US cyber-security firm Symantec has issued a warning today against a group of nation-state hackers that have managed to infiltrate several US and European energy firms, and are now in the dangerous position of sabotaging critical infrastructure if they wished to.
The group behind these attacks is a well-known foe of the cyber-security community, known primarily under the name of Dragonfly, but also as Energetic Bear, Crouching Yeti, and Iron Liberty.
Dragonfly has been active since 2010 but went dark in 2014 when Symantec published an exposé on its activities up to that point.
DragonFly revamped tactics and retooled malware arsenal
According to a new report on the group’s activity released today, Dragonfly didn’t cease activities but worked to revamp its entire mode of operation.
Symantec researchers say that looking back at historical data, they managed to identify attacks using these new techniques going back to December 2015.
The group switched from custom built malware to a “living off the land” approach that relies on using OS management tools already present on most Windows stations, such as PowerShell, PsExec, and Bitsadmin.
They also switched to using mundane malware and even employed the Phishery open source credentials-stealing toolkit available on GitHub.
Hackers move to second phase
Experts also observed a change in targeting. They say the initial campaigns detected up to 2014 were focused on learning how energy facilities worked, while the recent attacks are focused on “gaining access to operational systems themselves, to the extent that the group now potentially has the ability to sabotage or gain control of these systems should it decide to do so.”
The recent campaign, which they tracked under the name of Dragonfly 2.0 was also much more active than the first, with a larger number of attacks detected.
According to Symantec, Dragonfly 2.0 attacks were spotted in the US, Switzerland, and Turkey. “The U.S. and Turkey were also among the countries targeted by Dragonfly in its earlier campaign, though the focus on organizations in Turkey does appear to have increased dramatically in this more recent campaign,” Symantec said in a report today.
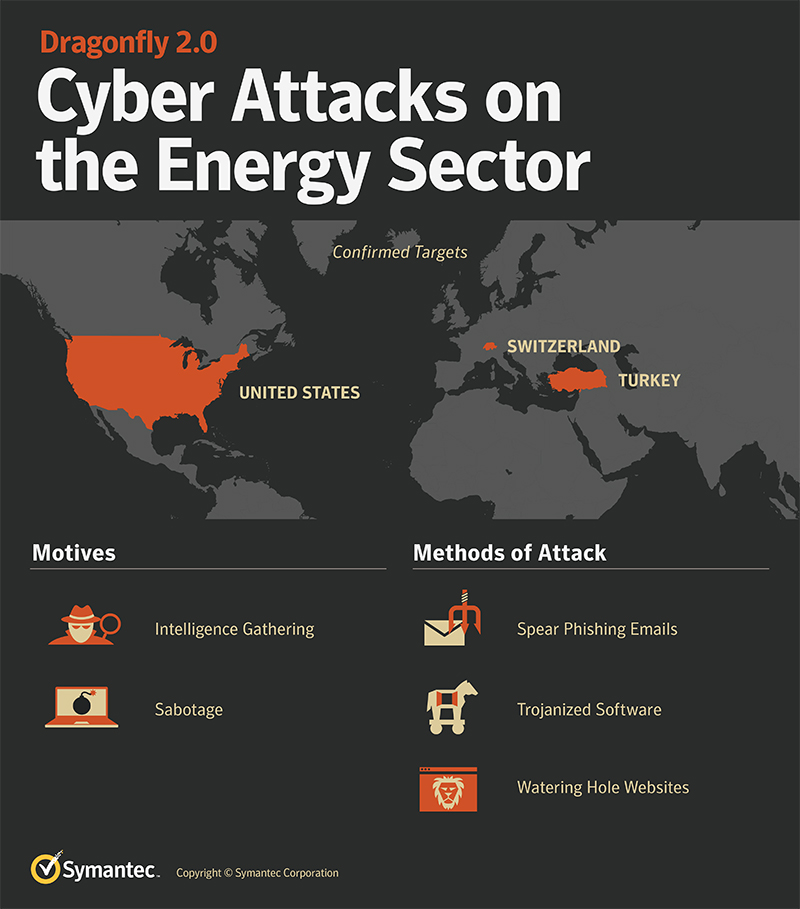
In July, the DHS and FBI issued alerts to companies in the energy sector regarding the attacks. For that attack, the Dragonfly group used a clever Word trick to collect credentials for internal networks via rogue SMB requests hidden in Word template files.
Experts fear sabotage
Researchers are particularly worried by the data the group managed to steal from infected computers. One of the backdoors the group deployed on infected computers had the ability to take screenshots of the user’s computer.
Researchers say the format of these screenshots was “[machine description and location].[organization name]” and that the term “cntrl” was found in many screenshots, meaning the group managed to infect computers that had “control” over key SCADA equipment and other operational systems.
“The Dragonfly 2.0 campaigns show how the attackers may be entering into a new phase, with recent campaigns potentially providing them with access to operational systems, access that could be used for more disruptive purposes in future,” Symantec explains.
In the past, researchers said they believed the group to be operating out of Russia, but no solid evidence was ever presented. Symantec didn’t find any new clues in this second campaign either. Researchers said they found text in both Russian and French in the malware samples they analyzed, but they were unable to determine if these were intentionally planted false flags, copy-pasted code, or authentic code written by the group itself.
At the time of writing, the only countries where cyber-espionage groups have carried out sabotage attacks on critical infrastructure are Iran (Stuxnet attack) and Ukraine (BlackEnergy and Industroyer attacks).
Source:https://www.bleepingcomputer.com/news/security/sabotage-warning-issued-on-hackers-hiding-deep-inside-energy-sector/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











