One of the vulnerabilities used to spread the Stuxnet virus was 2016’s most popular exploit, according to telemetry data gathered by Russia cyber-security firm Kaspersky Labs.
Identified as CVE-2010-2568, this is a security bug found in older versions of the Windows Shell (CplLnk) that affects Microsoft’s Windows 7, Vista, XP, Server 2008 and Server 2003 operating systems.
Discovered and patched in 2010, the vulnerability was one of the four zero-days used in the cyber-attacks against Iran’s nuclear program, part of the Olympic Games Operation, the official code name for the Stuxnet program.
CVE-2010-2568 was 2015 and 2016 most popular exploit
Once the attacks were known, CVE-2010-2568 was exposed, dissected, and broken down by various security firms, which helped other threat actors, from state-sponsored groups to mundane spammers leverage and embed it into their operations.
Despite being more than half a decade old, the vulnerability remained extremely popular, due to the high number of Windws7 and XP computers still left on the market, many of which have remained unpatched.
According to Kaspersky, CVE-2010-2568 ranked first in terms of the number of users attacked last year. The company says that almost a quarter of all users who encountered any exploit in 2016 were attacked with CVE-2010-2568.
Similarly, a Microsoft report [Microsoft Security Intelligence Report Volume 20] revealed CVE-2010-2568 was also 2015’s most popular exploit.
CVE-2010-2568 strived despite exploit kit decline
The success of many exploits is usually guaranteed if they’re supported by a famous exploit kit, like Angler or Nuclear, or if they’re added to an exploit generator like Ancalog. Their addition to one of these ensures a large number of attacks and easy deployment by low-skilled attackers.
In spite of the fact that the Angler, Nuclear, and Neutrino exploit kits shut down in 2016, CVE-2010-2568 remained the top exploited vulnerability on the market, showing the wide adoption of this exploit went beyond the exploit kit market.
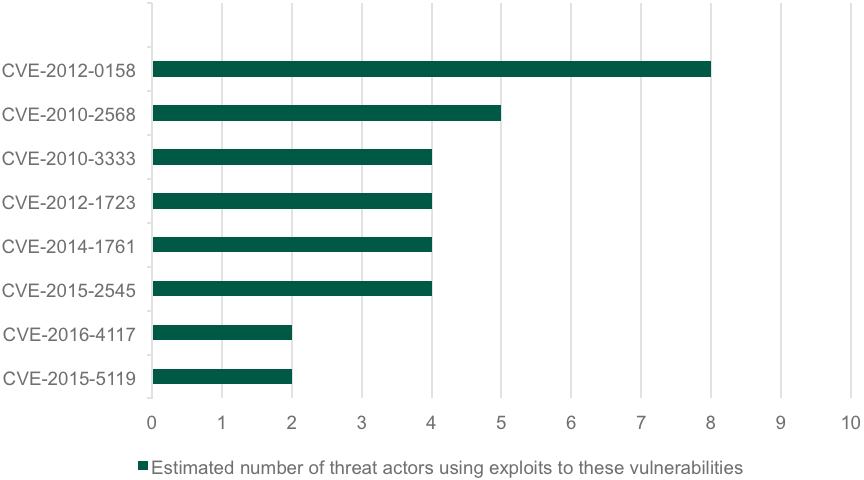
Furthermore, according to Kaspersky, CVE-2010-2568 was also the second favorite exploit kit used in targeted cyber-espionage campaigns, ranking second to CVE-2012-0158.
The conclusion of Kaspersky’s findings is that zero-days never die the day they’re patched unless users apply the patch. For example, most of the zero-days and vulnerabilities exposed in the Shadow Brokers leak from two weeks ago are bound to live on and plague millions of users for years.
This already became apparent last week, when security researchers already found over 36,000 Windows computers infected with the NSA’s DOUBLEPULSAR malware implant.
If you run older Windows OS versions and you want to avoid having machines vulnerable to the CVE-2010-2568, you can install MS10-046, the Microsoft security bulletin that patched this seven-year-old exploit. Similarly, Microsoft has also patched most of the flaws exposed by the Shadow Brokers dump, so why not hit two birds with one stone and patch those as well.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











