Recently security researcher’s from enSilo group presented new evasion technique called Process Doppelgänging at Blackhat Europe-2017. This technique bypasses most popular Antivirus, NGFW and EDR solutions present in the market. This technique works on all windows starting Vista till Windows Server 2016.
Process Doppelgänging makes malware capable to execute malicious code under radar of genuine executable without getting detected or flagged (Impersonating legitimate process).This attack uses the NTFS Transactions and windows process loader flaw. For more technical detail of how attacks works on kernel level, please refer to enSilo blog link’s in reference section.
Note :- Running this POC on Windows 10 will land you in BSOD.
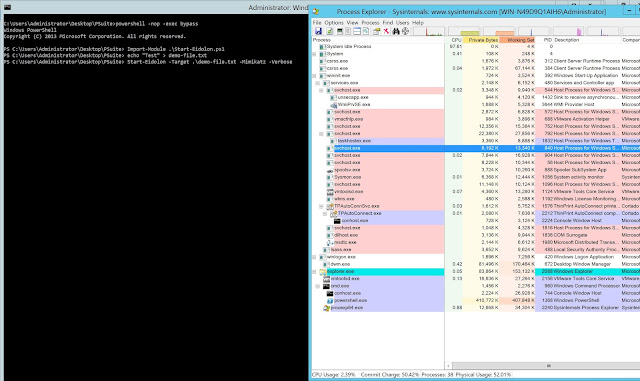
Let’s try to replicate this attack in our Lab on target system Windows Server 2016. Fuzzysec implemented Doppleganger in PowerShell and we going to see how it works. Download the Start-Eidolon.ps1 from the Github and import in Powershell. Use any valid file from the machine to be impersonated (we are using demo-file.txt as original file). We can see all the running process in Process Explorer .
Lets run the script and it generates new freshly baked Mimikatz !!
Lets look at Process Explorer and find which process is parent of this Mimikatz. We can see there is “System Idle Process” running under name of demo-file.txt
Finding the Process ID of idle process and checking its command line argument. (No signs of Mimikatz in memory leading failure of 99.99% of security tools)
Now using PE-Sieve of @hasherezade we can compare the loaded image in memory and original file on disk are same or not. If its not same, dump the malicious code of modified loaded image. Below is command line options for same.
C:\Users\Administrator\Desktop\PSuite>pe-sieve64.exe 2688
PID: 2688
Module filter: 3
—
[*] Scanning: C:\Users\Administrator\Desktop\PSuite\demo-file.txt
Invalid payload: 221d320000
Could not allocate memory at the desired base!
[!] Suspicious: could not read the module file! Dumping the virtual image…
[*] Scanning: C:\Windows\SYSTEM32\ntdll.dll
[*] Scanning: C:\Windows\system32\KERNEL32.DLL
[*] Scanning: C:\Windows\system32\KERNELBASE.dll
[*] Scanning: C:\Windows\system32\ADVAPI32.dll
[*] Scanning: C:\Windows\system32\CRYPT32.dll
[*] Scanning: C:\Windows\System32\cryptdll.dll
[*] Scanning: C:\Windows\System32\FLTLIB.DLL
[*] Scanning: C:\Windows\System32\NETAPI32.dll
[*] Scanning: C:\Windows\system32\ole32.dll
[*] Scanning: C:\Windows\system32\OLEAUT32.dll
[*] Scanning: C:\Windows\system32\RPCRT4.dll
[*] Scanning: C:\Windows\system32\SHLWAPI.dll
[*] Scanning: C:\Windows\System32\SAMLIB.dll
[*] Scanning: C:\Windows\System32\Secur32.dll
[*] Scanning: C:\Windows\system32\SHELL32.dll
[*] Scanning: C:\Windows\system32\USER32.dll
[*] Scanning: C:\Windows\System32\USERENV.dll
[*] Scanning: C:\Windows\System32\VERSION.dll
[*] Scanning: C:\Windows\System32\HID.DLL
[*] Scanning: C:\Windows\system32\SETUPAPI.dll
[*] Scanning: C:\Windows\System32\WinSCard.dll
[*] Scanning: C:\Windows\System32\WINSTA.dll
[*] Scanning: C:\Windows\system32\WLDAP32.dll
[*] Scanning: C:\Windows\system32\msasn1.dll
[*] Scanning: C:\Windows\system32\msvcrt.dll
[*] Scanning: C:\Windows\SYSTEM32\sechost.dll
[*] Scanning: C:\Windows\System32\netutils.dll
[*] Scanning: C:\Windows\System32\srvcli.dll
[*] Scanning: C:\Windows\System32\wkscli.dll
[*] Scanning: C:\Windows\SYSTEM32\combase.dll
[*] Scanning: C:\Windows\system32\GDI32.dll
[*] Scanning: C:\Windows\System32\profapi.dll
[*] Scanning: C:\Windows\system32\CFGMGR32.dll
[*] Scanning: C:\Windows\System32\DEVOBJ.dll
[*] Scanning: C:\Windows\System32\CRYPTSP.DLL
[*] Scanning: C:\Windows\System32\CRYPTBASE.DLL
[*] Scanning: C:\Windows\System32\bcryptPrimitives.dll
[*] Scanning: C:\Windows\System32\LOGONCLI.DLL
[*] Scanning: C:\Windows\System32\SSPICLI.DLL
[*] Scanning: C:\Windows\system32\IMM32.DLL
[*] Scanning: C:\Windows\system32\MSCTF.dll
[*] Scanning: C:\Windows\SYSTEM32\kernel.appcore.dll
[*] Scanning: C:\Windows\System32\rsaenh.DLL
[*] Scanning: C:\Windows\System32\bcrypt.dll
[*] Scanning: C:\Windows\System32\vaultcli.DLL
[*] Scanning: C:\Windows\system32\WINTRUST.dll
[*] Scanning: C:\Windows\SYSTEM32\shcore.dll
—SUMMARY:
Total scanned: 48
Hooked: 0
Replaced: 0
Other suspicious: 1
Total modified: 1
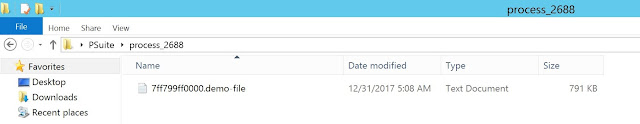
Dumps saved to the directory: process_2688
—
C:\Users\Administrator\Desktop\PSuite>
PID: 2688
Module filter: 3
—
[*] Scanning: C:\Users\Administrator\Desktop\PSuite\demo-file.txt
Invalid payload: 221d320000
Could not allocate memory at the desired base!
[!] Suspicious: could not read the module file! Dumping the virtual image…
[*] Scanning: C:\Windows\SYSTEM32\ntdll.dll
[*] Scanning: C:\Windows\system32\KERNEL32.DLL
[*] Scanning: C:\Windows\system32\KERNELBASE.dll
[*] Scanning: C:\Windows\system32\ADVAPI32.dll
[*] Scanning: C:\Windows\system32\CRYPT32.dll
[*] Scanning: C:\Windows\System32\cryptdll.dll
[*] Scanning: C:\Windows\System32\FLTLIB.DLL
[*] Scanning: C:\Windows\System32\NETAPI32.dll
[*] Scanning: C:\Windows\system32\ole32.dll
[*] Scanning: C:\Windows\system32\OLEAUT32.dll
[*] Scanning: C:\Windows\system32\RPCRT4.dll
[*] Scanning: C:\Windows\system32\SHLWAPI.dll
[*] Scanning: C:\Windows\System32\SAMLIB.dll
[*] Scanning: C:\Windows\System32\Secur32.dll
[*] Scanning: C:\Windows\system32\SHELL32.dll
[*] Scanning: C:\Windows\system32\USER32.dll
[*] Scanning: C:\Windows\System32\USERENV.dll
[*] Scanning: C:\Windows\System32\VERSION.dll
[*] Scanning: C:\Windows\System32\HID.DLL
[*] Scanning: C:\Windows\system32\SETUPAPI.dll
[*] Scanning: C:\Windows\System32\WinSCard.dll
[*] Scanning: C:\Windows\System32\WINSTA.dll
[*] Scanning: C:\Windows\system32\WLDAP32.dll
[*] Scanning: C:\Windows\system32\msasn1.dll
[*] Scanning: C:\Windows\system32\msvcrt.dll
[*] Scanning: C:\Windows\SYSTEM32\sechost.dll
[*] Scanning: C:\Windows\System32\netutils.dll
[*] Scanning: C:\Windows\System32\srvcli.dll
[*] Scanning: C:\Windows\System32\wkscli.dll
[*] Scanning: C:\Windows\SYSTEM32\combase.dll
[*] Scanning: C:\Windows\system32\GDI32.dll
[*] Scanning: C:\Windows\System32\profapi.dll
[*] Scanning: C:\Windows\system32\CFGMGR32.dll
[*] Scanning: C:\Windows\System32\DEVOBJ.dll
[*] Scanning: C:\Windows\System32\CRYPTSP.DLL
[*] Scanning: C:\Windows\System32\CRYPTBASE.DLL
[*] Scanning: C:\Windows\System32\bcryptPrimitives.dll
[*] Scanning: C:\Windows\System32\LOGONCLI.DLL
[*] Scanning: C:\Windows\System32\SSPICLI.DLL
[*] Scanning: C:\Windows\system32\IMM32.DLL
[*] Scanning: C:\Windows\system32\MSCTF.dll
[*] Scanning: C:\Windows\SYSTEM32\kernel.appcore.dll
[*] Scanning: C:\Windows\System32\rsaenh.DLL
[*] Scanning: C:\Windows\System32\bcrypt.dll
[*] Scanning: C:\Windows\System32\vaultcli.DLL
[*] Scanning: C:\Windows\system32\WINTRUST.dll
[*] Scanning: C:\Windows\SYSTEM32\shcore.dll
—SUMMARY:
Total scanned: 48
Hooked: 0
Replaced: 0
Other suspicious: 1
Total modified: 1
Dumps saved to the directory: process_2688
—
C:\Users\Administrator\Desktop\PSuite>
We can analyse the dropped/extracted file using PEstudio and see it’s Mimikatz binary.
Happy Hacking and Bypassing AV’s !!
Source:https://www.c0d3xpl0it.com/2017/12/process-doppelganging.html
Source:https://www.c0d3xpl0it.com/2017/12/process-doppelganging.html

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.