Hi Guys, I hope all of you are doing great and in a well state. Today i will show you a ClickJacking bug i found in Instagram that allowed me to iframe ajax responses and leads attackers to steal your instagram connected applications tokens hence hijack your account!
Long story short:
I have found that some instagram Ajax GET requests can be iframed, I reported this to instagram back in 2015 but they rejected the issue and the reason was “it involves a lot of social engineering and interactions”, I didn’t gave up hope and took the issue to another level.
While i was searching what can i do to convince Facebook Security Team with the impact of it an idea came to my mind, if most of the replies of the ajaxed requests of Instagram can be iframed why not trying to iframe the web page that manages the access tokens of the “Connected applications”?? This endpoint should be protected at least with a 20-mins re-auth or with a multi-factor authentication because it is critical. I went to the web page that manages the access token via this url: https://www.instagram.com/accounts/manage_access/ and it looked like this one:
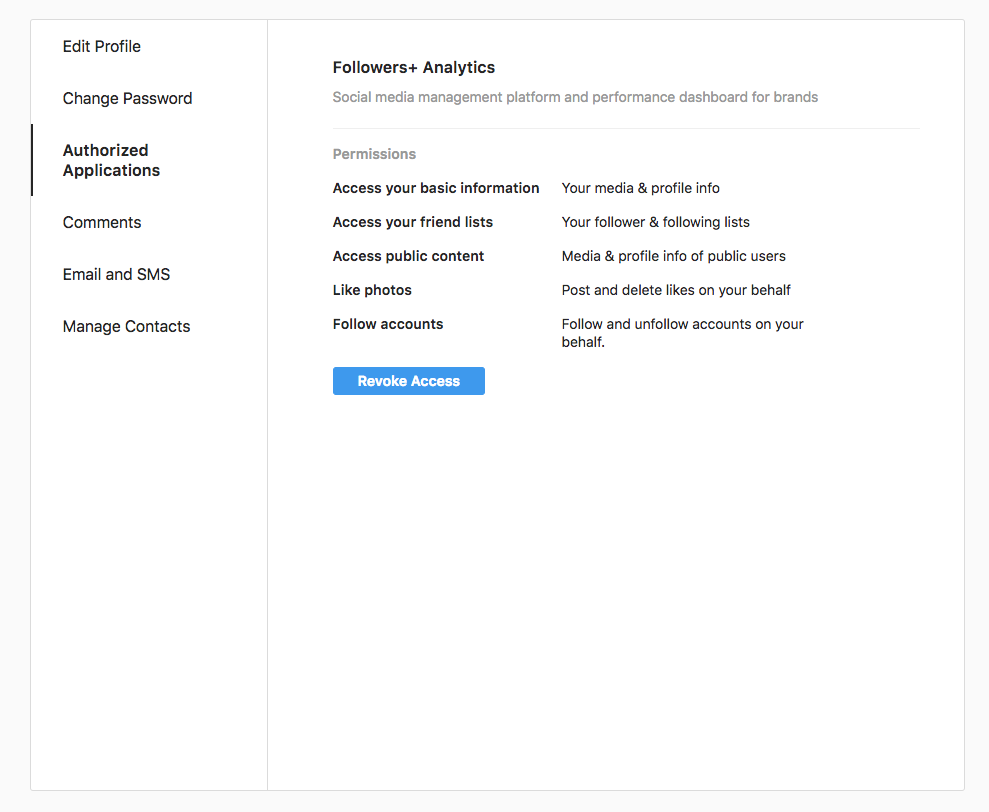
The UI is super solid no access tokens are shown or even it can be iframed because X-Frame-Options header is in place, adding __a=1 to the URL (If you’re an active facebook bug hunter you will be aware that most of facebook and instagram endpoints takes “__a=1” parameter to perform ajaxed requests) and here is what i’ve got:
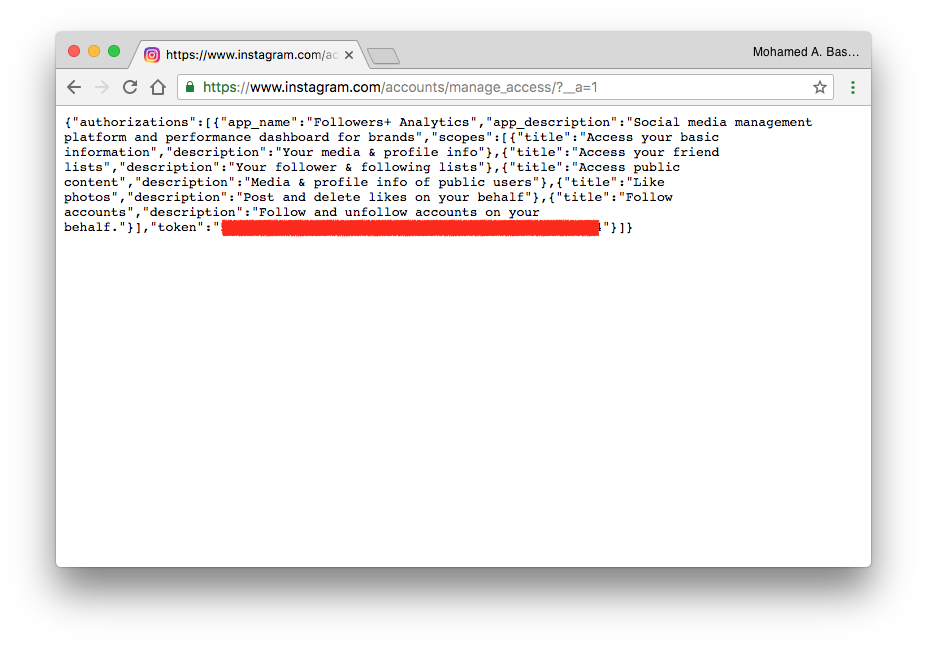 A json content-type reply along with the connected applications tokens and guess what? That reply could be iframed ?
A json content-type reply along with the connected applications tokens and guess what? That reply could be iframed ?
So, I picked up everything together, Opened a new ticket and suggested to my Friend Mostafa Kassem (a great developer BTW) to make a proof of concept but a very advanced one (A complete dashboard kinda like Instagram Phishing platform and you will see it in the proof of concept video), so quickly Mostafa shape the idea in a great way as suggested and i sent the issue back to Facebook again, here is their reply:
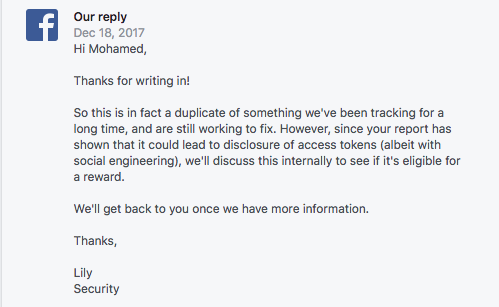
Me: *winking* Got their attention!
The suggested Impact:
The suggested impact was that the responses of this ajax request is vulnerable to ClickJacking which gives the attacker the ability to trick the victim into copying the content of the reply and send it back to him, allows him stealing your precious access tokens.
Remedy Suggested:
Add X-Frame-Options server header to the request responses to prevent it from being iframed.
Now, It’s the time of the PoC Video, I hope you guys like it, Again huge shouts to Mostafa Kassem!
Profit?
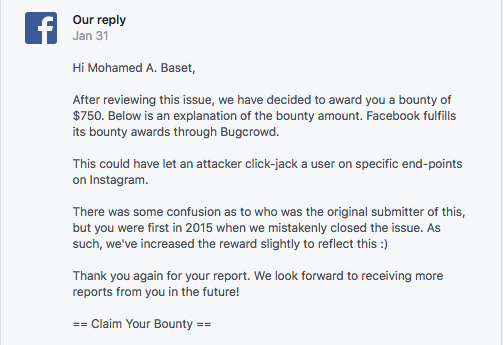
Till the next one, Peace!
A minute if you please!
Building a website, an application or any kind of business? Or already have one? Worried about your security? Think twice before going public and let us protect your business!

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











