Today, WikiLeaks has published the documentation manual for an alleged CIA tool that can track users of WiFi-capable Windows devices based on the ESS (Extended Service Set) data of nearby WiFi networks.
According to the tool’s 42-page manual, the tool’s name is ELSA. The manual includes the following image to explain to CIA operatives how the tool works. A summary of an ELSA operation is included below the image.
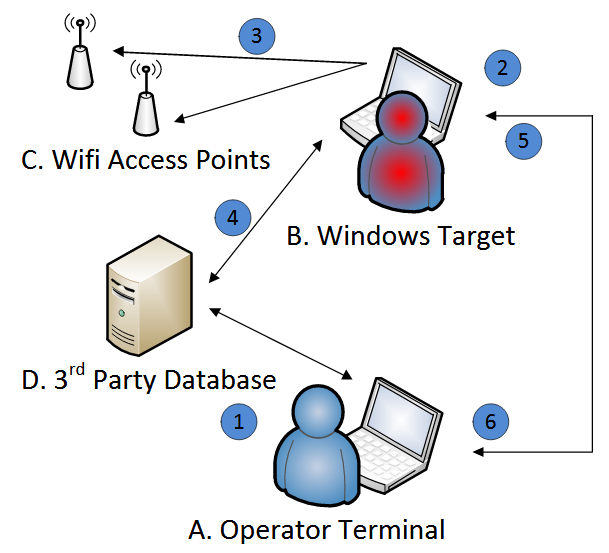
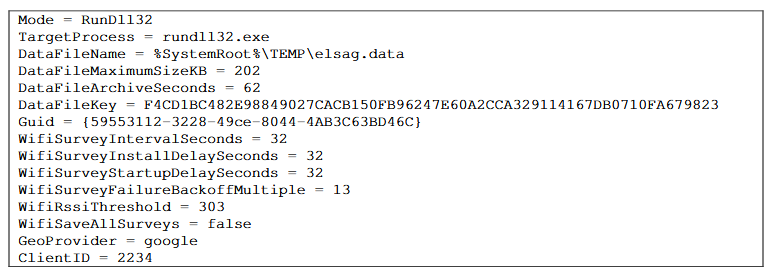
Step 1: CIA operative configures ELSA implant (malware) based on a target’s environment. This is done using a tool called the “PATCHER wizard,” which generates the ELSA payload, a simple DLL file. Target environment variables include:
The desired mode (dllhost, svchost, rundll32 or appinit)
The desired geo provider (Microsoft / Google)
The desired maximum log file size
Whether or not to resolve ap lists into geos from the target
Step 2: CIA operative deploys ELSA implant on target’s WiFi-enabled Windows machine. Because ELSA is an implant (malware), the CIA operator will likely have to use other CIA hacking tools and exploits to place the malware on a victim’s PC.
Step 3: The implant begins collecting wifi access point information based on the schedule set by the operator. Data collection can happen even if the user is disconnected from a WiFi network.
ELSA works by scanning for nearby networks and collecting their ESS information, which is unique for each network. ESS data includes MAC address, SSID, and signal strength. This information is stored in a local log file, which is encrypted with a 128-bit AES encryption key.
Step 4: When the target user connects to the Internet, ELSA will take the collected WiFi data and query a third-party database for geolocation information.
Each EES info is assigned a geographical location, and this data will allow CIA operatives to track the general location through which a target has moved.
These third-party databases exist and are managed by companies such as Google or Microsoft, who use them to support geolocation APIs for browsers such as Chrome, Opera, Firefox, Edge, or Internet Explorer.
Step 5: The CIA operative connects to the target’s computer and fetches the ELSA log. This is done via the tools that allowed the operator to place ELSA on his system, or through other tools.
Step 6: The operator decrypts the log and performs further analysis on their target. Optionally, he can use the collected WiFi data to query alternate EES geo-location databases, if he feels they provide a better accuracy.
Today’s WikiLeaks dump is part of a larger series called Vault 7, which contains documents WikiLeaks claims were stolen from the CIA by hackers and insiders. You can follow the rest of our WikiLeaks Vault 7 coverage here. Below is a list of the most notable WikiLeaks “Vault 7” dumps:
ᗙ Fine Dining – a collection of fake, malware-laced apps
ᗙ Grasshopper – a builder for Windows malware
ᗙ DarkSeaSkies – tools for hacking iPhones and Macs
ᗙ Scribble – beaconing system for Office documents
ᗙ Archimedes – a tool for performing MitM attacks
ᗙ AfterMidnight and Assassin – malware frameworks for Windows
ᗙ Athena – a malware framework co-developed with a US company
ᗙ Pandemic – a tool for replacing legitimate files with malware
ᗙ CherryBlossom – a tool for hacking SOHO WiFi routers
ᗙ Brutal Kangaroo – a tool for hacking air-gapped networks

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











