A team of researchers from Fox-IT and Riscure has put together a device using off-the-shelve electronic parts that deduces encryption keys using only electromagnetic emissions coming from a nearby computer.
The device exploits a well-known side-channel attack known as “Van Eck phreaking” and was specifically built to recover the encryption key from AES256 algorithms.
Attack carried out with €200/$230 test rig
Attacks like these usually employ expensive equipment, but researchers say they were able to pull something like this off using a rig that cost around €200, or $230.
The encryption-key-sniffing rig consists of a magnetic loop
antenna, an external amplifier, bandpass filters, and a software-defined radio receiver USB stick.
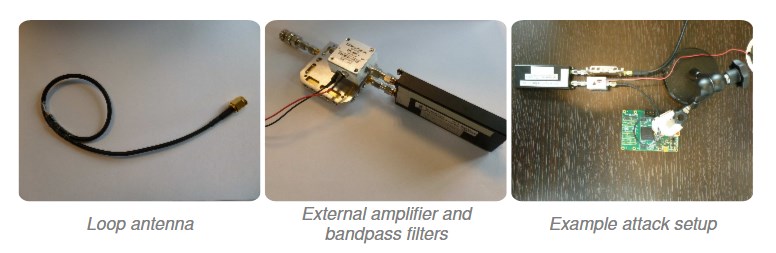
The research team says the rig is small enough to fit in a jacket pocket, a laptop case, or any other inconspicuous bag. Researchers say that an attacker can carry this device near a computer or device known to handle encryption operations and let it sniff out electromagnetic waves.
If the sniffing device is placed around one meter away from the target, the device needs up to five minutes to sniff out an encryption key. If the distance is shortened to 30 centimeters, the device only needs 50 seconds.
Theoretically, the closer the attacker can get to his target, the stronger the electromagnetic waves coming from the device get, and the shorter time the device needs to sniff the encryption key.
Device guesses encryption key
Internally, the device works by recording electromagnetic waves coming from a nearby computer, which equate to its power consumption spikes.
“This is useful because part of the power consumption depends on the data the device is handling,” researchers say. “It is this data dependence we exploit to extract the key.”
Experts say they can identify blocks where encryption is applied by a spike in power consumption needed to compute the mathematical operations for the AES256 algorithm. Once they identify one of these blocks, researchers move to the next step.
Now we try to extract the secret key using a combination of guessing and correlation. […]as attackers, we do not know the [encryption] key… but we can simply perform this prediction and correlation for all 256 possible values of 1 byte from the key. The value which provides the biggest peak in correlation should be the correct value. Using this approach only requires us to spend a few seconds guessing the correct value for each byte in turn (256 options per byte, for 32 bytes — so a total of 8192 guesses). In contrast, a direct brute-force attack on AES-256 would require 2256 guesses and would not complete before the end of the universe.
Attack only tested in a lab environment
In theory, the device is well suited to attack network encryption appliances situated in data centers or air-gapped networks, but also regular computers.
Nonetheless, the team’s experiments were only carried out in an isolated test environment, where both the target and the test rig where isolated from external electromagnetic waves. It is unclear how the attack rig would perform in a real-world environment where the device could be confused by all the electromagnetic waves bouncing around from nearby devices.


The team’s research is documented in a paper entitled TEMPEST attacks against AES.
Van Eck phreaking attacks have been carried out before in similar research papers. Computer tech expert William Entriken has carried out a similar experiment.
A team of scientists from an Israeli university used a similar attack to get an encryption key from a computer in another room, through a thin wall.
Another research project carried out by Australian and Israeli researchers recovered encryption keys from the electromagnetic emissions given by Android and iOS devices.
Source:https://www.bleepingcomputer.com/news/security/experts-recover-aes256-encryption-key-from-a-pcs-electromagnetic-emissions/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










