advanced services, such as contact editor, or the possibility of becoming a partner of the company as a distributor.
Free Caller ID Spoofing
According to enterprise network security experts, Free Caller ID Spoofing service offers in its broader plans features like group calling, ambient sound effects and voice disguise.

https://freecalleridspoofing.com/
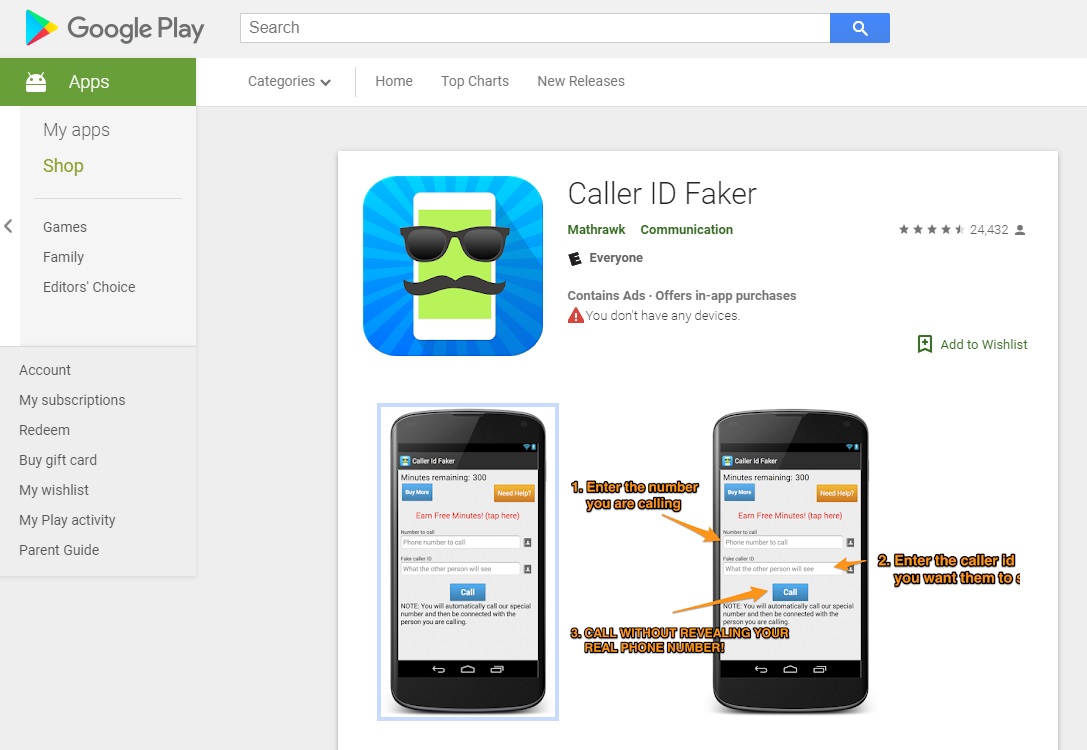
Caller ID Faker
By acquiring credits for this payment app for Android, you can enjoy a basic spoofing service limited only to spoofed calls.
https://play.google.com/store/apps/details?id=com.mathrawk.calleridfaker&hl=en
Crazy Call
The Crazy Call service is limited only to spoofing calls, and is only available for certain areas of the world. The advantage of Crazy Call is that it also operates in Android and iOS. This was the most famous and used spoofing method back in time, as reported by experts in enterprise network security.

MyPhoneRobot
MyPhoneRobot offers the standard spoofing services, as well as including features such as the purchase of phone numbers, or pre-recorded voice messages. Also available on Android, but it’s only available in the US and Canada.

In case you want to learn more about spoofing tactics, you can get training inenterprise network security by the IICS.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











