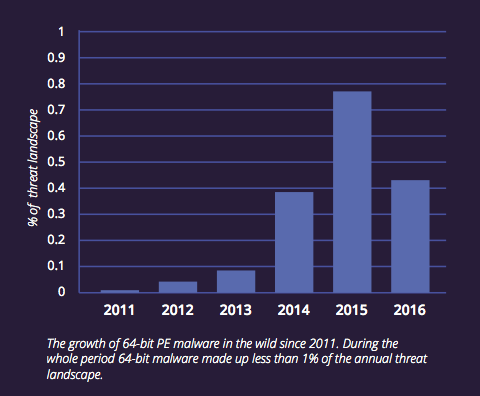
The volume of 64-bit malware in the wild remains low even though computers running 64-bit operating systems became ubiquitous years ago.
The vast majority (93 per cent) of new computers sold worldwide operate on 64-bit Windows but most nasties were written to infect 32-bit systems, according to a new study by security firm Deep Instinct.
Deep Instinct reckons that 64-bit malware still makes up less than 1 per cent of the current threat landscape. But malware variants have recently begun to appear in 64-bit versions so this small figure is likely to grow.
Various strains of ransomware and banking Trojan families (Zeus) have appeared in 64-bit versions over the last two years or so. Around 60 per cent of the 64-bit threat landscape is dominated by the worm-like Expiro spyware. Following that, the most common 64-bit families are Virut (20 per cent) and Nimda (10 per cent).
“Zeus, the leading banking Trojan, which is responsible for the theft of hundreds of millions of dollars, was the first of its kind to contain a 64-bit version,” Deep Instinct reports. “We expect other banking Trojans and ransomware to follows this trend, causing the numbers of 64-bit malware to increase in the coming years.
“Sophisticated 64-bit malware has already appeared in several APT campaigns. Notably, the destructive disk-wiping Shamoon malware, which destroyed data on 35,000 computers at Saudi Aramco.”
The the cyber-security industry may face “serious challenges in detecting malicious 64-bit files,” according to Deep instinct. Studies presented at Black Hat 2014 and elsewhere show that the industry underperforms on 64-bit files. White hats demonstrated that use of a 64-bit Meterpreter facilitates security package bypass.
A more recent study, published in July 2016, that tested the detection rates of different Meterpreter stagers based on VirusTotal scan results also highlighted shortcomings.
 Source: Deep Instinct
Source: Deep Instinct
Code shift
32-bit applications can run on 64-bit systems through the WOW64 (Windows-on-Windows-64) functionality, which provides backwards compatibility for 32-bit applications installed on 64-bit Windows. This explains why the shift in the malware landscape has lagged behind customer adoption of 64-bit systems.
While both 32-bit and 64-bit applications can be run on a 64-bit system, in most cases 32-bit code cannot access the memory of a 64-bit process. Driver-signing and the kernel “PatchGuard” protection make it extremely hard to infect 64-bit systems with rootkits. These factors, among others, are pushing miscreants into developing 64-bit malware.
“While many 32-bit malware variants can work on 64-bit systems, attacks demanding access to 64-bit process memory, such as code injection or privilege escalation attacks, will be much easier to undertake using 64-bit malware,” according to Deep Instinct. “Therefore, the threat landscape is expected to gradually shift to 64-bit malware, as 64-bit architectures and operating systems become the norm.”
Multiplatform
Malicious 64-bit executables are not unique to Windows systems. Linux and macOS systems are also potentially at risk.
As of the end of 2016, 64-bit variants make up just less than 10 per cent of the Linux threat landscape but their numbers are growing, according to Deep Instinct. Malware that supports 64-bit architecture makes up the majority of the macOS threat landscape – unsurprising as all macOS platforms since the 2011 vintage Lion run only on 64-bit architectures.
Examples of recent 64-bit macOS malware include KeRanger, a fully functional ransomware that specifically targets Mac users, and Komplex, a cyber-espionage Trojan created by APT28.
“As users continue to transition to 64-bit, malware authors will follow,” Deep Instinct concludes, adding that many advanced persistent threats discovered in recent years (such as BlackEnergy and Shamoon) included 64-bit malware.
Source:https://www.theregister.co.uk/2017/05/24/64bit_malware/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











