An attacker or a rogue employee can create and register custom control panel items and use these files to bypass the Windows AppLocker security feature.
AppLocker is a security service introduced with Windows 7 and Windows Server 2008 R2 that allows system administrators to restrict access to Windows applications based on a rule-based system.
Besides blocking access to games and non-work related applications, system administrators also use AppLocker to set up rules to prevent malware installed on the accounts of low-privileged users from accessing apps that can be abused to carry out attacks, such as cmd.exe, powershell.exe, rundll32.exe, and others.
Researcher bypasses AppLocker using CPL files
AppLocker is not impregnable, and there are various bypass techniques available online. The latest of these was disclosed last Friday by Francesco Mifsud, a researcher at Context Information Security.
Mifsud’s method relies on CPL files, which are modified DLLs that load control panel items. For example, ncpa.cpl loads the Network Connections management screen.
CPL items aren’t fixed. Microsoft allows software installers to create CPL items that will show up in your Control Panel. For example, installing a video driver adds icons in your control panel for controlling that video driver’s configuration. That icon is a CPL file, and every time you load it, your computer basically runs “control.exe name.cpl”.
The Windows OS keeps a list of all CPL items inside the following registry key:
HKLM\Software\Microsoft\Windows\CurrentVersion\Control Panel\CPLsAttackers can edit registry key to create rogue control panel items
Mifsud says that an attacker can modify the value of this registry key and add his own CPL that he previously altered to launch cmd.exe and execute malicious commands.
Despite AppLocker blocking direct access to cmd.exe, this proxy-like technique starts the cmd.exe file, executing rogue commands or other scripts. Similarly, PowerShell or other wide-reaching Windows utilities can be launched via this method.
This bypass technique is possible because both “reg” and “regedit” are Microsoft-signed binaries, located in a trusted folder and allowed by AppLocker by default unless specifically blocked by administrators. Similarly for Control Panel (control.exe), who is also another Windows binary allowed by default AppLocker rules.
While blocking access to utilities like reg, regedit, and the Control Panel is one alternative, Mifsud recommends another method.
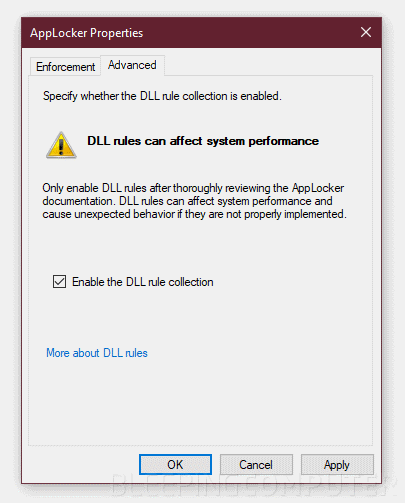
“[T]his attack can be mitigated, at the cost of performance, by enabling the ‘DLL Rule Collection’ under the AppLocker ‘Advanced’ tab,” Mifsud says.
There are various techniques to execute this attack, all of which are detailed in Mifsud’s technical write-up.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











