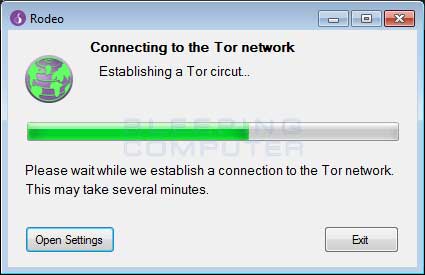
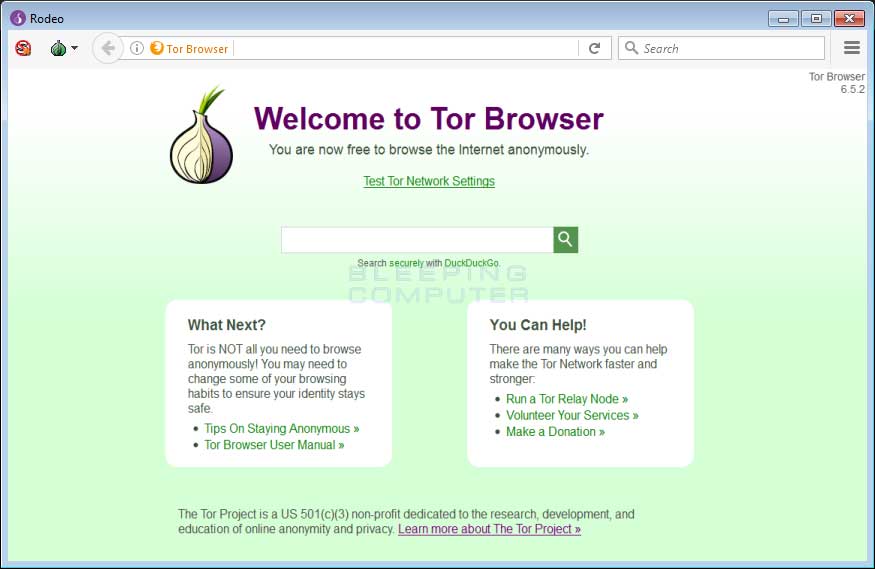
A malicious app disguised as a modified version of the Tor Browser is targeting users looking to buy illegal products off the Dark Web.
Discovered by BleepingComputer’s Lawrence Abrams last week, this malicious app is distributed using YouTube videos that teach non-technical users how to buy products from a Dark Web marketplace called The Rodeo.
Instructions in the YouTube videos tell users to download the Rodeo Browser, which is a modified version of the Tor Browser specifically built to let users access The Rodeo marketplace.
Rodeo Browser mimics Tor. Is coded in .NET
In reality, the Rodeo Browser is nothing more than a basic UI shell that was made to mimic the Tor Browser interface, and nothing more.
|
|
|
The Rodeo Browser is coded in .NET and none of its buttons work. When users try to click on anything, an error like the one below is displayed.
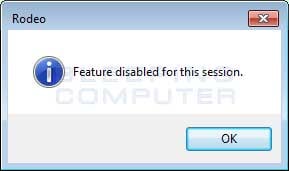
The only thing that works is the Settings drop-down menu, which provides users with the option to load The Rodeo marketplace. When users press this option, the fake Tor Browser pretends to connect to a fake onion site called th3rod3o3301jtxy.onion.
At no times does the Rodeo Browser use Tor. The Rodeo browser’s sole purpose is to connect to a remote FTP server and retrieve content to show on the “site.”
Everything on the site is fake. Everything. All content is downloaded from a FTP or web server, where it’s usually stored in either text or Base64 or encrypted HTML files. The FTP server is located at th3rod30.xyz, and some files are also available on a public web folder at th3rod30.xyz/s.
The Rodeo was built to scam foolish users
While it is not known for sure whether the site is a legit marketplace or a scam, it does appear that it was built to scam users and to perfectly mimics the classic model of any Dark Web marketplace.
Users need to register, log in, explore the merchandise, view vendor profiles, and place orders. The site says that all orders are encrypted via PGP keys, but we found no evidence of such behavior.
In reality, this supposed Dark Web marketplace appears to con non-technical users into placing orders and paying via Bitcoin for products they’ll never receive.
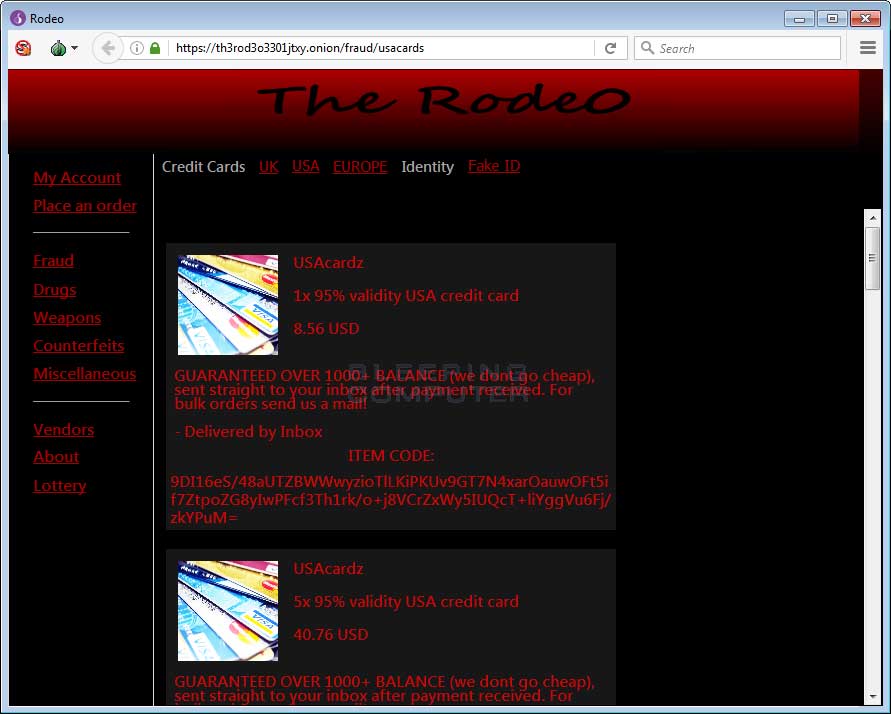
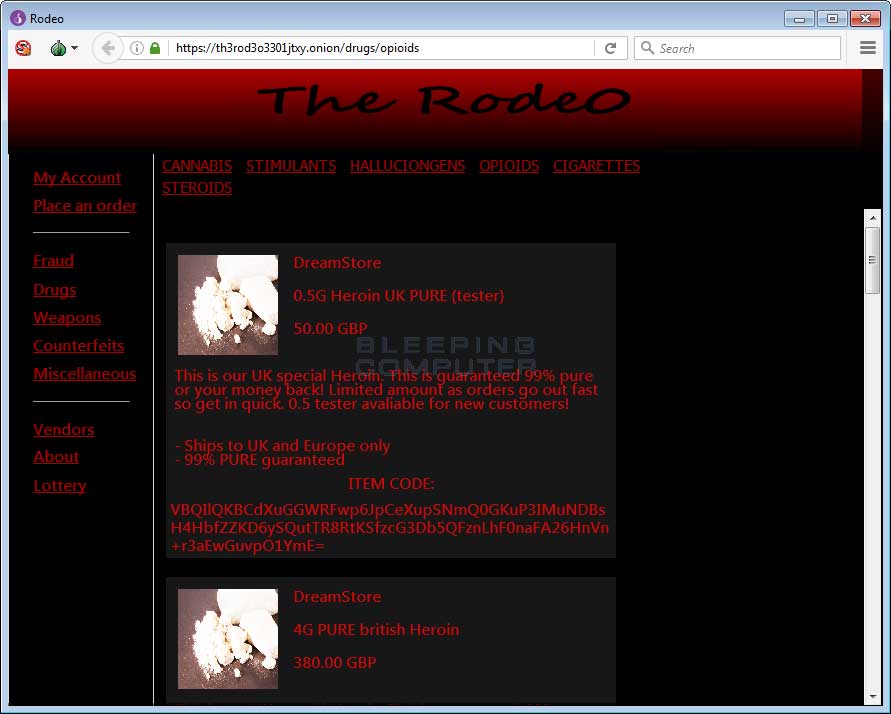
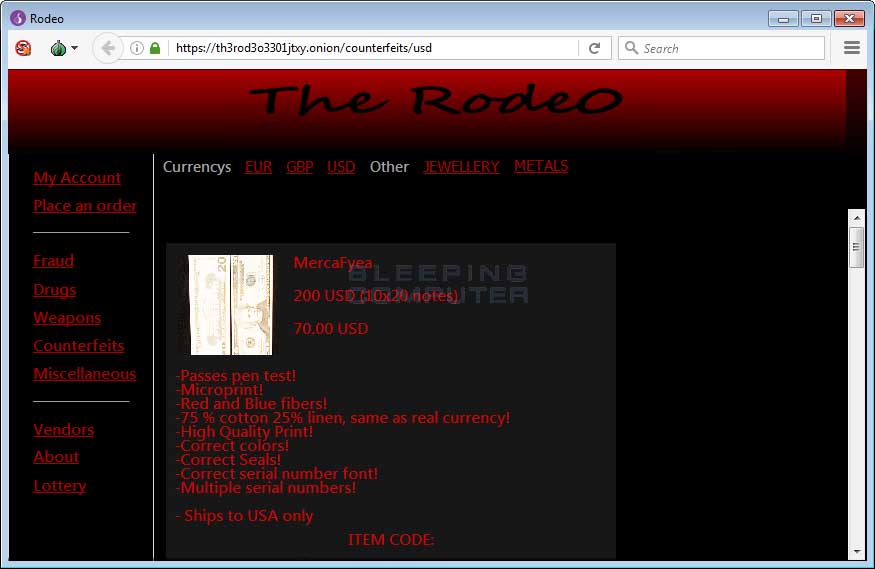
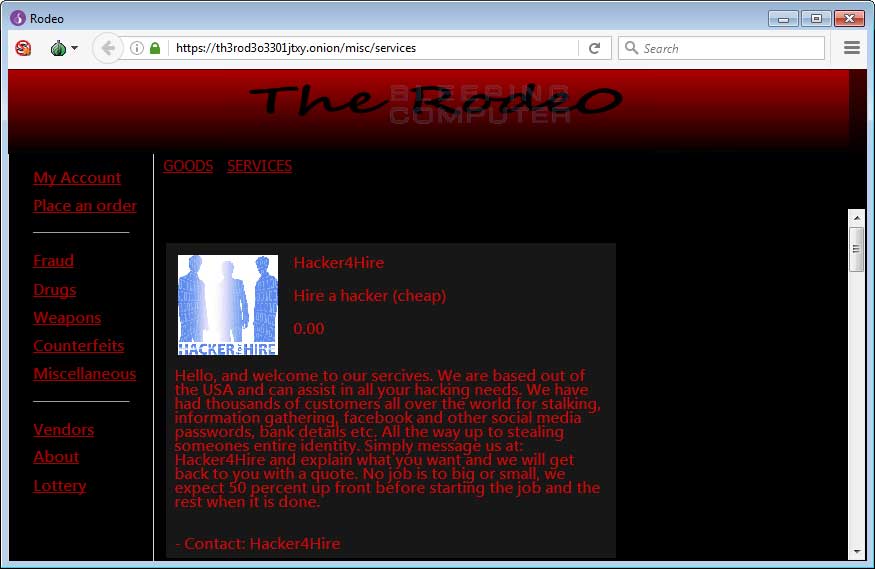
To make sure the fake marketplace makes as much money as possible, the site lists products from a wide variety of categories, such as drugs, weapons, counterfeit money, unlocked phones, hacking services, fake credit cards, and more. If AlphaBay admins weren’t so busy pulling off an exit scam right now, they’d probably be very jealous.
The Rodeo loads files from a remote FTP server
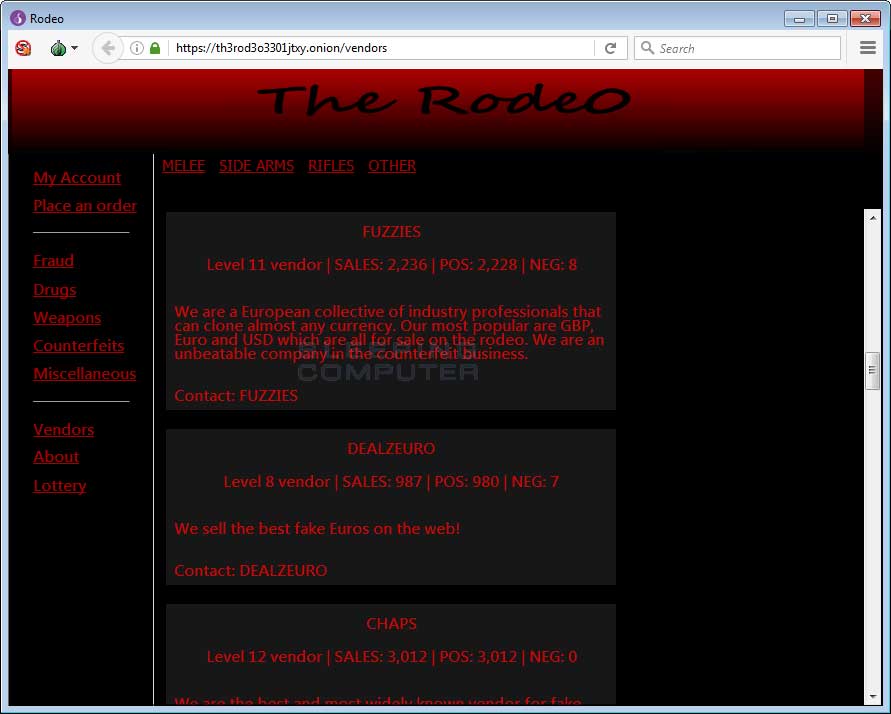
In reality, all the content users see on this fake marketplace was retrieved from text files stored on a remote FTP and web server. For example, we found text files for all the site’s vendors, all the products, and all the site’s menu options.
Furthermore, there are also folders for each user who registered on the site. Based on our research, the site has 138 users at the time of writing.
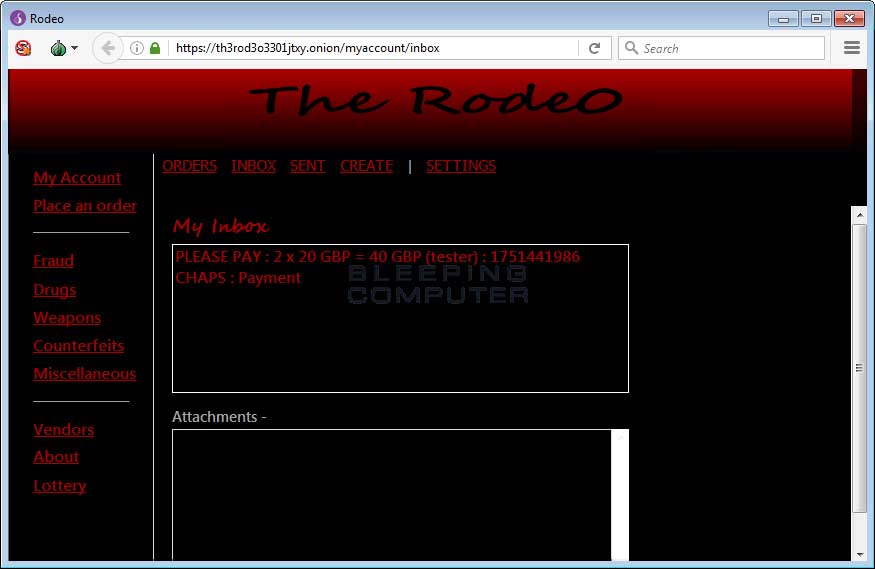
The folders for each user store the user’s password in cleartext, along with his private messages. (In cleartext. No PGP encryption. What a surprise!)
Bleeping Computer believes the site’s operator allows users to place orders to various vendors, but all messages reach the same person, who then provides victim’s with Bitcoin addresses where they can make payments before receiving their products. Based on the three Bitcoin addresses we found, at least three users sent Bitcoin to the site’s operator(s).
While we’ve seen plenty of scams in the past, this one takes the cake when it comes to creativity, even if the technical execution was not up to par with the social engineering part.
Below is a gallery of The Rodeo marketplace.
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
SHA256 hash:
e0742edb81c8626c6c4befa64f487c68611cc8969bb55f66accc3f4028697057
Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.