A research paper published by four Israeli scientists details a new attack called PRMitM, or the “Password Reset Man-in-the-Middle,” in which attackers hide password reset interactions for a user’s legitimate profile inside account registration interactions on another site.
The attack falls under the category of social engineering, as it requires an attacker to convince or lure a potential victim to register a profile on a boobytrapped website.
PRMitM attacks are hard to pull of
PRMitM attacks require an attacker to create special backends that take data entered into registration forms and sends it to another site’s password reset systems.
For example, as a victim is entering his username or email inside a registration form on a boobytrapped site, the malicious site’s backend send this information to the target’s Google, Yandex, or Yahoo page to initiate a password reset operation.
If the service asks for various challenges, such as CAPTCHAs, security questions, or SMS verification codes, the attacker updates the registration process with new steps asking the user to fill in these details to complete the registration form.
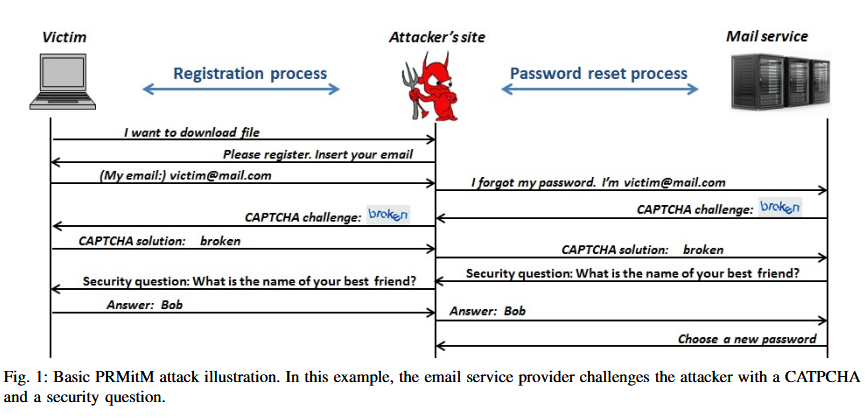
PRMitM attacks are efficient at taking over email accounts
This type of attack is only efficient for taking over email accounts. This is because most of today’s websites send a password reset link via email, exposing the attacker’s true actions. This is not true for email providers, who handle the process via other methods, such as the aforementioned CAPTCHAs, security questions, or SMS verification codes.
Furthermore, the attack relies on careless users. During their tests, researchers said that many users entered all the details the registration page asked for, without having a clue someone was trying to hack into their account.
Even when victims received verification codes via SMS, most users grabbed the code from the phone’s notifications panel, without reading the SMS’ entire content.
Some services such as Twitter or Facebook provide information in SMS messages regarding the code’s true purpose (for password resets, for sign-ups, etc.). Reading the entire SMS message would have saved users from having their accounts taken over.
Mitigation: Password reset links via SMS, not just email
To counteract PRMitM attacks in the future, researchers propose that services send at least a password reset link via SMS if they don’t send one via email already.
Receiving a password reset link via SMS when trying to sign-up on another website would alert any victim that something shady is going on.
Nonetheless, this mitigation won’t protect victims from state-level or determined actors who have resources at their disposal to exploit flaws in the SS7 protocol and hijack phone numbers to receive these password reset notifications on their own phones.
More details, case studies, and mitigations are available on the researchers’ paper entitled The Password Reset MitM Attack.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











