Decryption tool is of limited value, because XP was unaffected by last week’s worm.
Owners of some Windows XP computers infected by the WCry ransomware may be able to decrypt their data without making the $300 to $600 payment demand, a researcher said Thursday.
Adrien Guinet, a researcher with France-based Quarkslab, has released software that he said allowed him to recover the secret decryption key required to restore an infected XP computer in his lab. The software has not yet been tested to see if it works reliably on a large variety of XP computers, and even when it does work, there are limitations. The recovery technique is also of limited value because Windows XP computers weren’t affected by last week’s major outbreak of WCry. Still, it may be helpful to XP users hit in other campaigns.
“This software has only been tested and known to work under Windows XP,” he wrote in a readme note accompanying his app, which he calls Wannakey. “In order to work, your computer must not have been rebooted after being infected. Please also note that you need some luck for this to work (see below), and so it might not work in every case!”
Matt Suiche, a researcher and founder of Comae Technologies, reported he was unable to make Guinet’s decryptor tool work.
WCry, which also goes by the name WannaCry, covertly encrypts computer files after infecting a computer and then demands owners pay a $300 to $600 ransom to obtain the decryption key required to restore a computer to normal working condition. The ransomware uses the Microsoft Cryptographic Application Program Interface included with Windows to handle many of the functions, including generating the key for encrypting and decrypting the files. After creating and securing the key, the interface erases the key on most versions of Windows.
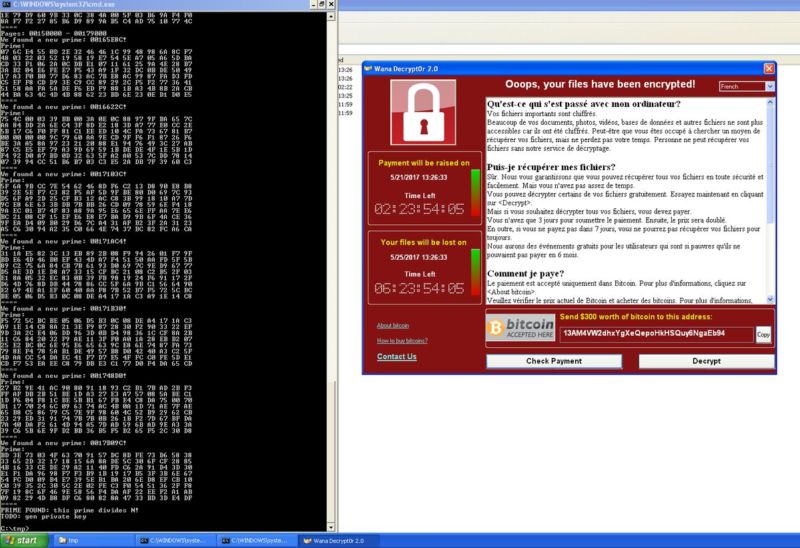
A previously overlooked limitation in XP, however, can prevent the erasure from occurring in that Windows version. As a result, the prime numbers used to generate a WCry secret key may remain intact in computer memory until the PC is powered down. Wannakey was able to successfully scour the memory of an infected XP machine and extract the p and q variables that the secret key was based on.
“If you are lucky (that is the associated memory hasn’t been reallocated and erased), these prime numbers might still be in memory,” Guinet wrote.
The researcher also wrote on Twitter: “I got to finish the full decryption process, but I confirm that, in this case, the private key can [be] recovered on an XP system #wannacry!!” He provided the screenshot at the top of this post.
Source:https://arstechnica.com/security/2017/05/windows-xp-pcs-infected-by-wcry-can-be-decrypted-without-paying-ransom/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.