WikiLeaks dumped today the manuals of several hacking utilities part of Brutal Kangaroo, a CIA malware toolkit for hacking into air-gapped (offline) networks using tainted USB thumb drive.
According to WikiLeaks, Brutal Kangaroo is the generic name of a project that includes the following tools:
✶ Shattered Assurance – a server component running on infected hosts that automates the infection of thumb drives using malware generated via Drifting Deadline
✶ Shadow – tool to create and coordinate multiple infected computers on an air-gapped network, allowing operators to define a series of tasks to be executed on offline computers
✶ Broken Promise – tool to evaluate and exfiltrate data collected from air-gapped networks
How a Brutal Kangaroo attack works
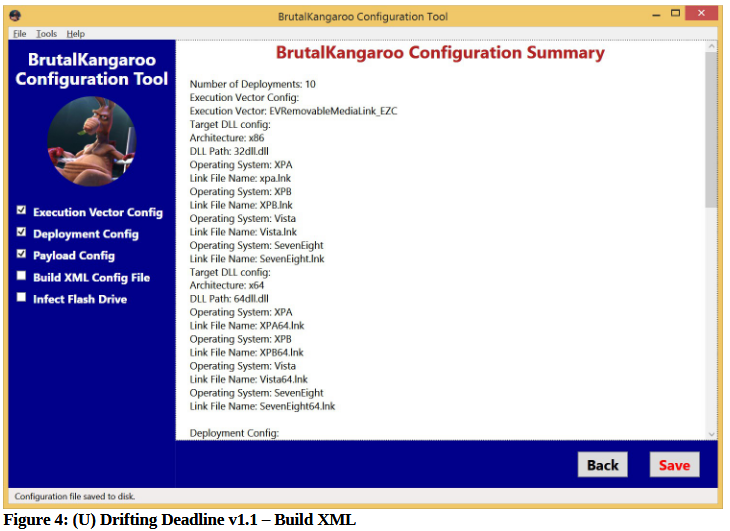
The CIA uses these tools as part of a very complex attack process, which starts with a CIA operative using Drifting Deadline to generate first and second-stage malware used in the attacks, on a per-target basis.
The process then moves on to using various other CIA tools to infect a computer in the target’s network. This process is not detailed, meaning CIA operatives can use whatever they have at their disposal to achieve this first infection.
This computer is called the “primary host” and is used as an infection hub. Whenever a user inserts a USB thumb drive into this primary host, the Brutal Kangaroo components will infect the thumb drive with malware, different from the one that infected the primary host, and tailor-made for USB thumb drives.
If the user takes this USB thumb drive and connects it to another PC, this second-stage malware will execute and infect that computer as well.
Air-gapped computers infected via malicious shortcut files
This second-stage malware dropped on tainted USB is extremely efficient, relying on malformed Windows LNK (shortcut) files. These LNK files will automatically execute their malicious payload whenever they are viewed inside a Windows Explorer window.
This is the same attack vector used in the Stuxnet attacks that took aim at Iran’s nuclear program.
Responsible for this attack are two CIA exploits named Giraffe and Okabi. Both support 32-bit and 64-bit architecture, but Okabi seems more efficient as its execution vector is supported for target machines running Windows 7, 8, and 8.1. On the other hand, the Giraffe “execution vector has been patched for all versions of Windows except for Windows XP,” according to data on page 3 and 4 of the Drifting Deadline manual.
The Brutal Kangaroo attack implies a heavy dose of luck, as it relies on the user taking the infected USB flash drive and using it to transfer data to and from air-gapped networks.
CIA can coordinate infections inside air-gapped networks
Brutal Kangaroo is also designed to support multiple infections inside the same air-gapped network. This feature is covered by the Shadow utility that’s installed on infected hosts via the malicious LNK files.
“Once multiple Shadow instances are installed and share drives, tasking and payloads can be sent back-and-forth,” the manual reads.
The purpose of such tool is for CIA operatives to send new commands into an infected air-gapped network after the initial Shadow tasks have been executed and initial data has been retrieved (via Broken Promise installed on the primary host).
Initial and additional Shadow tasks can be configured via a builder application, similar to the one used by Drifting Deadline.
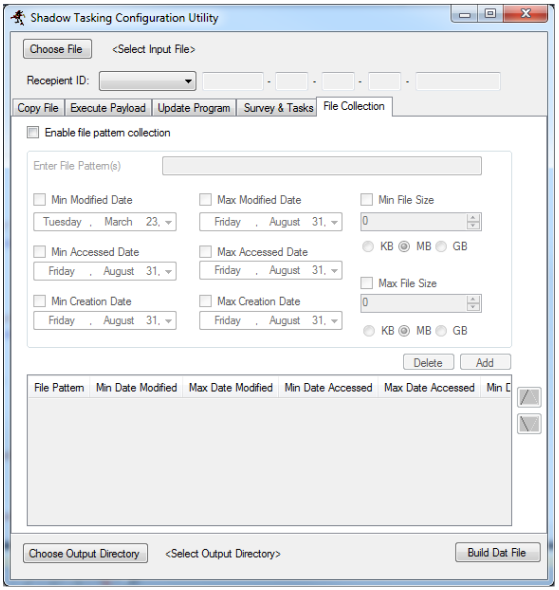
New versions of the Shadow malware can be generated this way, containing new malicious instructions. The CIA relies on the same primary host and the first-stage malware to infect new USB thumb drives to deliver this new Shadow malware versions to the same air-gapped network.
Some antivirus software detects Brutal Kangaroo attacks
But there are also some good news. According to the Drifting Deadline manual, dated February 23, 2016, several antivirus products are capable of detecting Brutal Kangaroo malware. The list includes Avira, Bitdefender, Rising Antivirus, and Symantec.

Furthermore, since February 2016, Microsoft has issued several security updates that patched flaws in LNK file handling, including one this month. It’s hard to believe that the CIA didn’t develop new execution vectors after some of the Giraffe and Okabi vectors were patchedd. Earlier this year, WikiLeaks promised to work with software vendors to patch some of the issues it received via the Vault 7 dump. It is unclear if the LNK issues Microsoft patched in the past few months are related to Brutal Kangaroo. Bleeping Computer has reached out to Microsoft for confirmation.
WikiLeaks published details about Brutal Kangaroo in March, when it announced its Vault 7 series. The initial mention was a simple document that included few details, unlike the user guides released today.
Today’s WikiLeaks dump is part of a larger series called Vault 7, which contains documents WikiLeaks claims were stolen from the CIA by hackers and insiders. You can follow the rest of our WikiLeaks Vault 7 coverage here. Below is a list of the most notable WikiLeaks “Vault 7” dumps:
ᗙ Fine Dining – a collection of fake, malware-laced apps
ᗙ Grasshopper – a builder for Windows malware
ᗙ DarkSeaSkies – tools for hacking iPhones and Macs
ᗙ Scribble – beaconing system for Office documents
ᗙ Archimedes – a tool for performing MitM attacks
ᗙ AfterMidnight and Assassin – malware frameworks for Windows
ᗙ Athena – a malware framework co-developed with a US company
ᗙ Pandemic – a tool for replacing legitimate files with malware
ᗙ CherryBlossom – a tool for hacking SOHO WiFi routers

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











