A self-proclaimed member of the Anonymous hacker collective is behind a campaign to spread the Houdini RAT and is currently looking into deploying the MoWare H.F.D ransomware.
The name of this “hacker” is Mohammed Raad, according to his Facebook profile, but he also goes online by the nickname of “vicswors baghdad,” according to his Facebook, Twitter, Google+, and YouTube profiles.
 |
 |
 |
 |
While there are countless of people who download and fool around with malware kits, Recorded Future claims this actor took it one step further by launching real-world campaigns.
Recorded Future: Raad behind some Houdini campaigns
Raad’s actions would have gone unnoticed if he wouldn’t have weaponized and started distributing Houdini (or H-worm), a VBScript-based RAT that was created and first spread in 2013. His biggest mistake was by using PasteBin to store the RAT’s main body, a VBScript file.
Because threat intelligence firm Recorded Future regularly scrapes and archives PasteBin uploads, his actions were uncovered earlier this month, after experts observed an overall increase in VBScripts posted on online paste sites.
Analyzing this surge, experts realized that most of the scripts were the Houdini VBScript. Analyzing the data, they identified three spikes of activity in August 2016, October 2016, and March 2017.
Recorded Future experts believe an infected computer would download the VBScript from the paste site, which would later connect to a C&C server and gain persistence on the infected host by setting up a local folder and registry key.
Raad registered a C&C domain under his real name
To find more details on who was behind this surge in VBScripts on paste sites, researchers took a look at all the C&C server URLs found inside the Houdini scripts.
This search identified C&C servers hosted on 105 subdomains for dynamic DNS providers (ddns.net, no-ip.com, etc.), but also one clear net domain.
That domain was microsofit[.]net, which was registered by Raad. At this point, researcher realized that many of the other 105 dynamic DNS subdomains were variations on this actor’s name, either using Raad or the word Mohammed in the subdomain name (mohammadx47.ddns.net; mohamedsaeed.ddns.net; etc.).
It didn’t take long for researchers to find Raad’s social media profiles, where they found his affiliation with the Anonymous hacker collective, inclination for dabbing in malware, and messages through which he entered promotions for the dynamic DNS services he used in the C&C server infrastructure.
Raad is playing around with ransomware
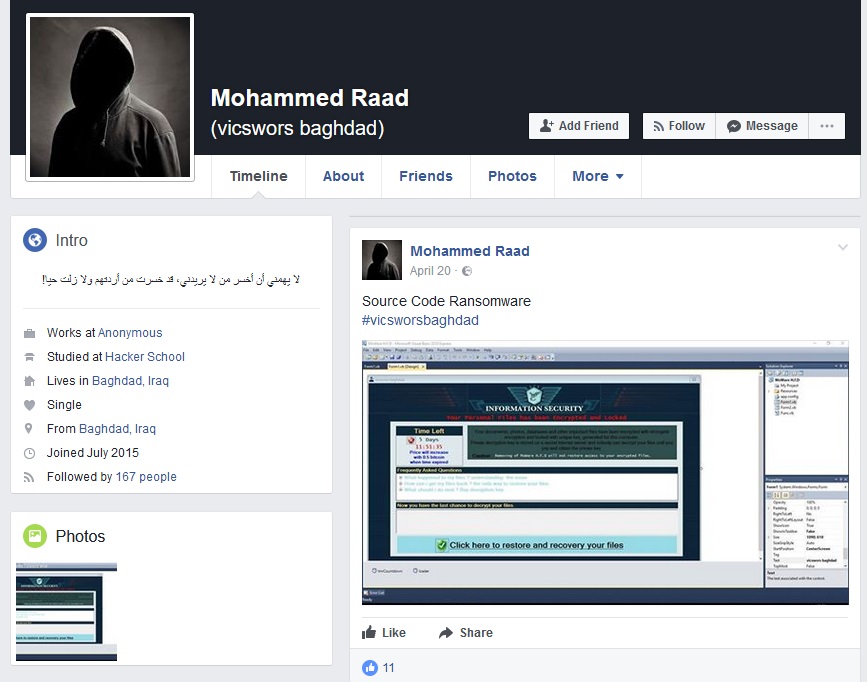
Furthermore, they found comments made by Raad on a YouTube video advertising the MoWare H.F.D ransomware, asking the author for a copy of the ransomware package. A few days later, Raad posted an image on Facebook showing the MoWare ransomware source code, implying that he received a copy, and was currently editing the code.
There is no evidence the author released his ransomware in the wild. Raad’s social media profiles suggest he’s an Iraqi national living in Munich, Germany.
Raad did not respond to a request for comment from Bleeping Computer in time for this article’s publication.
Other actors leveraging paste sites
According to Recorded Future experts, malware authors are increasingly abusing paste sites as cogs in their malware distribution campaigns.
A day before the report unmasking Raad’s activity, Recorded Future experts uncovered the activity of another crook, going by the name of Leo and wzLeonardo.
Experts say Leo was using a VBScript hosted on Pastebin that when executed would install the njRAT remote access trojan on the victim’s computer, while also downloading encrypted RAT encrypted strings stored on HasteBin, another paste site. Recorded Future believes Leo is based either in Brazil or Tunisia.
Source:https://www.bleepingcomputer.com/news/security/anonymous-member-playing-with-houdini-rat-and-moware-ransomware/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










