A team of information security experts explains that a domain name represents some kind of label for IP addresses on the Internet. Since some companies move their infrastructure to the cloud, we must find business servers in the set of IP addresses in the cloud, such as finding a needle in a haystack. This is why domains provide a good link to IP addresses.

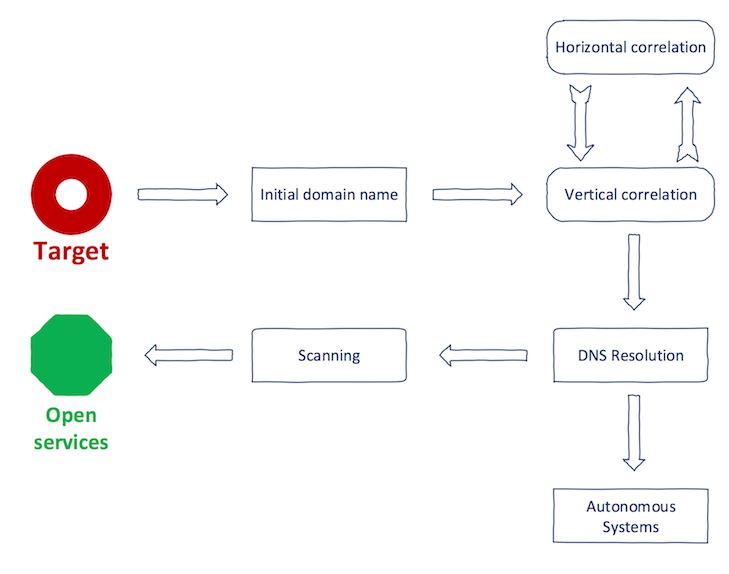
The goal is to find all the domain names of a single entity. This can only be achieved step by step with the correlation of vertical and horizontal domains. In the text, a word denotes the entity of interest in the correlation process.
Vertical domain mapping: with the domain name, the vertical domain mapping is a method of searching for domains that match the same base domain. This process is called subdomain enumeration 1.
Horizontal domain mapping: with the domain name, horizontal domain mapping is a method of searching for domain names, which have a different second-level domain name but match the same entity 1.

As an example, eff.org has been selected as an objective.
For the first step, experts say that you should perform a vertical correlation on eff.org
This is done with tools like Sublist3r, amass or aquatone. You should keep in mind that there are many open source tools for enumerating subdomains that give poor results. The information security professional comments that it is better to use “meta-sub-domain enumeration” that combines results from multiple enumeration services.
Sample output of Sublist3r.

Stop the next step, you should perform a horizontal correlation on eff.org. This step can be a little complicated. You cannot rely on a syntactic match like in the previous step. Surely, abcabcabc.com and cbacbacba.com will be owned by the same entity; however, they do not match syntactically. For this we can use WHOIS data. These are inverse services that allow you to search based on the common value of the WHOIS database.
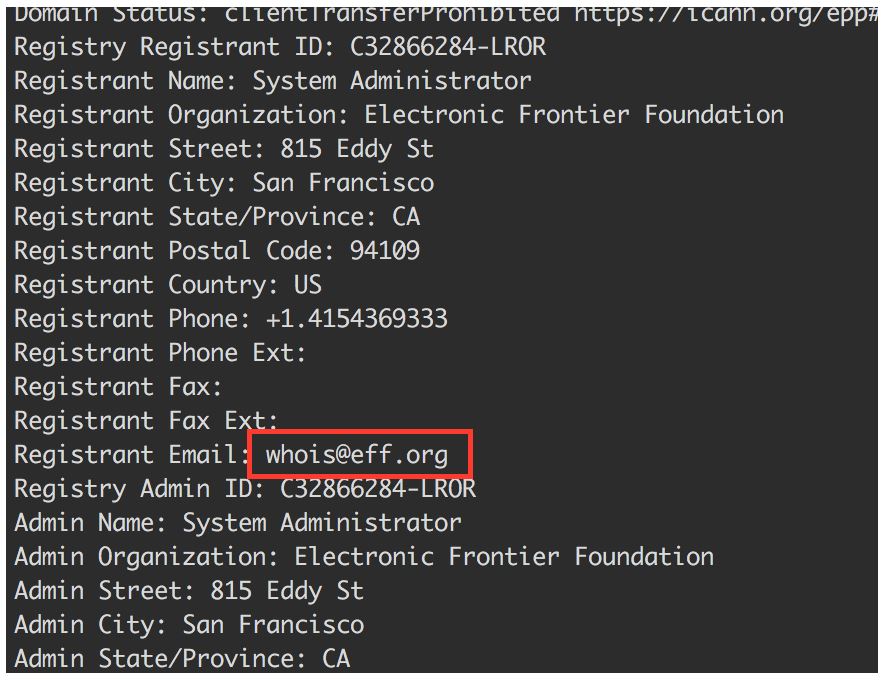
An email address is provided as a registration contact, says the security expert. At this point you can do a reverse WHOIS search to reveal other domains with the same email.
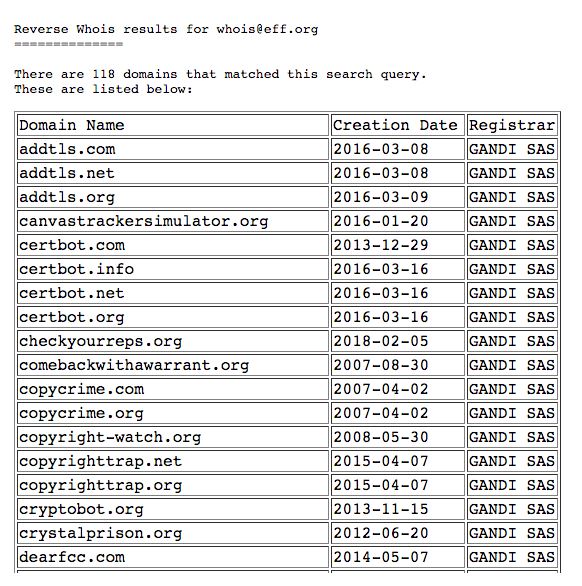
For reverse WHOIS, the expert recommends using the viewdns.info service.
In step number three, it is necessary to identify the interesting domains of step two and execute a vertical correlation.
Must have a large list of domain names linked to your goal, says the information security professional.
With any luck, your goal will have registered a range of dedicated IP addresses. To verify this, the easiest way is to execute the translation from IP to ASN in three IP addresses that are in the domain names.

Now it seems that EFF.org does not have dedicated IP space. As a counterexample, let’s look at Google.
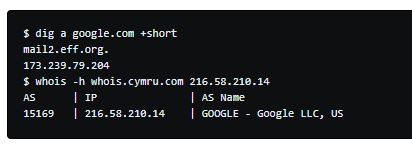
Google operates on AS15169 which is one of its AS.
Obtaining a dedicated IP range makes things easier: the company has IP ranges listed in the AS. With this information, we can compile a list of IP addresses from the CIDR notation.
If our goal does not have dedicated space, we must trust the domain names compiled previously. From this, we will solve the IP addresses. Even if the objective has a dedicated IP range, it is recommended to follow the process. There is a possibility that part of the infrastructure is already running in the cloud.
The information security researcher tells us that it is important to keep in mind that there is a possibility of false positives with this approach. The target can use shared hosting, p. for a landing page. The IP address of this host will be included in your list, this address is clearly not dedicated to your goal.
For DNS resolution, the expert recommended massdns. It will resolve the domain names in the compiled list to the IP addresses of its corresponding registers.

A list of IP addresses corresponding to the FQDNs of the target will be generated. Now, you can add the result set to the IP addresses of the CIDR blocks. You must have a list of IP addresses linked to your goal.
Now the most interesting part, services. The reason for collecting domain names and then IP addresses is to reveal what services is the target that is exposed to the Internet. For this, we need to scan the hosts, commented the information security professional.
We have two options:
Active scanning: traditional nmap approach. For a list of hosts, it can also be Masscan. It is important to note that active scanning consumes more time and can trigger IDS for the public. But you get more accurate representation of open services.
Passive analysis: it is based on data collected from another source. These sources include, for example, Shodan or Censys. The drawback is that the results may take several days and some services may already be closed. On the other hand, this “stealth” mode is generally preferred when performing APT simulations.
Shodan offers dork for this purpose. You can search for a specific IP range like this:
net: 64,233,160.0/19
Also, we can filter according to the organization in the WHOIS database:
org: “Google”
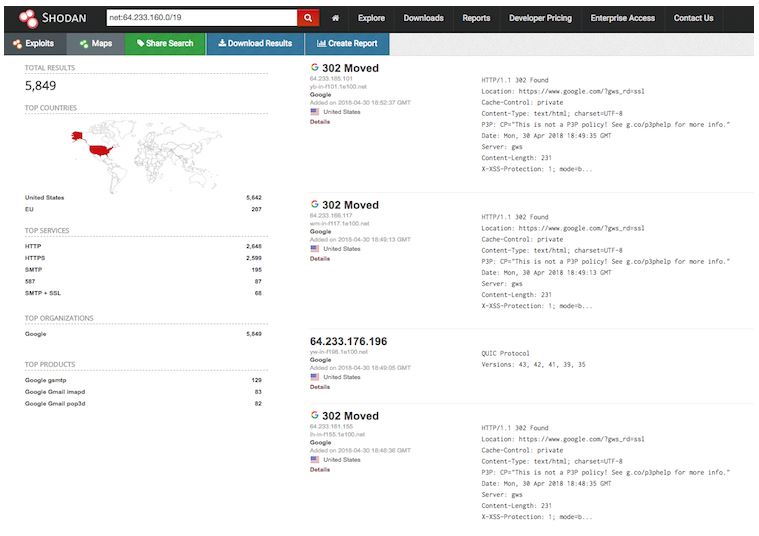
Censys offers the same functionality:
ip: 64.233.160.0/19
For the organization / filter ASN:
autonomous_system.asn: 15169
autonomous_system.organization: “Google Inc.”

For stealth mode, you can use Project Sonar to recover everything.
Now, you must have very good visibility in your goal.
The final set must contain IP port that belongs to the target.
Information security experts comment that post-processing tasks can be performed to reveal the most interesting services; you can run the screen capture tool of the massive site, such as Snapper, which will provide an overview of the running of websites in one place.
Source:https:// 0xpatrik.com/asset-discovery/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











