A recent surge in Android banking malware can be traced back to December 2016, when a malware coder under the name of Maza-in uploaded a tutorial on how to build Android malware on an underground hacking forum named Exploit.in.
Besides instructions on how to create a basic Android banking trojan, Maza-in’s tutorial also came with sample code, including a web-based backend with which the trojan would communicate and report on infected devices.
BankBot code weaponized in less than a month
In the past decade, whenever we saw the source code of various malware families leak online, we’ve also seen an immediate surge in crooks using that code to build their own tools. We’ve seen it with the ZeuS banking trojan, the EDA2 and HiddenTeam ransomware kits, and more recently with the GM Bot Android banking trojan, in early 2016.
It was the same with Maza-in’s creation, which he named BankBot. Barely a month after he published the BankBot tutorial and source code, Russian antivirus maker Dr.Web had detected the first malware using it to target Russian banks.
This first version was not distributed via apps uploaded on the Play Store, but it didn’t take long before such campaigns were detected by researchers from ESET [1, 2], and later by Securify [1, 2].
BankBot campaigns intensified in the last three months
Maza-in didn’t only publish his tutorial on Exploit.in, but also continued to update it with new info. The hacking community also chipped in, creating a weird melting pot of Android malware knowledge.
The knowledge shared there convinced more people to join in on “the fun.” Securify and ESET researcher Lukas Stefanko have put together blog posts detailing these campaigns, and they’re not a short read. Stefanko’s blog post alone lists 62 different BankBot campaigns, with the vast majority occurring in the last three months, April, May, and June.
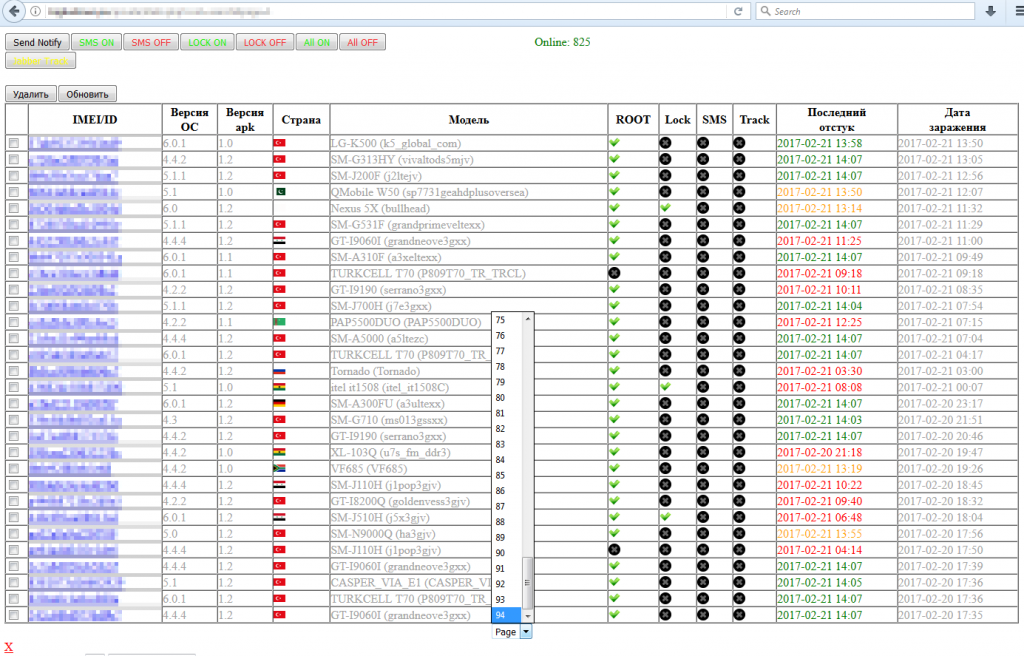
Searching Twitter for BankBot yields tens of tweets per day with security researchers reporting new BankBot control panels.
BankBot consistently fools Play Store security checks
This sudden surge in BankBot-based malware has also caught the attention of Fortinet and Check Point, two cyber-security firms that echoed Dr.Web’s initial findings and traced back this wave of Android banking trojans back to Maza-in’s forum post.
A vast majority of the infections these security companies detected used apps uploaded on the Google Play Store to spread to victims.
According to Check Point, this happened when malware devs obfuscated the malware’s code. This was more than enough to prevent Google’s automatic malware scanners from detecting the BankBot malware hidden inside apps submitted for review.
Maza-in suspected of creating Mazar BOT malware?
While Maza-in has been seen asking for help with basic questions about Android functions, it appears that he had “enough” knowledge to create BankBot.
Furthermore, in a private conversation posted on Ripper, a platform for exposing thieves and scammers in the underground community, Maza-in inadvertently revealed that he might have created Mazar BOT, an older banking trojan that was active in 2015 and early 2016.
If this is true, then according to IBM Maza-in is the mysterious coder who bought the GM Bot Android banking trojan in its earliest stages of development and developed it as Mazar BOT.
This is important because GM Bot is one of the most sophisticated banking trojans seen today, and who is behind the first surge of Android banking trojans that took place in 2015-2016.
The trojan was offered for sale on underground hacking forums, and the crooks who bought it used GM Bot as the platform to create other Android banking trojans such as Bankosy, Acecard, SlemBunk, and Mazar BOT.
GM Bot was the work of a crook called GanjaMan, and v1 was dumped online by a dissatisfied customer in early 2016. GanjaMan came back with GM Bot v2 a few months later, but he was banned from most hacking communities for lack of proper customer support.
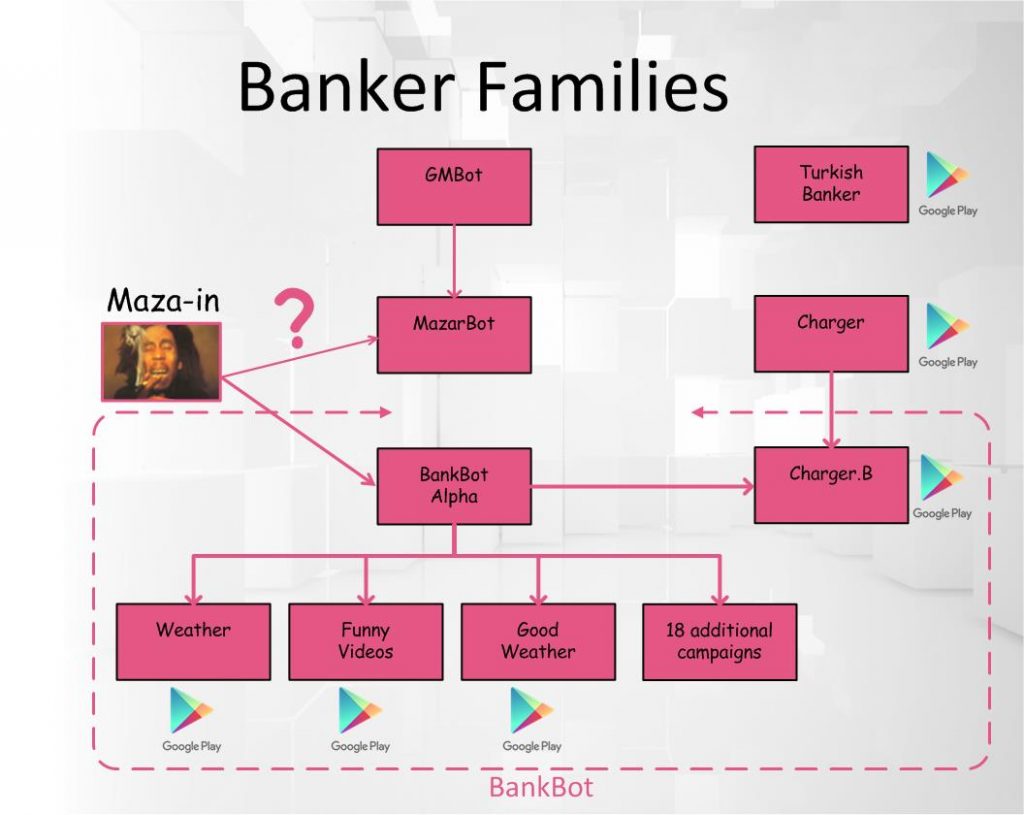
BankBot is choke full of features
Maza-in’s early involvement with GM Bot explains from where he got all his experience with Android malware because, in spite of being dumped online as a tutorial, BankBot is choke full of features.
For example, the malware can show overlays on top of apps on different Android OS versions, can intercept SMS messages and USSD codes to defeat two-step verification, and can steal credentials from a long list of apps, not just banking applications.
Furthermore, the BankBot malware has been packaged in such a way that malware authors downloading its sample source code only need to create the fake overlay that gets shown on top of the real app they want to target.
This greatly reduces the entry barrier for many crooks who might not have the technical expertise to create their own trojan.
In an interview with Forbes, Maza-in said he published the tutorial and BankBot source code only to raise awareness to security holes in the Android OS. This is complete BS.
Maza-in knew exactly what he was doing. If he wanted to raise awareness to Android security flaws, he would have reached out to Google, not publish his “worries” about the poor Android OS on the Internet’s most infamous underground hacking forum.
Source:https://www.bleepingcomputer.com/news/security/you-can-blame-this-guy-for-the-recent-surge-in-android-malware-on-the-play-store/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










