rop-tool v2.4.1 A tool to help you writing binary exploits.
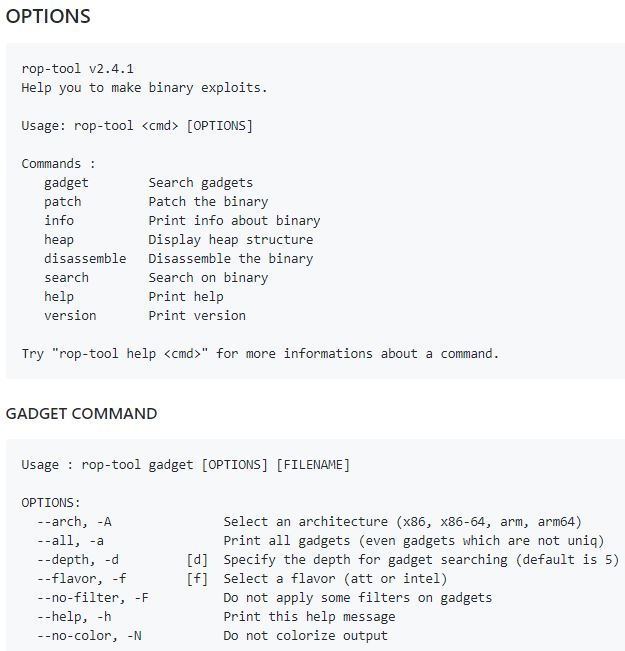


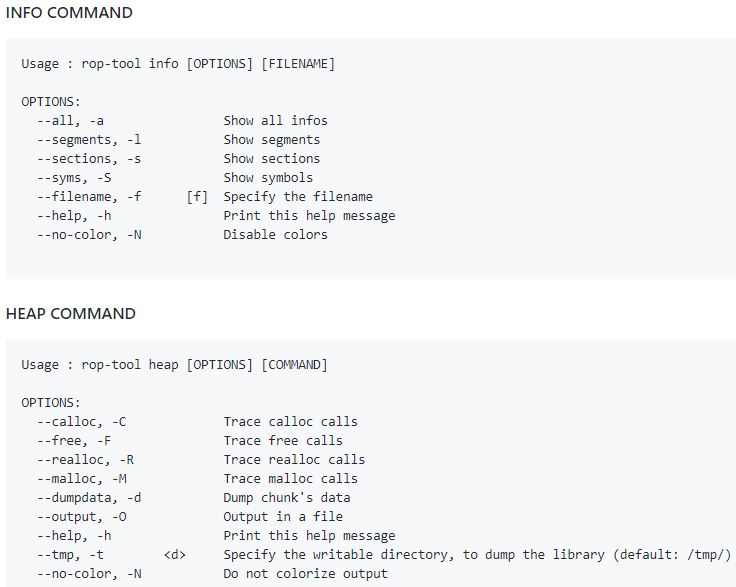

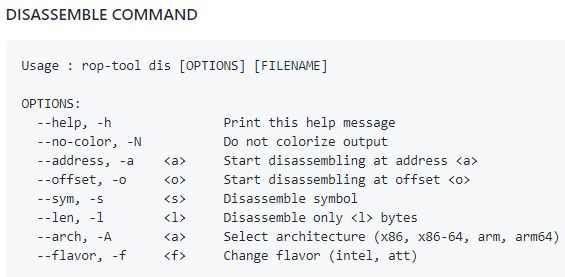
An information security training expert gives a small explication about output of heap command
Each line correspond to a malloc chunk, and the heap is dumped after each execution of heap functions (free, malloc, realloc, calloc)
- addr: is the real address of the malloc chunk
- usr_addr: is the address returned by malloc functions to user
- size: is the size of the malloc chunk
- flags: P is PREV_INUSE, M is IS_MAPED and A is NON_MAIN_ARENA



FEATURES
- String searching, Gadget searching, patching, info, heap visualization, disassembling
- Colored output
- Intel and AT&T flavor
- Support of ELF, PE and MACH-O binary format
- Support of big and little endian
- Support of x86, x86_64, ARM and ARM64 architecture
The information security training expert gives some examples:
Basic gadget searching
- rop-tool gadget ./program
Display all gadgets with AT&T syntax
- rop-tool gadget ./program -f att -a
Search in RAW x86 file
- rop-tool gadget ./program -A x86
Search a “splitted” string in the binary
- rop-tool search ./program -s “/bin/sh”
Search all strings in binary
- rop-tool search ./program -a
Patch binary at offset 0x1000, with “\xaa\xbb\xcc\xdd” and save as “patched” :
- rop-tool patch ./program -o 0x1000 -b “\xaa\xbb\xcc\xdd” -O patched
Visualize heap allocation of /bin/ls command :
- rop-tool heap /bin/ls
Disassemble 0x100 bytes at address 0x08048452
- rop-tool dis /bin/ls -l 0x100 -a 0x08048452

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











