A team of Oxford and Cambridge researchers is the latest to join a chorus of voices sounding the alarm on a new attack vector named Intra-Library Collusion (ILC) that could make identifying Android malware much harder in the upcoming future.
The research team has described the ILC attack vector in a research paper released last month and named “Intra-Library Collusion: A Potential Privacy Nightmare on Smartphones.”
ILC attacks are undetectable and devilishly clever
An ILC attack relies on threat actors using libraries to deliver malicious code, instead of standalone Android apps packed with all the malicious commands.
Apps usually require permissions for all the operations they need to perform. An ILC attack relies on spreading the malicious actions across several apps that use the same library(ies).
Each app gets different permissions, and malicious code packed in one app could use shared code from other apps — with higher privileges — to carry out malicious operations.
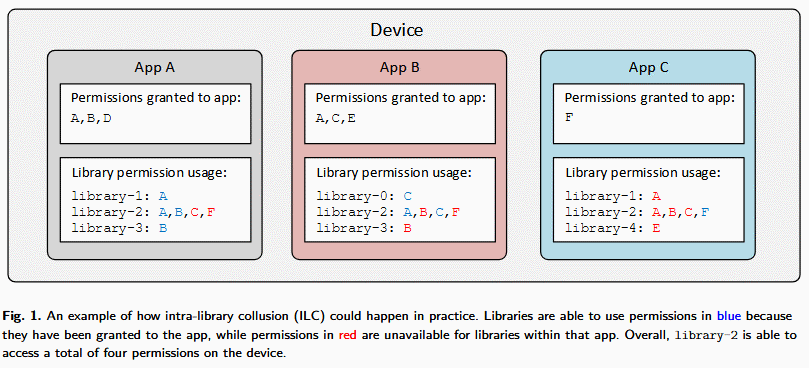
The advantage — for malware authors — is that investigators analyzing a compromised devices would see the breadth of malicious activities, but would exclude certain apps as the infection’s source because they do not possess all the permissions needed to execute the attack.
Current danger comes from advertising and analytics SDKs
For their research, experts analyzed 15,052 of the most popular Android applications installed on 30,444 devices.
The results showed that at the moment, the most popular libraries spread across different apps are advertising and analytics related, such as the SDKs offered by Facebook (11.9%), Google (9.8%), Flurry (6.3%), and others.
Researchers argue that unscrupulous advertising and analytics companies could very well exploit the SDKs they provided to app developers to gather data from users’ devices using ILC attacks.
Similarly, an attacker could deliver a malicious app that asks for little to no permissions but takes advantage of Google, Facebook, and other SDKs already installed in legitimate apps to carry out spyware-like behavior by collect location data, call information, access the microphone, or the device’s storage to spy on users and retrieve files.
Attack vector is known for years
The ILC attack vector — also known as Mobile App Collusion (MAC) — is nothing new and other researchers have investigated the topic in the past [1, 2, 3], and some have warned that both iOS and the browser permission model could be abused in the same way [1, 2].
This scenario is far from theory, as it has already been detected used in the wild. In June 2016, Intel Security (now McAfee), reported it discovered 21 Android apps carrying out ILC attacks.
Currently, the immediate danger comes from advertising and analytics companies, but it’s not hard to imagine spyware and surveillance tech vendors deploying ILC in the upcoming future.
Furthermore, because malicious operations are spread across different apps, Google is currently unable to detect ILC-capable apps when uploaded on the Play Store and will have to revamp its security checks in order to catch future threats. Currently, the only way to detect ILC attacks is by manual code review.
Proposed mitigations to deal with ILC attacks call for proper software isolation or the usage of library-level permissions, but none have been deemed acceptable solutions so far, creating more problems than fixing.
Source:https://www.bleepingcomputer.com/news/security/intra-library-collusion-attacks-open-the-door-for-a-whole-new-kind-of-android-malware/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











